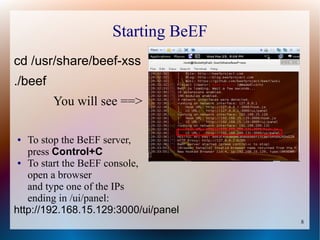
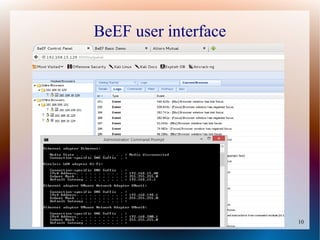
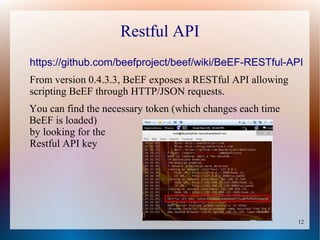
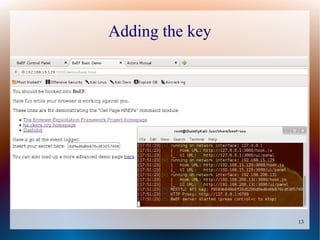
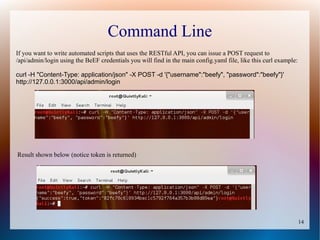
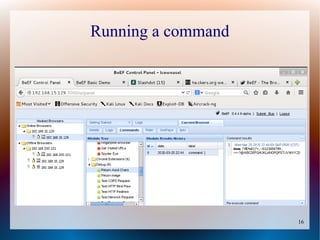
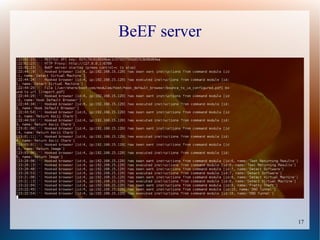
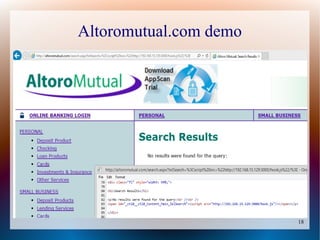
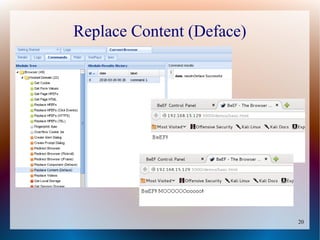
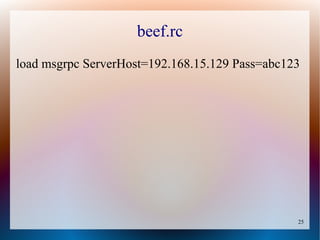
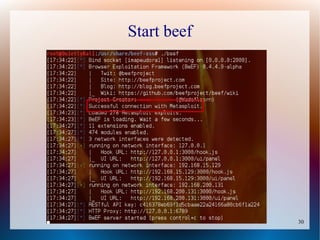
The document provides a tutorial on using the Browser Exploitation Framework (BeEF), an open-source pentesting tool that allows assessing client-side attacks by exploiting browser vulnerabilities to execute JavaScript code on the target system. It discusses how to install, configure, and use BeEF to hook browsers, run commands, interface with Metasploit, and find cross-site scripting vulnerabilities. Resources for additional exploitation techniques and modules are also referenced.



![4
Installation
● Installed by default on Kali
Directions for installing on other types of systems:
● https://github.com/beefproject/beef/wiki/Installation
● http://resources.infosecinstitute.com/beef-part-1/
[see section 2.1]](https://image.slidesharecdn.com/beef-project-tutorial-150419192545-conversion-gate01/85/Browser-Exploitation-Framework-Tutorial-4-320.jpg)