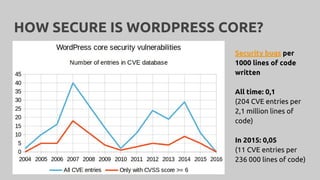
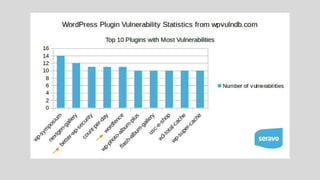
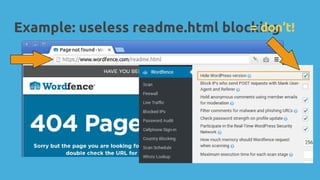
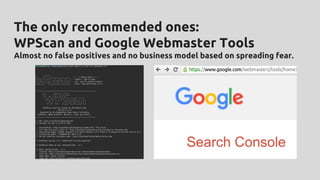
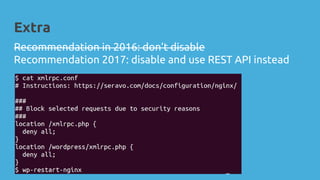
WordPress security involves critical aspects like confidentiality, integrity, and availability to prevent unauthorized access and attacks. Key recommendations include maintaining password hygiene, using HTTPS, minimizing software vulnerabilities, keeping plugins updated, and implementing a reliable backup system. The document stresses that neglecting security can lead to serious consequences, including reputation damage and potential legal issues.