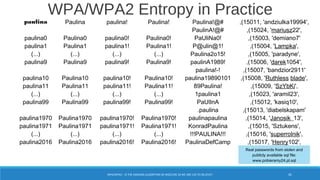
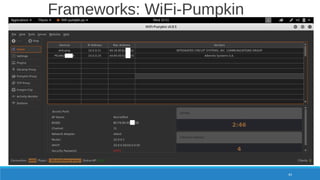
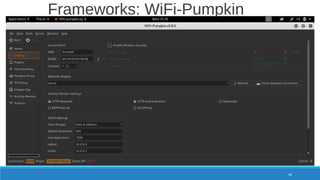
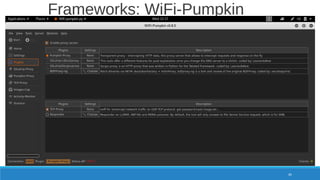
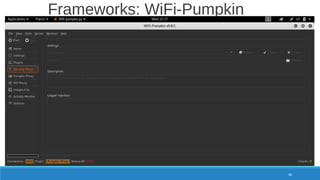
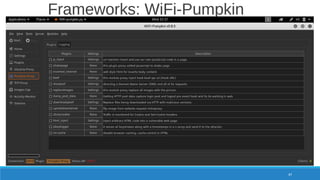
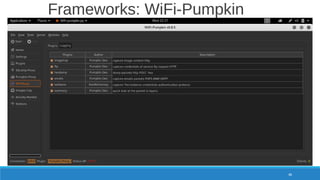
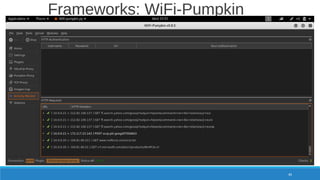
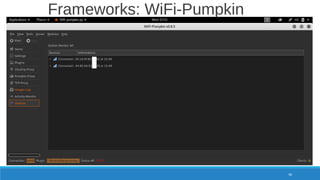
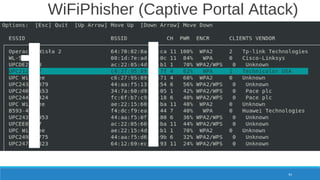
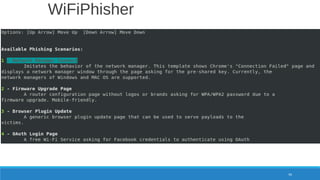
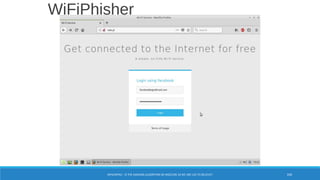
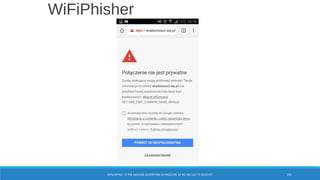
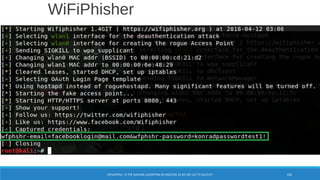
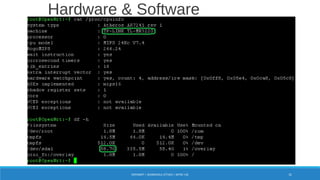
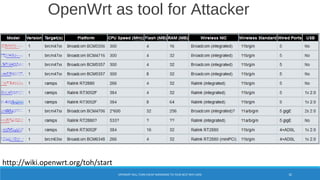
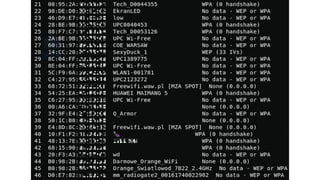
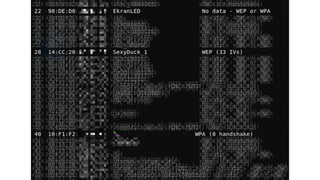
The document is a comprehensive guide on Wi-Fi hacking techniques, focusing on various hardware and software tools involved in wireless network penetration testing. It discusses multiple attacks, including WPA/WPA2 vulnerabilities, WPS exploitation, and the use of tools like Aircrack-ng and Hashcat for password cracking. Additionally, it covers preparation, gathering intelligence, and practical applications of these methods in a cybersecurity context.











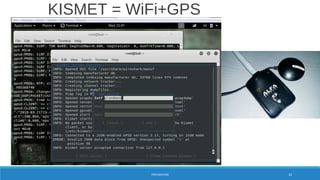
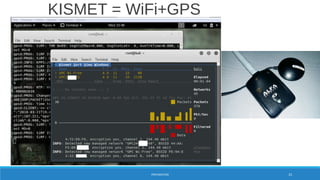
![Kismet-[date+hour].nettxt
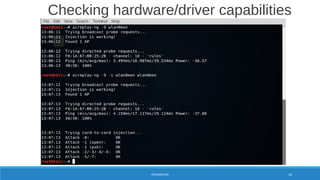
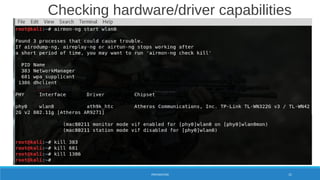
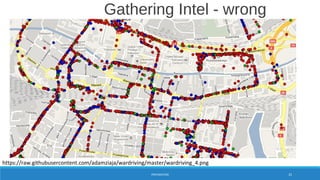
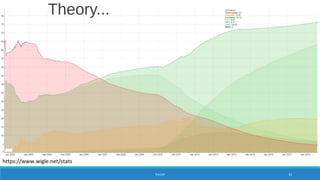
PREPARATION 24
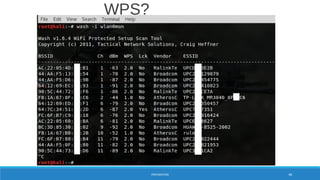
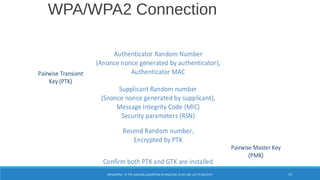
Network 4253: BSSID DC:53:7C:B7:AF:A2
Manuf : CompalBr
First : Wed Mar 21 16:05:29 2018
Last : Wed Mar 21 16:05:50 2018
Type : infrastructure
BSSID : DC:53:7C:B7:AF:A2
SSID 1
Type : Beacon
SSID : "House of Cards"
First : Wed Mar 21 16:05:29 2018
Last : Wed Mar 21 16:05:50 2018
Max Rate : 144.4
Beacon : 10
Packets : 3
WPS : Configured
Encryption : WPA+PSK
Encryption : WPA+TKIP
Encryption : WPA+AES-CCM
WPA Version: WPA+WPA2
Channel : 8
Frequency : 2447 - 3 packets, 100.00%
Max Seen : 1000
LLC : 3
Data : 0
Crypt : 0
Fragments : 0
Retries : 0
Total : 3
Datasize : 0
Min Pos : Lat 52.238670 Lon 20.988529 Alt 148.658997 Spd 0.000000
Max Pos : Lat 52.238674 Lon 20.988548 Alt 149.800995 Spd 0.000000
Peak Pos : Lat 52.238674 Lon 20.988548 Alt 148.658997
Avg Pos : AvgLat 52.238673 AvgLon 20.988536 AvgAlt 149.156900
Last BSSTS : Feb 26 09:02:14
Seen By : wlan0mon (wlan0mon) bc17995e-2d40-11e8-925d-5905352b2c03 3 packets
Wed Mar 21 16:05:50 2018
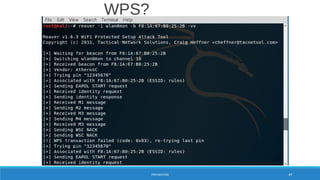
Client 1: MAC DC:53:7C:B7:AF:A2
Manuf : CompalBr
First : Wed Mar 21 16:05:29 2018
Last : Wed Mar 21 16:05:50 2018
Type : From Distribution
MAC : DC:53:7C:B7:AF:A2
Channel : 8
Frequency : 2447 - 3 packets, 100.00%
Max Seen : 1000
LLC : 3
Data : 0
Crypt : 0
Fragments : 0
Retries : 0
Total : 3
Datasize : 0
Min Pos : Lat 52.238670 Lon 20.988529 Alt 148.658997 Spd 0.000000
Max Pos : Lat 52.238674 Lon 20.988548 Alt 149.800995 Spd 0.000000
Peak Pos : Lat 52.238674 Lon 20.988548 Alt 148.658997
Avg Pos : AvgLat 52.238673 AvgLon 20.988536 AvgAlt 149.156900
Seen By : wlan0mon (wlan0mon) bc17995e-2d40-11e8-925d-5905352b2c03 3 packets
Wed Mar 21 16:05:50 2018](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-24-320.jpg)



![36
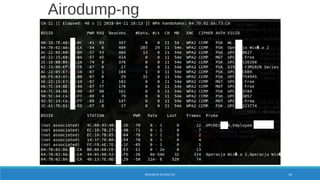
#!/bin/bash
MAC="$(echo $1 | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6)";
result="$(grep -i -A 4 ^$MAC ./oui.txt)";
if [ "$result" ]; then
echo "For the MAC $1 the following information is found:"
echo "$result"
else
echo "MAC $1 is not found in the database."
fi](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-36-320.jpg)






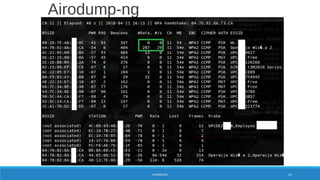
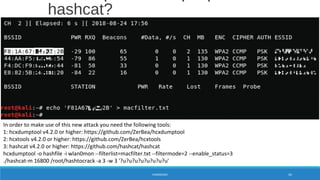
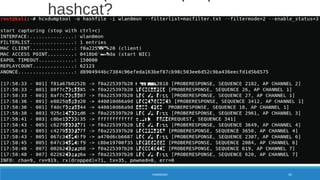

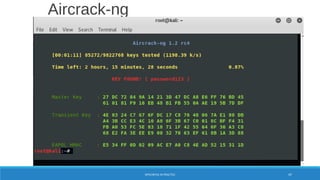
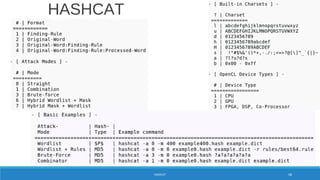
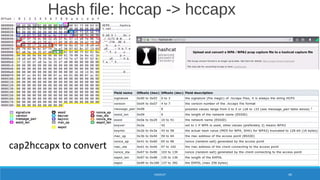

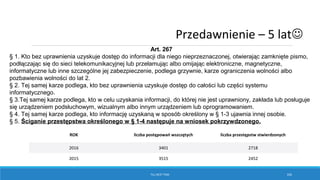
![X = Cn
Where:
X - Number of combinations
C - Number of characters in a charset
n - Password range (>=8)
Example:
8 char lowercase alpha
[a-z or (not and) A-Z] = 268
= 208827064576
Example for Radeon R9 270 OC (~98 kH/sek)
WPA/WPA2 Password Entropy
GPU 72
n Charset Time
Single R290 (~140 kH/s)
8 [0-9] = 10 12 minutes
8 [a-z] or [A-Z] = 26 17 days
8 [a-z + 0-9] or [A-Z + 0-9] = 36 233 days
9 [a-z] or [A-Z] = 26 1 year and 83 days
9 [a-z + 0-9] or [A-Z + 0-9] = 36 23 years
8 a-z + A-Z + 0-9 = 62 50 years
12 x R270 (12 x ~100 kH/s)
8 [a-z] or [A-Z] = 26 2 days
8 [a-z + 0-9] or [A-Z + 0-9] = 36 27 days
9 [a-z] or [A-Z] = 26 52 days
Single i5 CPU (~3,3 kH/s) depending on version
8 [a-z] or [A-Z] = 26 2 years and 1 month](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-72-320.jpg)
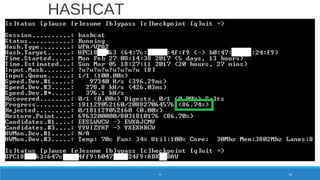
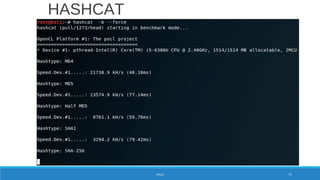
![8 char lowercase alpha
[a-z or (not and) A-Z] = 268
= 208827064576
WPA/WPA2 Password Entropy
PASSWORD 77](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-77-320.jpg)
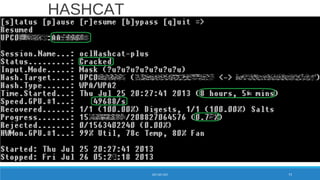
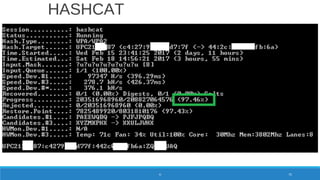
![8 char lowercase alpha
[a-z or (not and) A-Z] = 268
= 208827064576
WPA/WPA2 Password Entropy
PASSWORD 78](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-78-320.jpg)
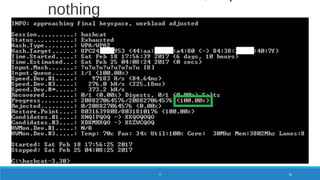
![8 char lowercase alpha
[a-z or (not and) A-Z] = 268
= 208827064576
WPA/WPA2 Password Entropy
PASSWORD 79](https://image.slidesharecdn.com/konradwifipracticalhackingdefcamp9d-190531064454/85/WiFi-practical-hacking-Show-me-the-passwords-79-320.jpg)