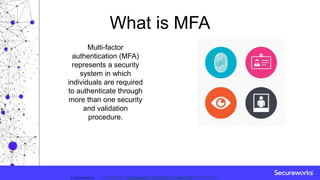
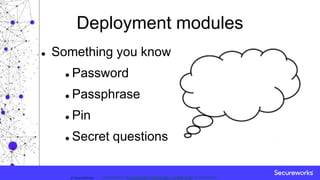
This document discusses multi-factor authentication (MFA) and methods for bypassing it. It defines MFA as requiring more than one validation procedure to authenticate individuals. It describes the different factors of authentication as something you know, something you have, and something you are. It outlines various deployment modules for each factor type, including passwords, tokens, biometrics. It also covers challenges of MFA implementation and methods attackers could use to bypass MFA security, such as email filtering or legacy protocol exploitation.











![Classification: //Secureworks/Public Use:© SecureWorks, Classification: //Secureworks/Confidential - Limited External Distribution:
Bypassing SPAM filters
Most popular enterprise email solution
Outlook/Office365
Moving from an “on-prem” exchange to a hybrid or
full cloud model
test@[domain].com vs test@[domain.]onmicrosft.com](https://image.slidesharecdn.com/nenciumirceastefanmitroi-190531064512/85/Trust-but-verify-Bypassing-MFA-16-320.jpg)



