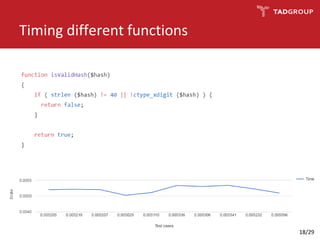
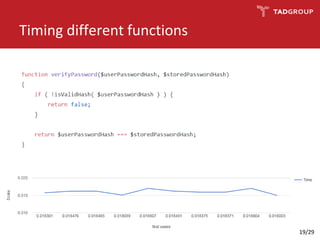
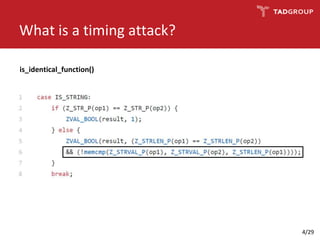
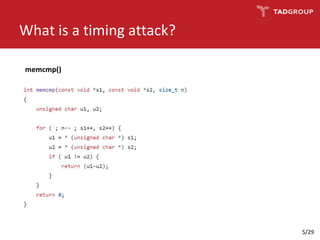
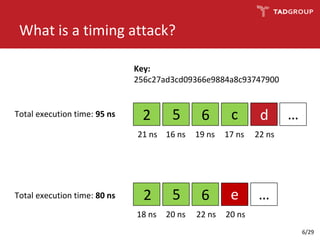
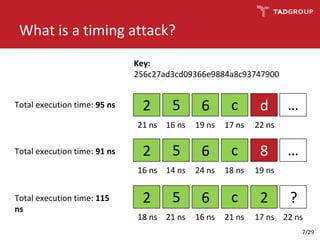
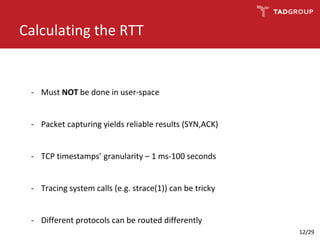
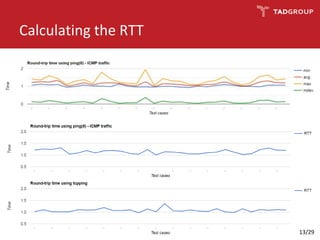
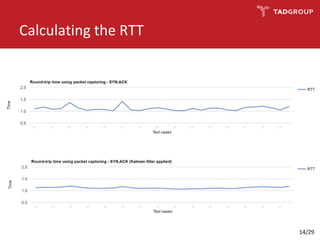
This document discusses the practicality of timing attacks against web applications. It begins by explaining what a timing attack is and detailing the author's plan to conduct one against a target application. The plan involved studying the application's code, pinpointing an exploitable function, collecting timing data, filtering noise, and reducing the search space. The author was able to measure response times and identify spikes but encountered challenges averaging server performance. They demonstrate conducting a timing attack to recover hashed credentials over many requests. Ultimately, while timing attacks can be efficient, they are difficult to execute remotely and most applications and servers have protections that render the attacks impractical. Constant-time algorithms and rate limiting are presented as solutions to prevent these types of attacks.

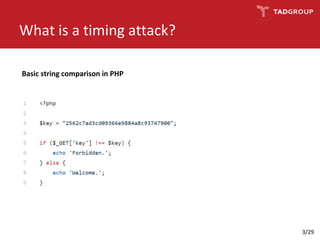



![Calculating server response time
0.000978360
X.X.X.X → Y.Y.Y.Y HTTP 146 GET / HTTP/1.1
0.001722918
Y.Y.Y.Y → X.X.X.X TCP 66 80 → 33930 [ACK] Seq=1 Ack=81 Win=29056 Len=0
TSval=1737072019 TSecr=3816704019
0.004035262
Y.Y.Y.Y → X.X.X.X HTTP 481 HTTP/1.1 301 Moved Permanently (text/html)
Packet capturing with tshark(1)
15/29](https://image.slidesharecdn.com/ivanpetrovtadgroup-190531064505/85/Timing-attacks-against-web-applications-Are-they-still-practical-15-320.jpg)