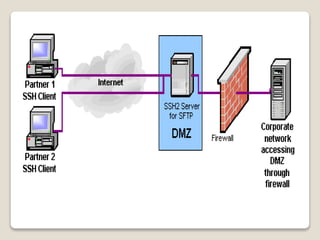
SSH is a protocol for secure remote access and file transfer that replaces insecure protocols like telnet. It uses encryption and authentication to securely transmit data, remote shell access, port forwarding, and file transfers between a client and server. Reasons to use SSH include enabling secure communication channels, arbitrary port redirection, optional compression, and protecting against spoofing and routing attacks.