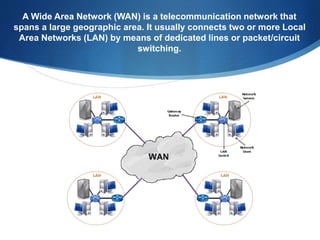
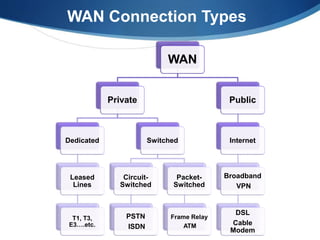
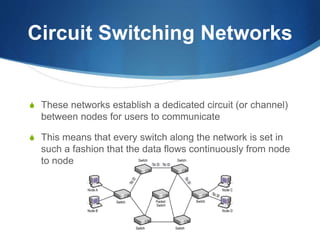
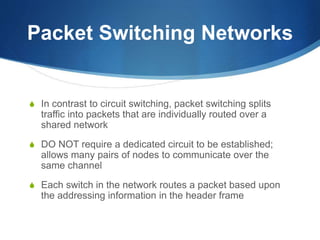
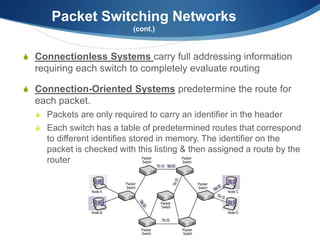
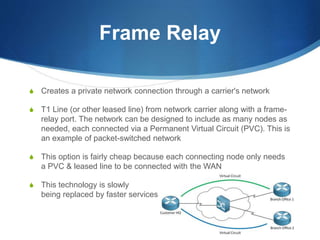
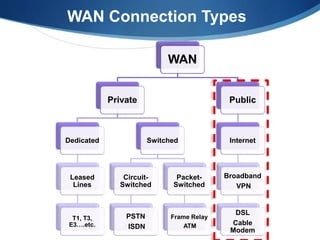
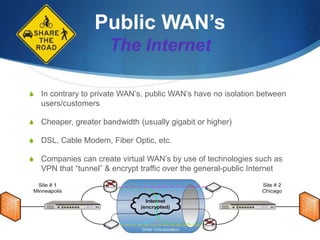
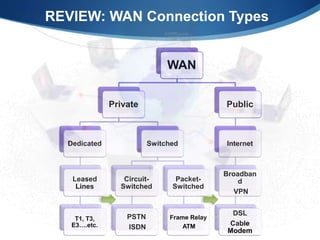
A Wide Area Network (WAN) spans large geographic areas, connecting multiple Local Area Networks (LANs) via dedicated lines or packet switching. WANs are used for various applications, including voice, video, and data transmission, and can utilize different connection types like leased lines, circuit-switched, and packet-switched networks. Public WANs, such as the internet, offer lower costs and higher bandwidth but lack isolation compared to private WANs, with trends indicating a shift to cloud computing solutions.