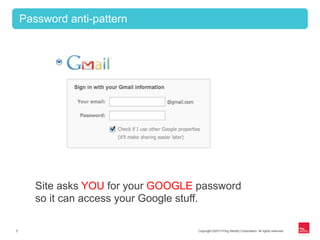
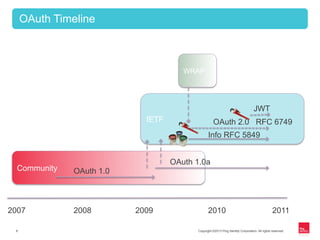
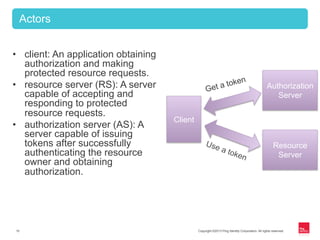
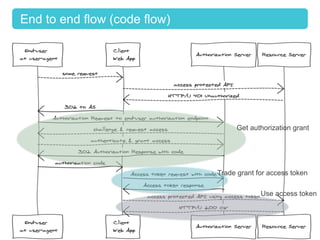
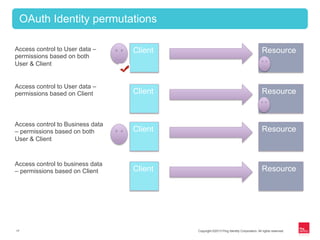
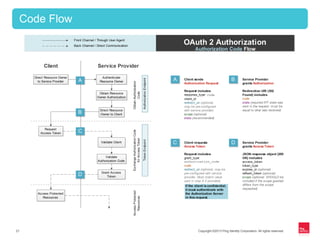
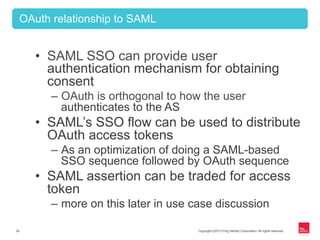
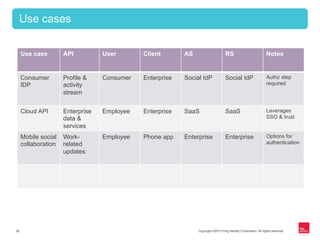
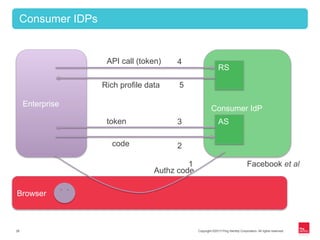
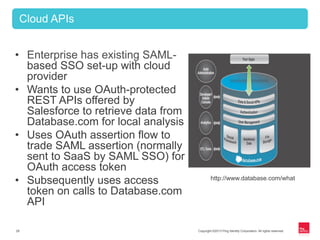
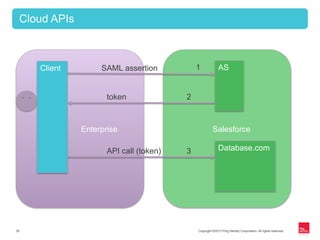
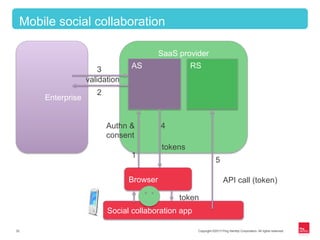
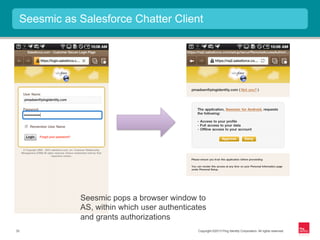
This document provides an overview of OAuth 2.0 and how it addresses issues with the previous "password anti-pattern" approach to API authentication. It describes the key actors in OAuth - clients, authorization servers, and resource servers. It also summarizes the different flows for obtaining access tokens, common use cases for OAuth, and how OAuth compares to SAML for SSO and authorization.