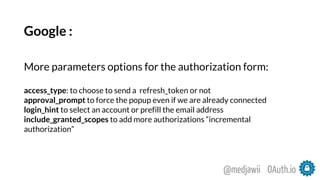
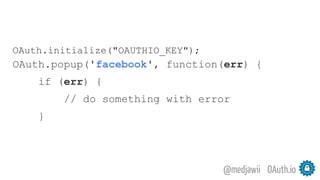
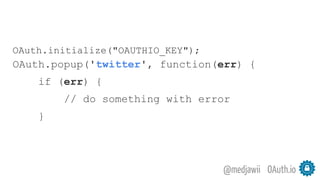
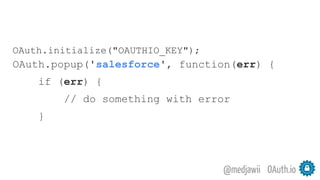
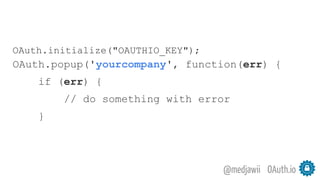
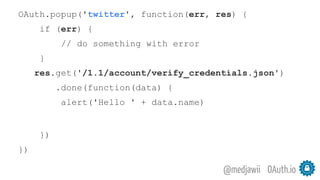
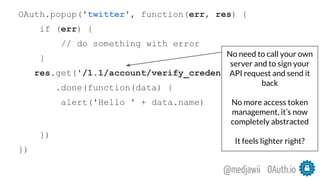
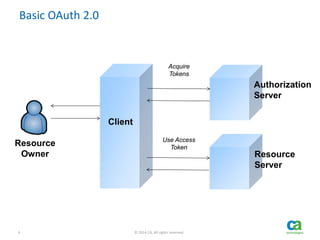
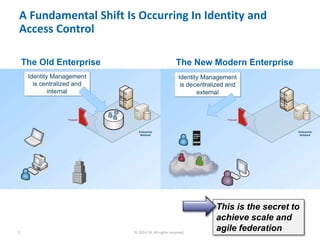
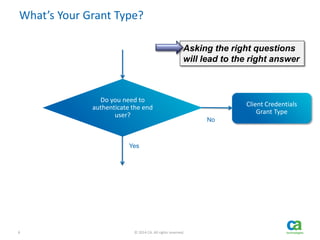
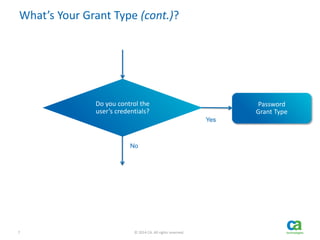
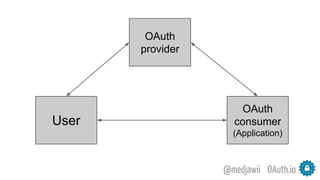
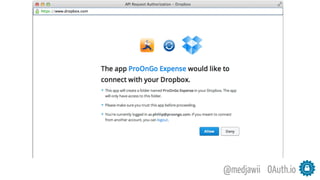
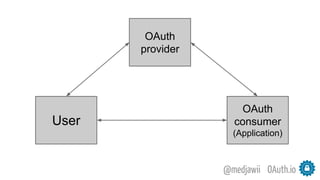
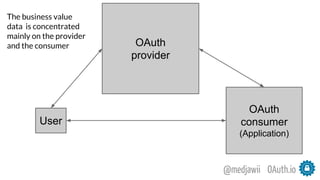
The document discusses OAuth's significance in modern security architecture, emphasizing its evolution from OAuth 1.0 to 2.0, alongside the various grant types and token management strategies. It highlights challenges around scalability, token revocation, and proper placement of tokens within secure environments, as well as the importance of scopes and consent in the authorization flow. With practical examples and recommendations, the presentation aims to clarify misconceptions and promote effective usage of OAuth in integrating identity and access control.















![Deezer
client_id -> app_id=...
scope -> perms=email,read_friendlists...
state=... [non documented]
response_type=code [useless]
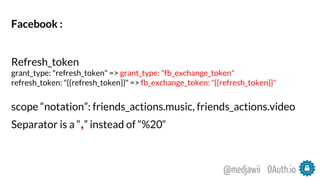
“Facebook is the standard”
OAuth.io@medjawii](https://image.slidesharecdn.com/oauthintherealworldcalayer7webshell-140403120014-phpapp02/85/OAuth-in-the-Real-World-featuring-Webshell-37-320.jpg)