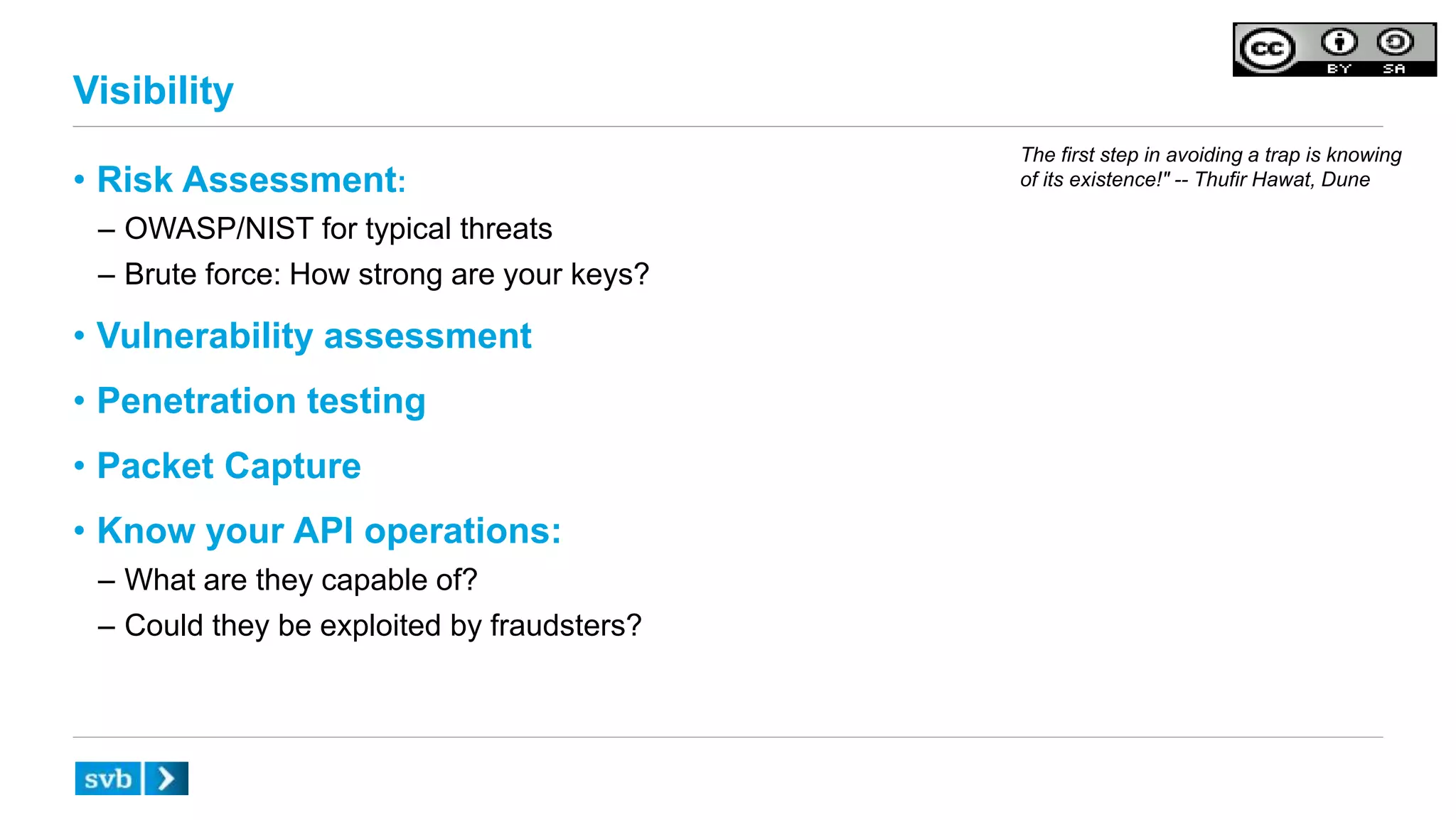
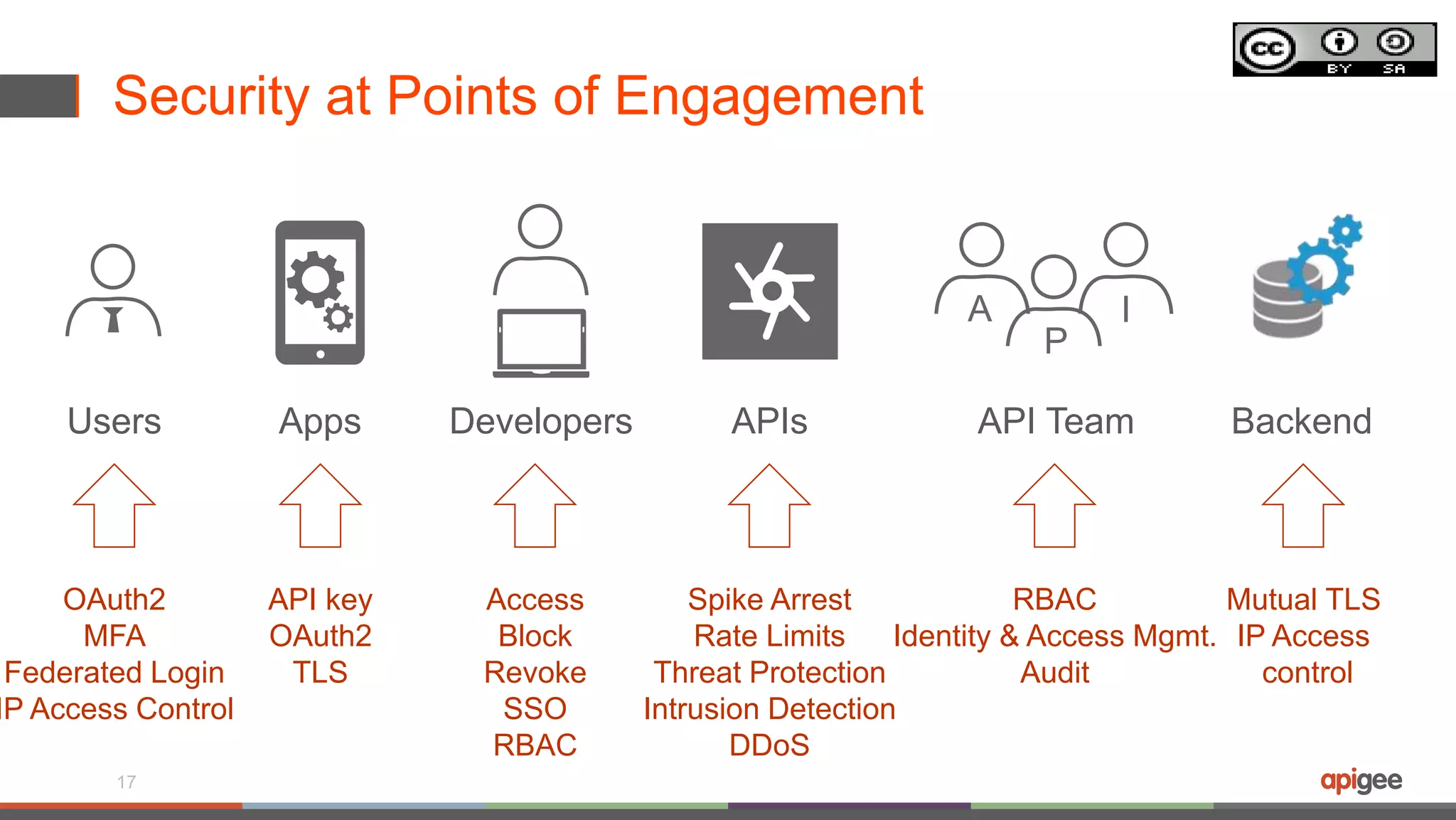
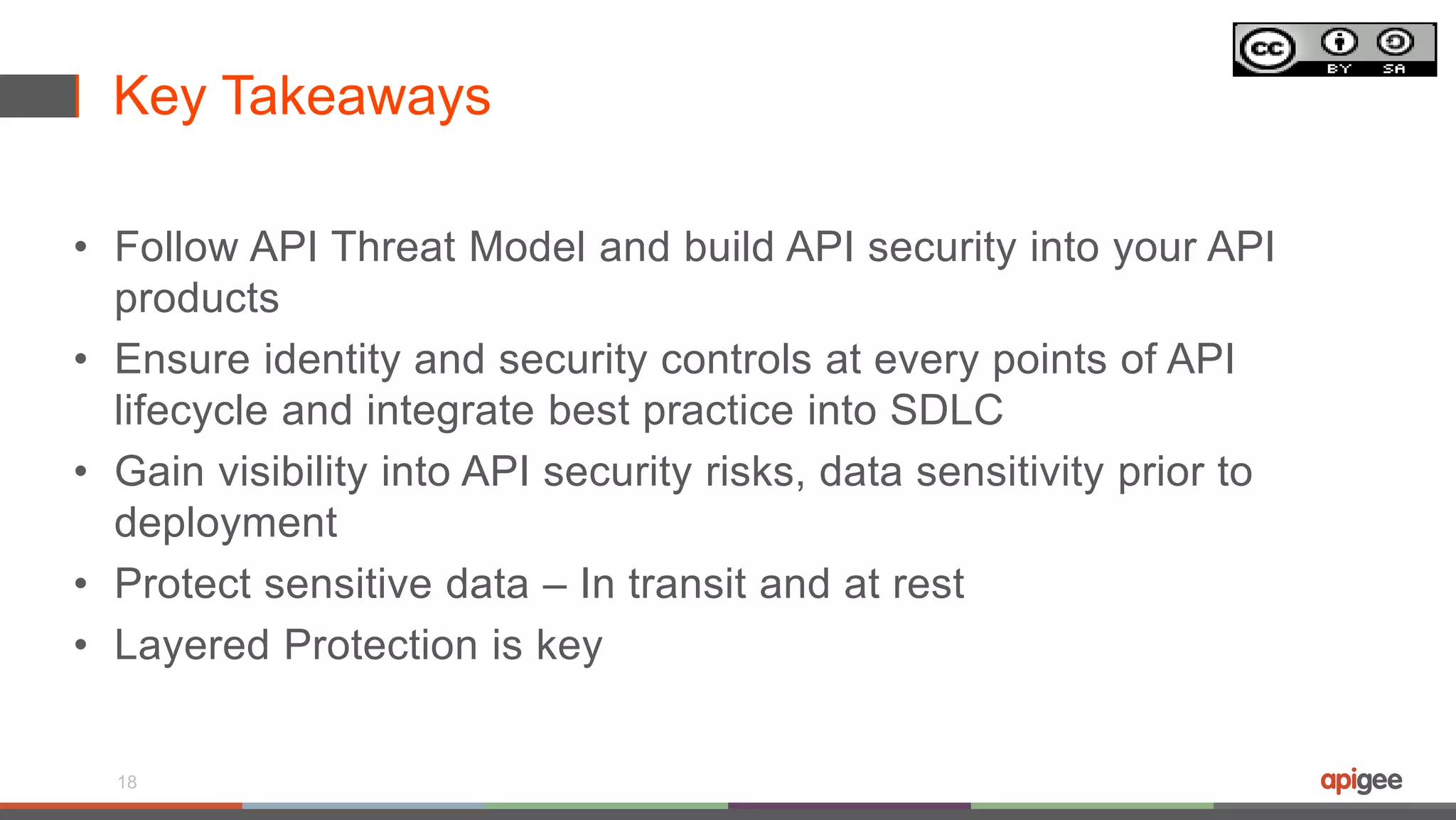
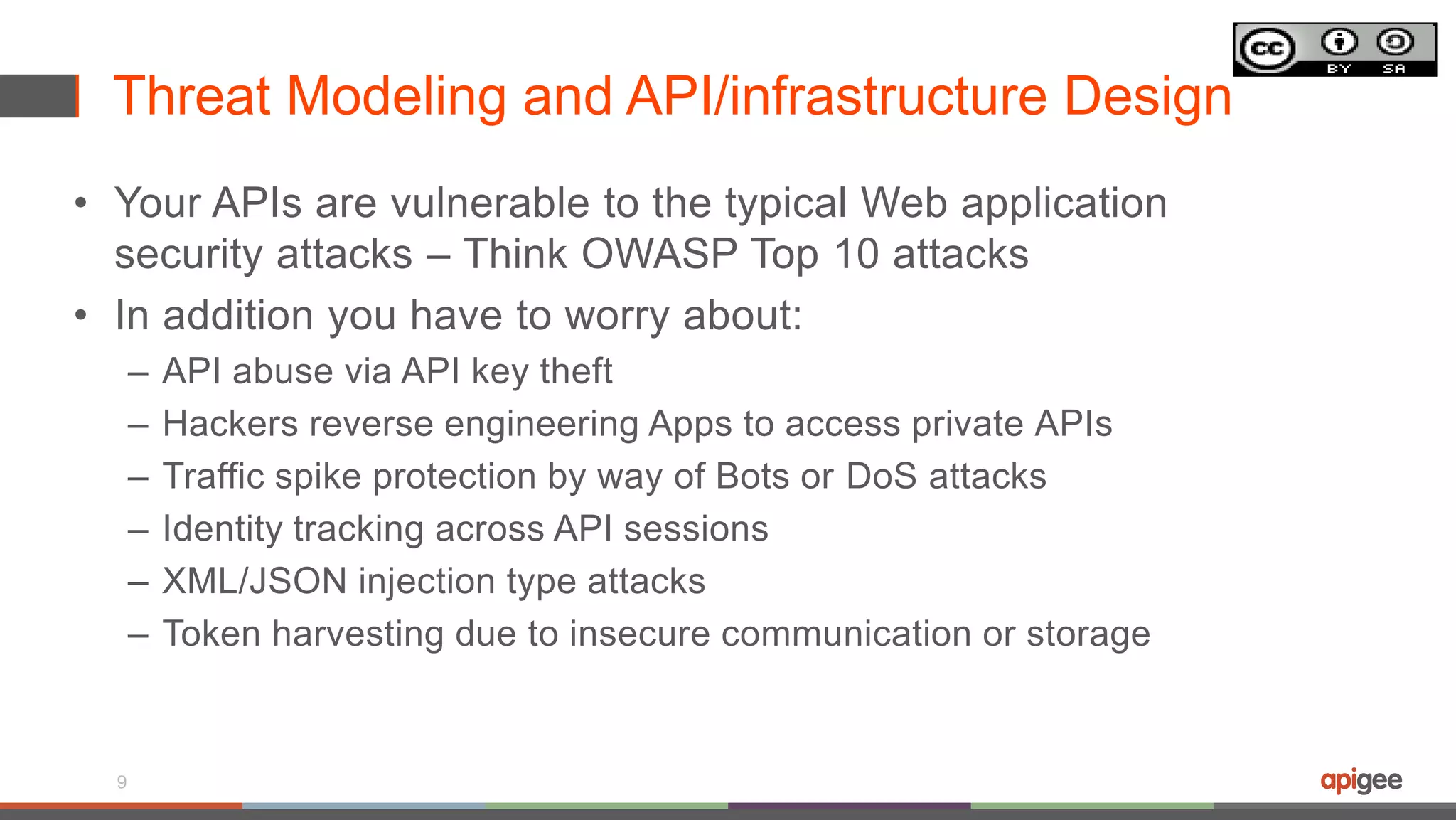
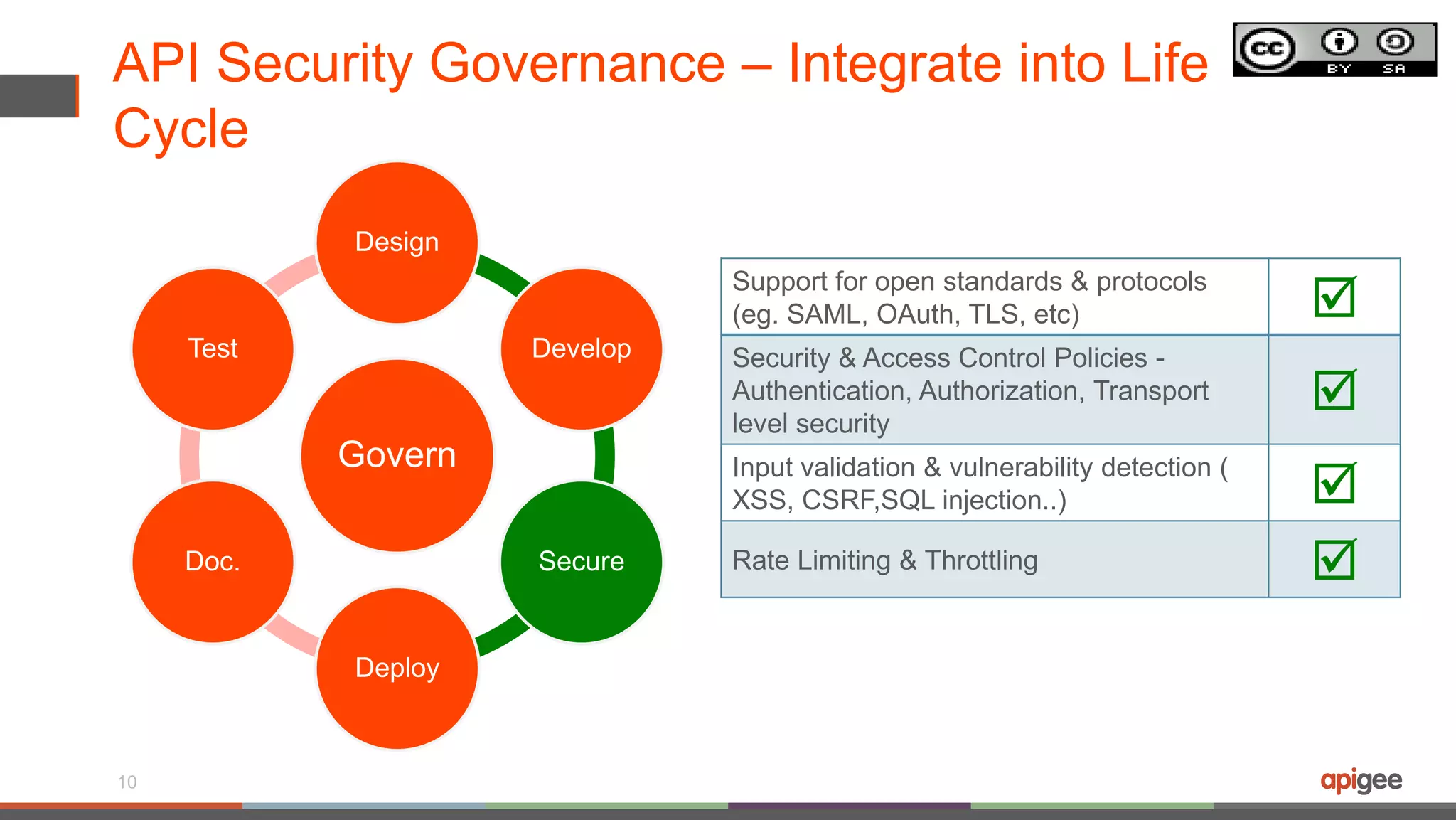
The document discusses API security in the context of regulated financial services, highlighting the importance of integrating security throughout the API lifecycle, from design to deployment. It addresses various threats faced by APIs, including typical web application attacks and specific vulnerabilities such as API key theft and traffic spikes from DDoS attacks. Key takeaways emphasize the need for layered protection, visibility into data sensitivity, and compliance with industry standards.

![Launching an API Platform for a regulated
company
{
“Jason Kobus”: {
“role”: “Director API Banking / Fintech Integration”,
“company”: “Silicon Valley Bank”,
“credentials”: {“current”: [“CSPO”, “CISSP”, “CISA”]}, {“former”: [“CIA”, “CISM”, “CIPP, “Series 7”, “PMP”, “ISO 27001 LI”]},
“mission”: “Deliver secure financial APIs to make clients happy and extend reach / increase revenue”
}
}
September 29, 2015
DISCLAIMER: The content on this site, and comments made during the presentation, are my own and don't necessarily represent the positions,
strategies, or opinions of Silicon Valley Bank.](https://image.slidesharecdn.com/deep-dive-security-in-digital-age-92915-151007205313-lva1-app6892/75/Deep-Dive-API-Security-in-the-Digital-Age-11-2048.jpg)