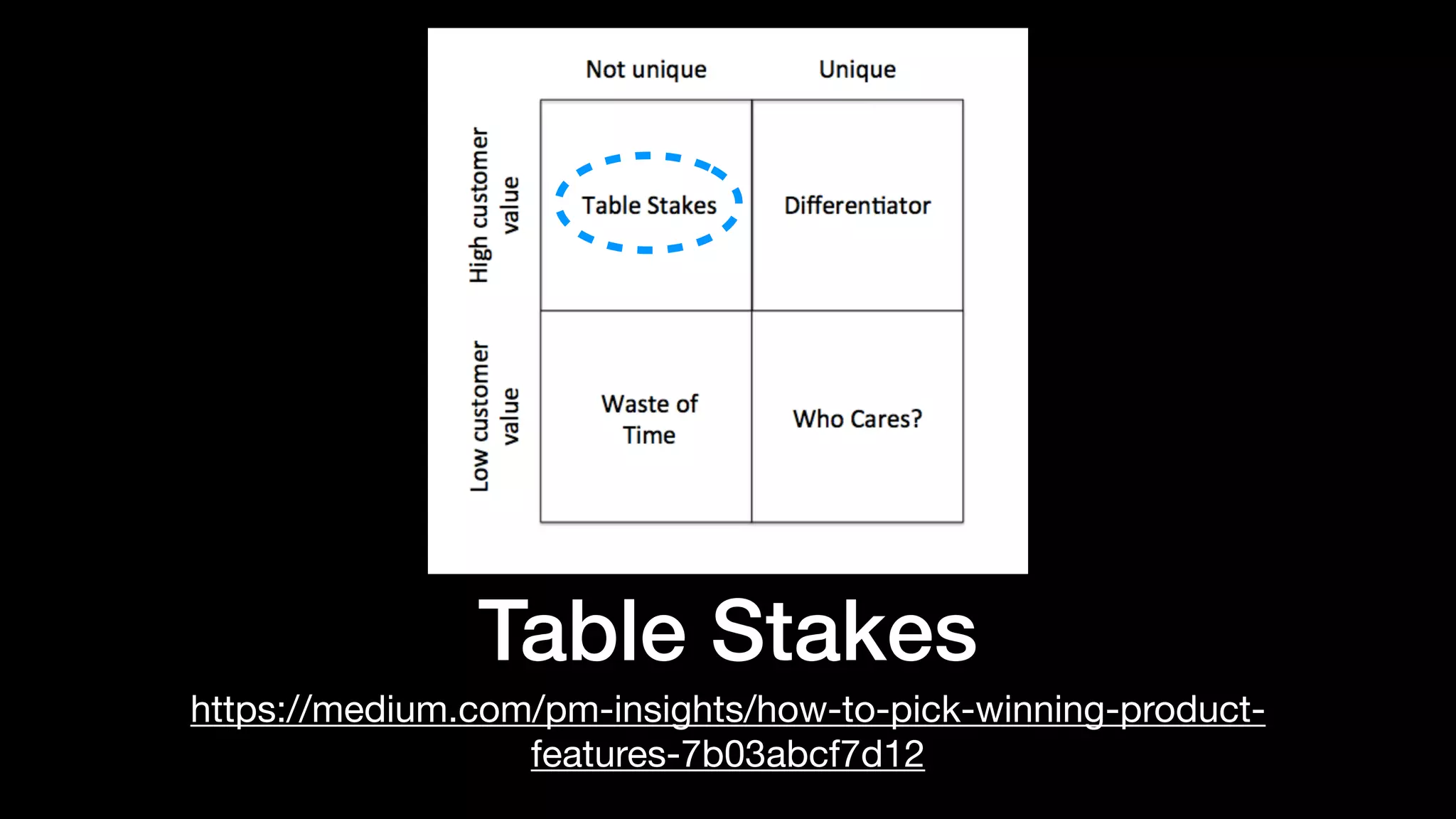
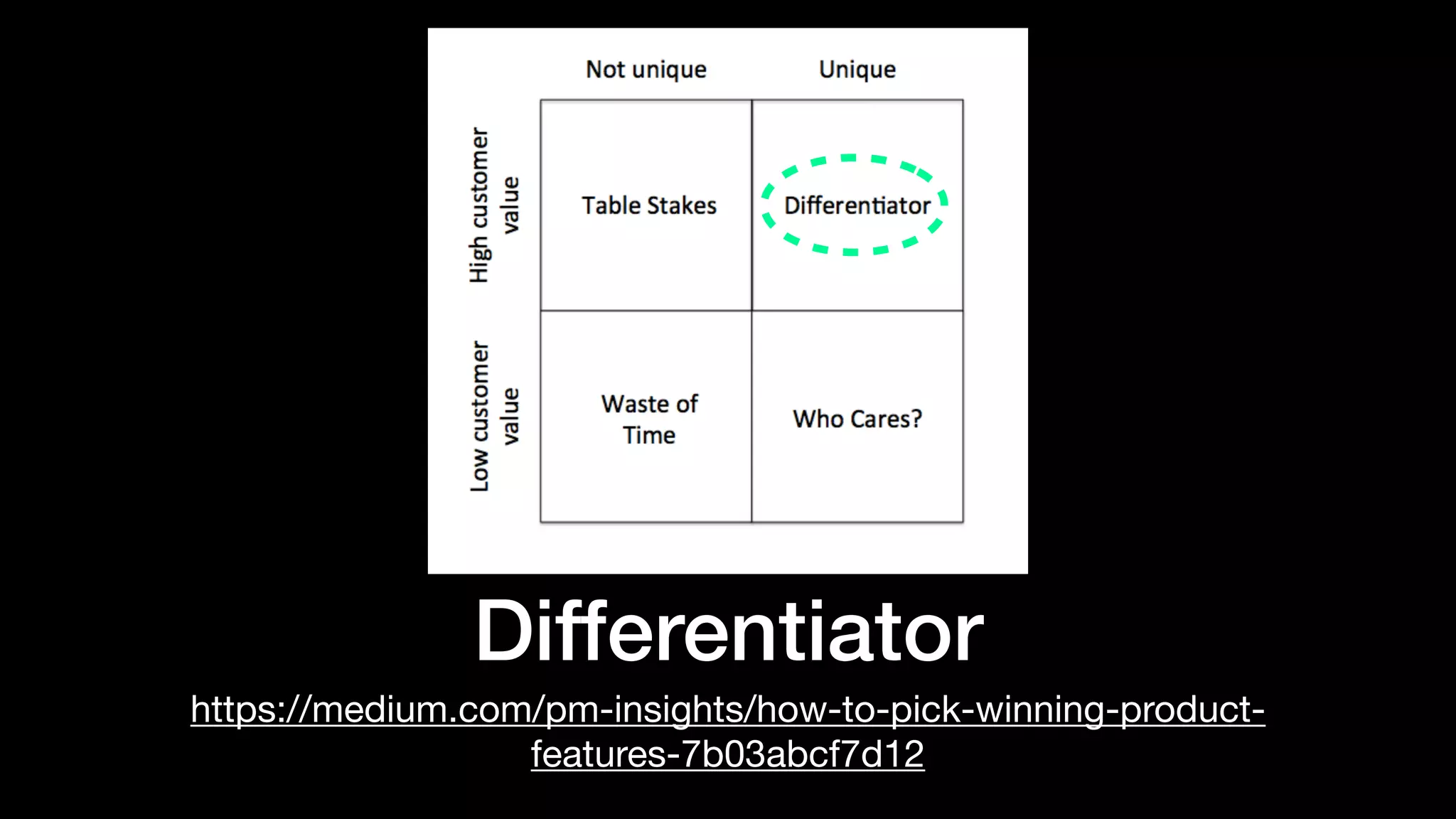
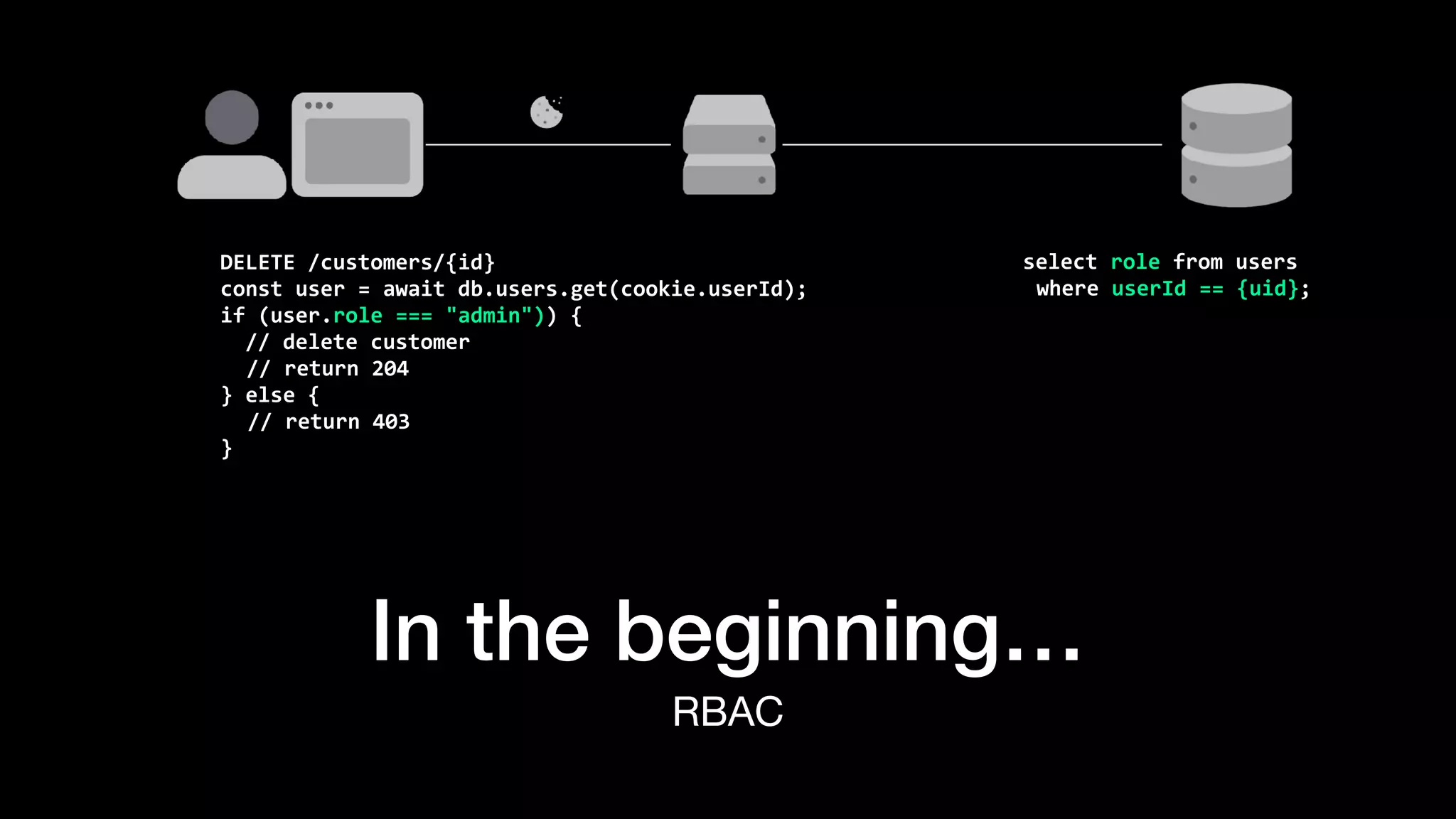
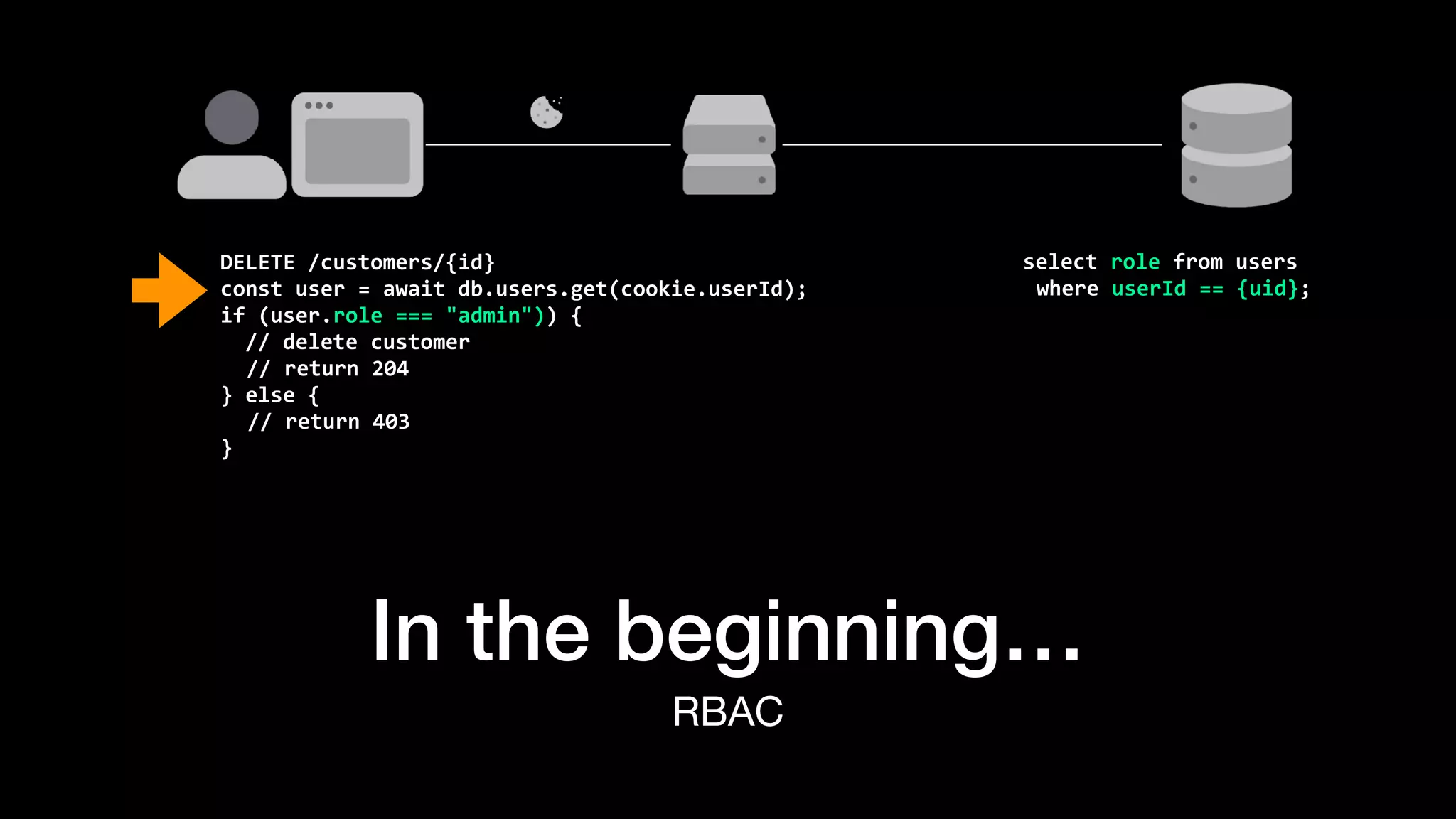
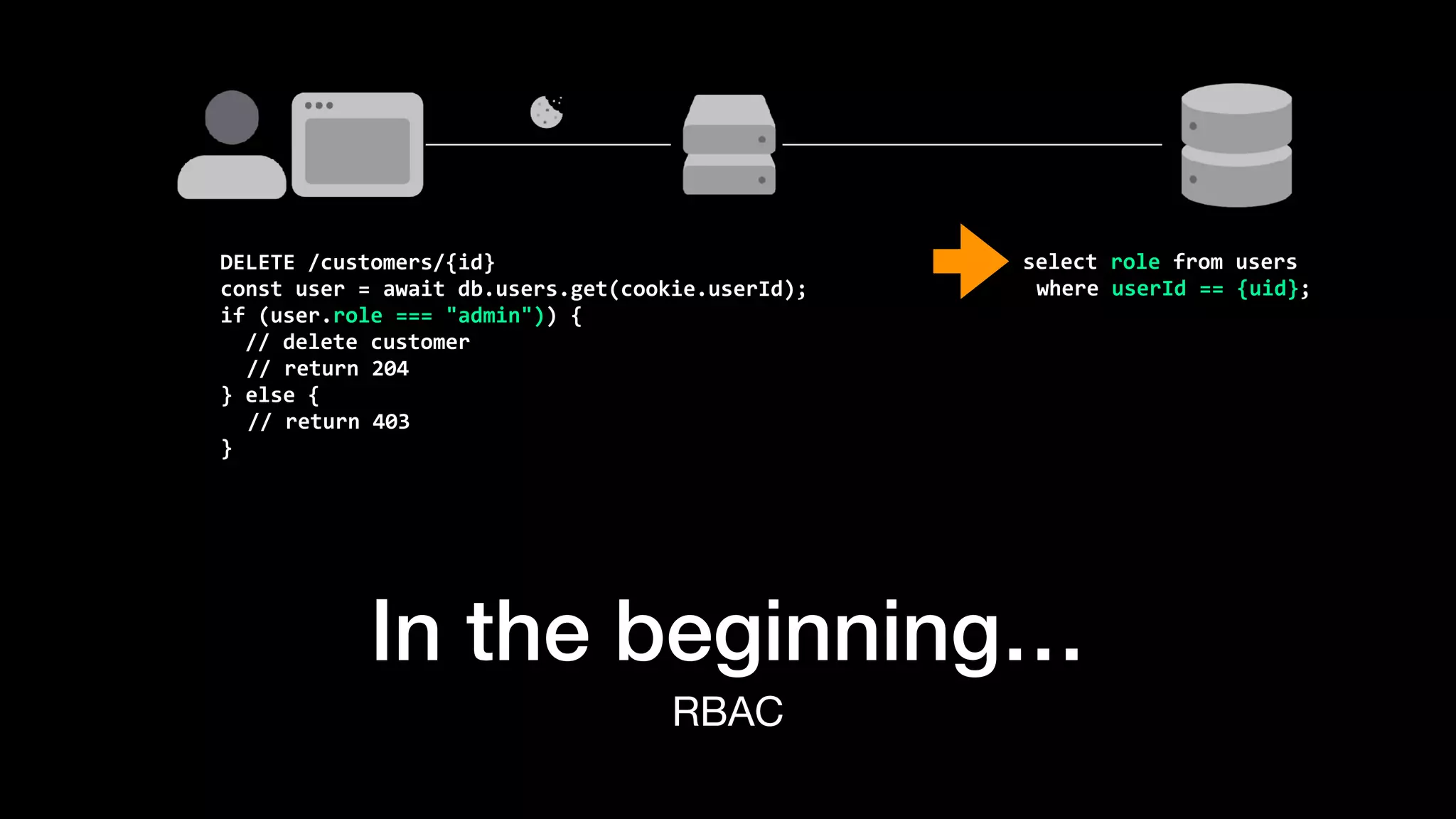
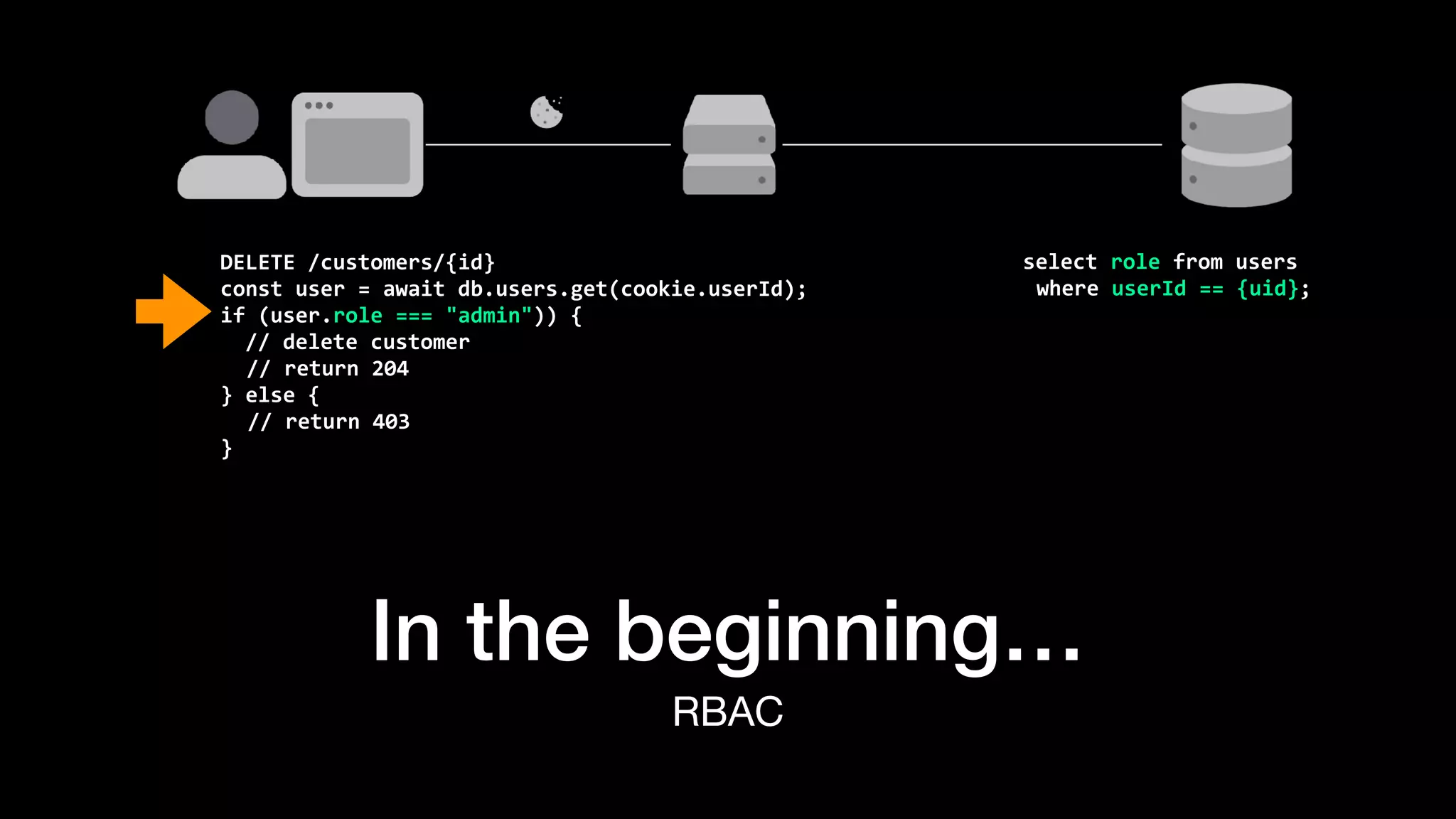
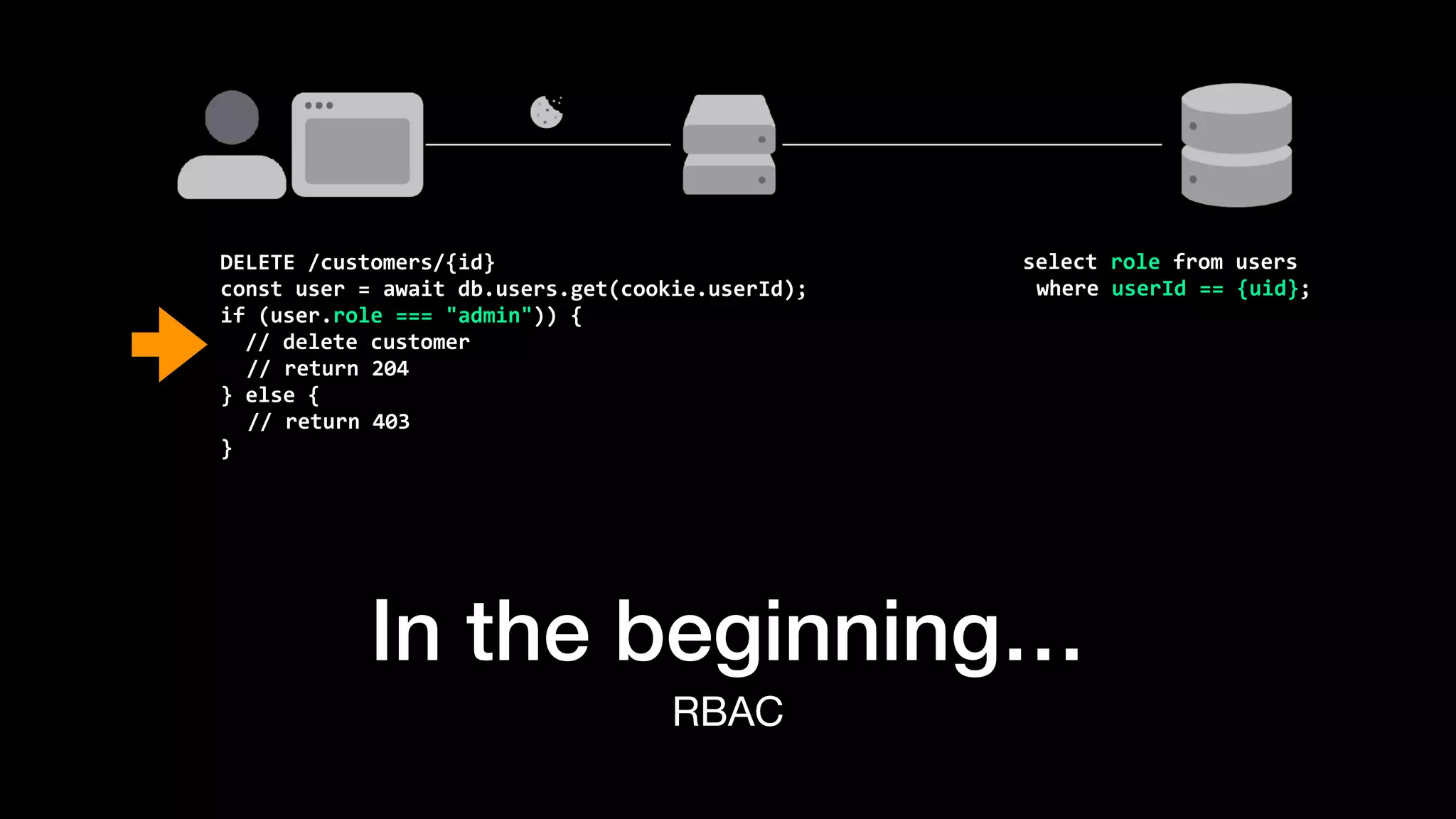
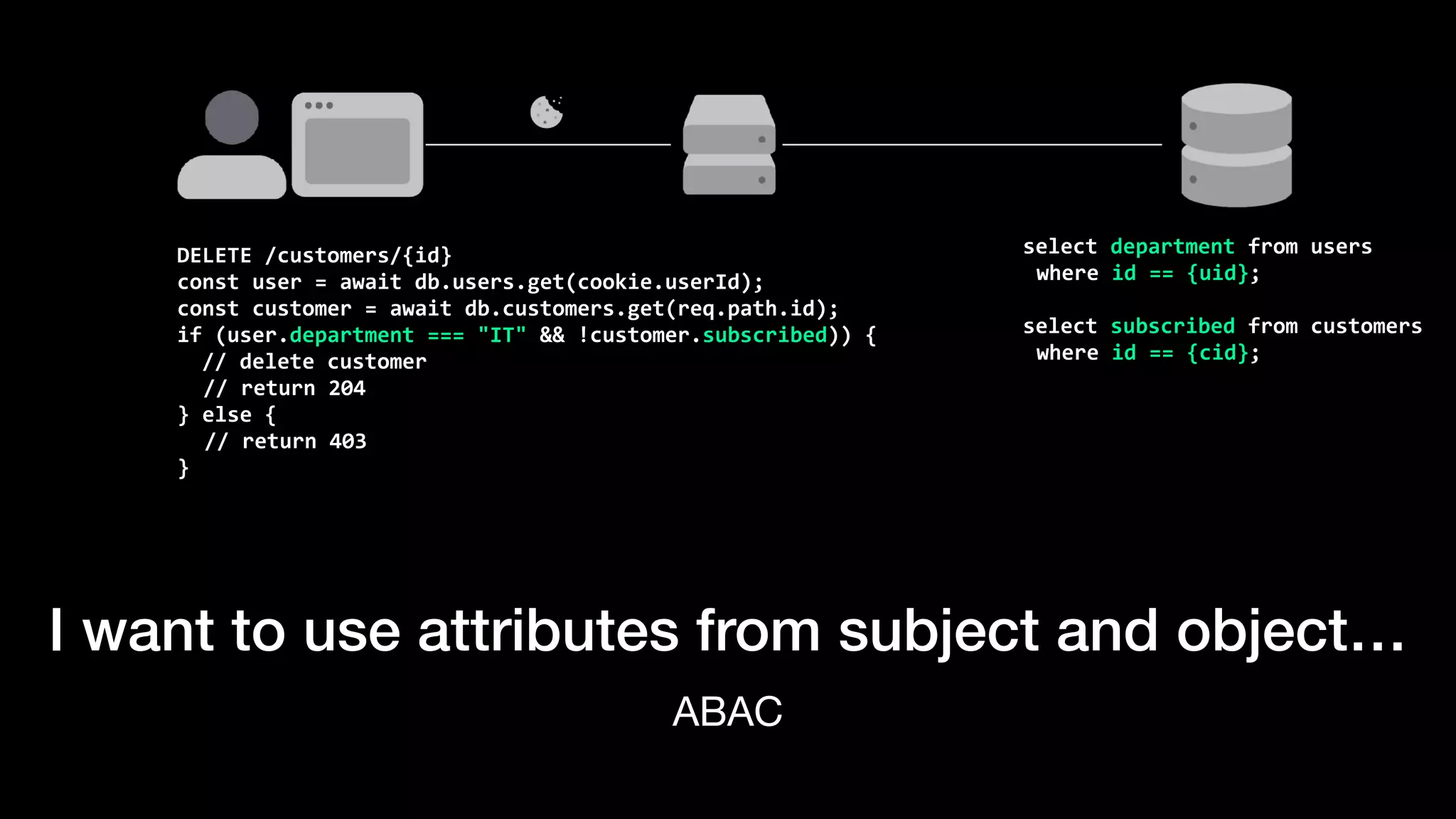
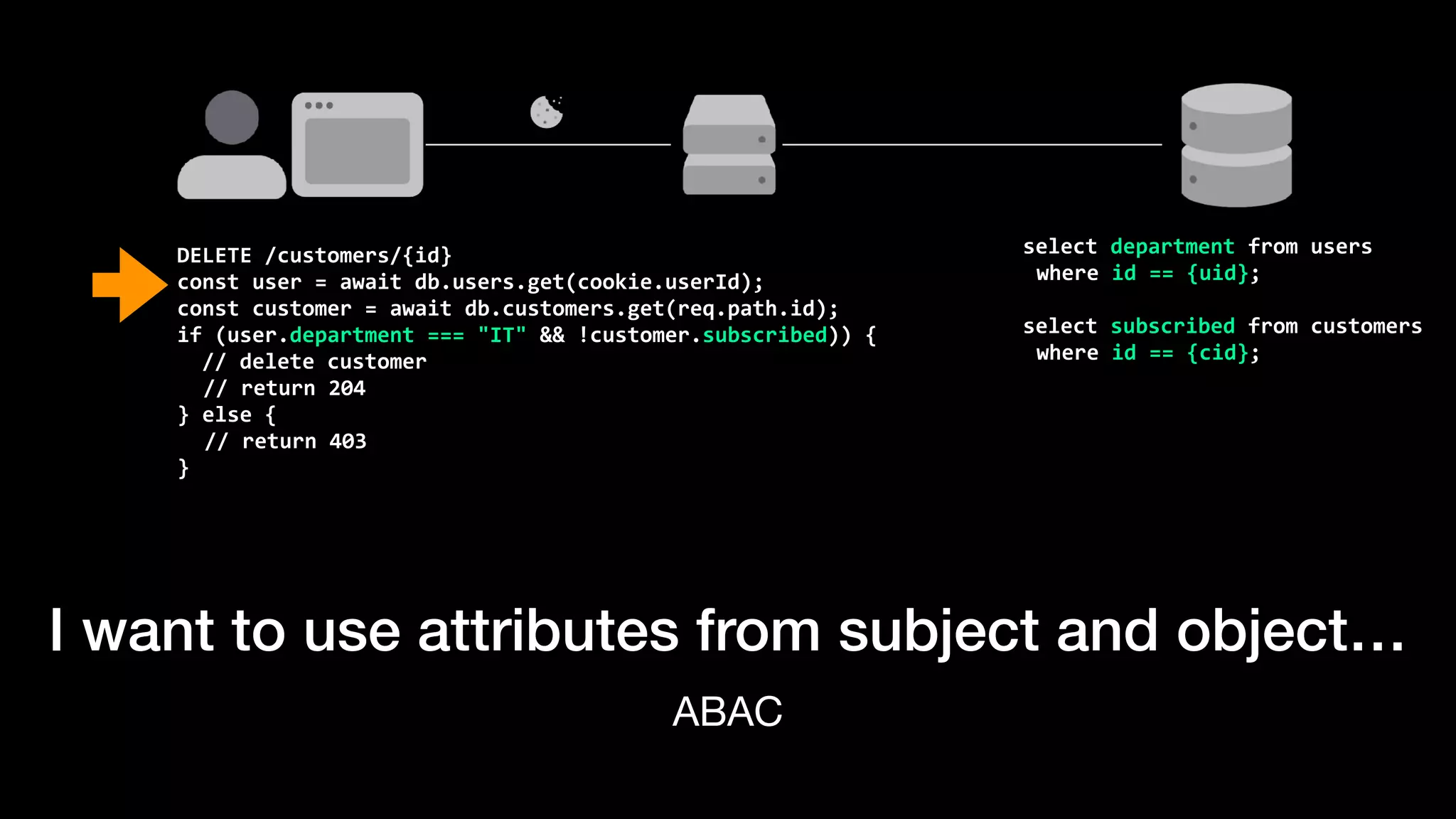
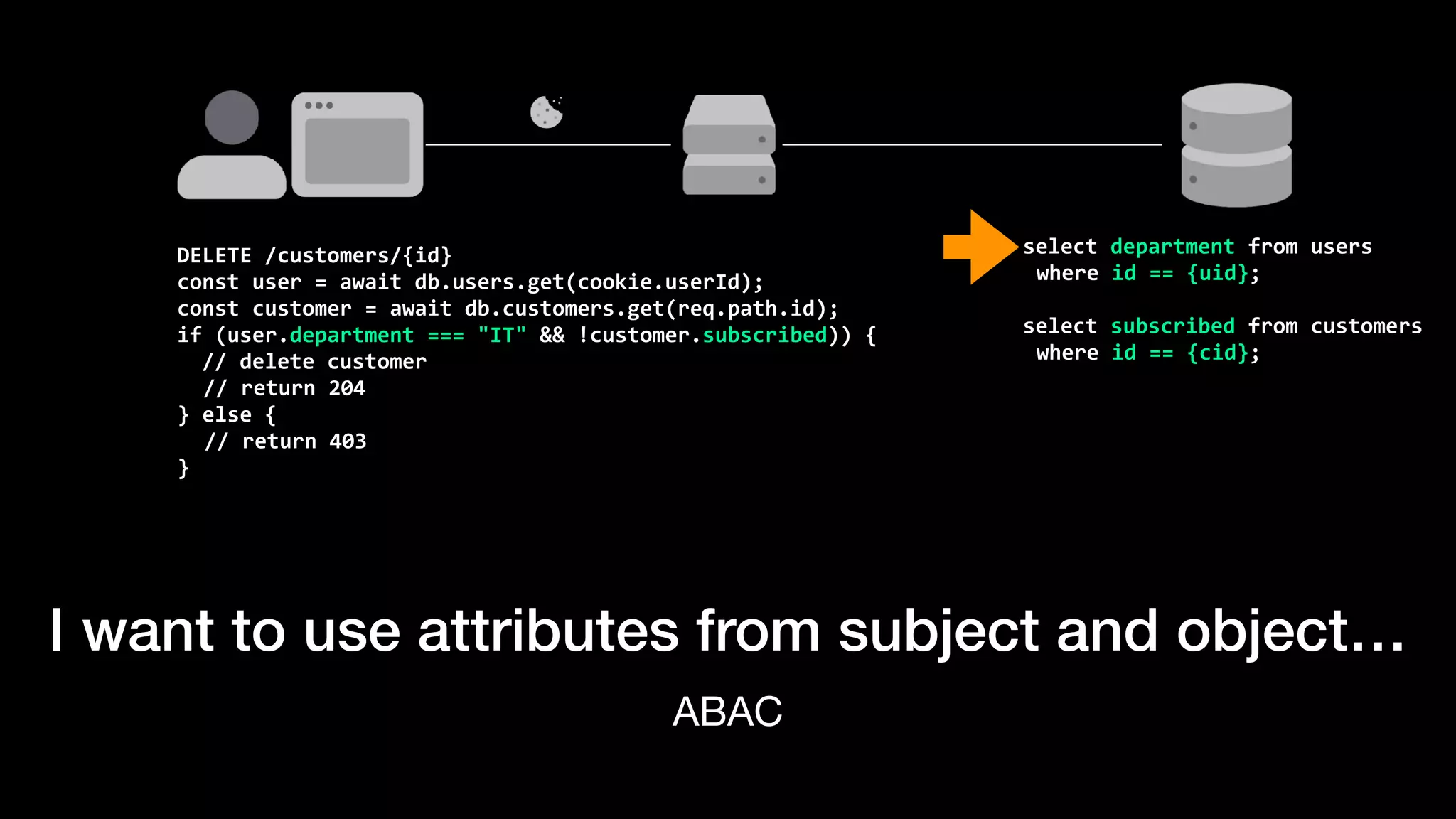
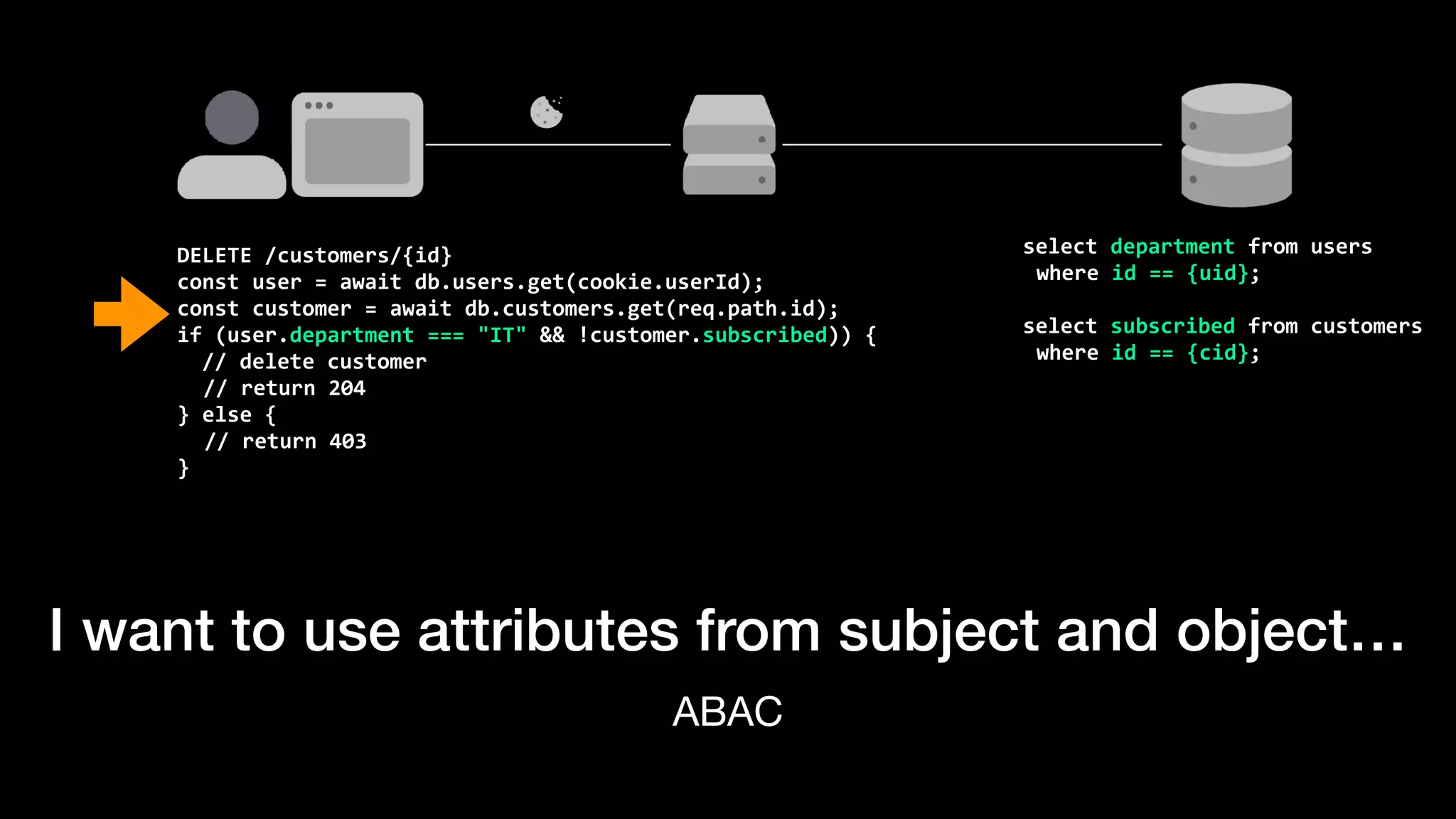
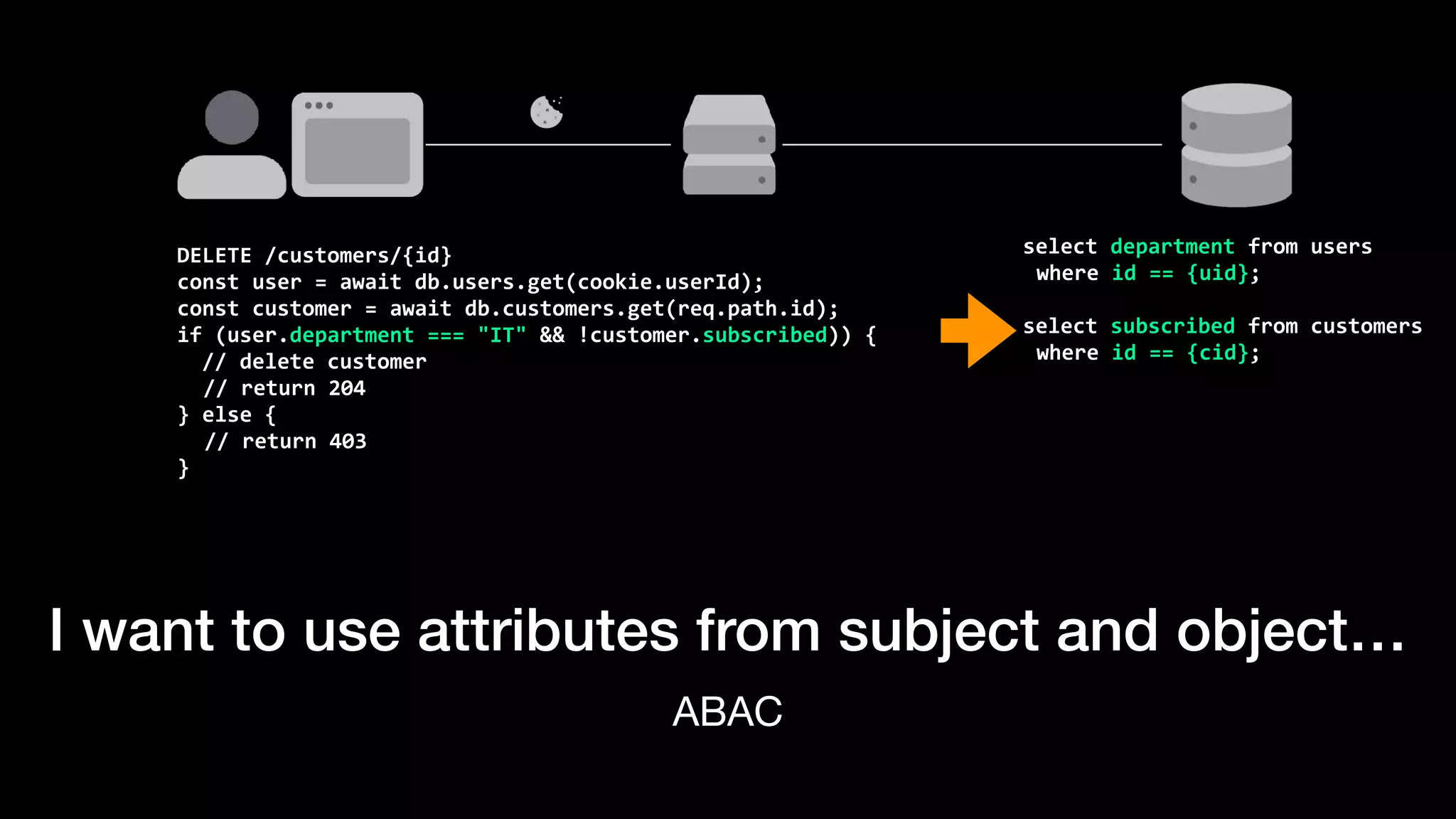
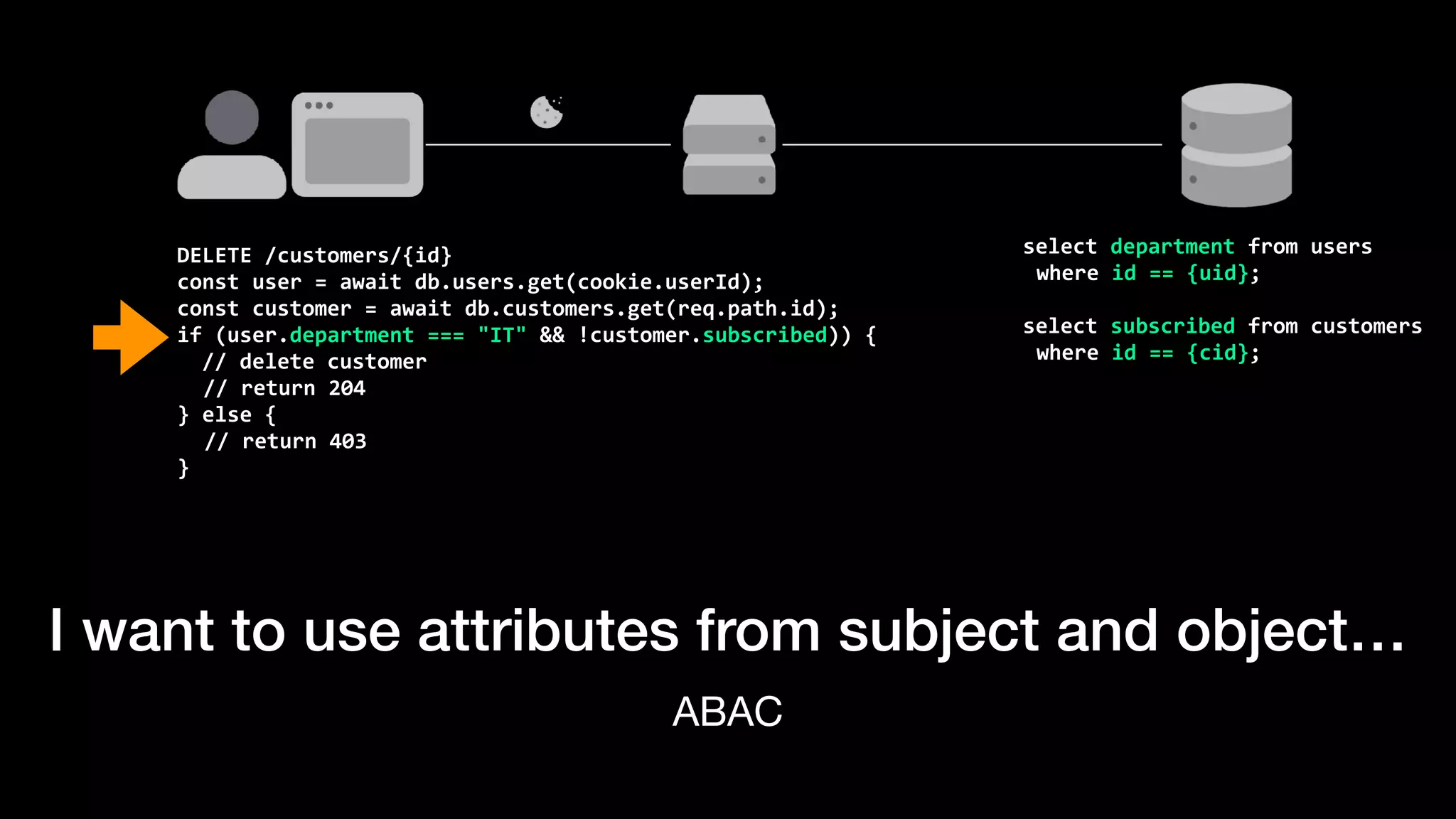
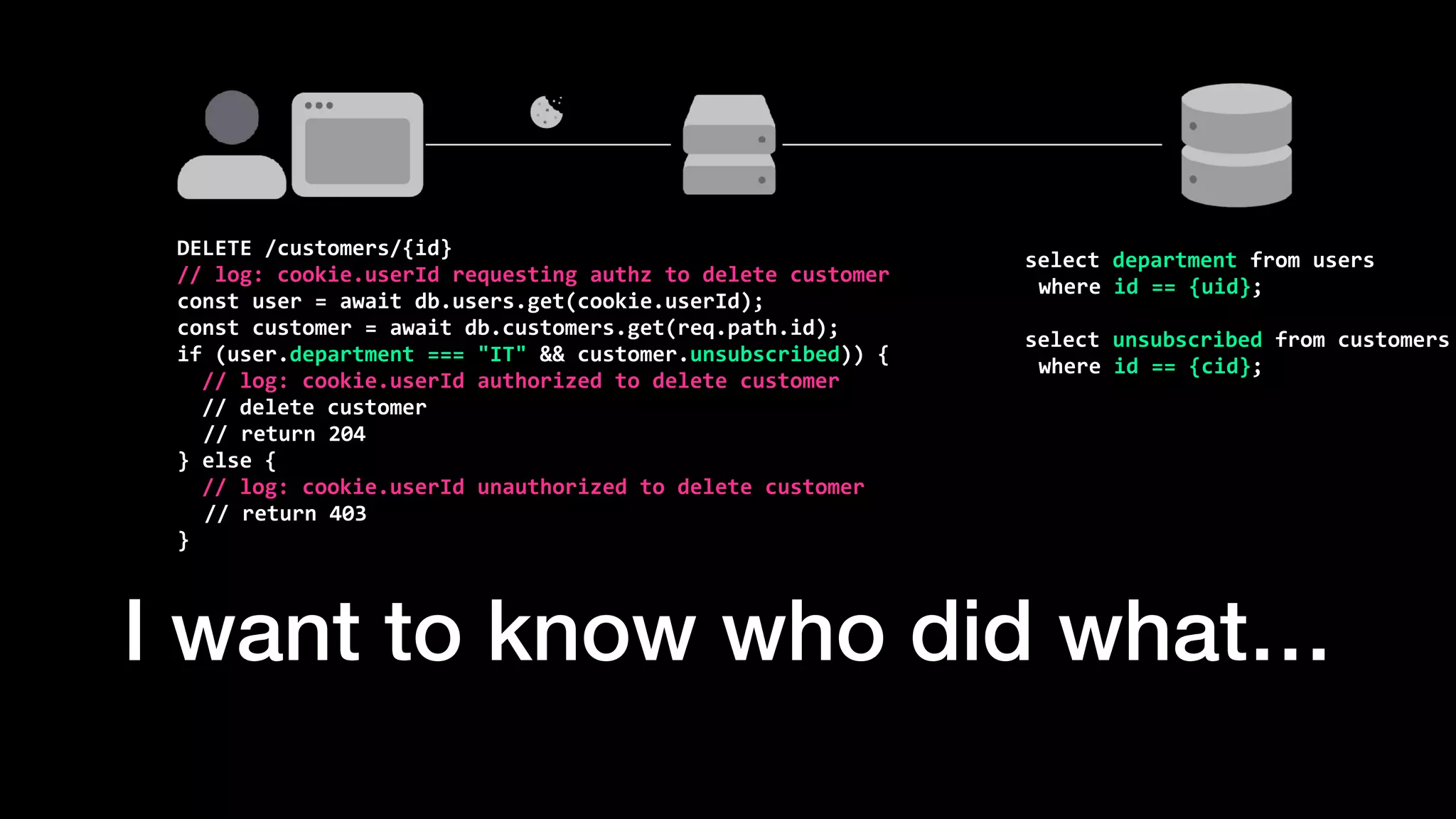
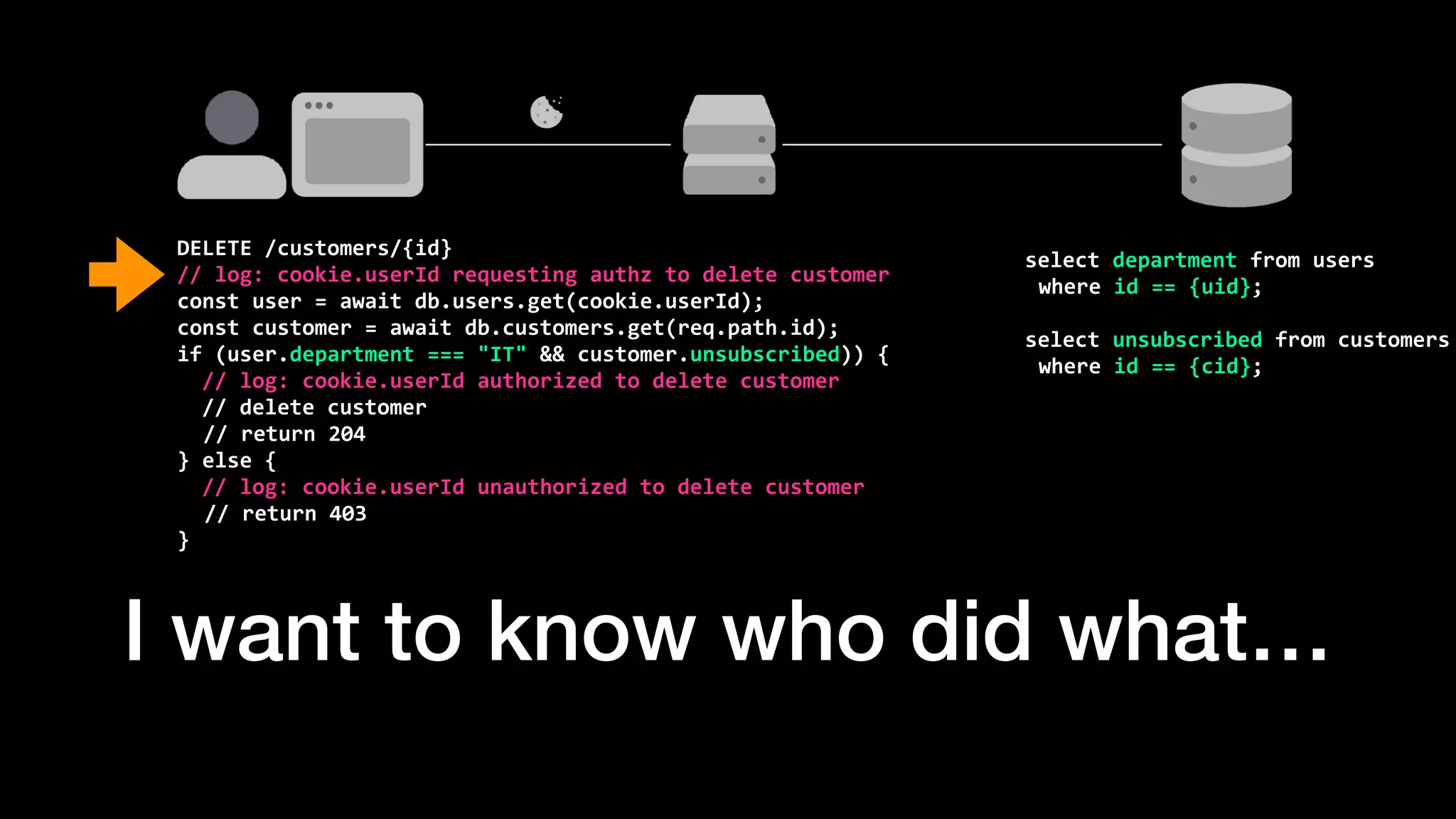
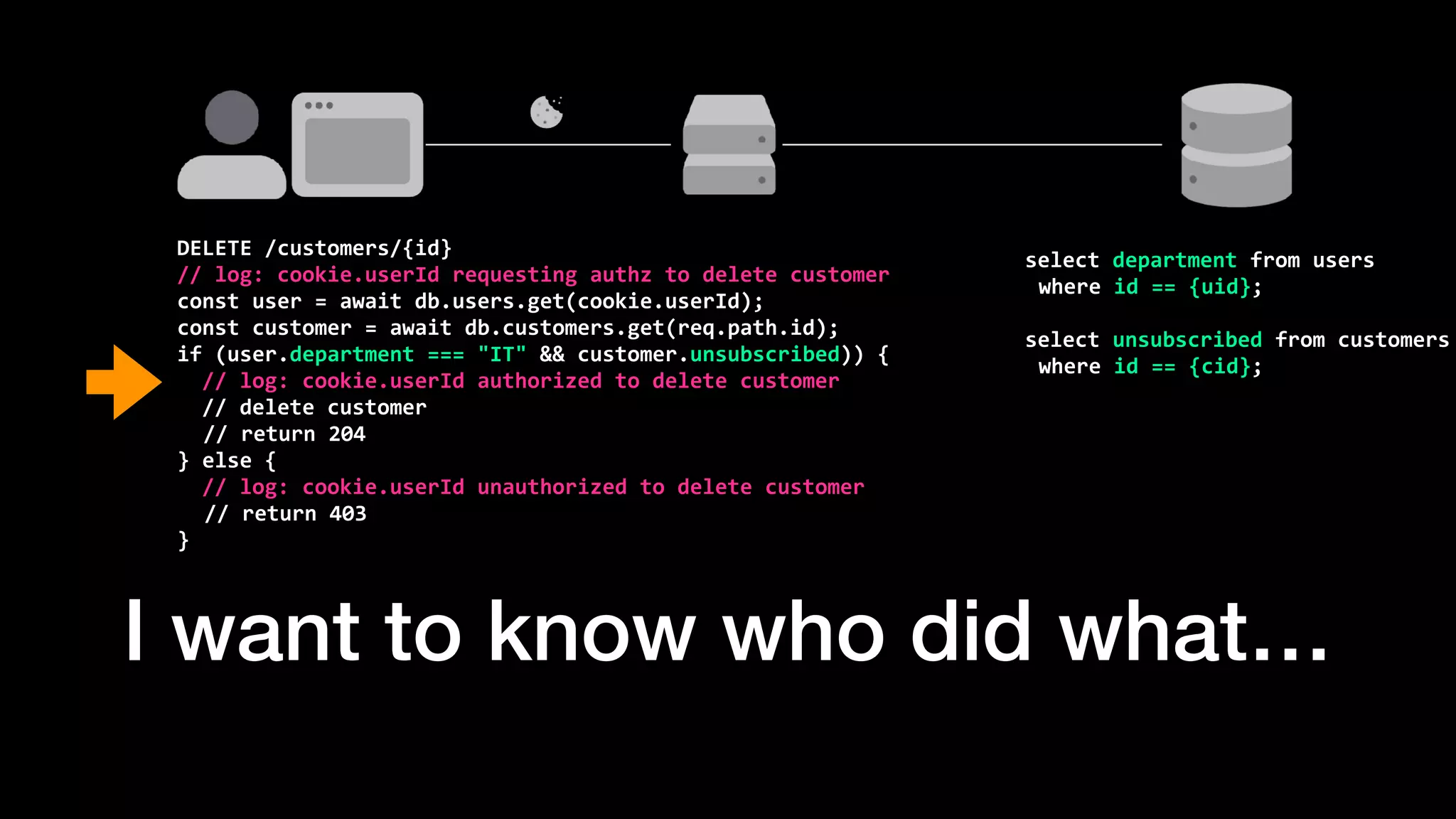
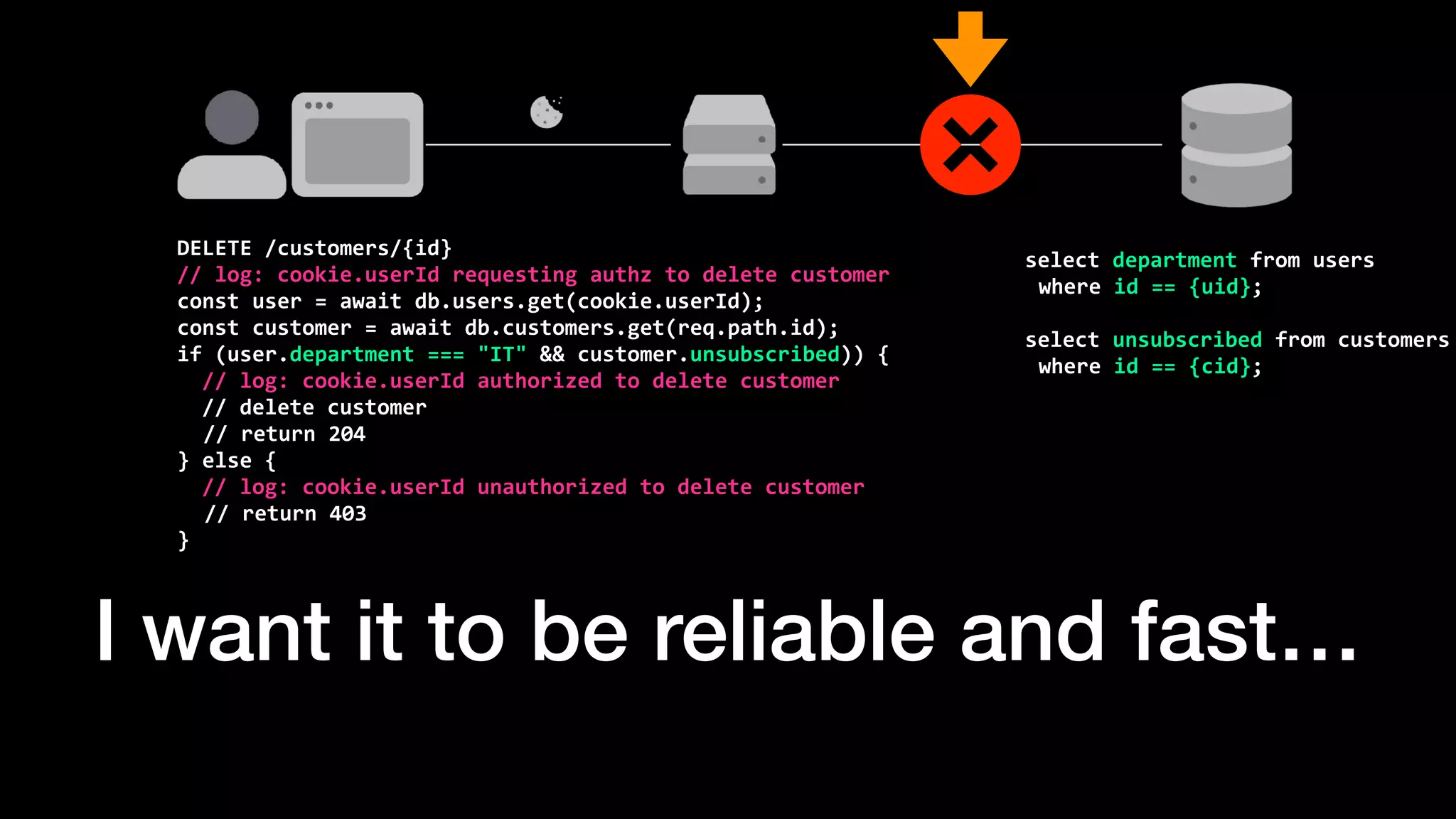
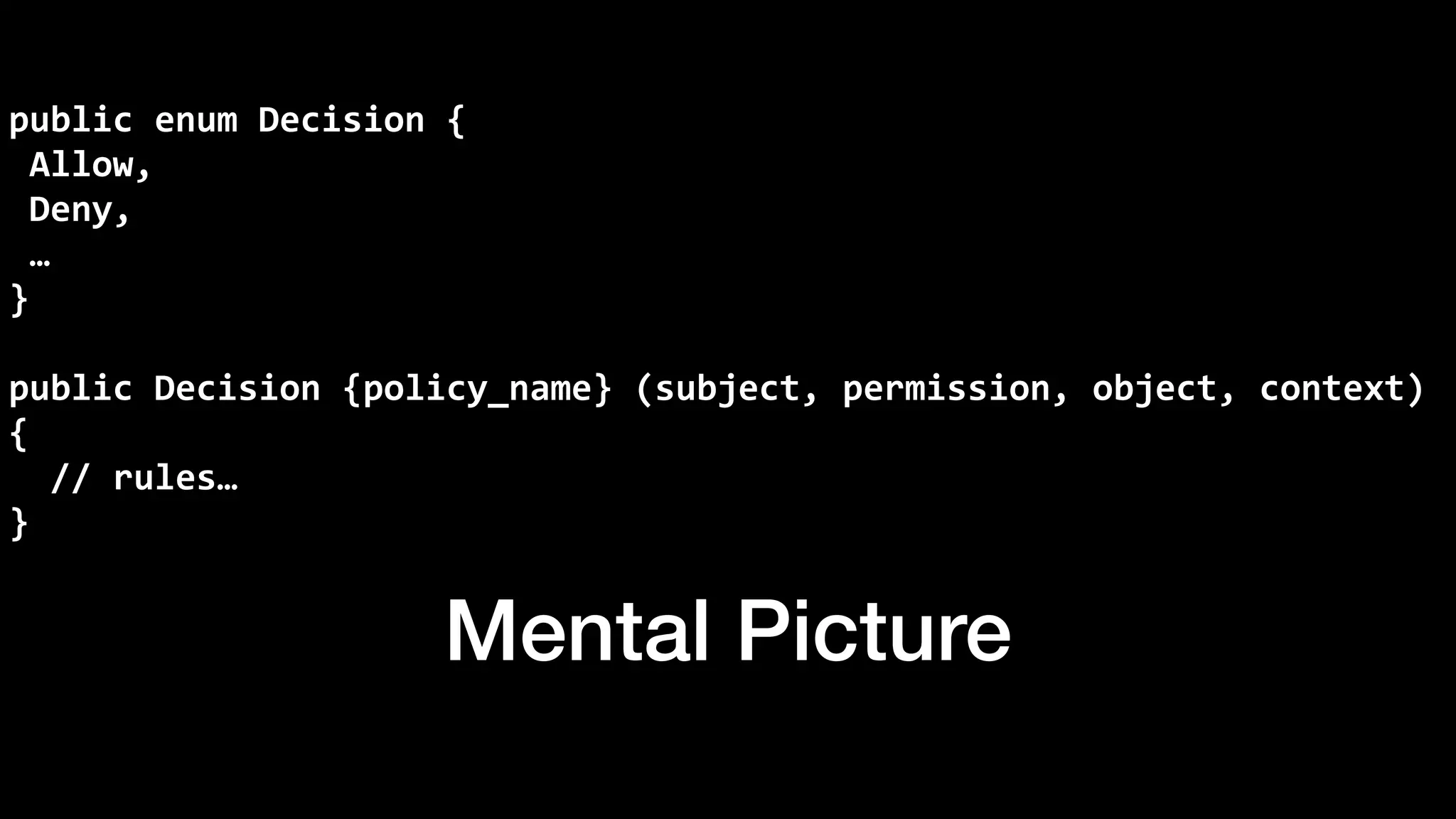
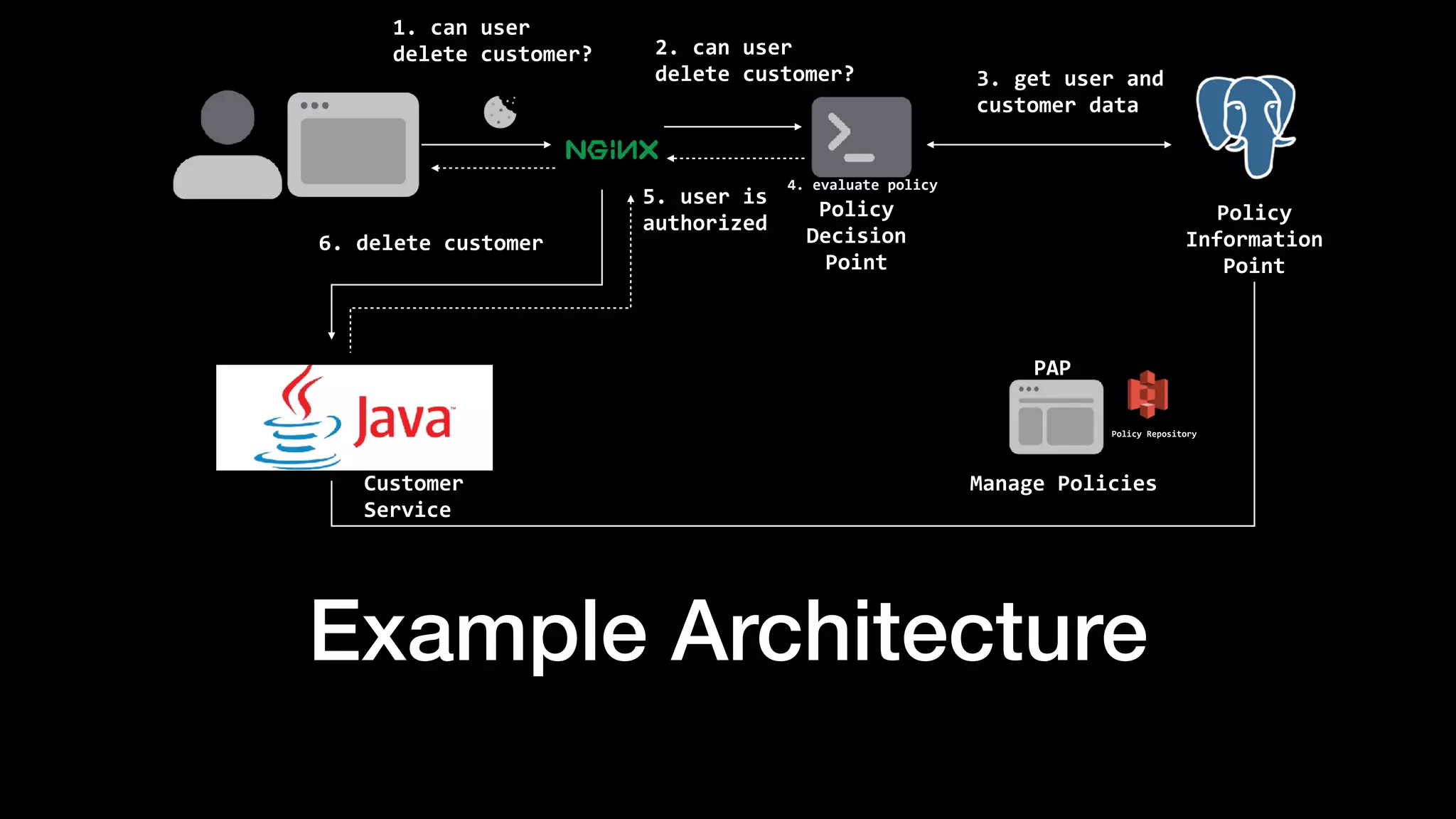
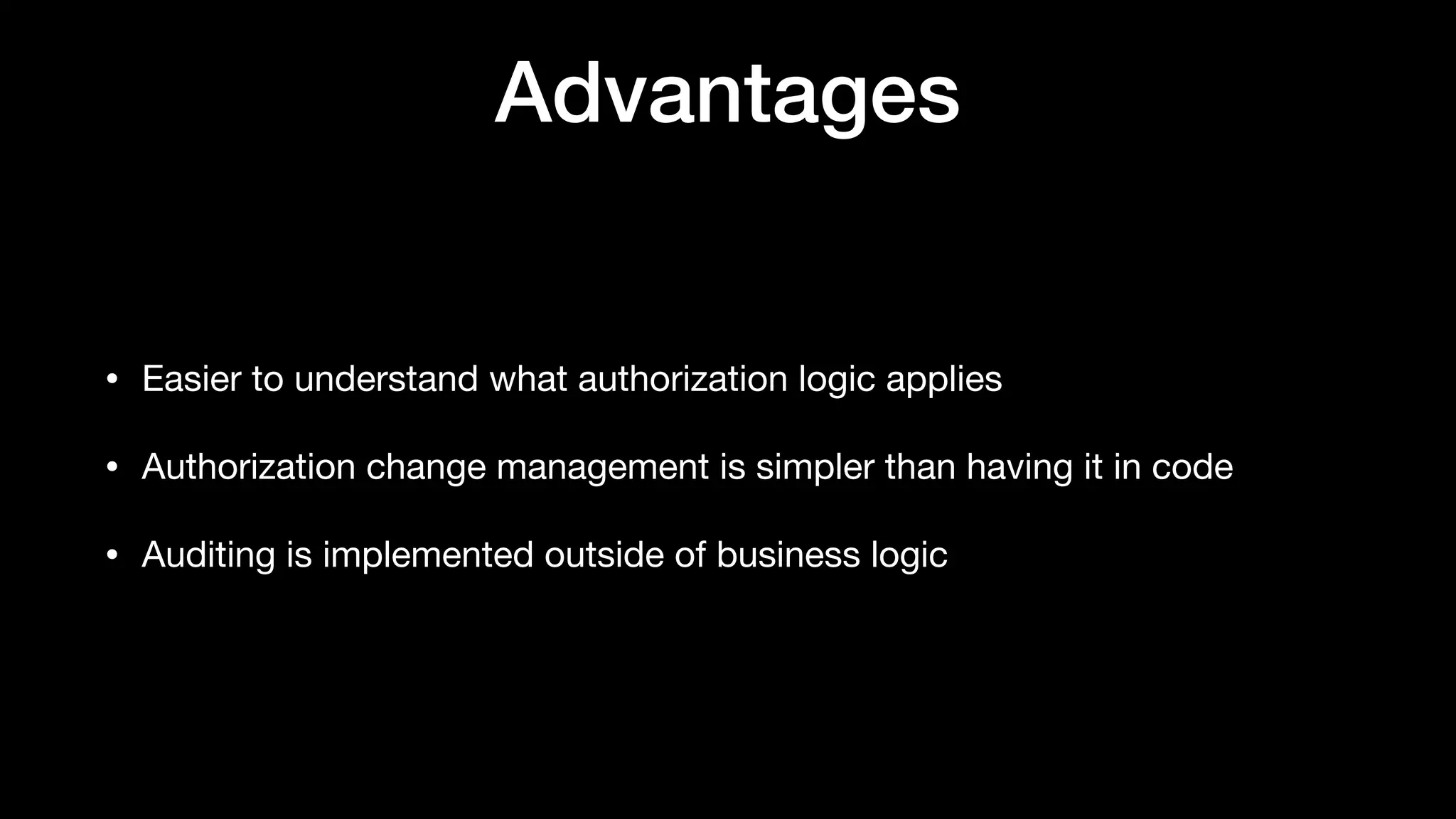
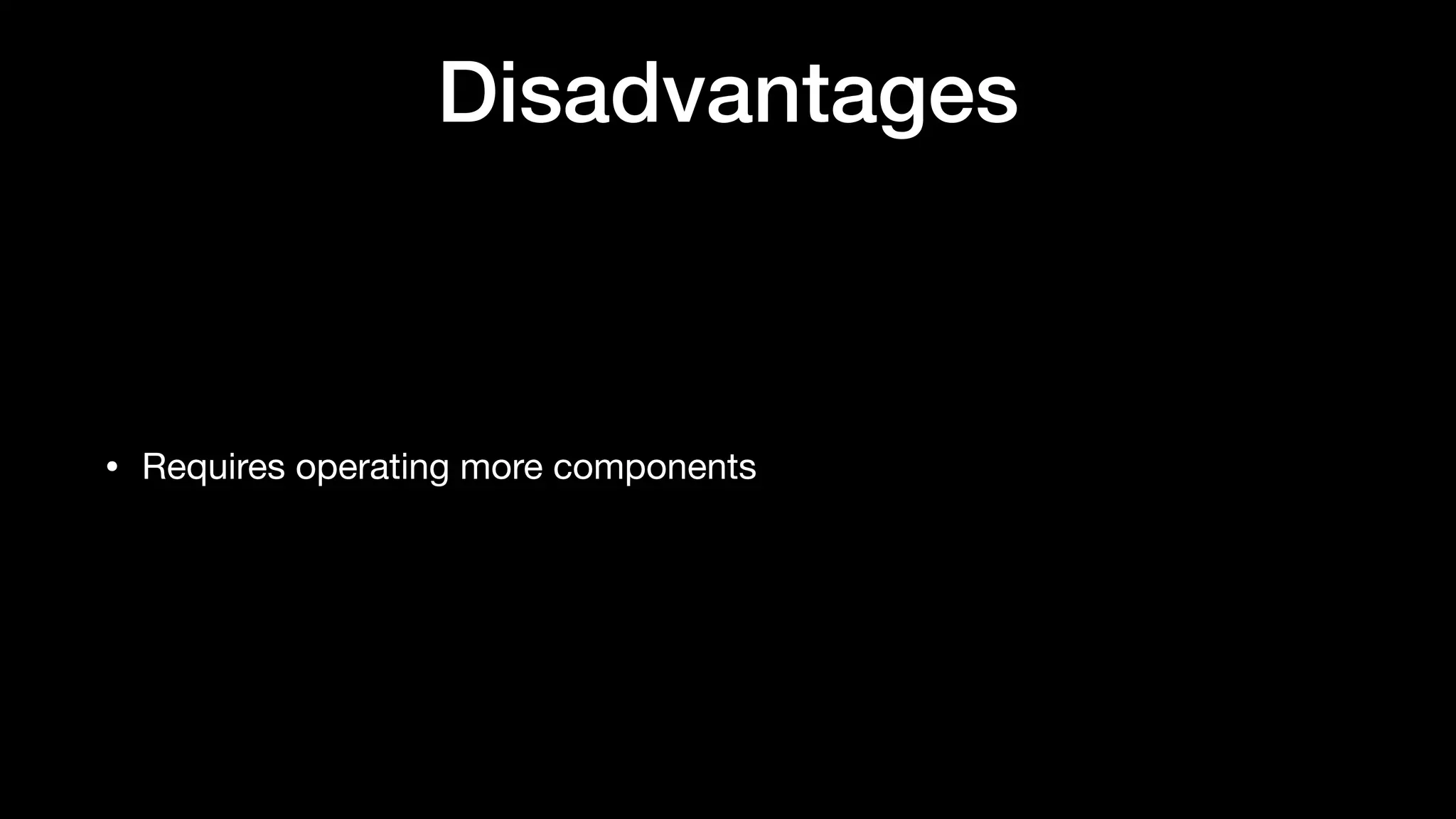
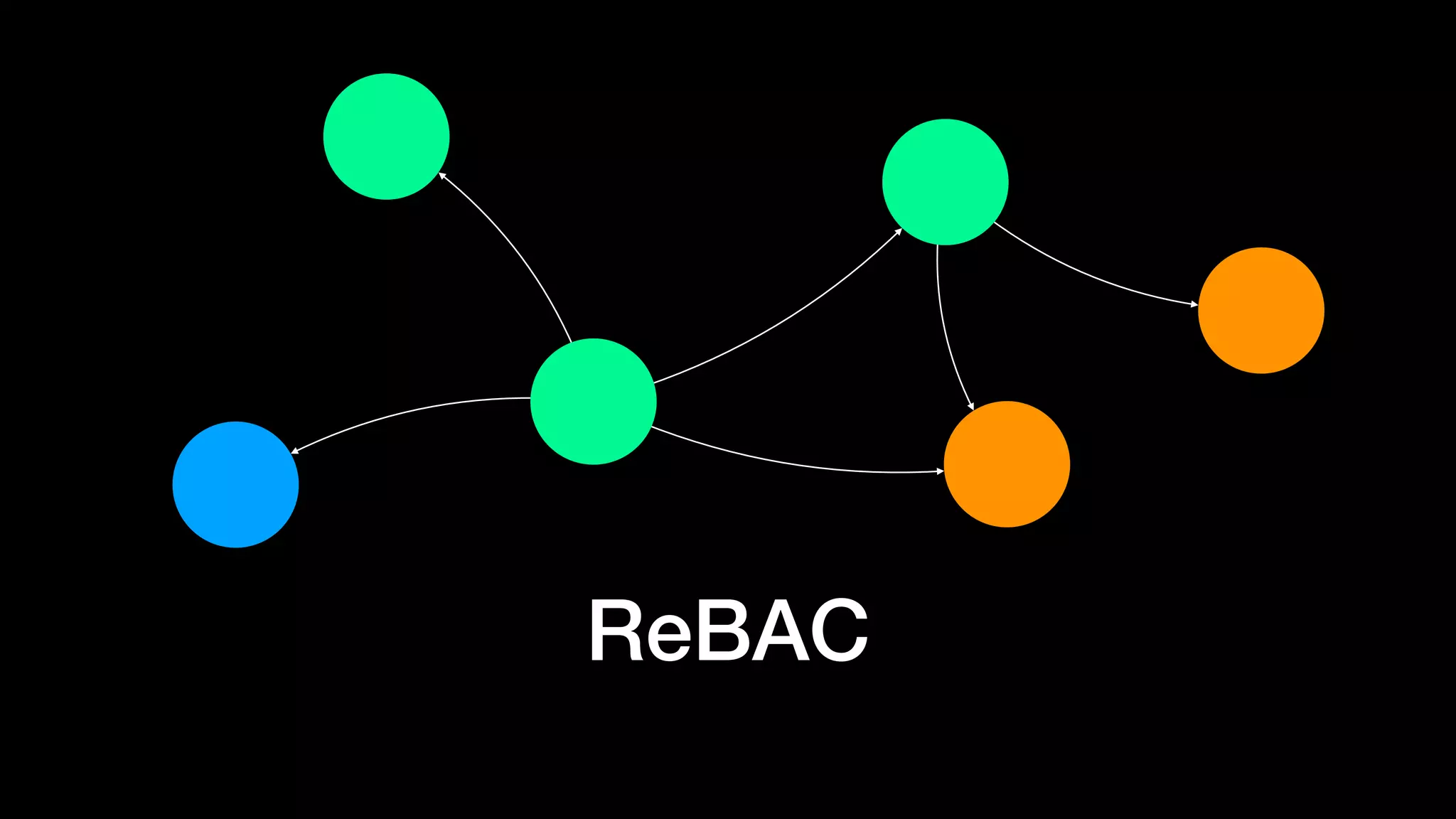
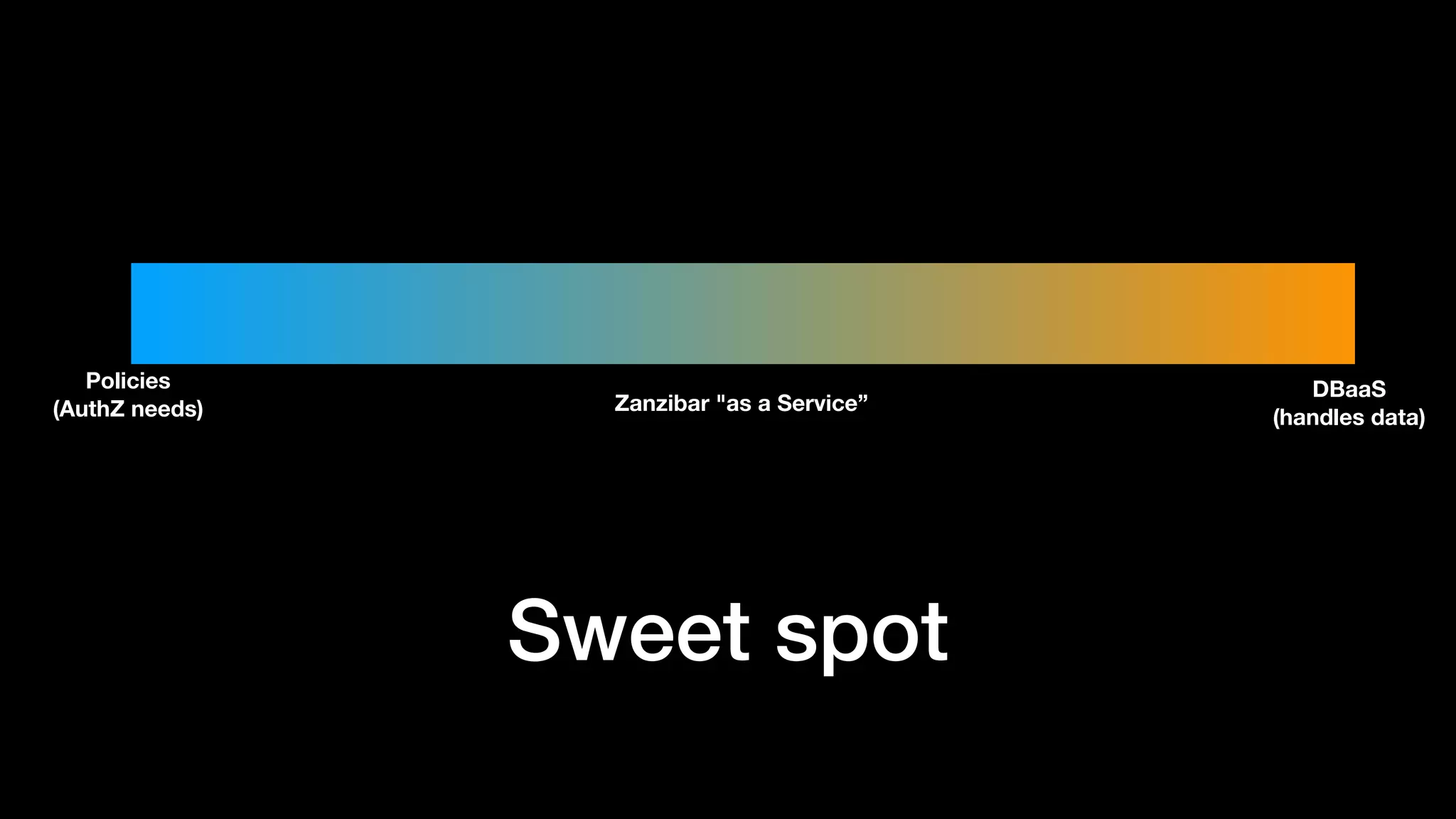
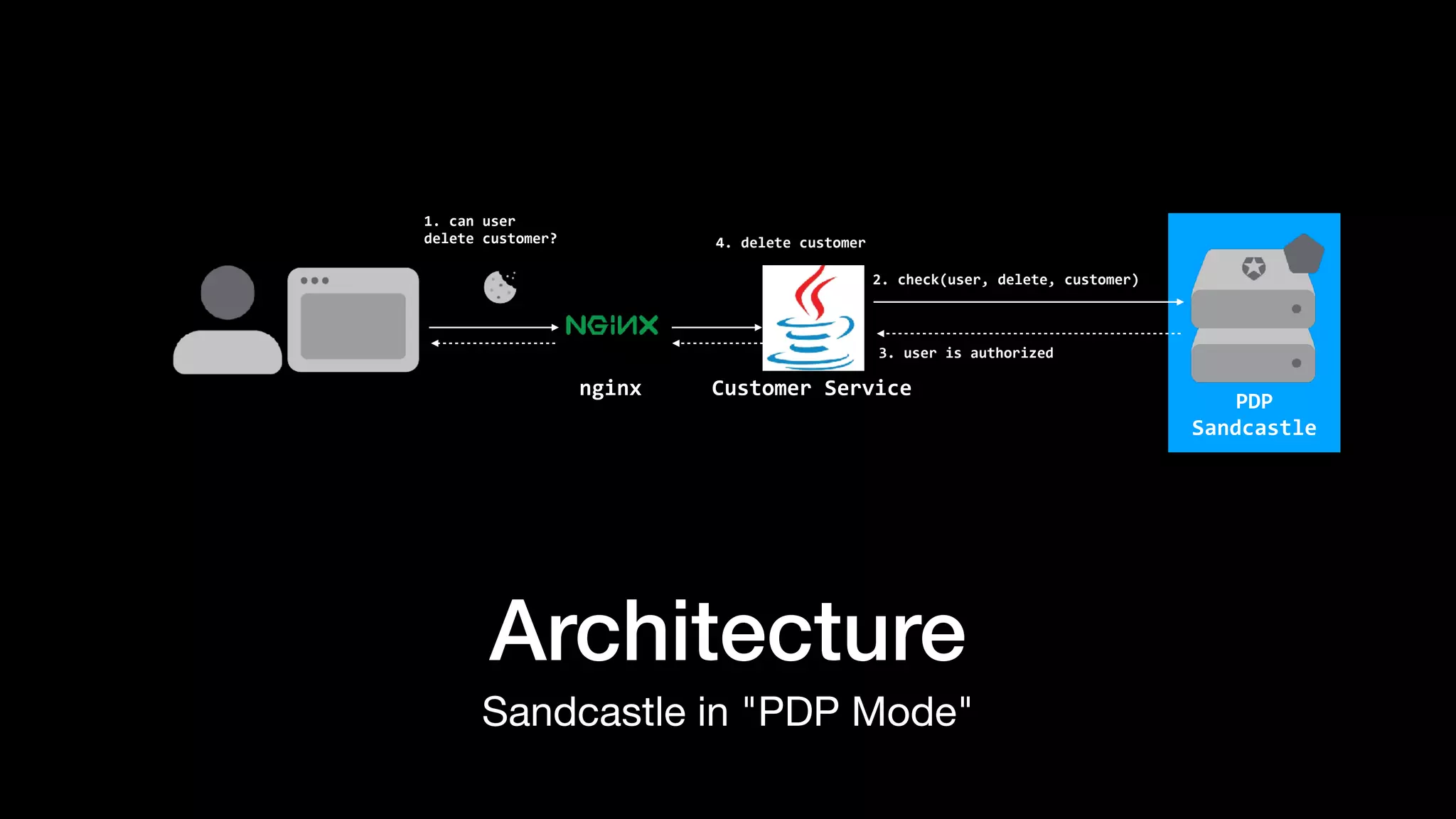
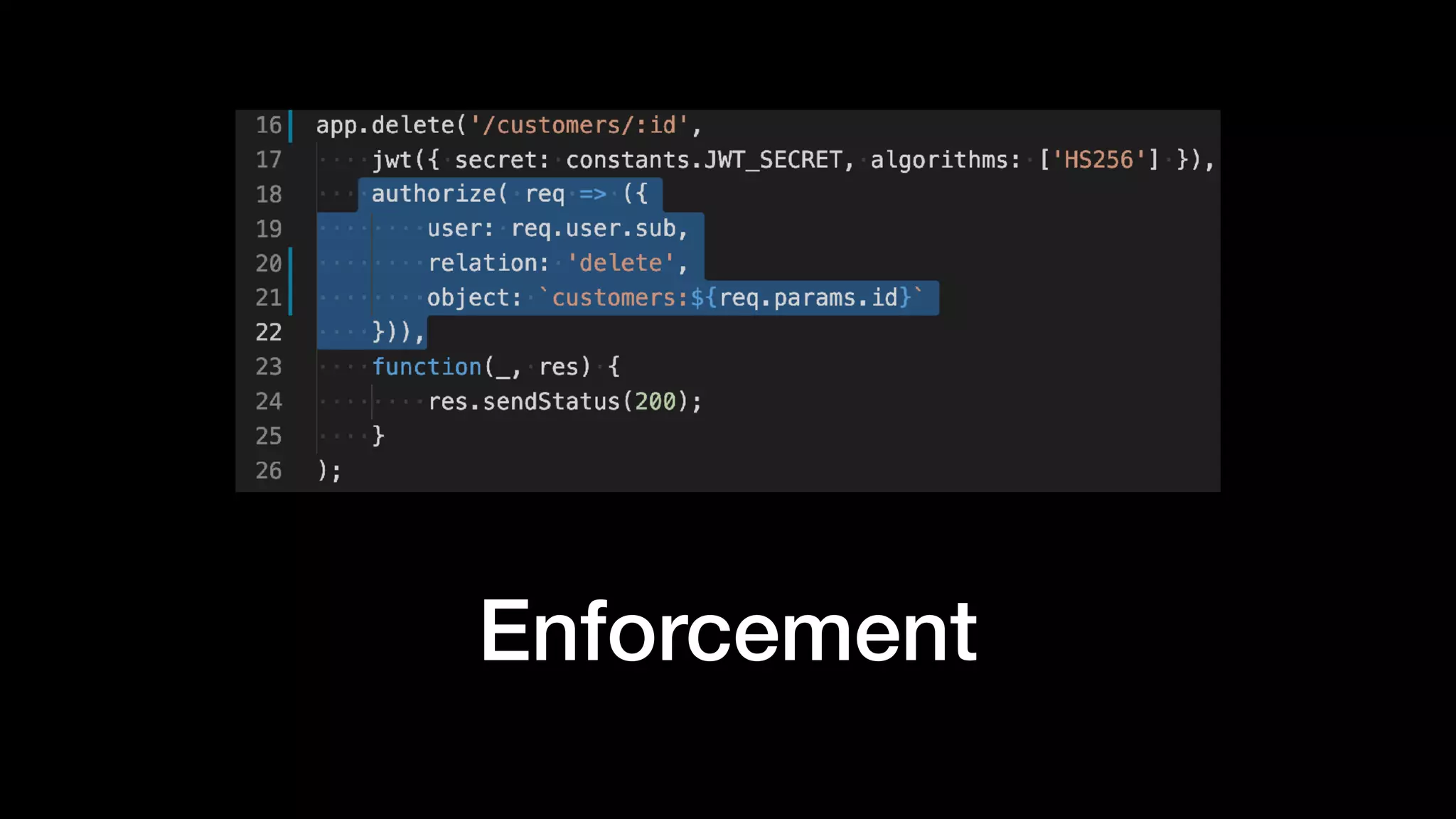
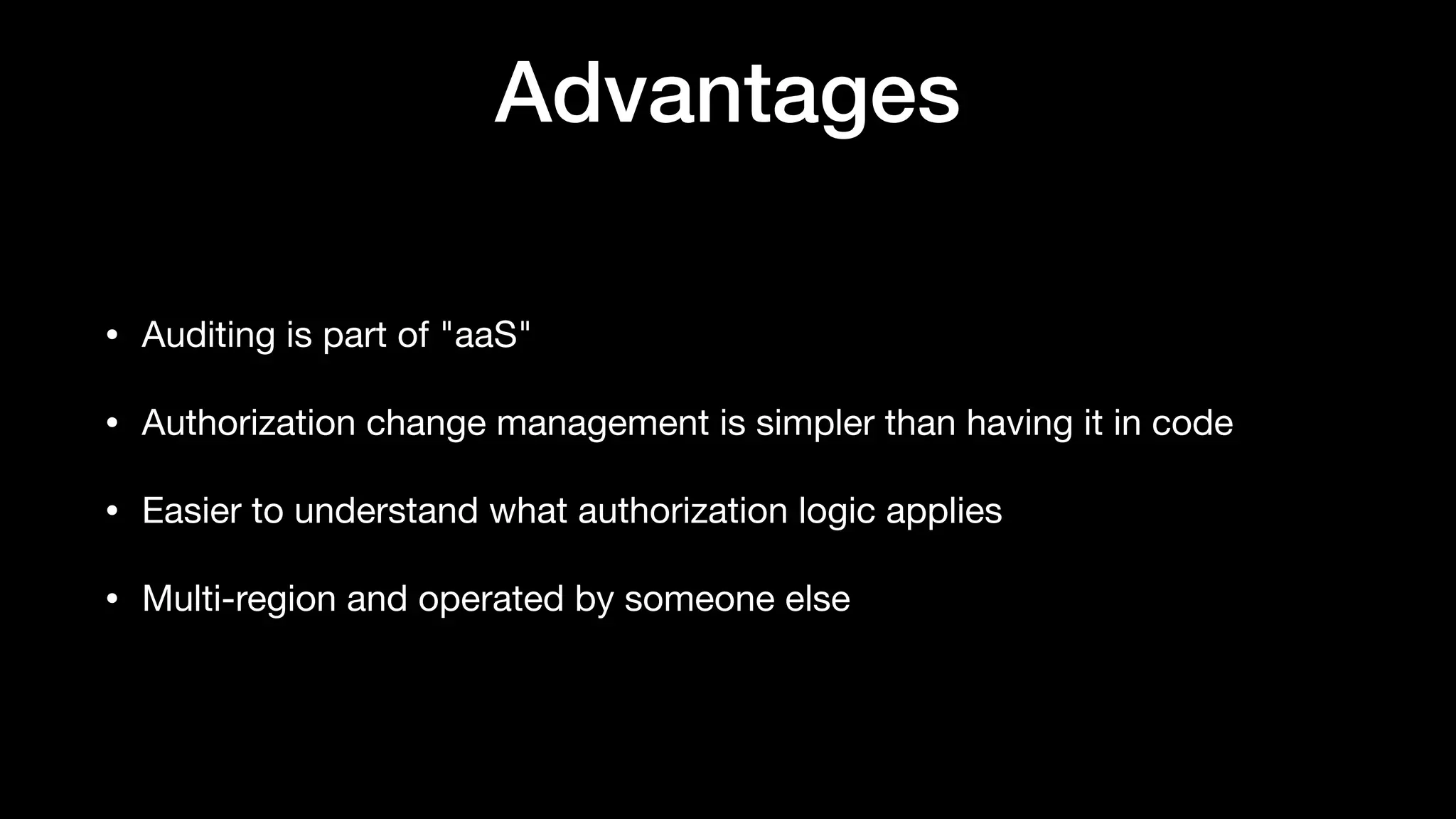
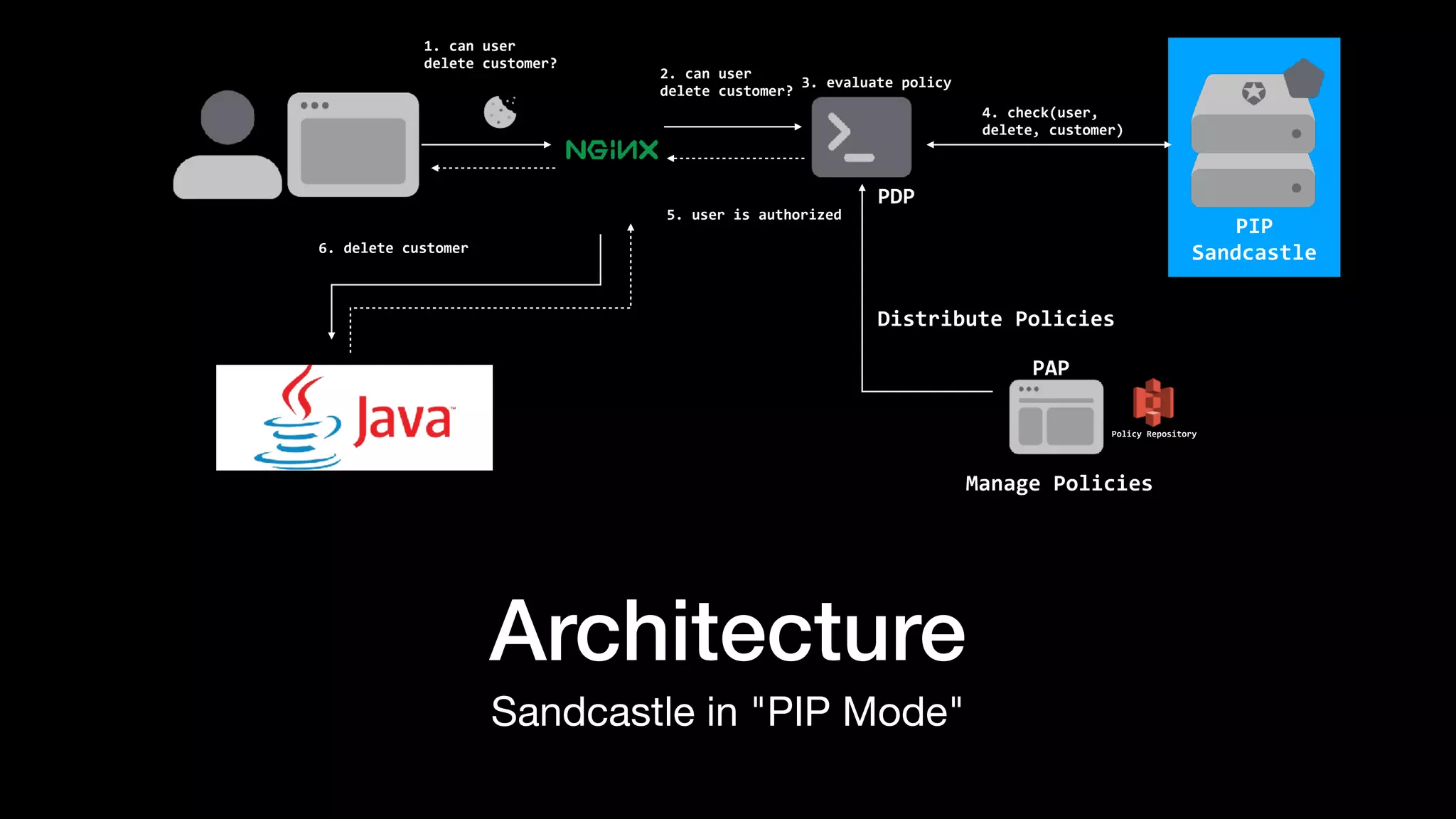
The document discusses the increasing importance of authorization in software development and proposes the need for an API to manage it effectively. It outlines various approaches to authorization, including Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), while also highlighting the advantages and disadvantages of each method. Additionally, it references several resources and tools related to authorization systems and mentions upcoming conferences related to the topic.