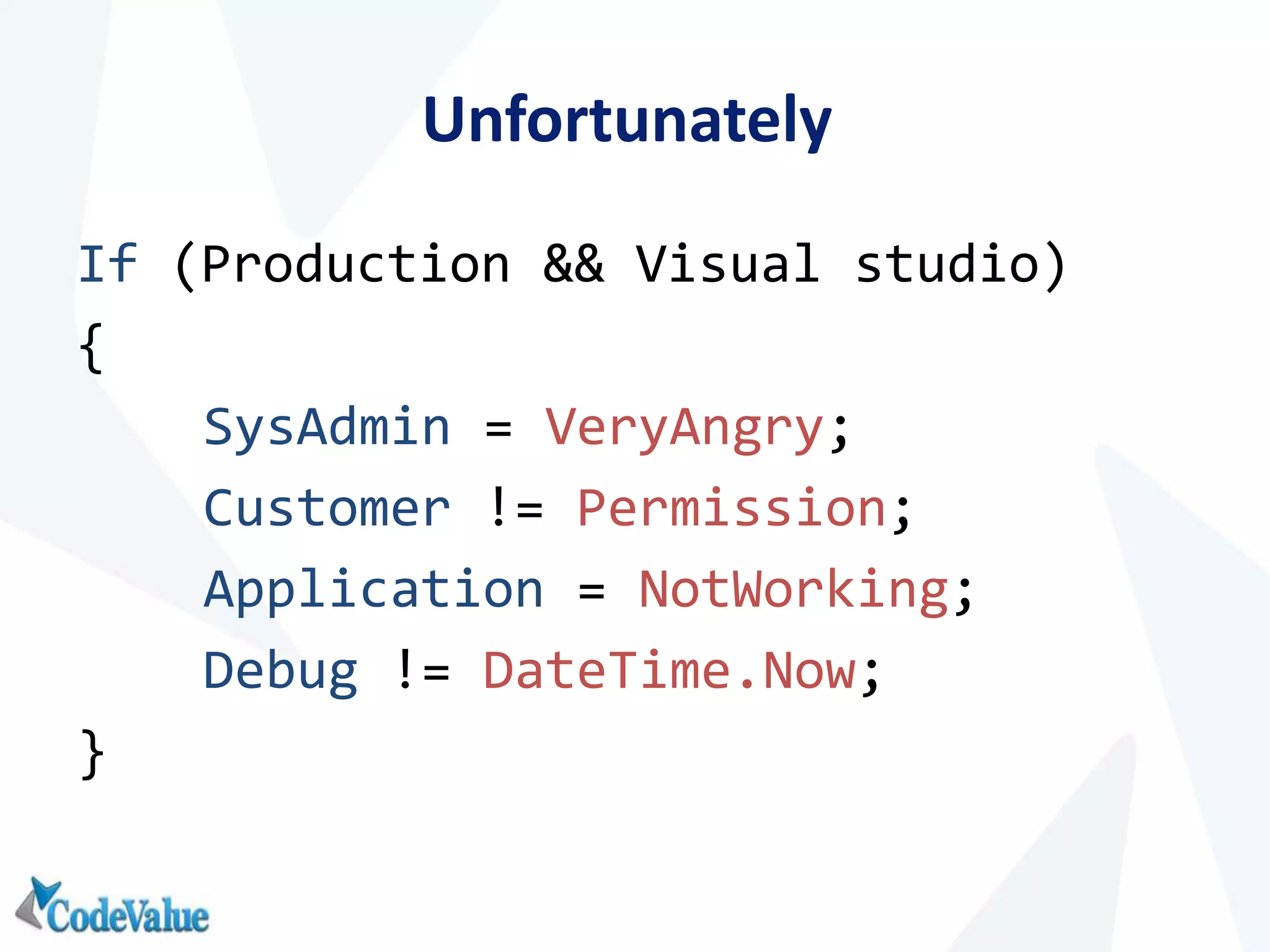
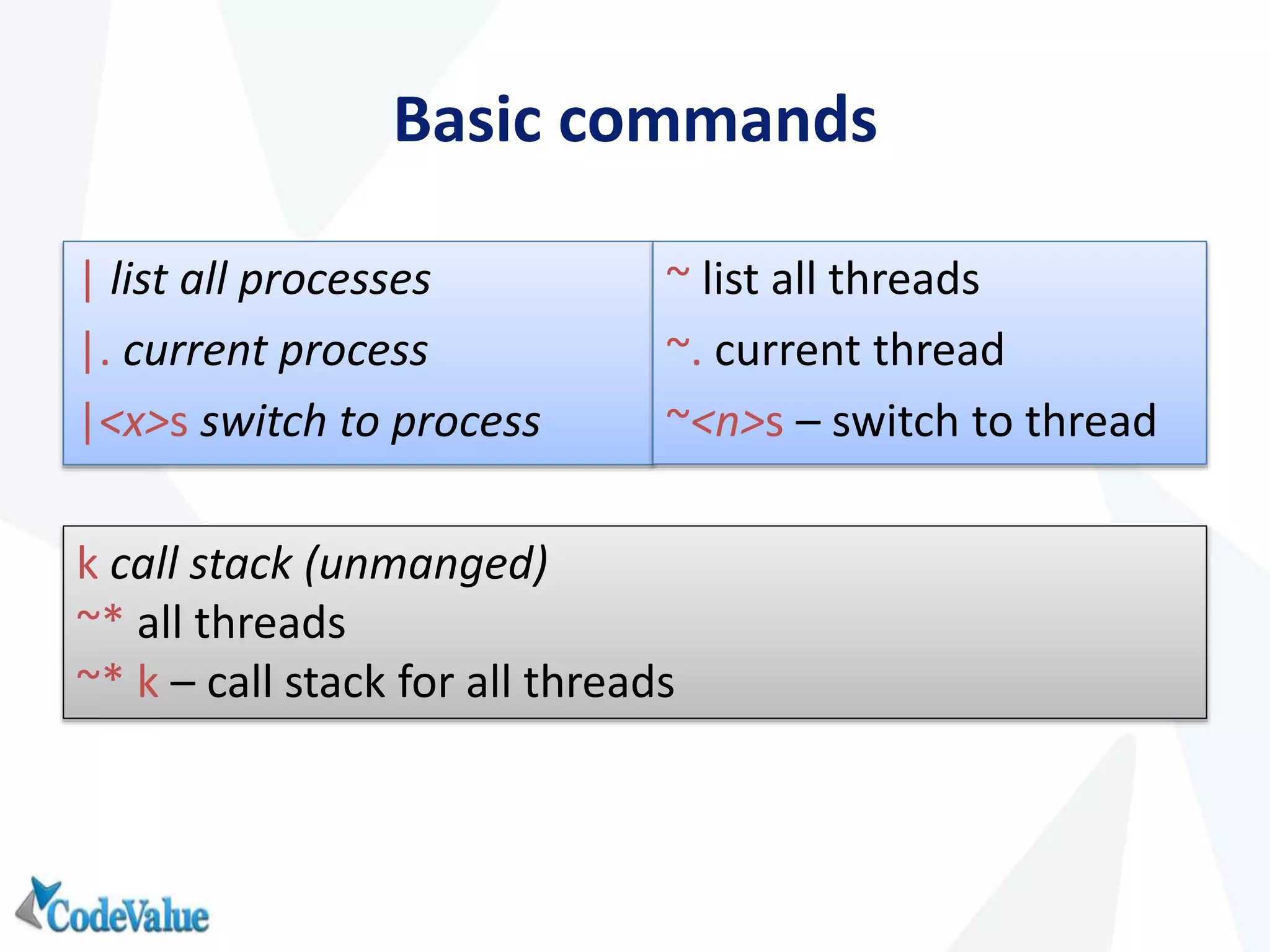
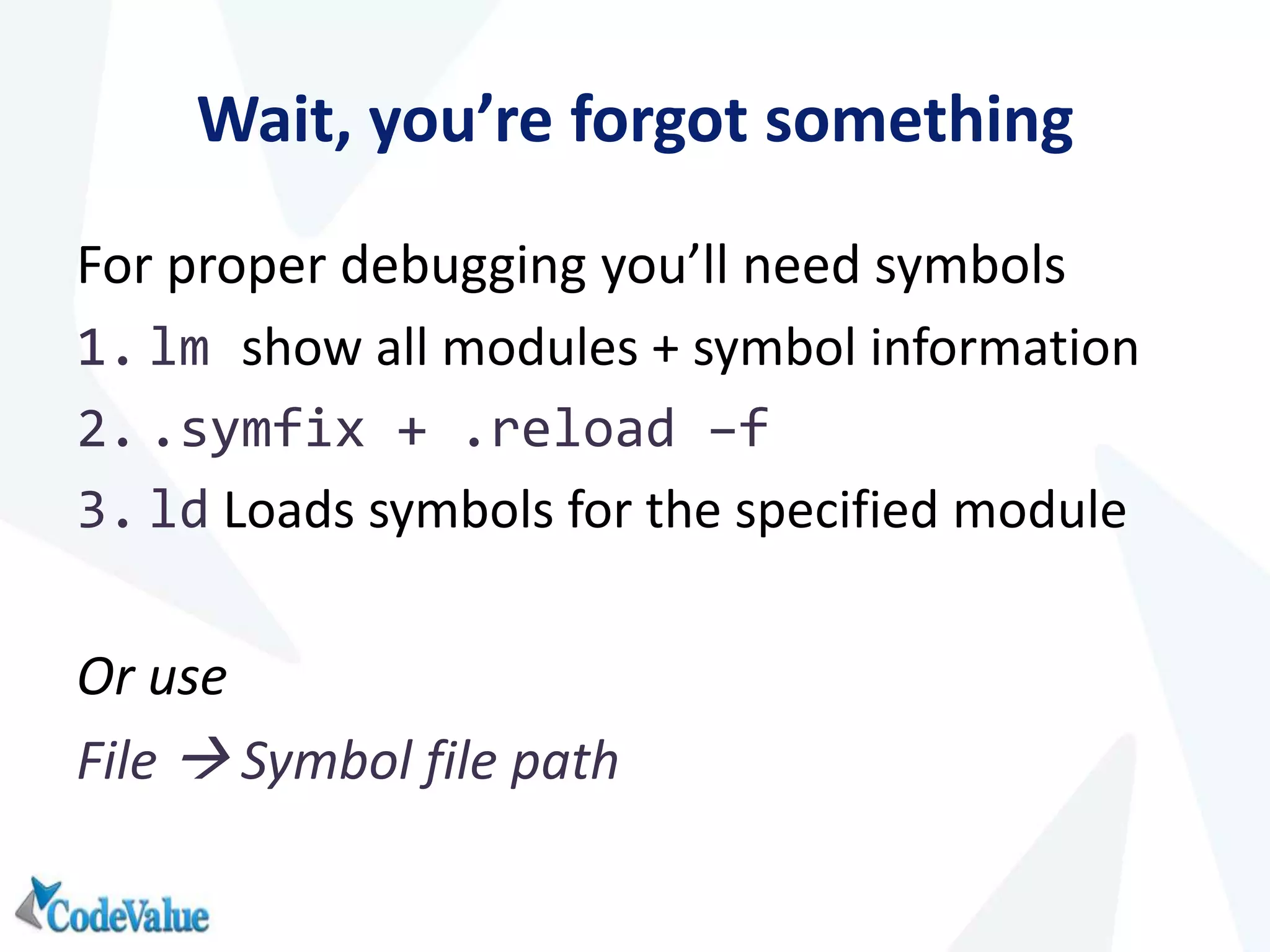
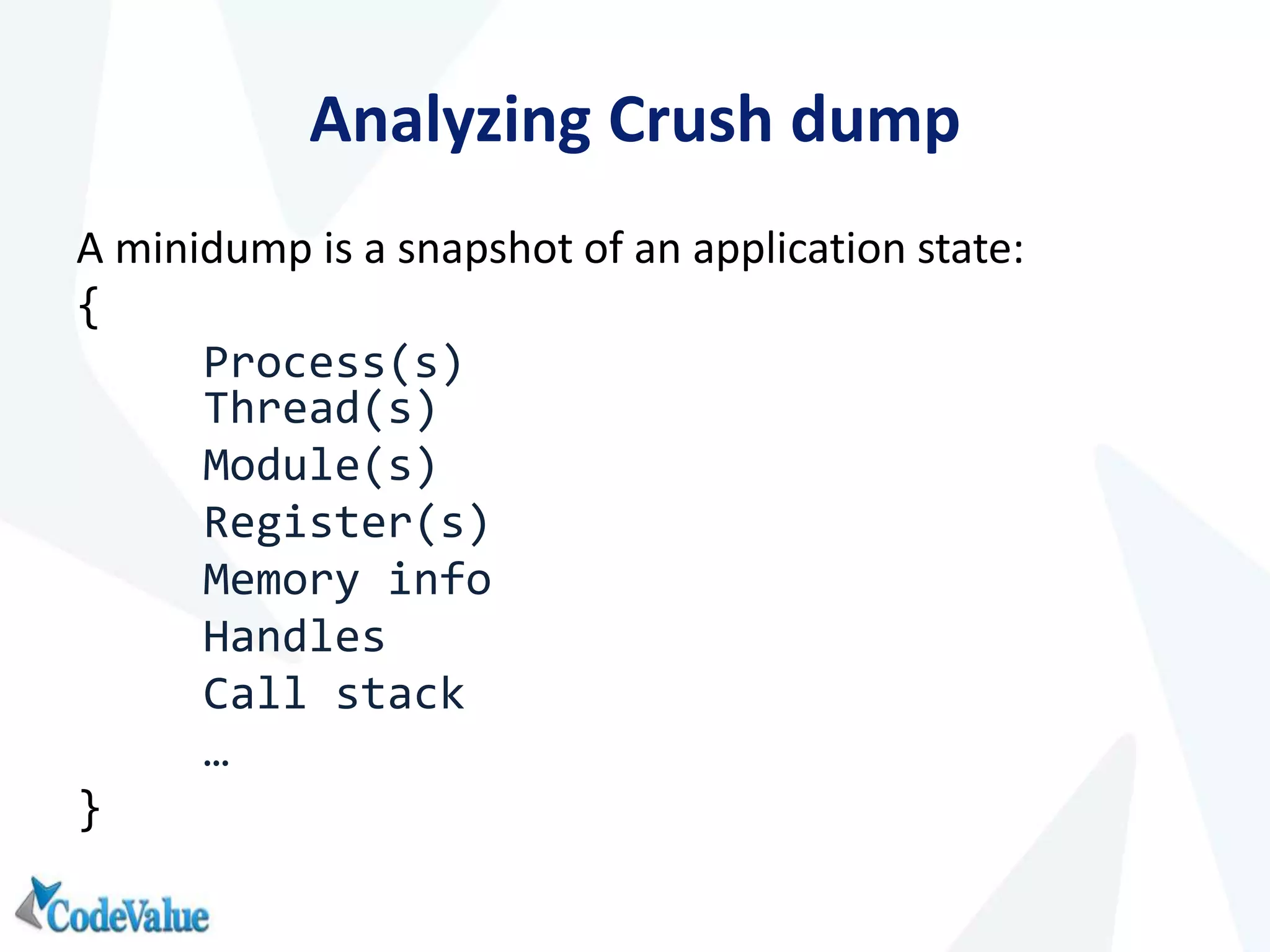
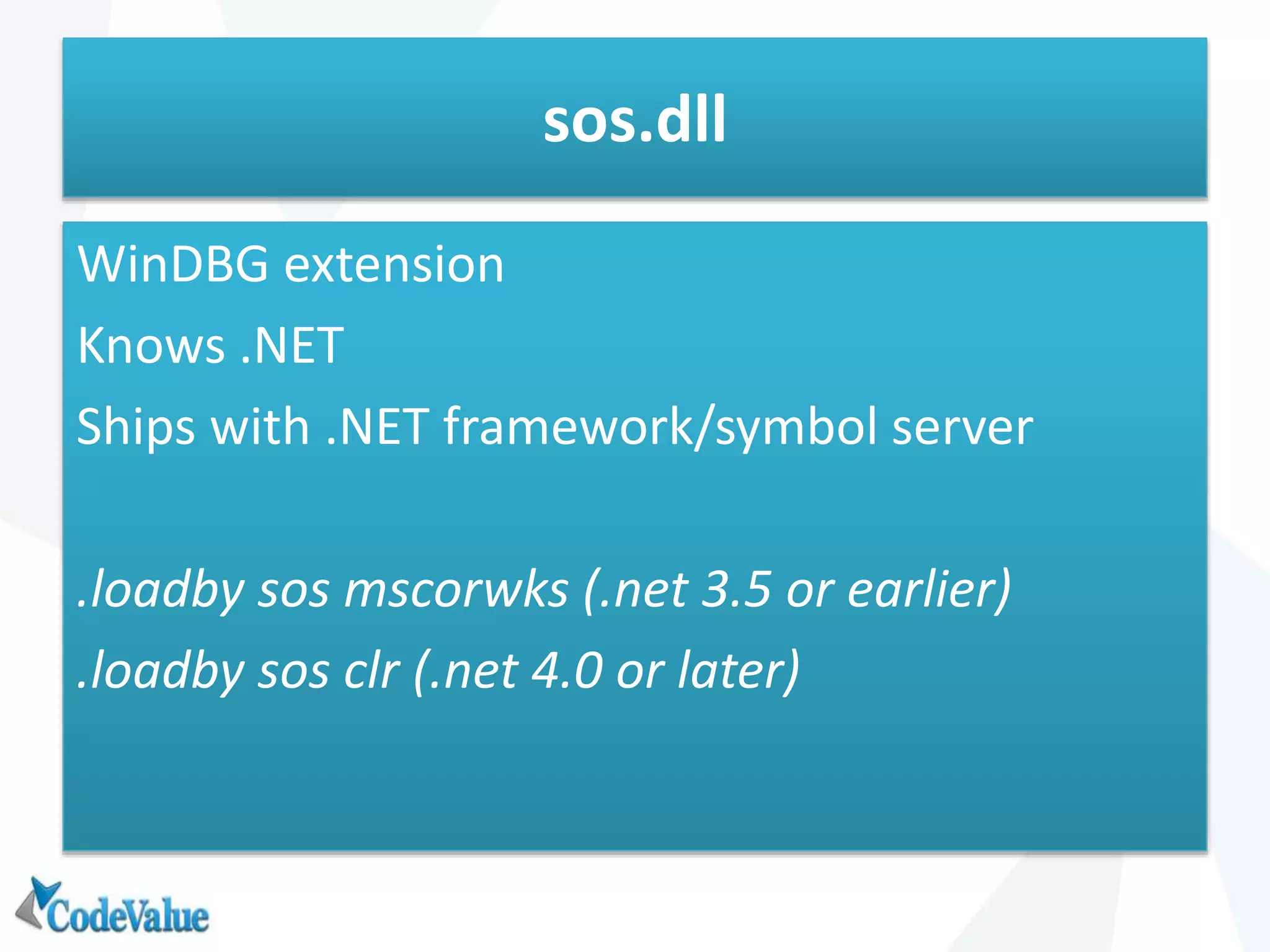
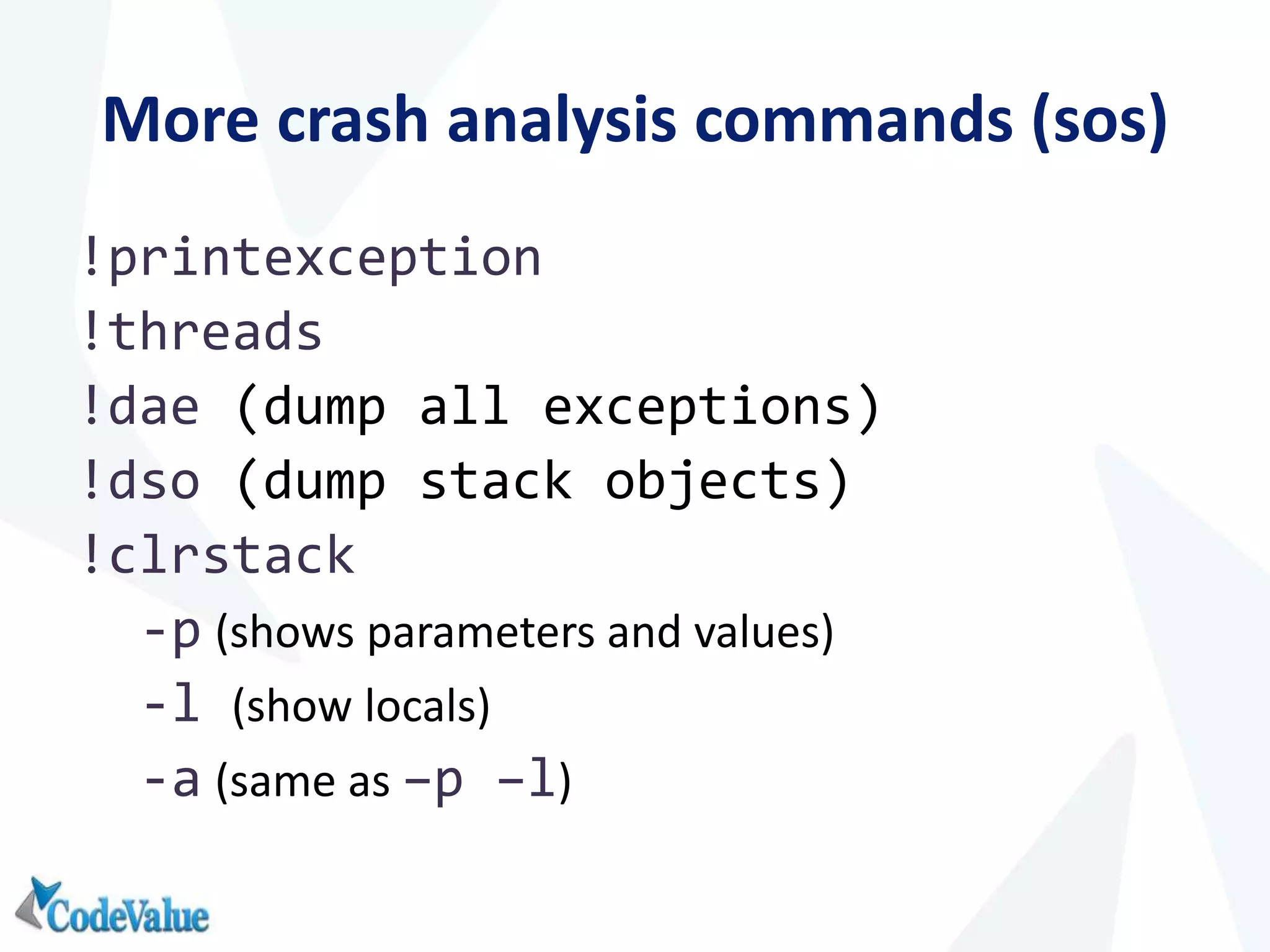
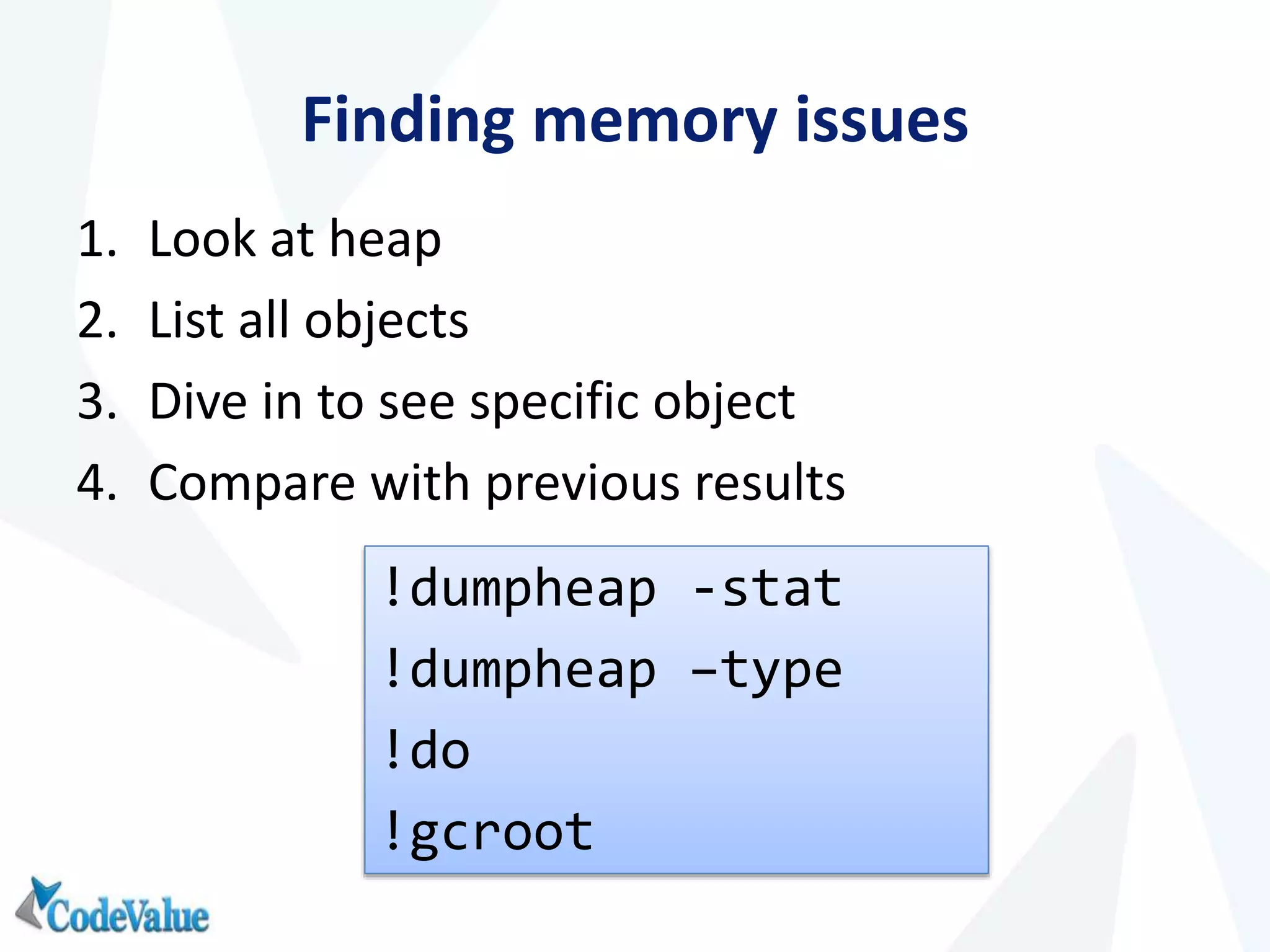
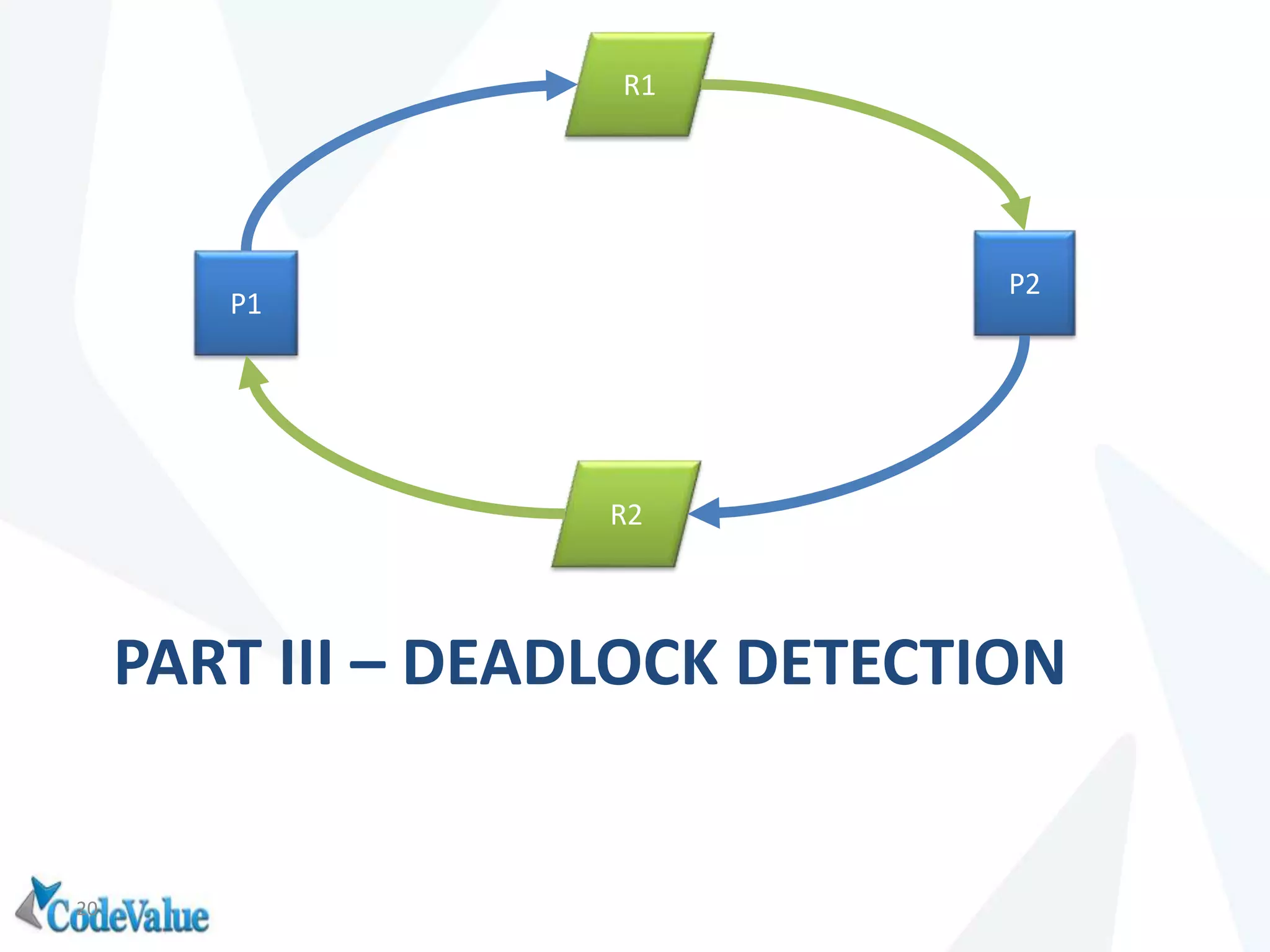
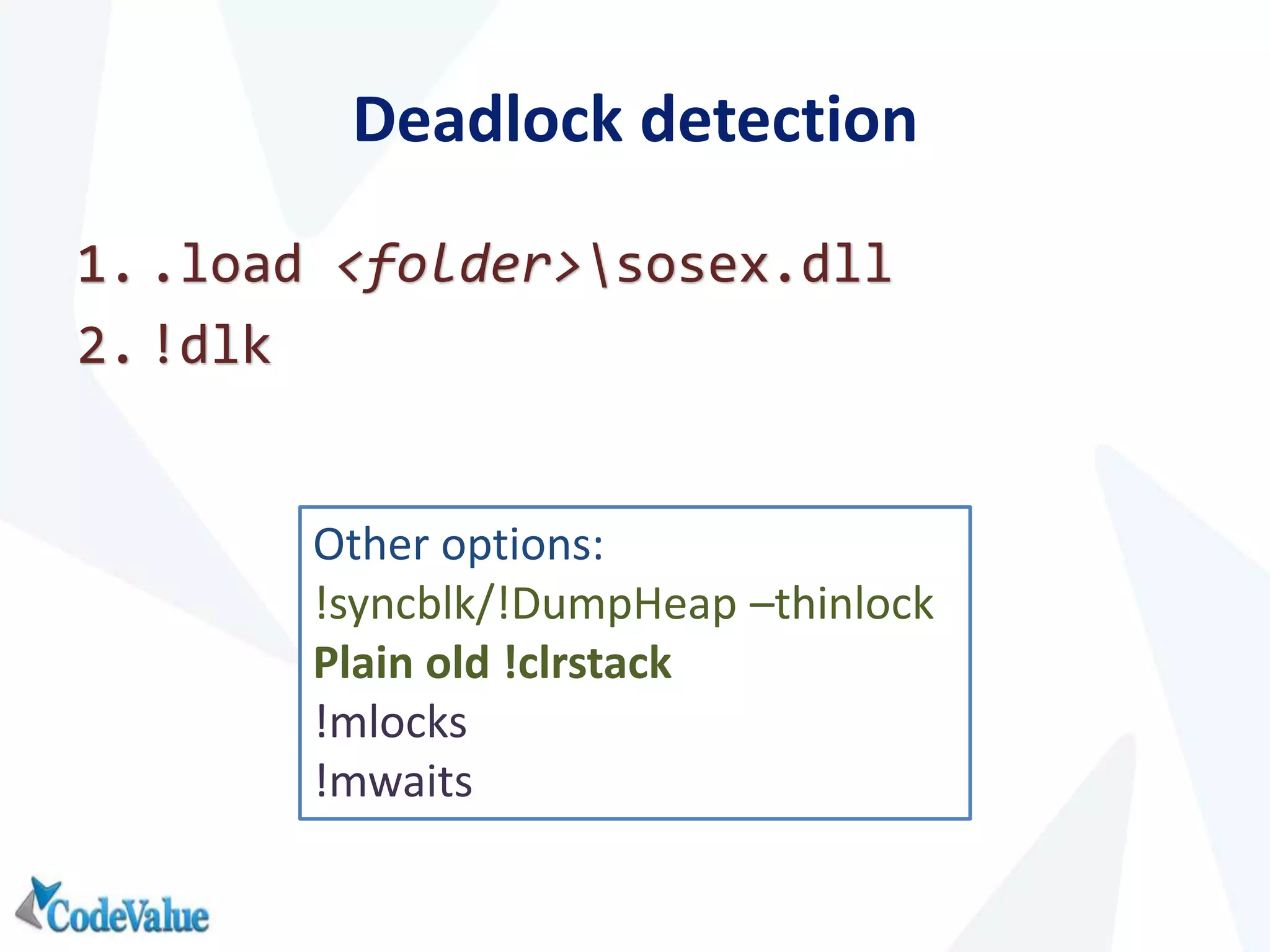
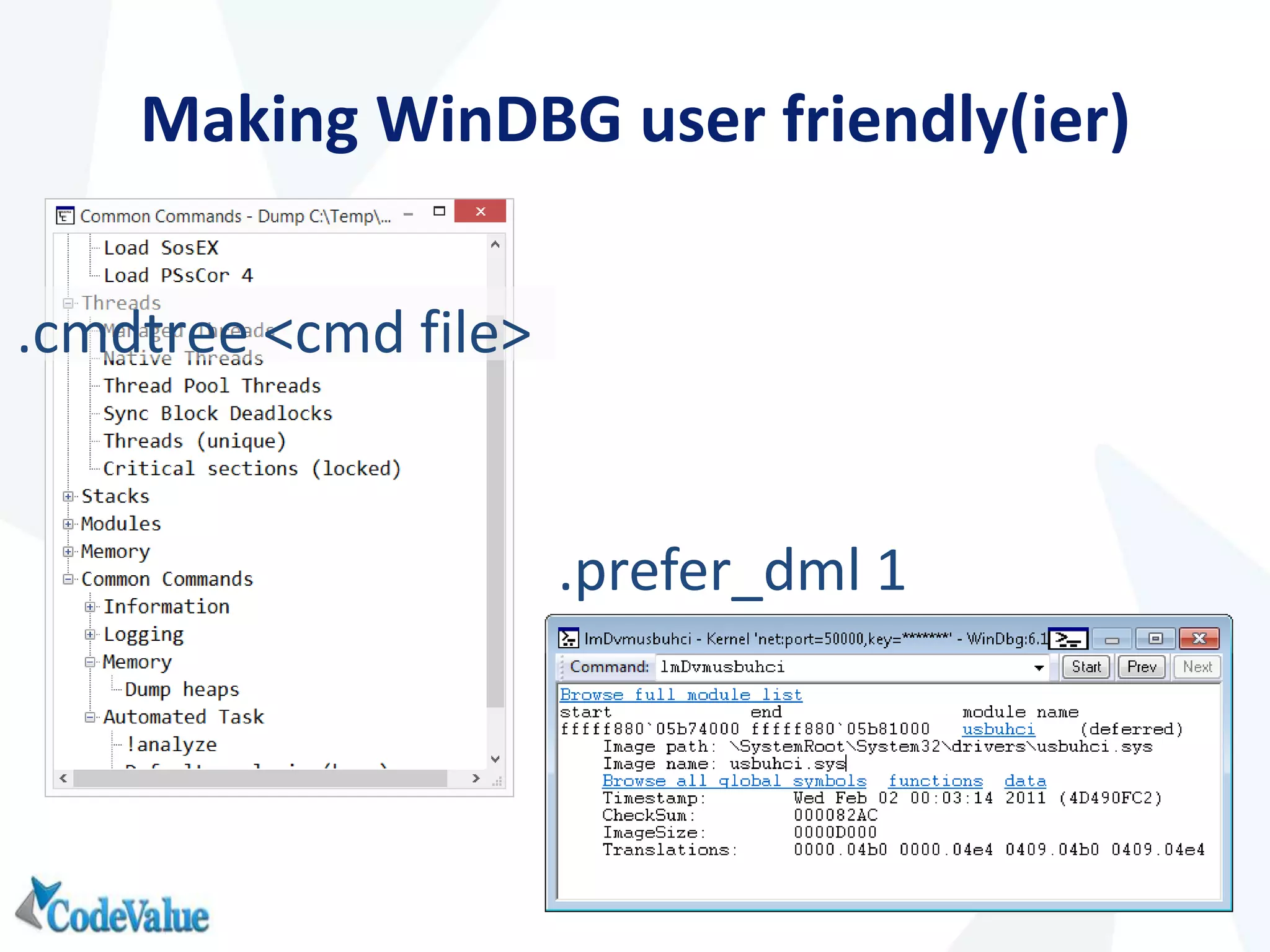
This document introduces WinDbg, a debugger tool that can be used for post mortem crash analysis, memory leak detection, and deadlock discovery. It discusses how to load crash dumps and symbols, and provides an overview of basic commands like listing processes and threads. Crash analysis commands for .NET like !analyze, !printexception, and !clrstack are presented. Commands for investigating memory issues like !dumpheap and !gcroot are also highlighted. The document concludes with discussing deadlock detection using commands like !dlk and !mwaits.