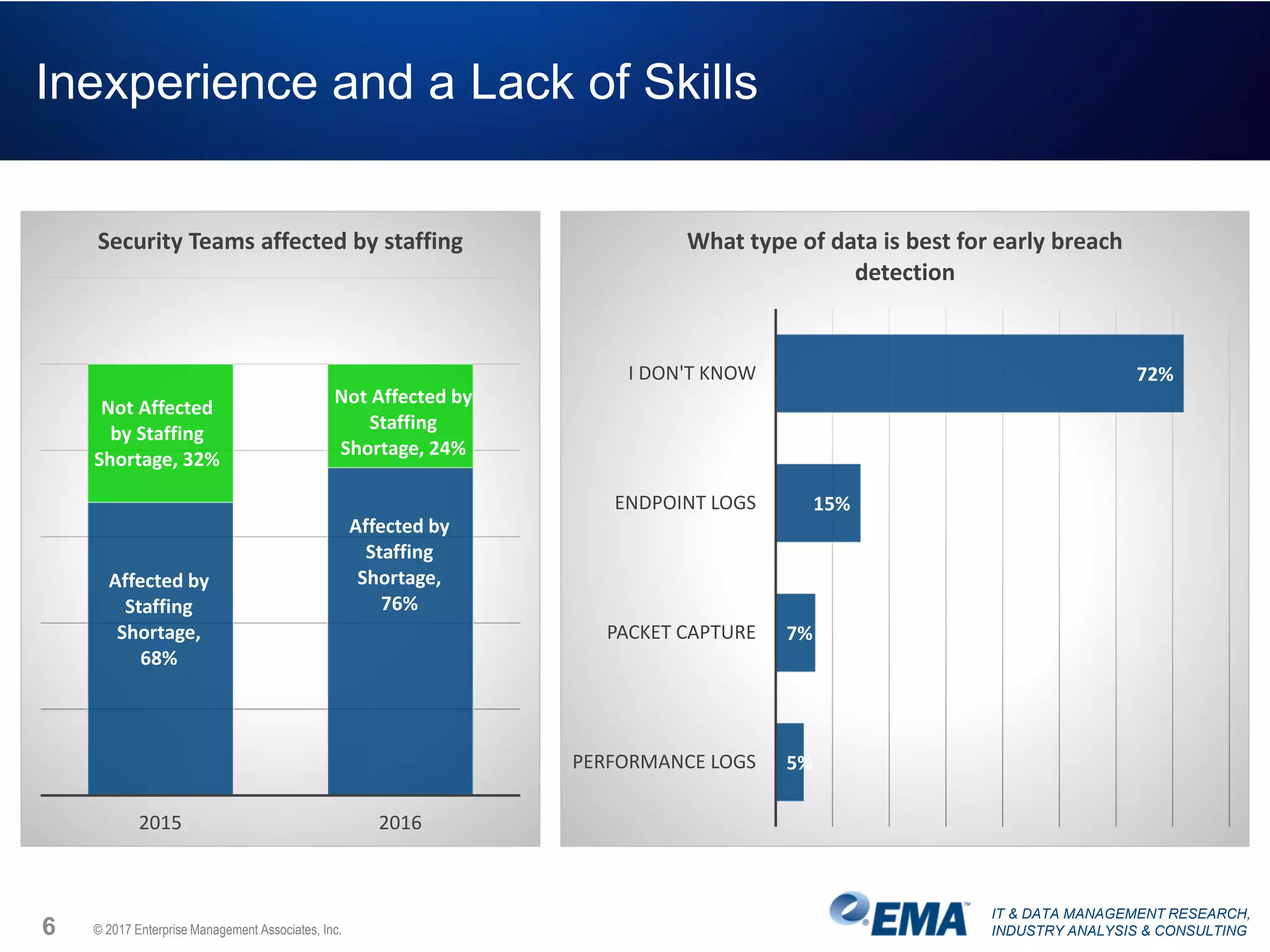
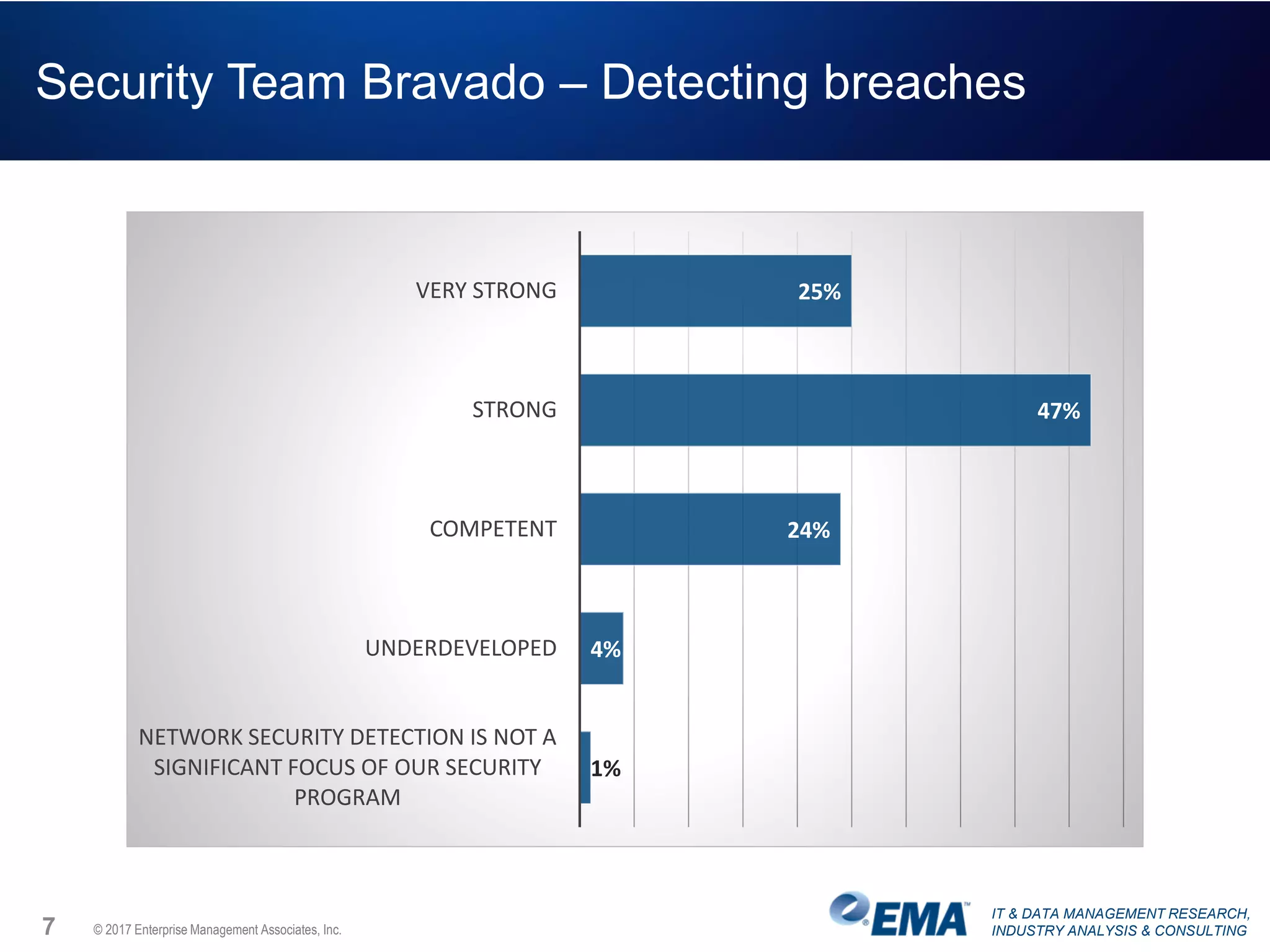
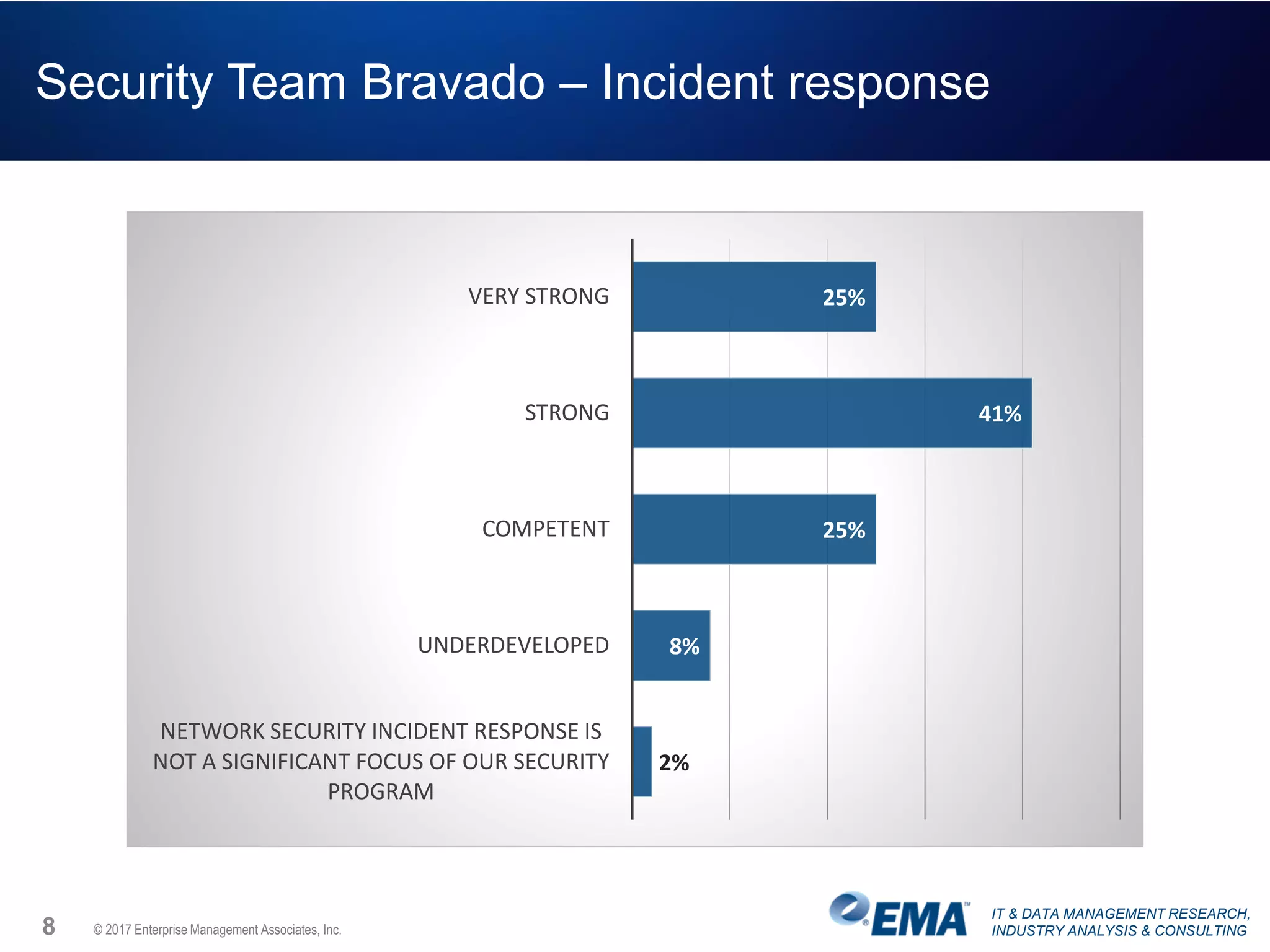
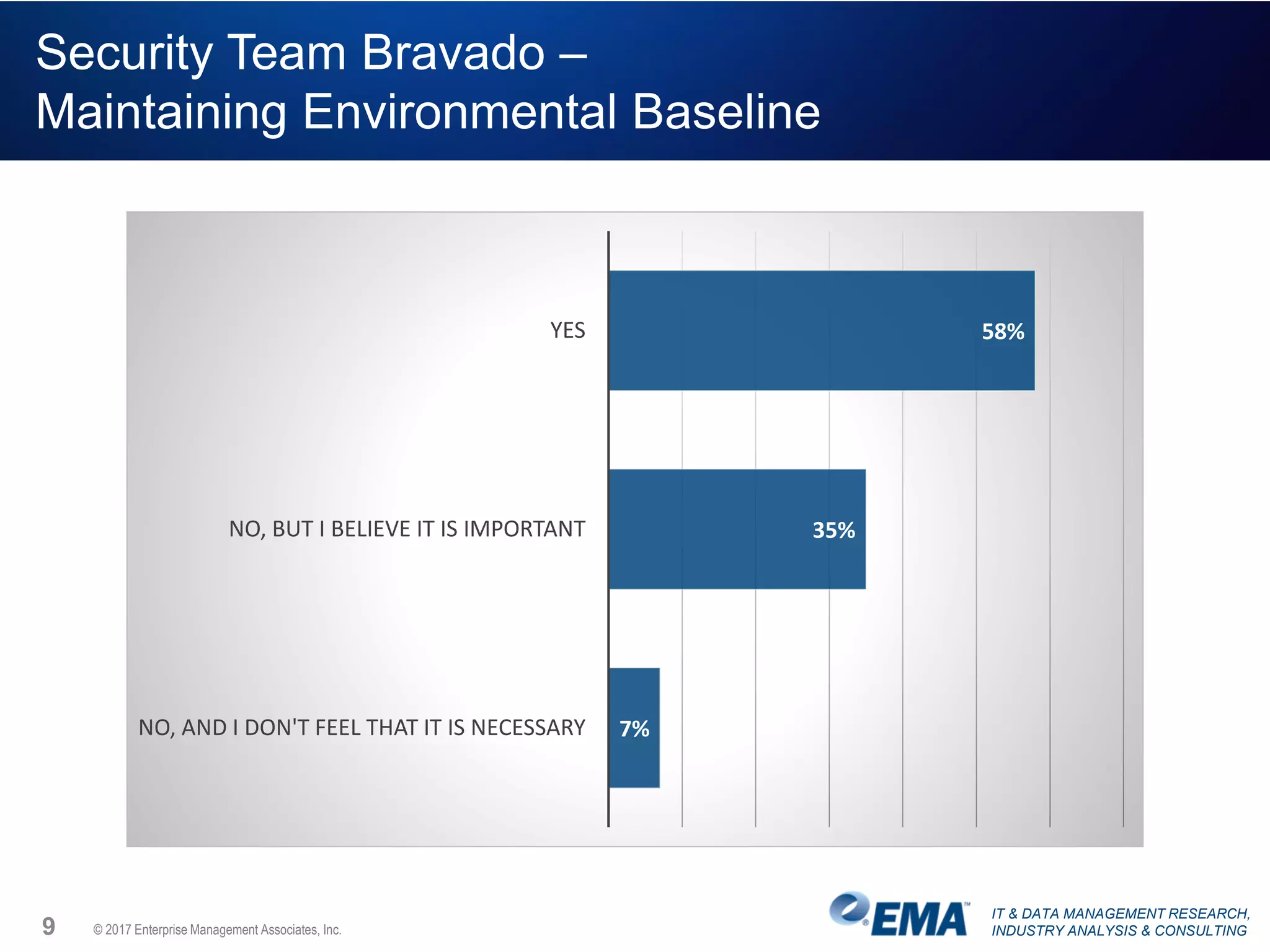
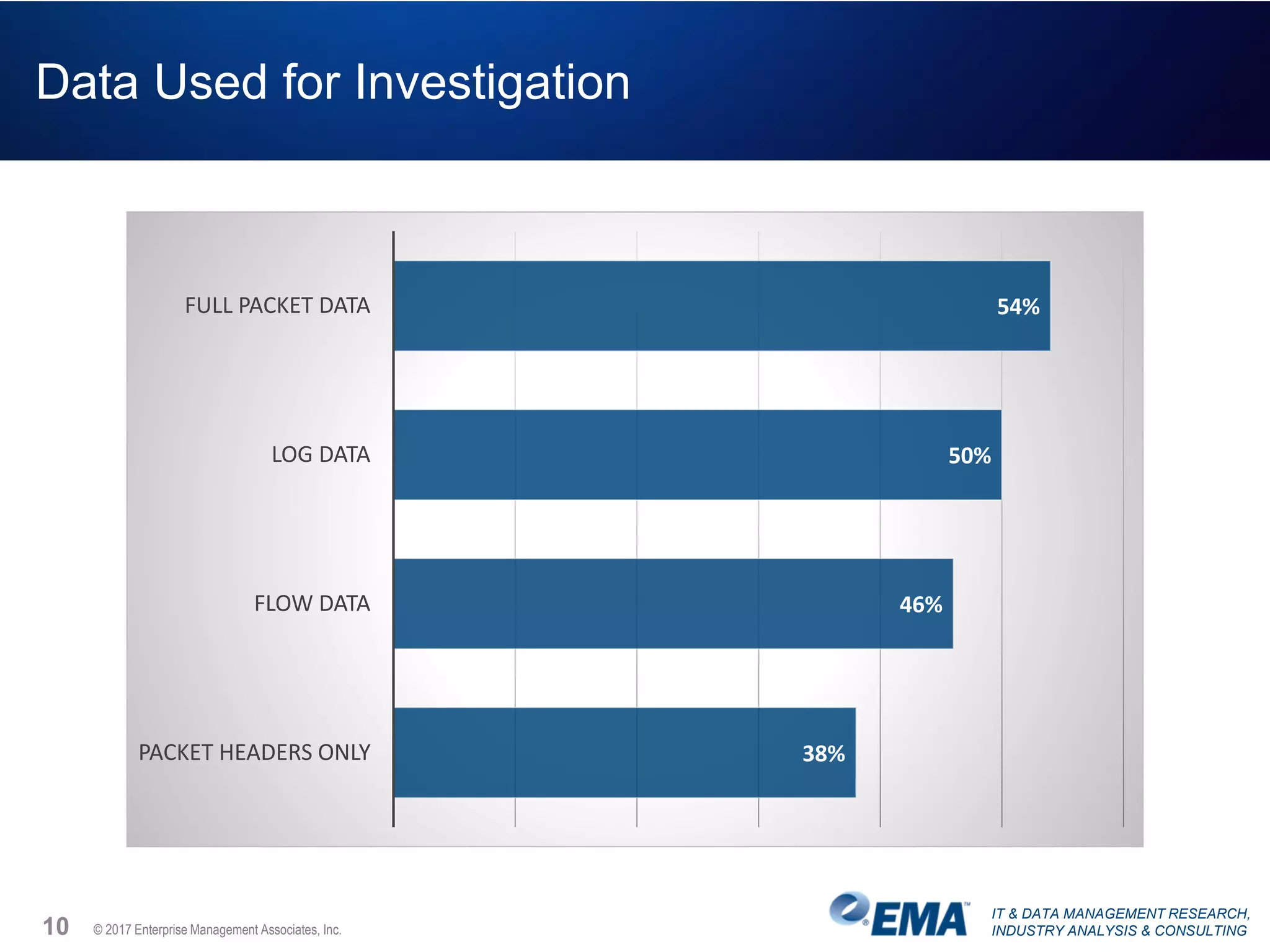
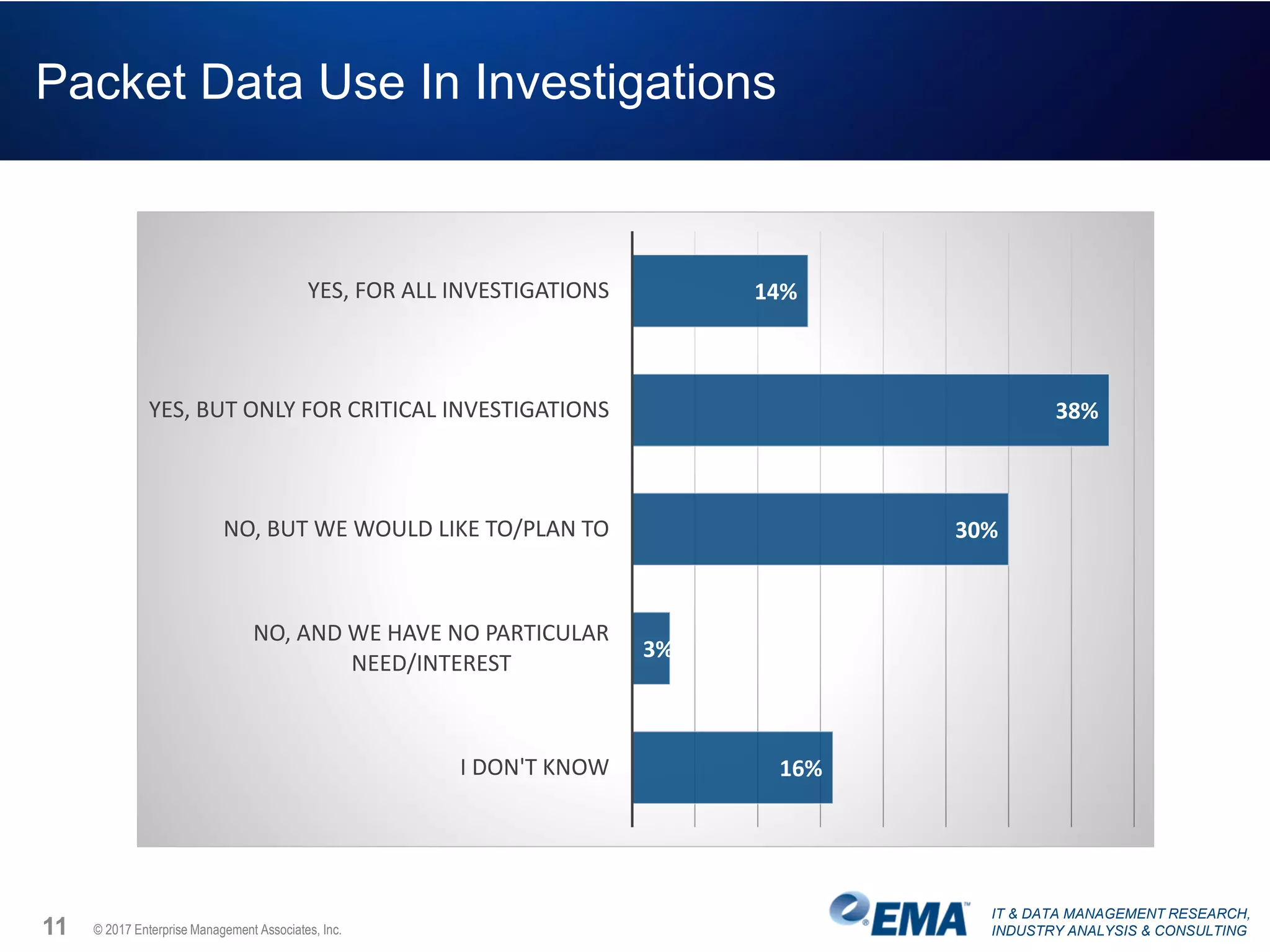
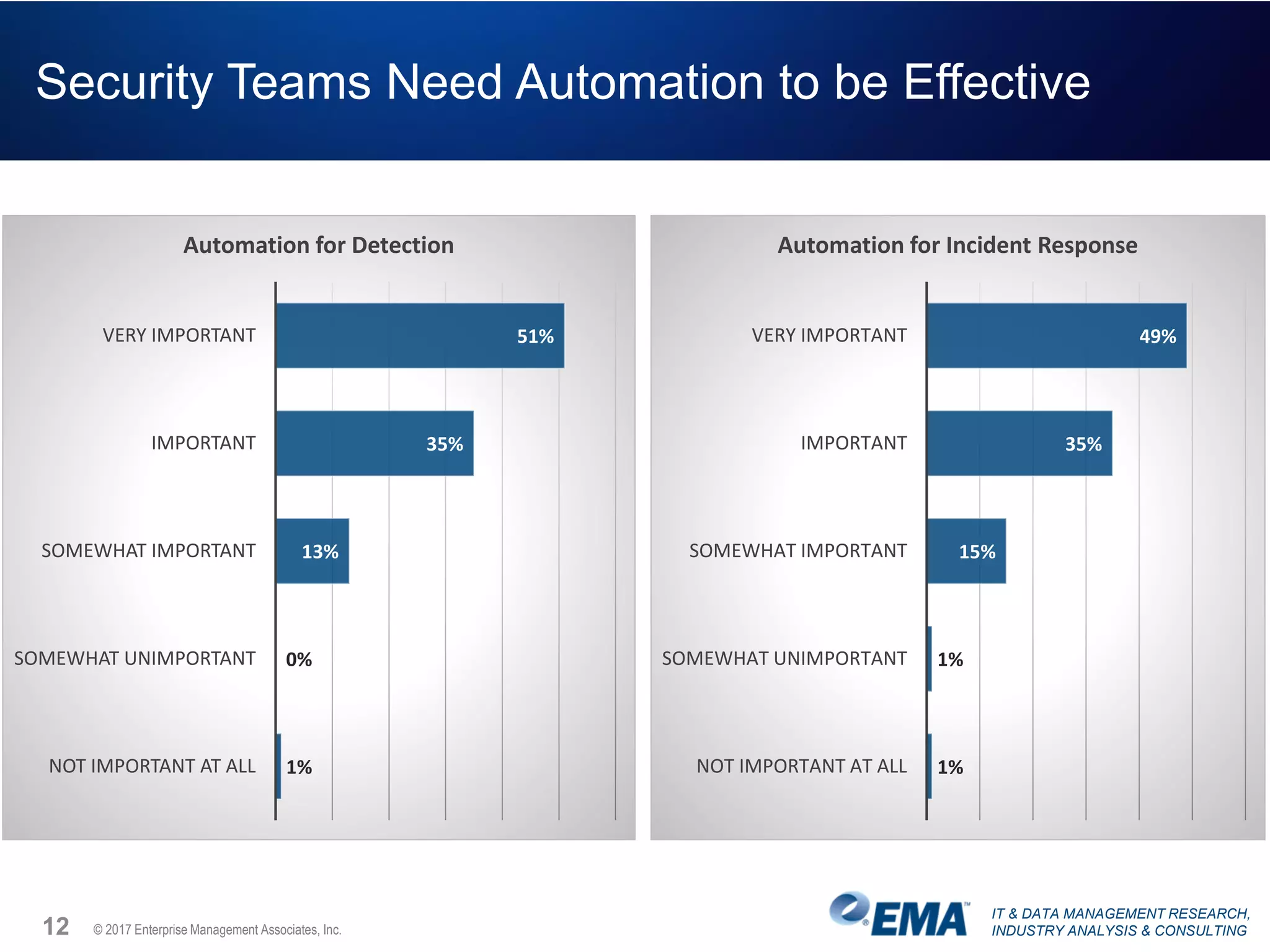
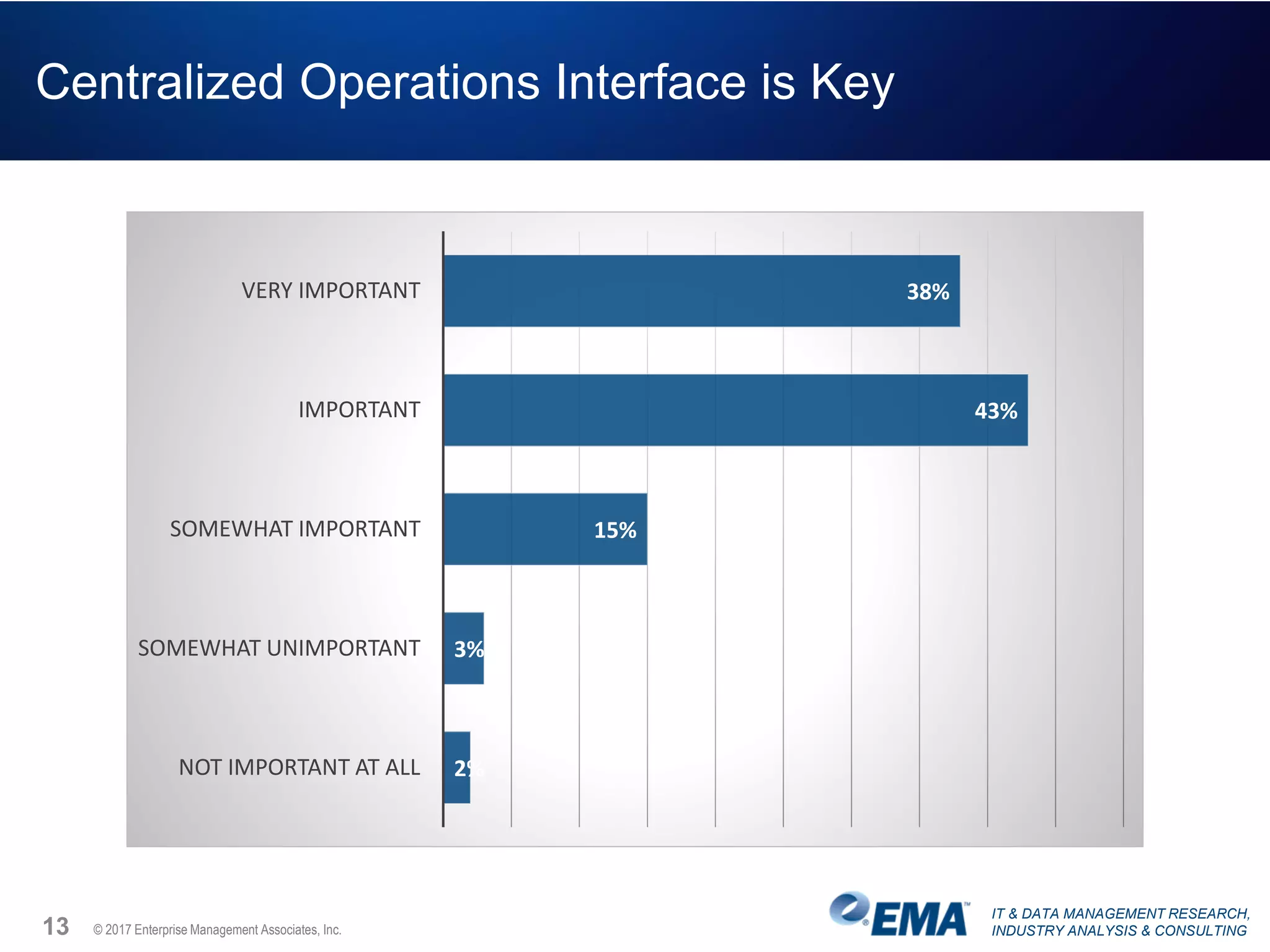
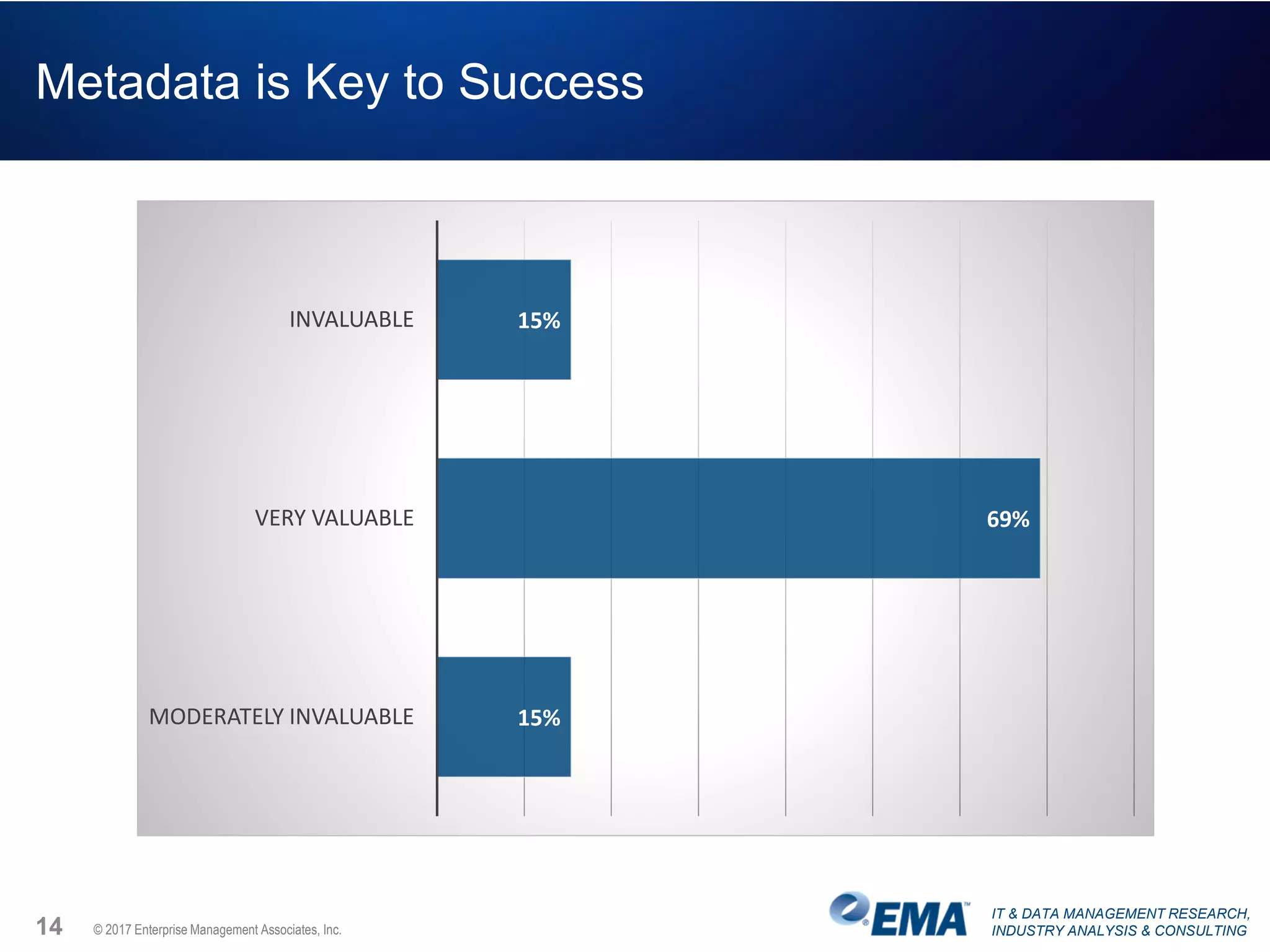
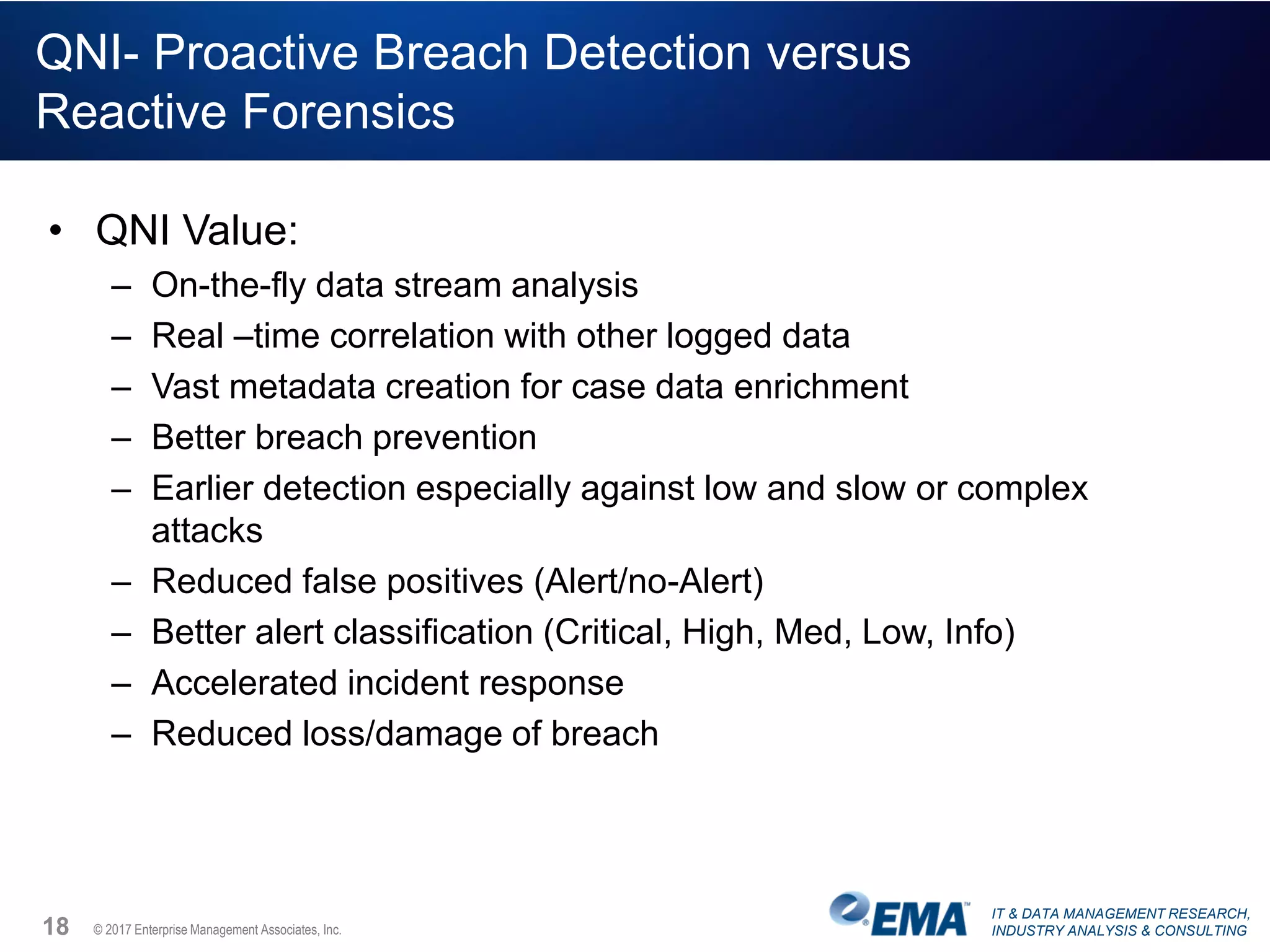
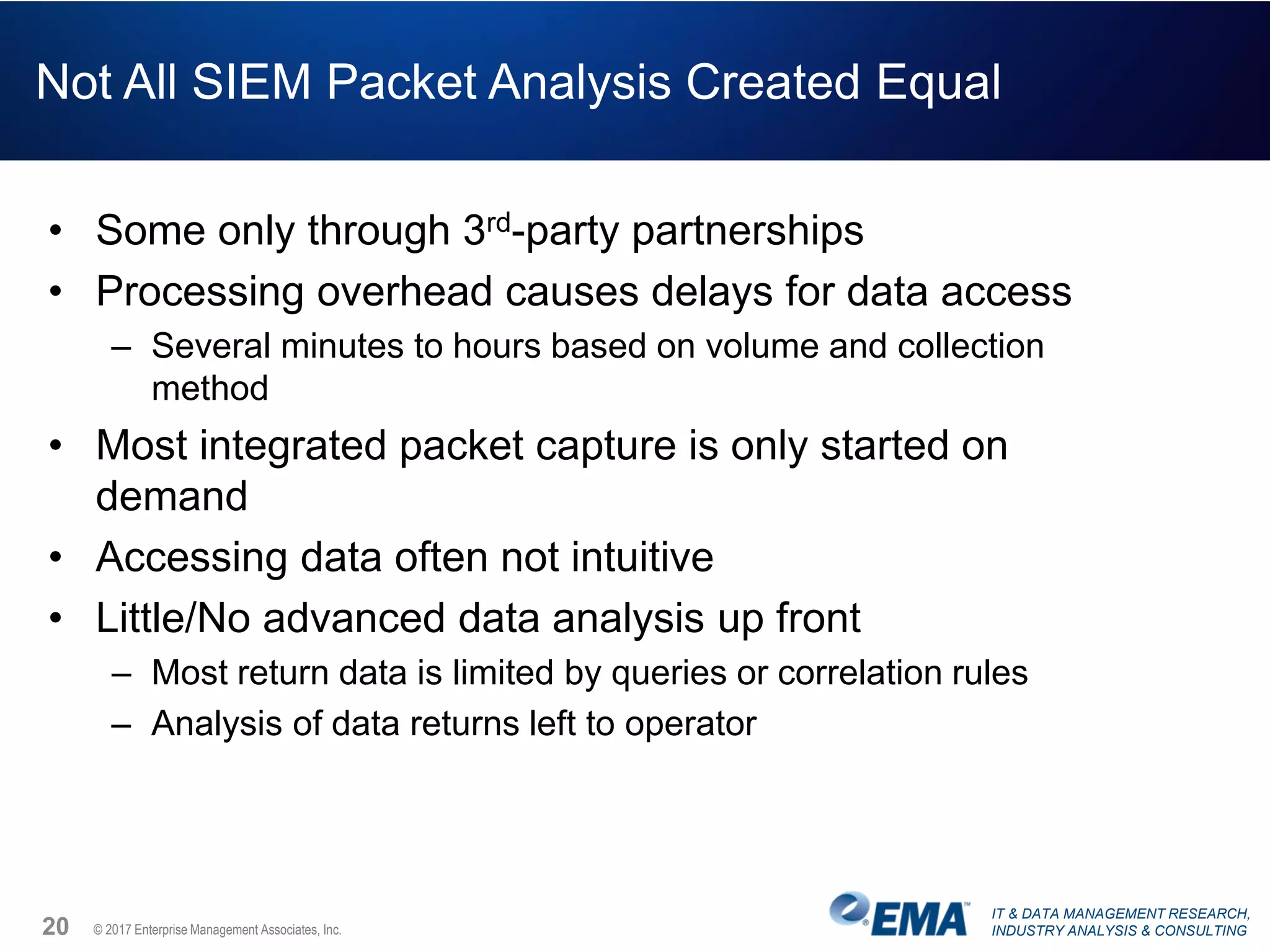
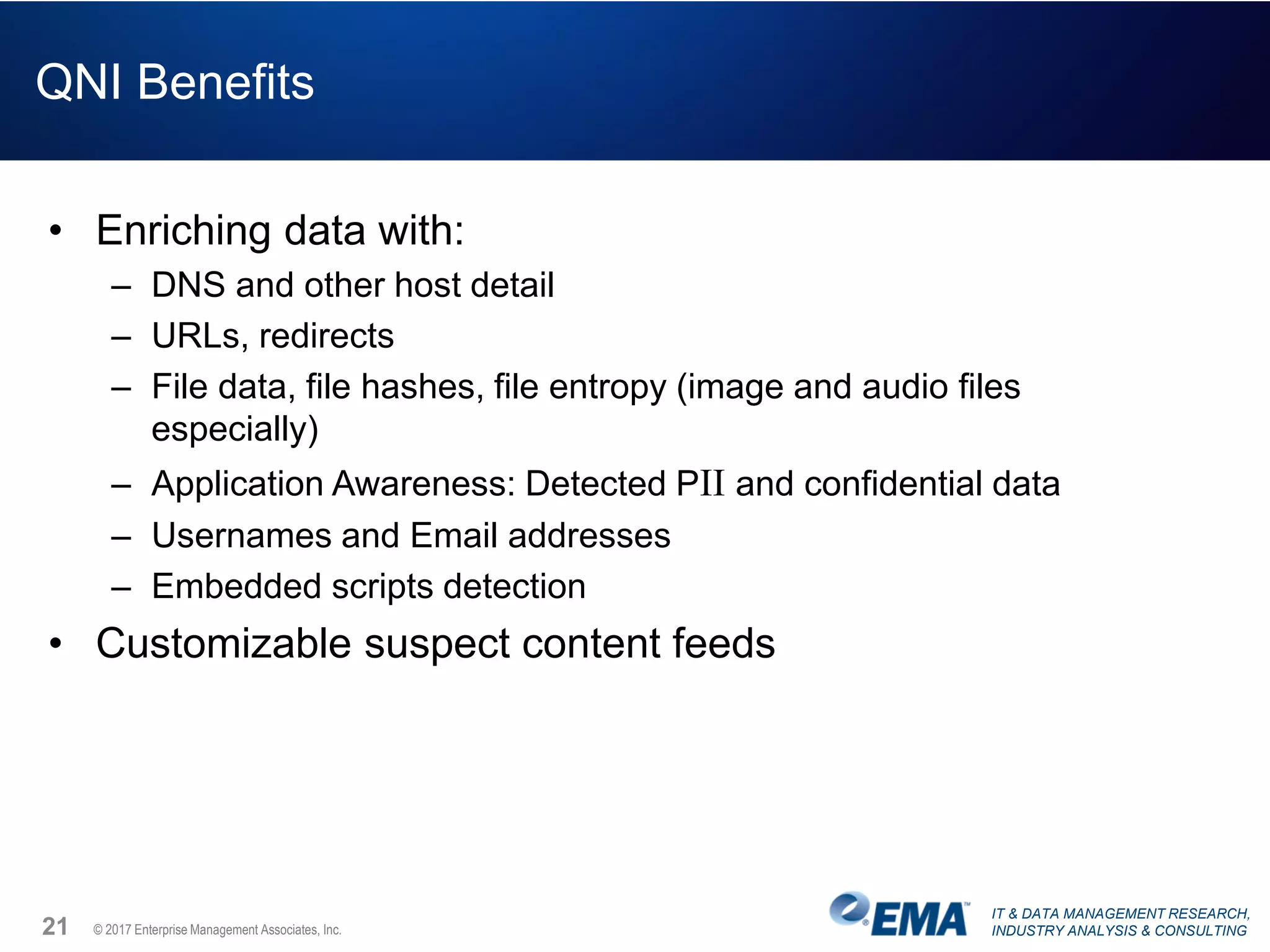
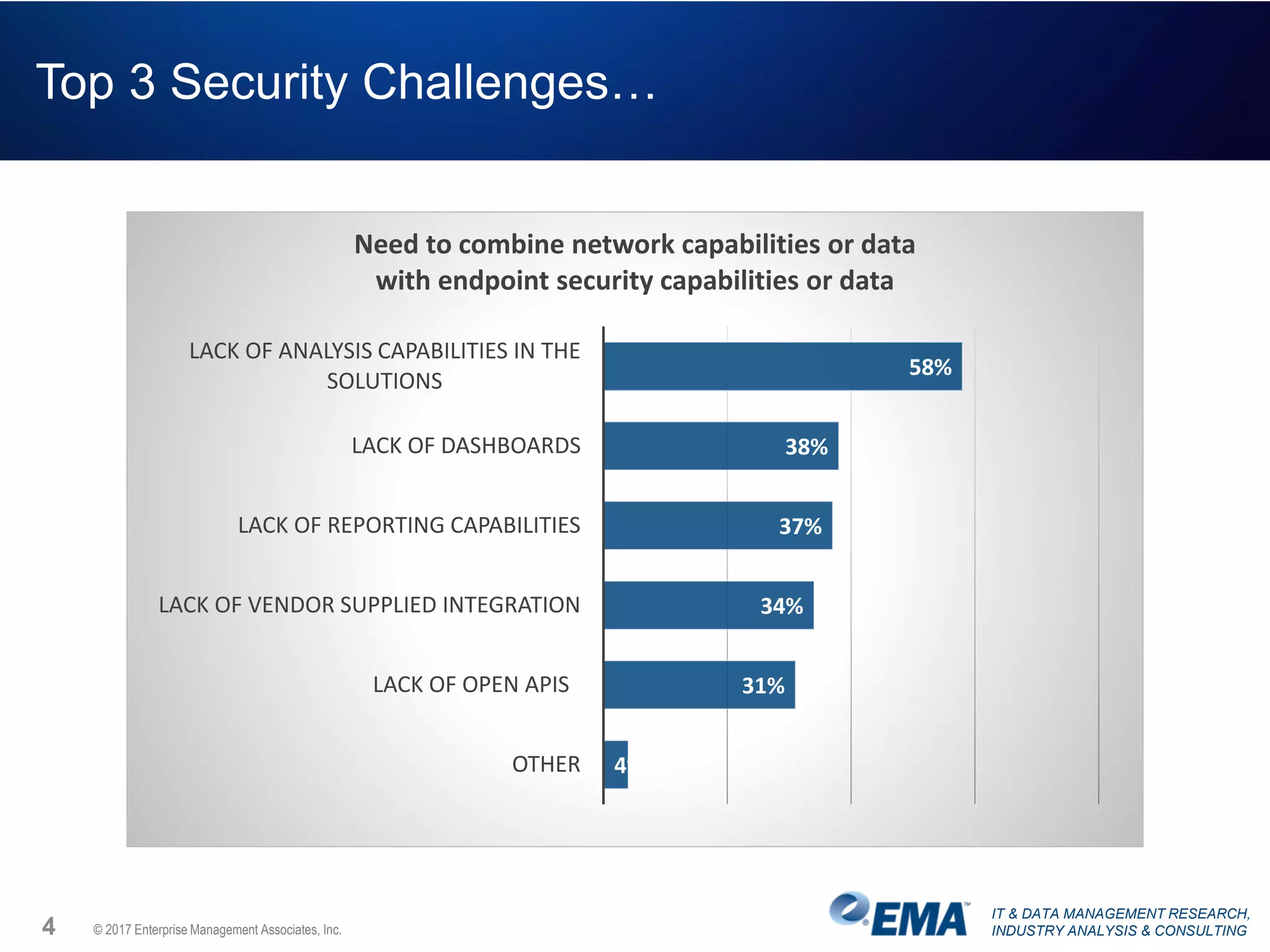
The document discusses the challenges faced by security teams in organizations, highlighting issues such as overwhelming alerts, lack of analysis capabilities, and insufficient skilled personnel. It emphasizes the need for automation and better data integration for timely breach detection and incident response. Additionally, it outlines the benefits of utilizing advanced data stream analysis for proactive breach detection and improved operational efficiency in security operations.



![IT & DATA MANAGEMENT RESEARCH,
INDUSTRY ANALYSIS & CONSULTING© 2017 Enterprise Management Associates, Inc.
More Context
• 92% of organizations receive as many as 500 overall alerts per
day
• 88% or organizations receive as many as 500 severe/critical
alerts/day
MEANING: Most incidents are being classified as severe/critical
CAUSE: A lack of context [data] to properly prioritize the events
Result: Attacks cannot be properly prioritized
• 67% of organizations can only investigate <=10 severe/critical
events/day
• 88% of organizations can only investigate <=25 severe/critical
events/day.
MEANING: Most incidents are not being investigated
CAUSE: A lack of context [data] to properly prioritize the events.
Result: Attacks are going unidentified/uninvestgated
5](https://image.slidesharecdn.com/emaanalystsecuritywebinarjan2017-170222224317/75/Where-There-Is-Smoke-There-is-Fire-Extracting-Actionable-Intelligence-from-Network-Traffic-with-Real-Time-Analysis-5-2048.jpg)