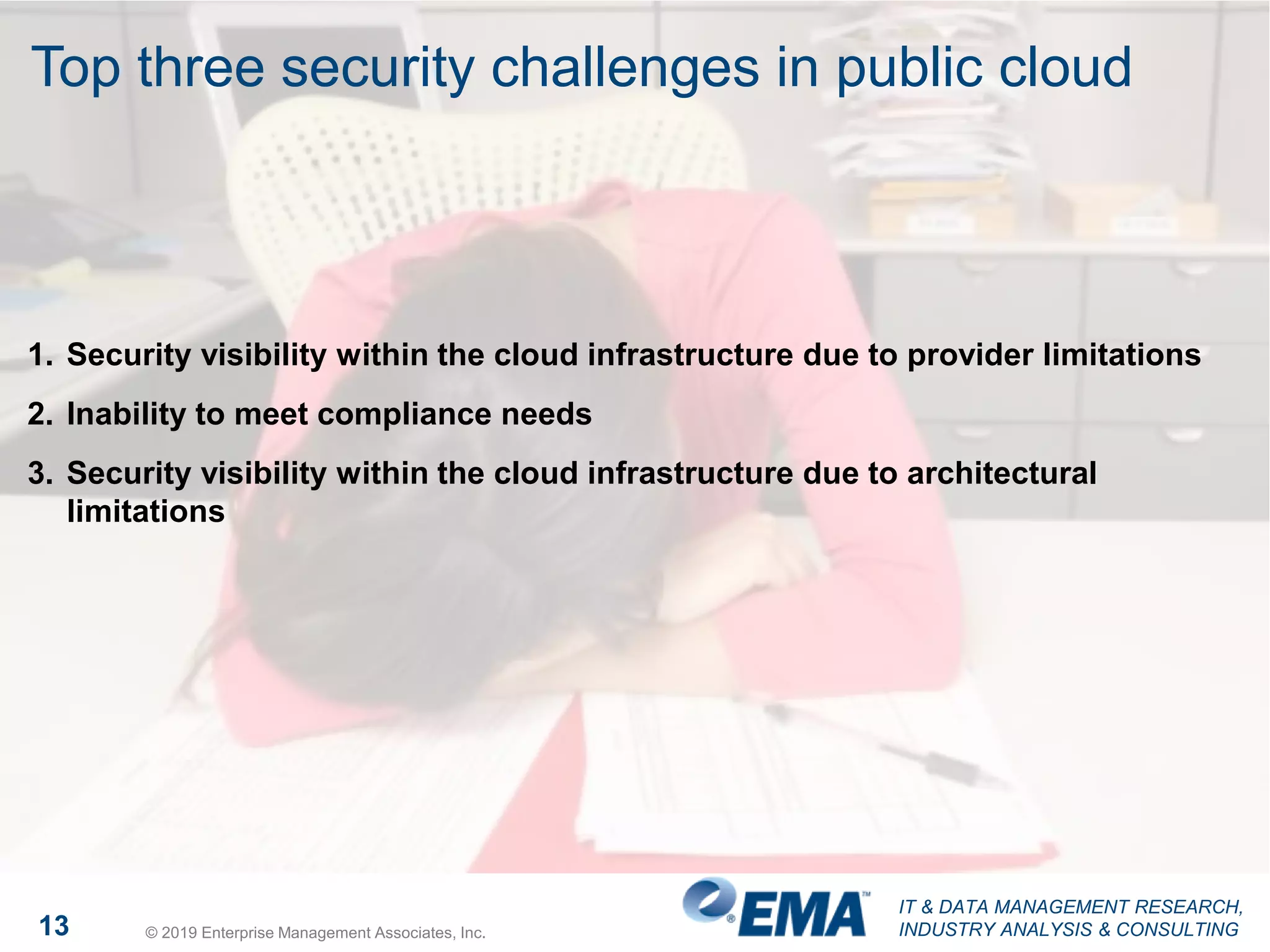
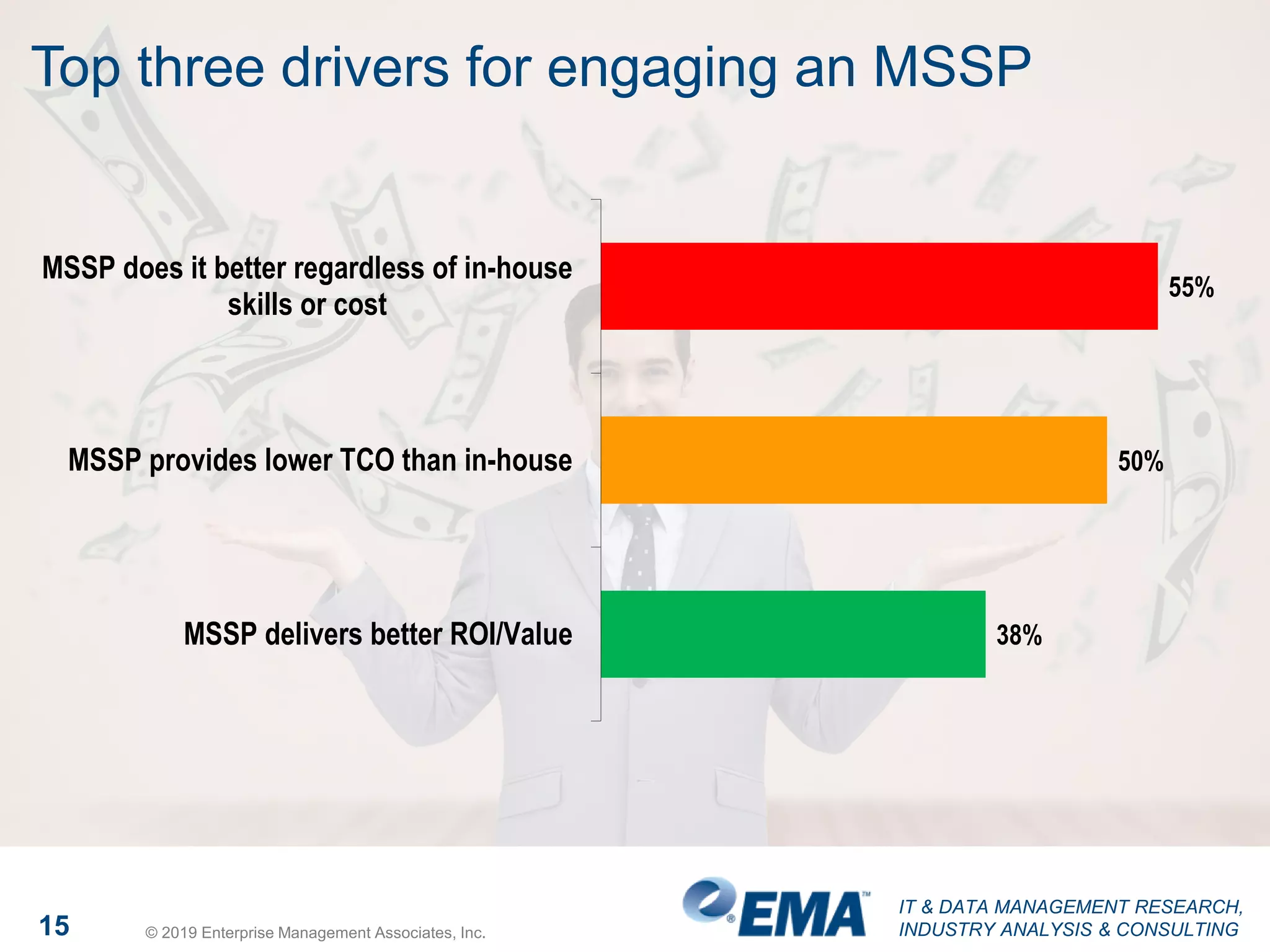
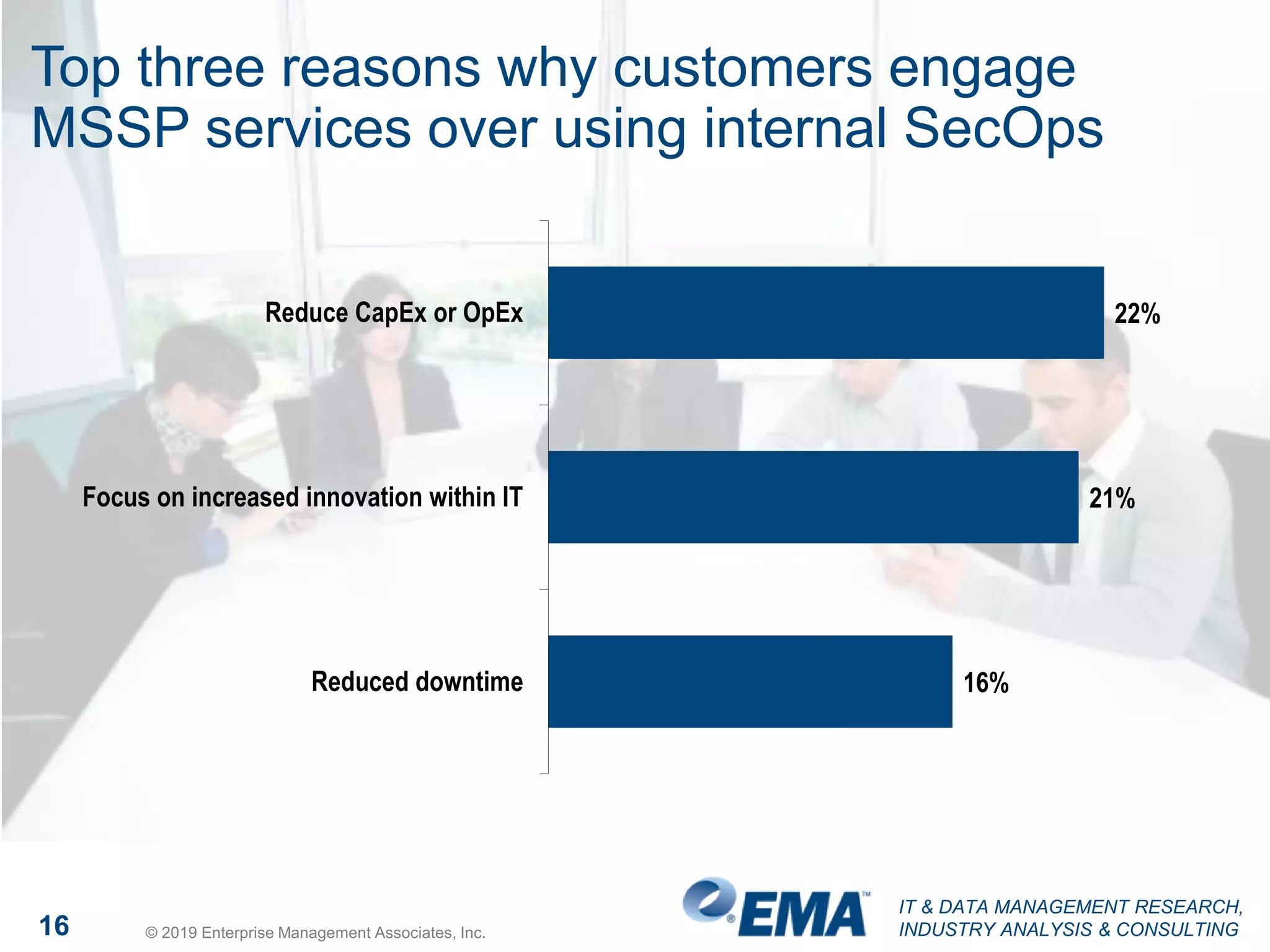
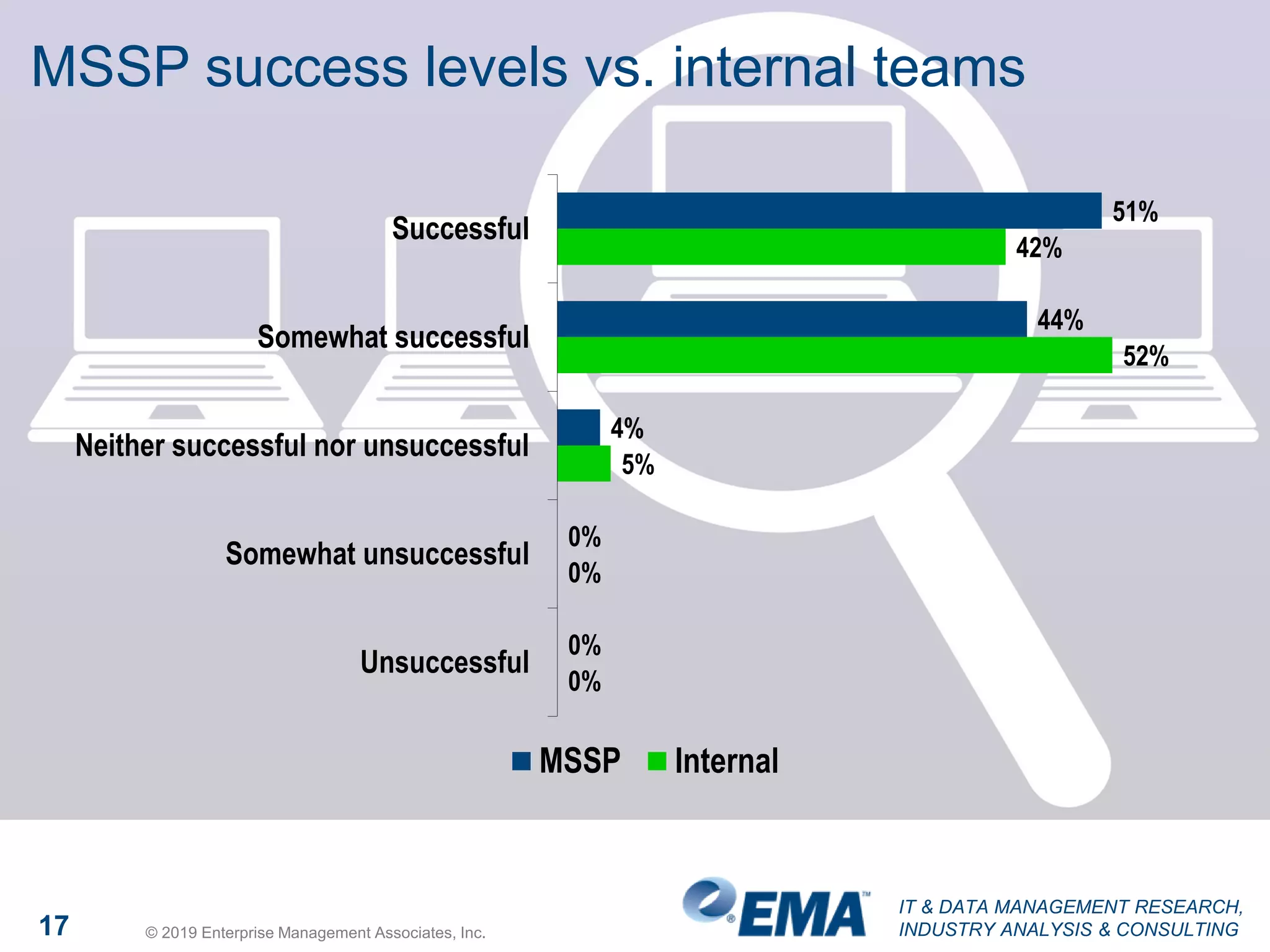
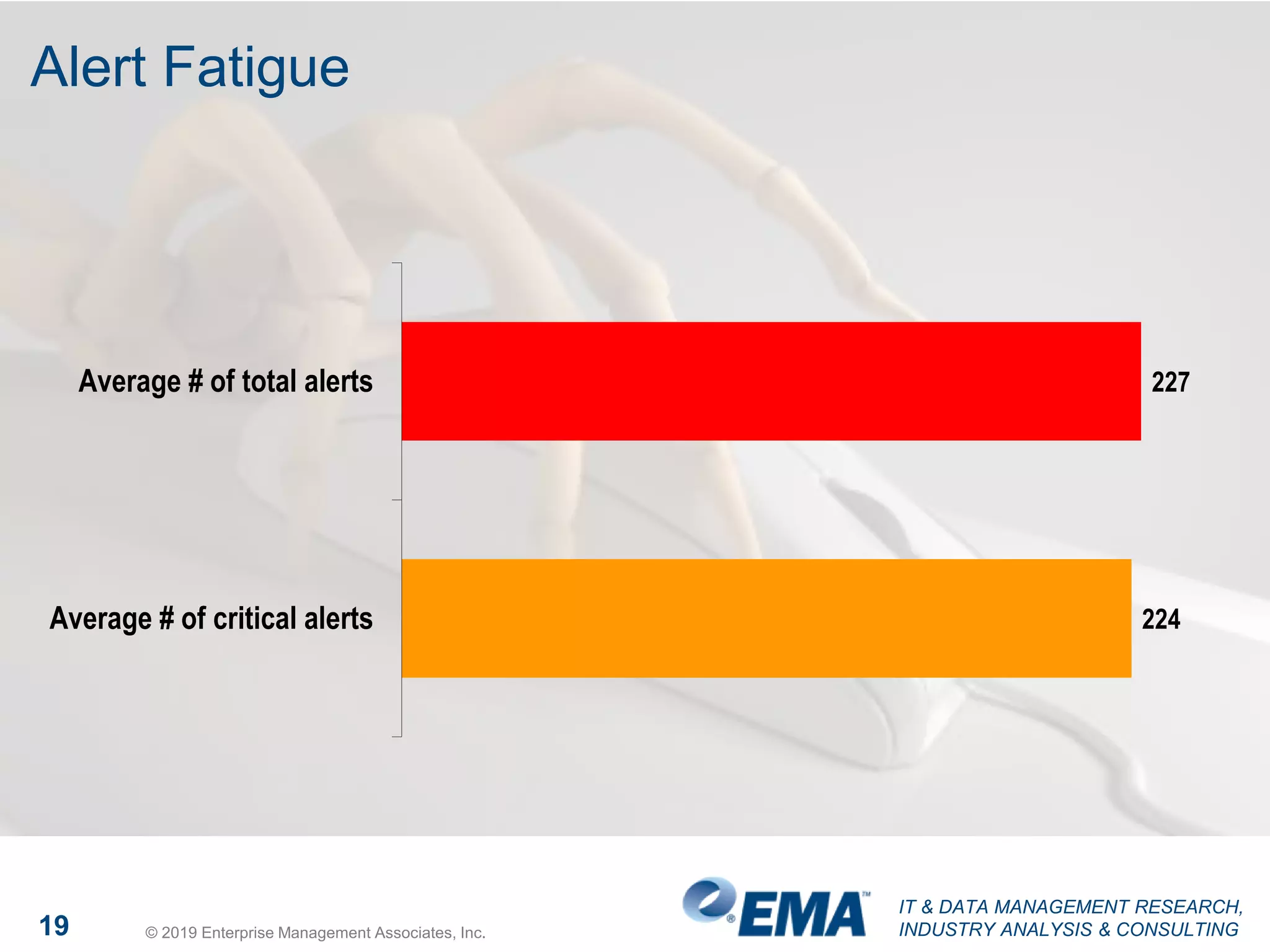
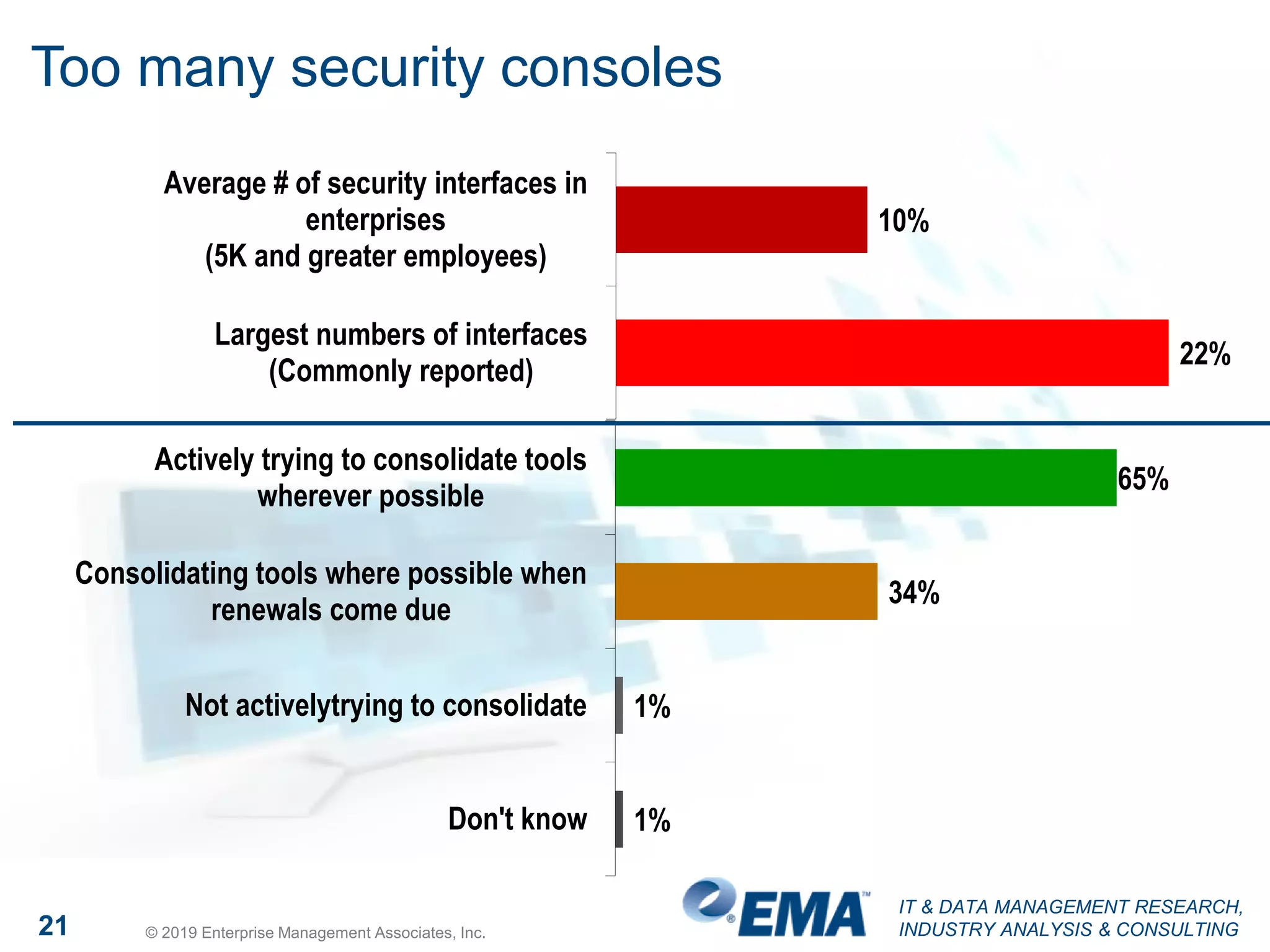
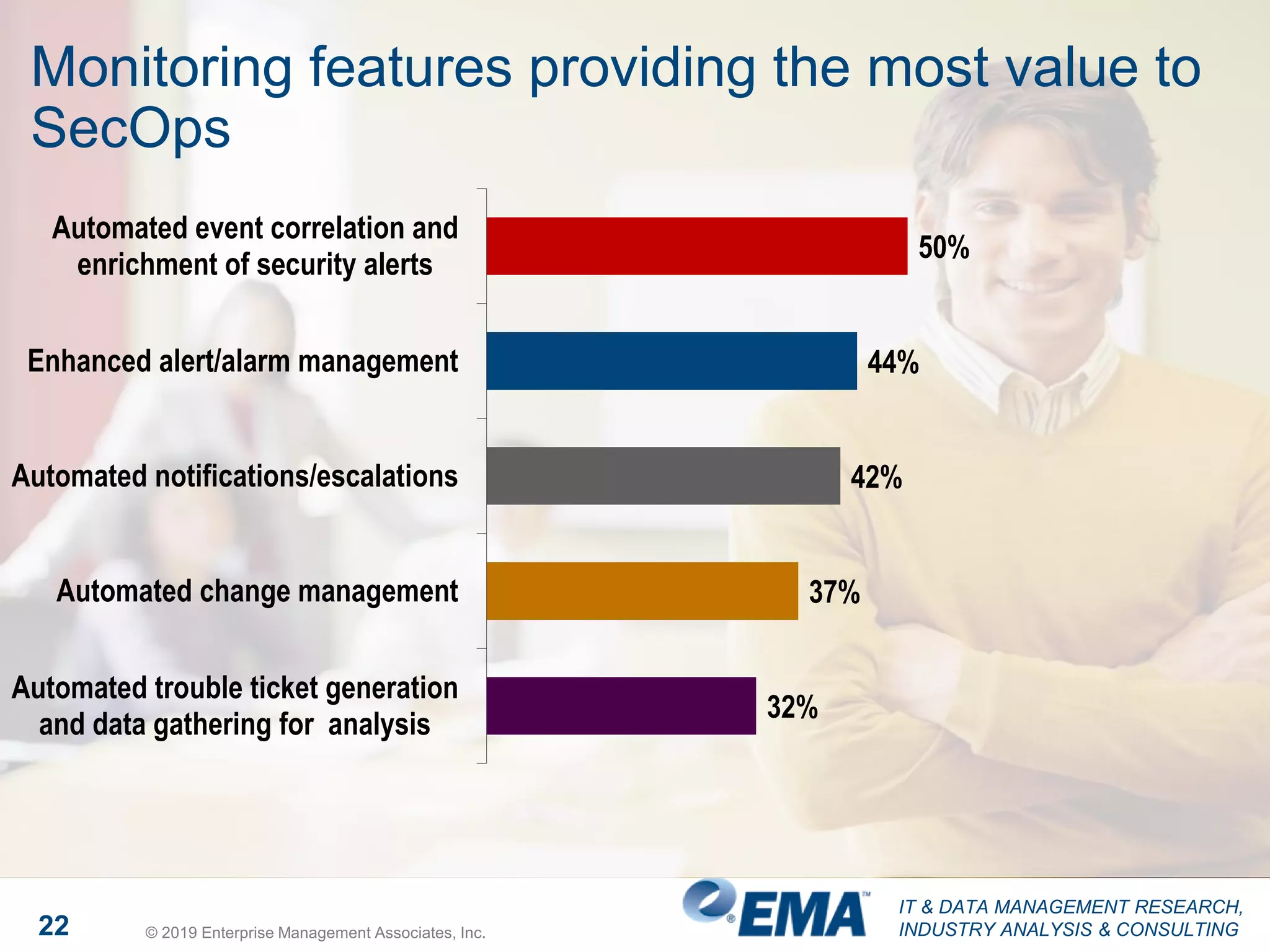
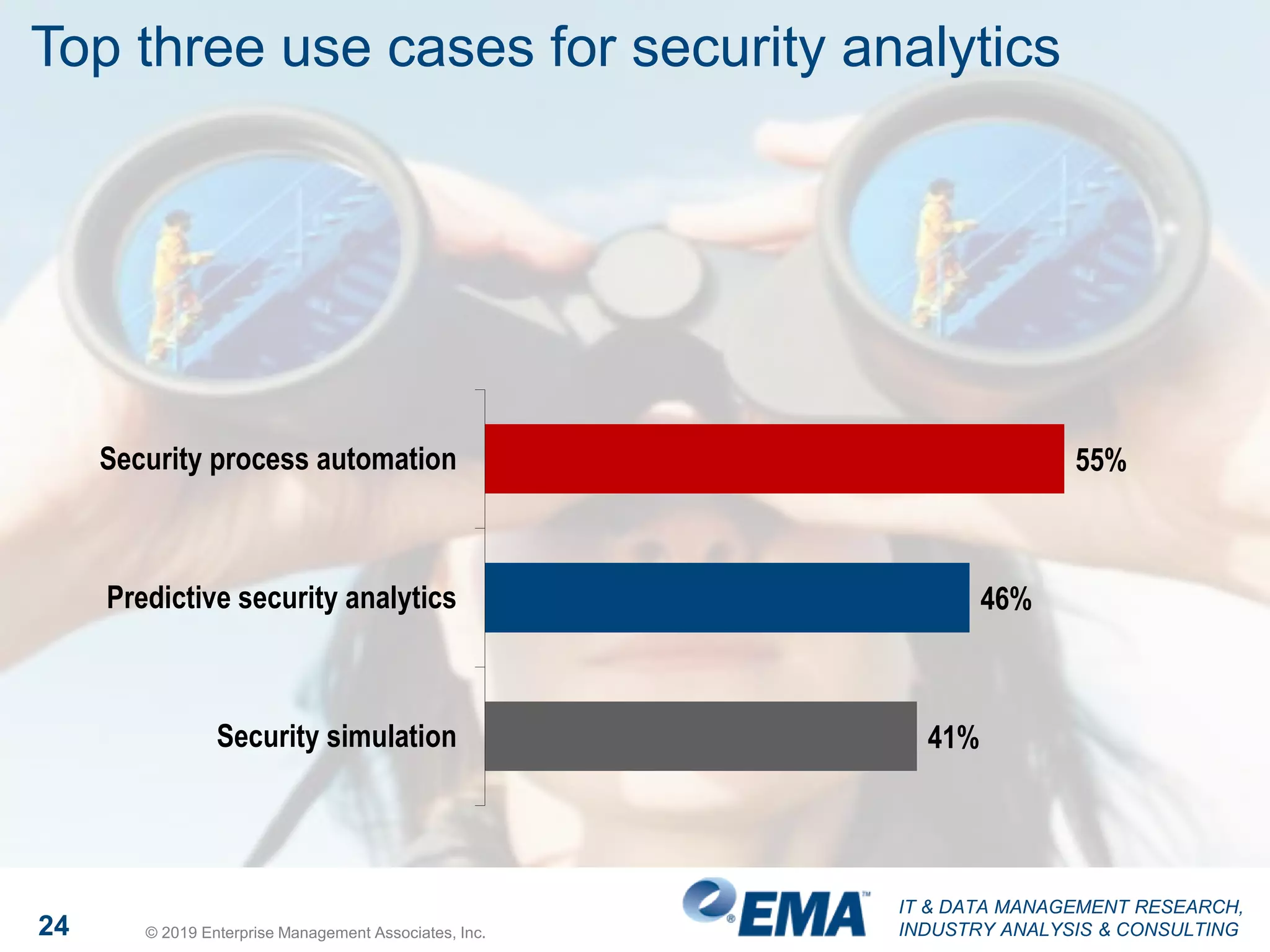
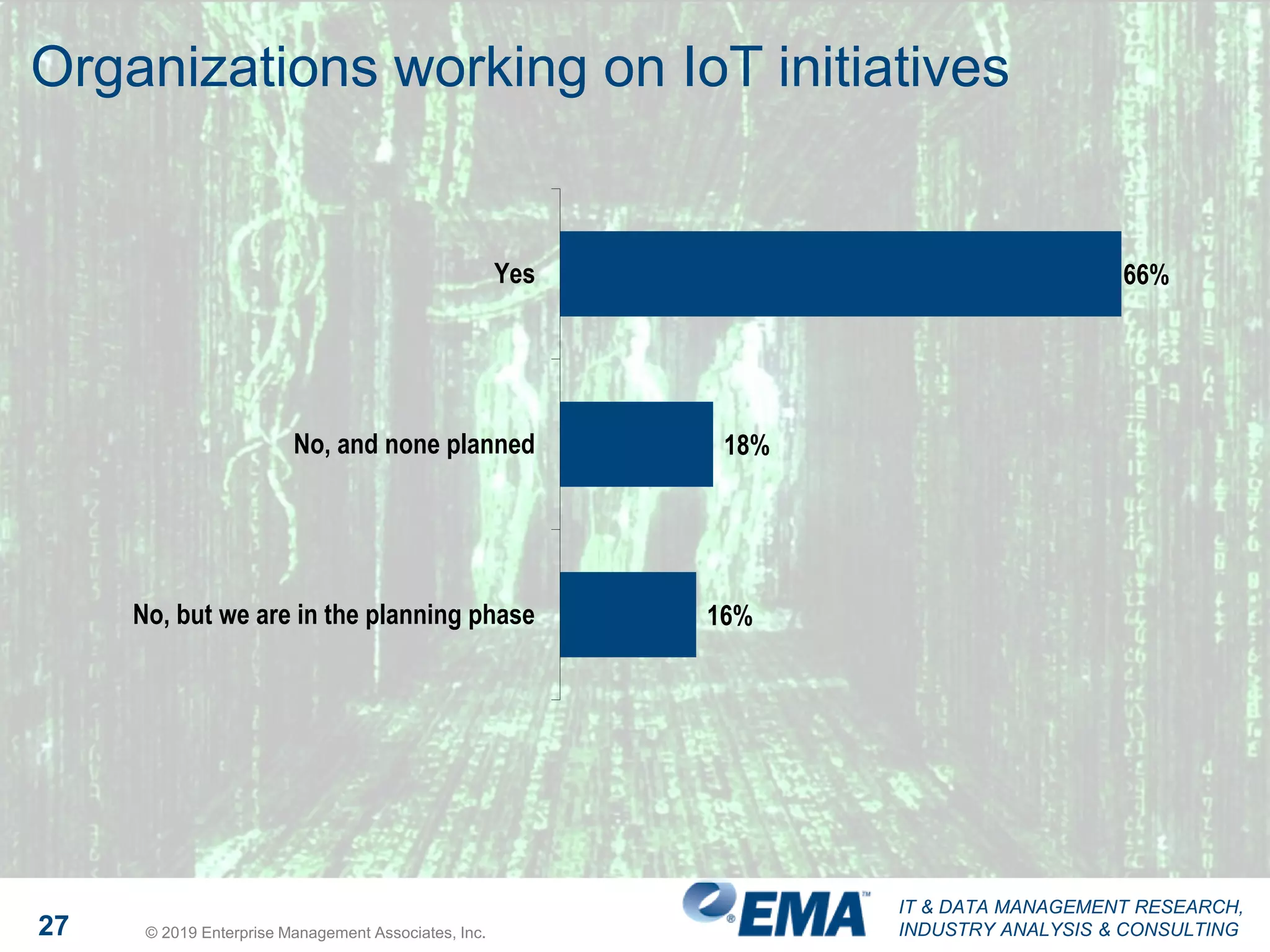
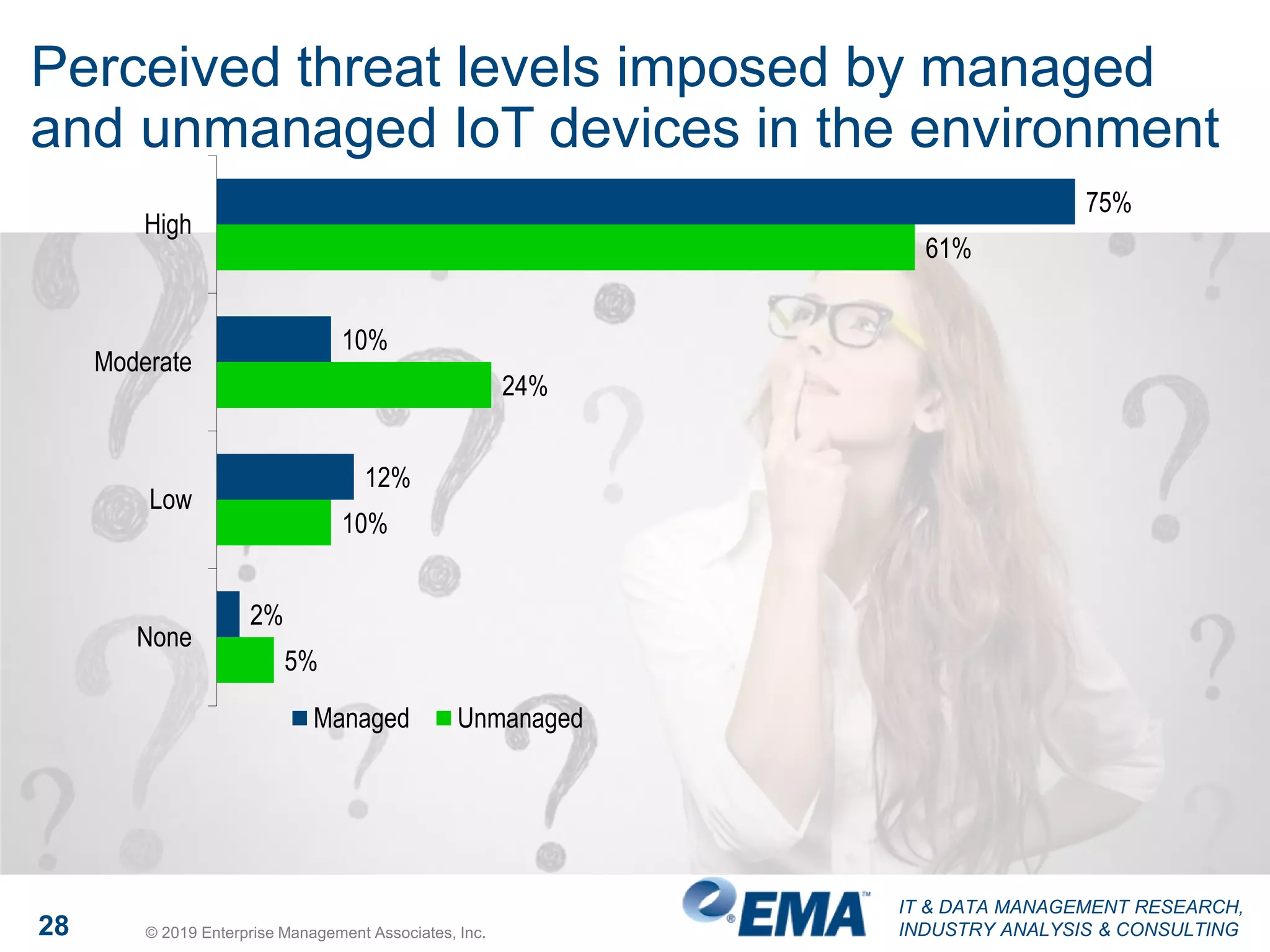
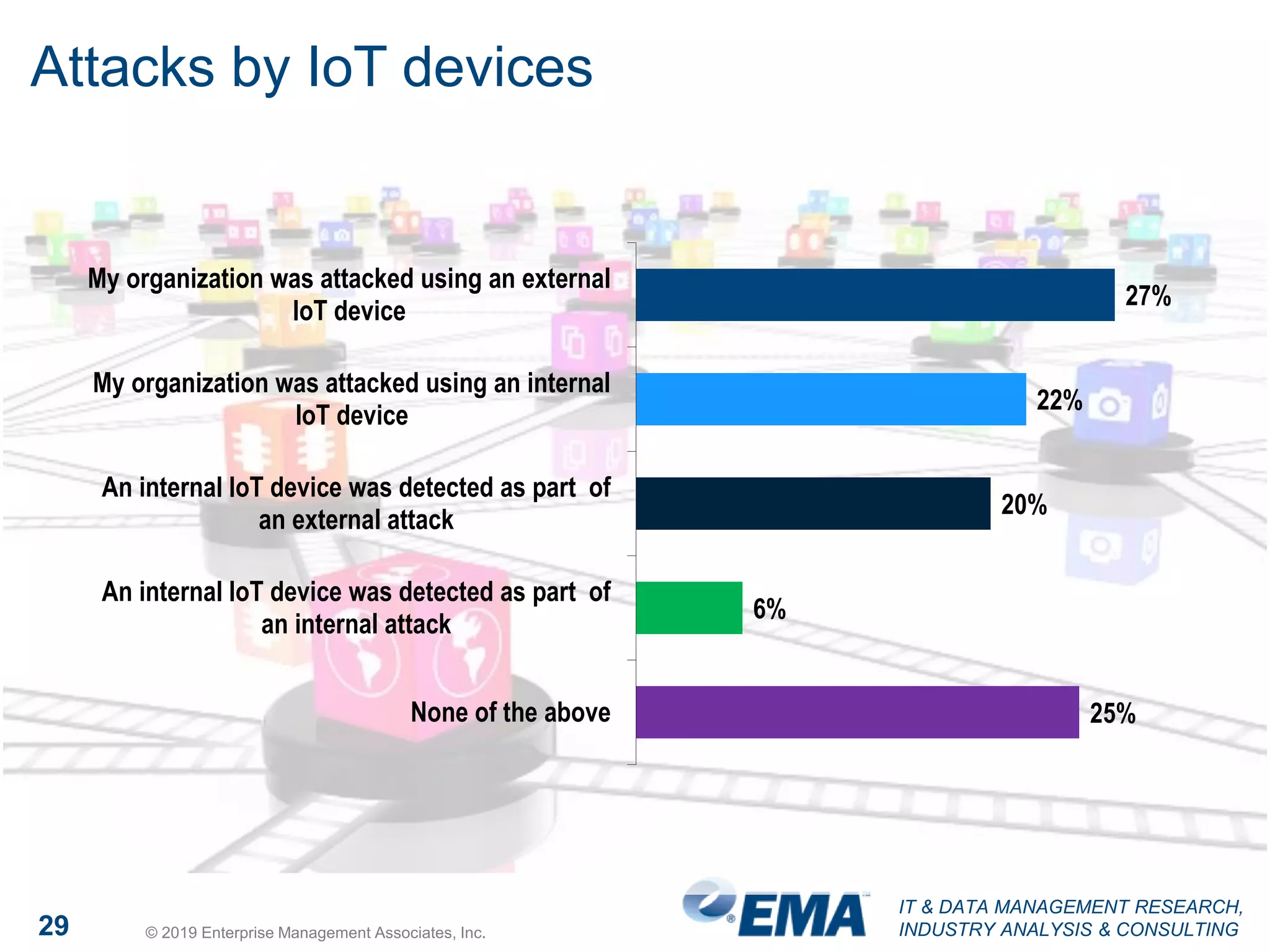
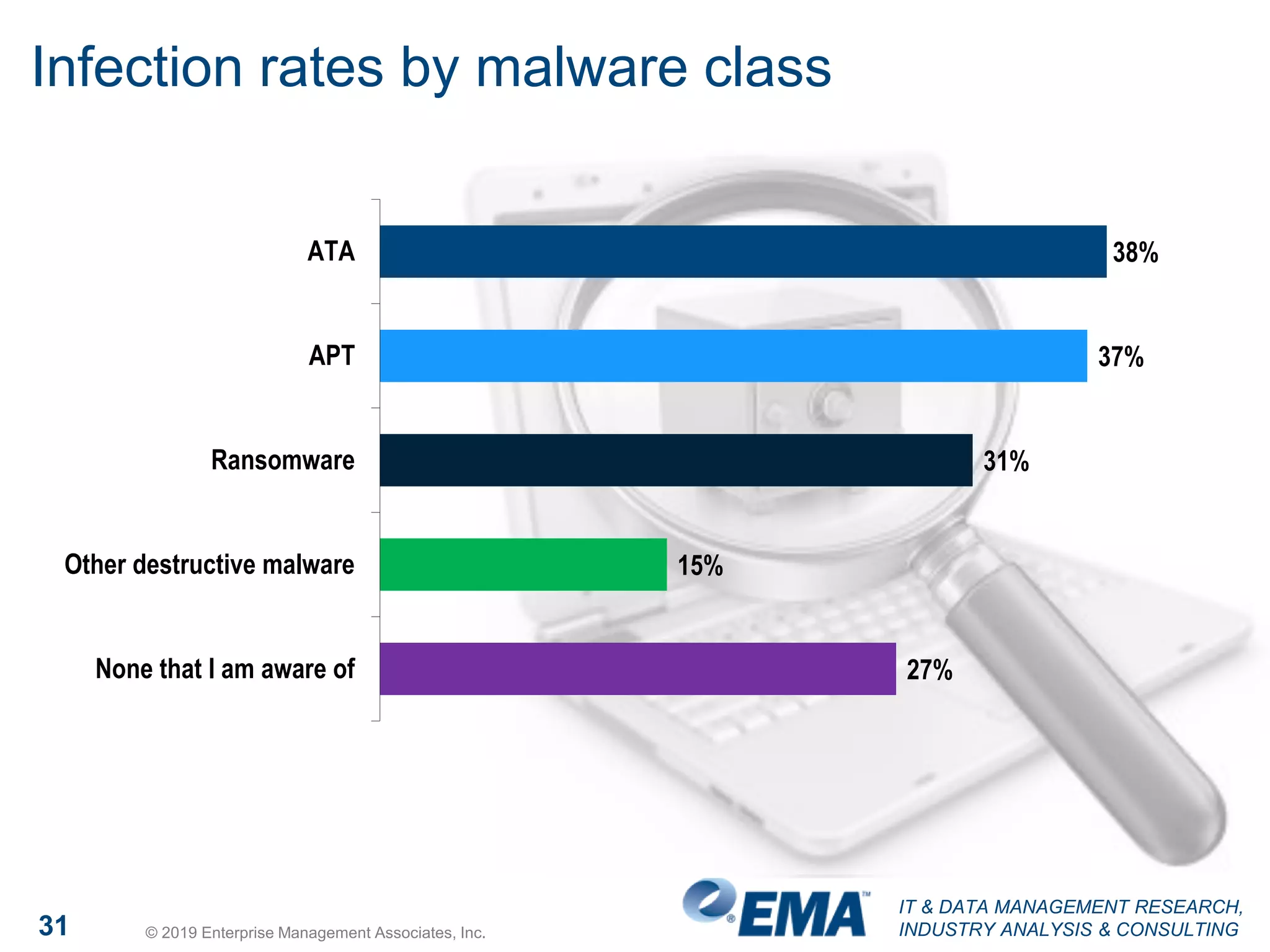
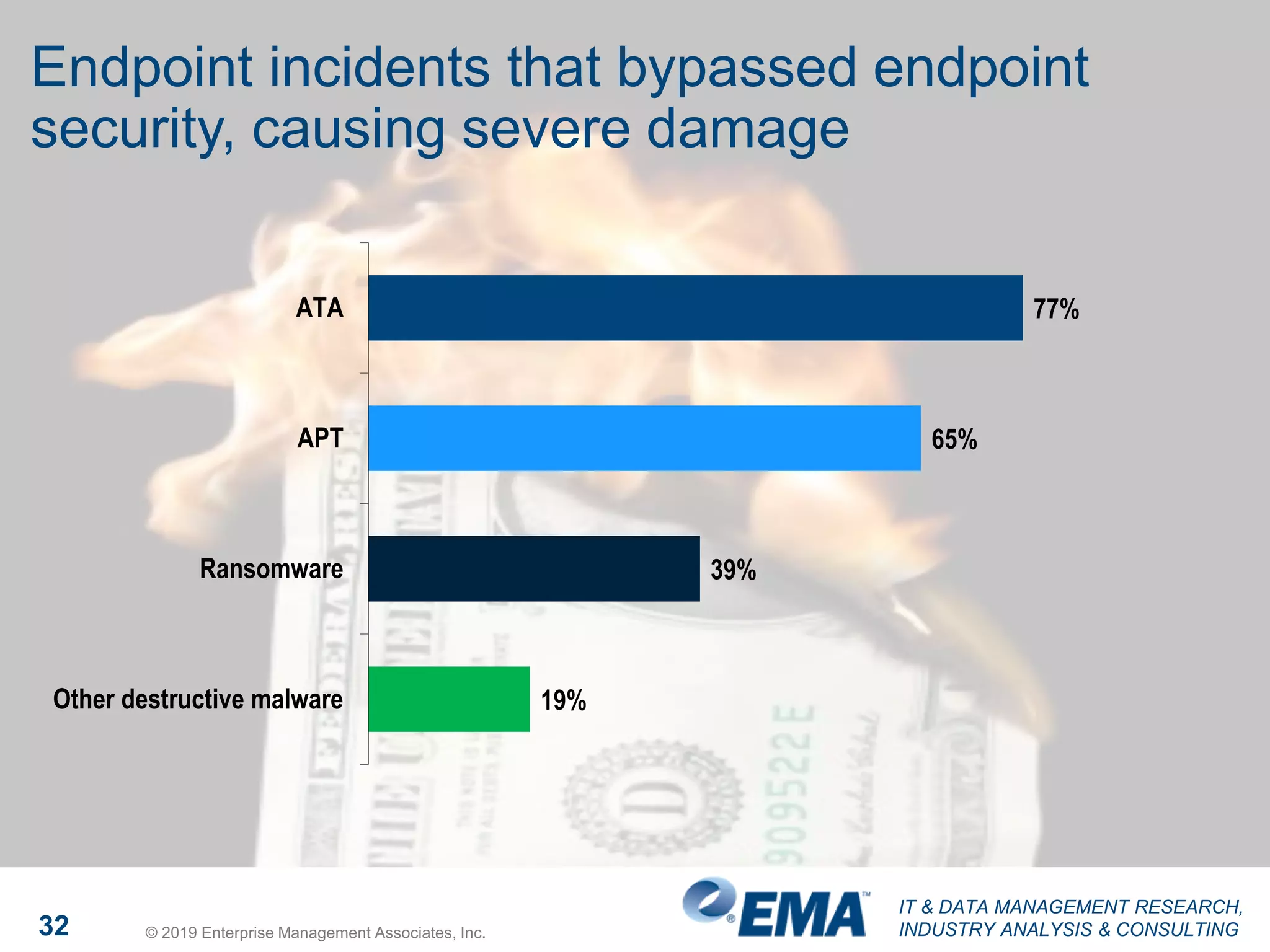
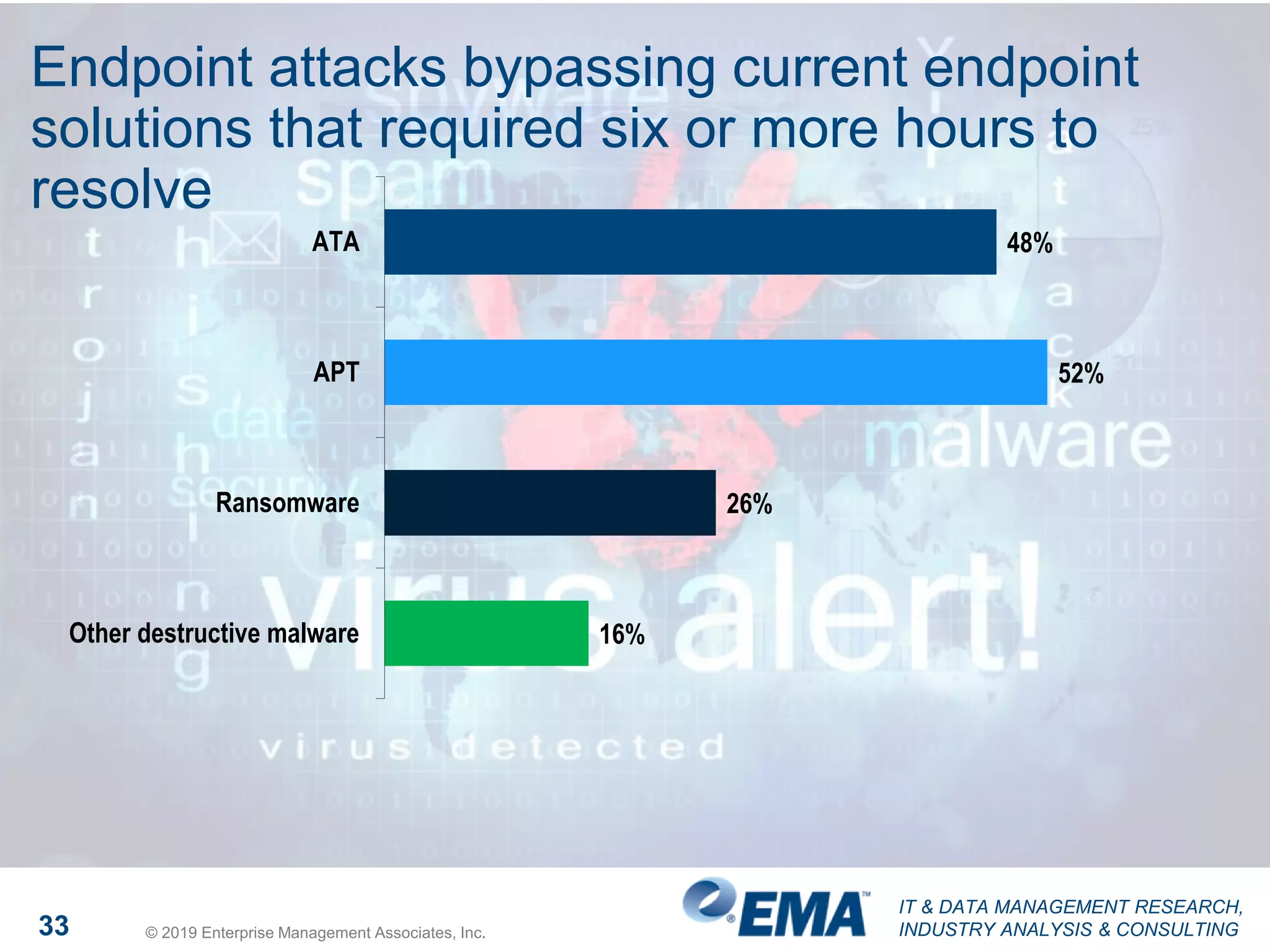
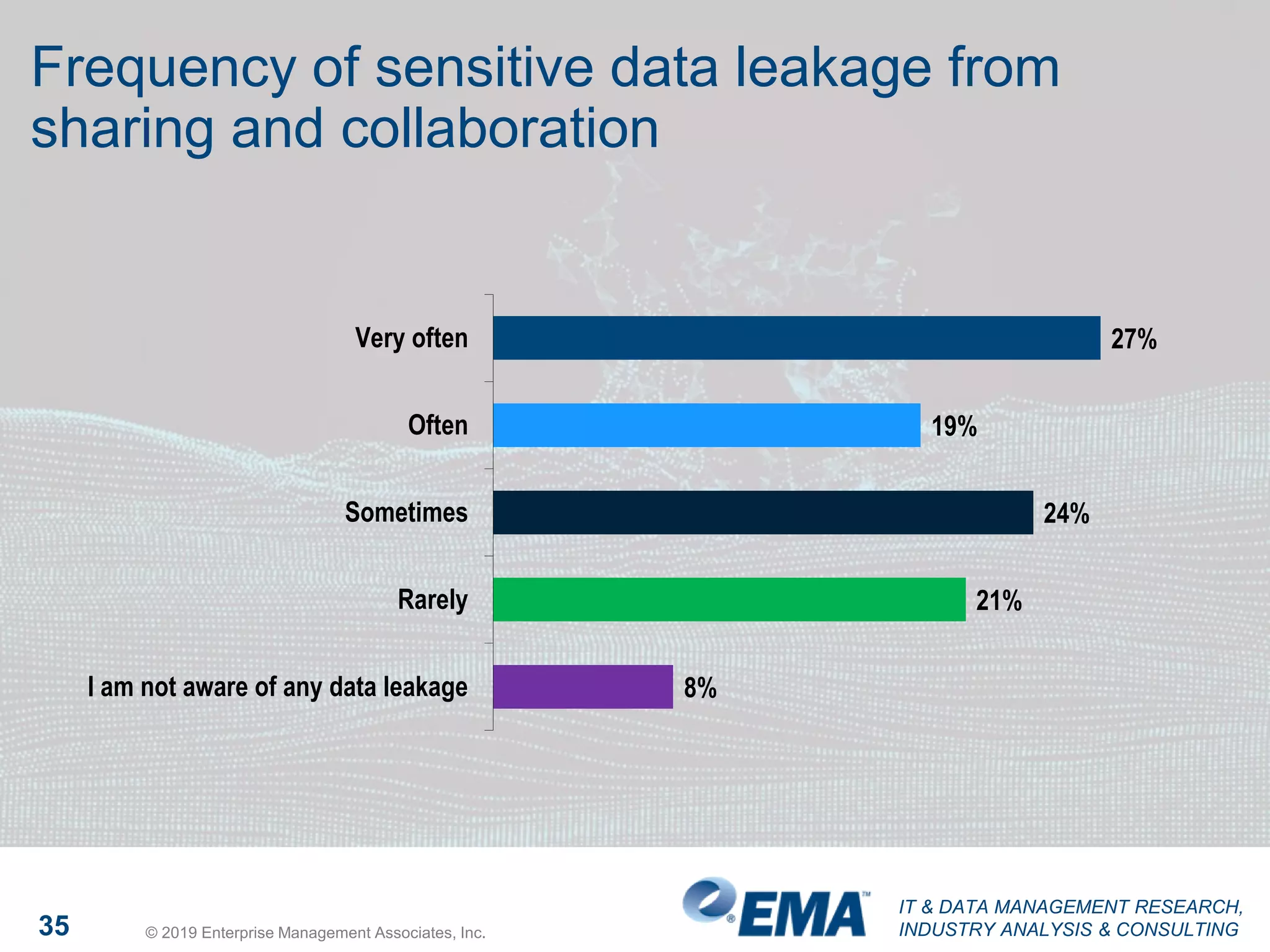
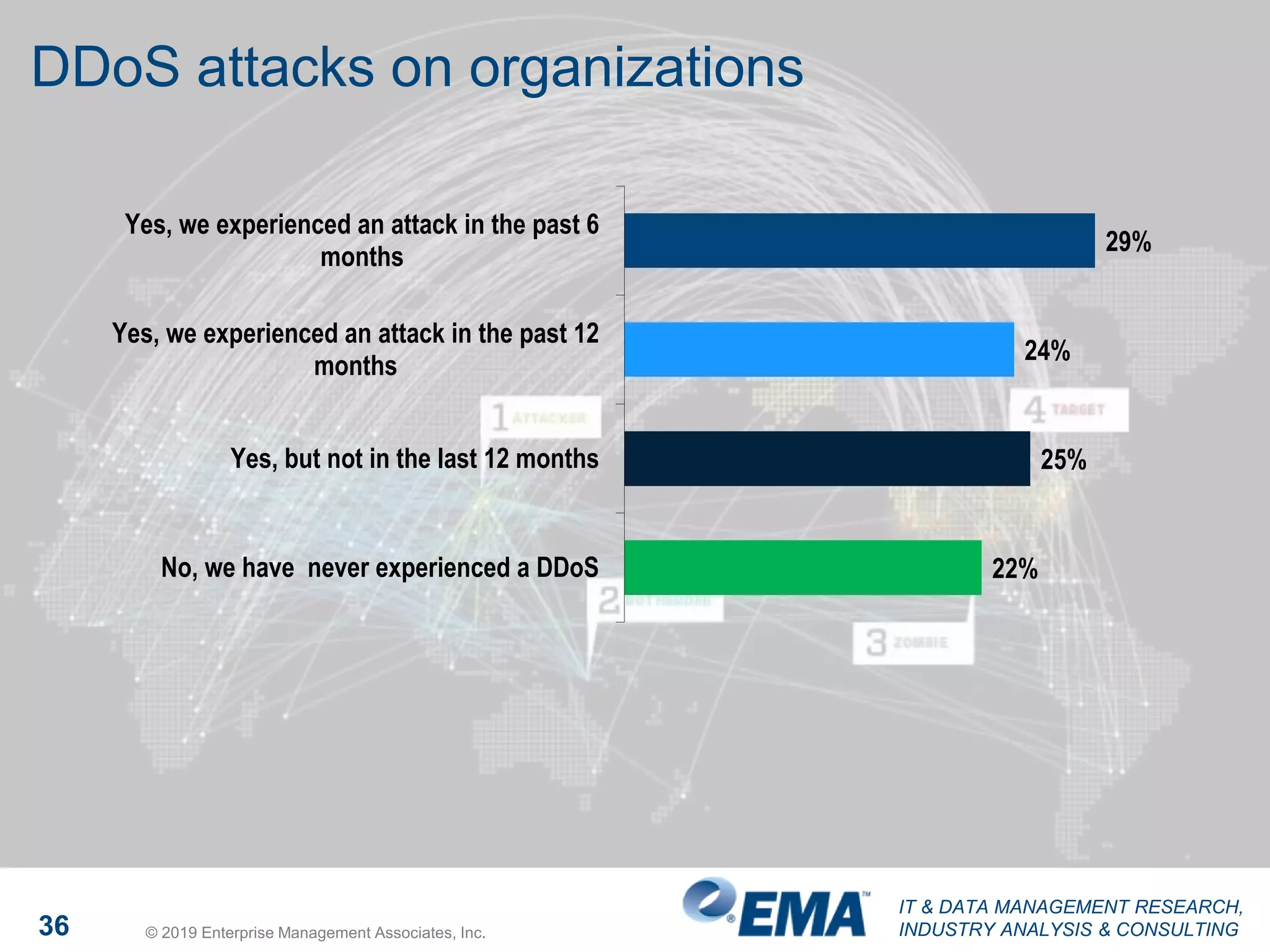
The document presents findings from a research study focused on cyber-security trends, featuring insights from 250 North American respondents, primarily from director-level positions in various industries. Key highlights include the critical security challenges organizations face, the adoption of managed security service providers (MSSPs), and the importance of cloud security monitoring. Additionally, the document addresses the impact of emerging technologies like AI and IoT on security practices and the operational impediments to effective security analytics.







![IT & DATA MANAGEMENT RESEARCH,
INDUSTRY ANALYSIS & CONSULTING12 © 2019 Enterprise Management Associates, Inc.
Many cloud consumers [errantly] believe the
cloud providers are responsible for security
53%
21%
15%
All or majority provider-owned
Shared equally
All or majority customer-owned](https://image.slidesharecdn.com/emasecuritymegatrends2019-190507145613/75/EMA-Megatrends-in-Cyber-Security-12-2048.jpg)