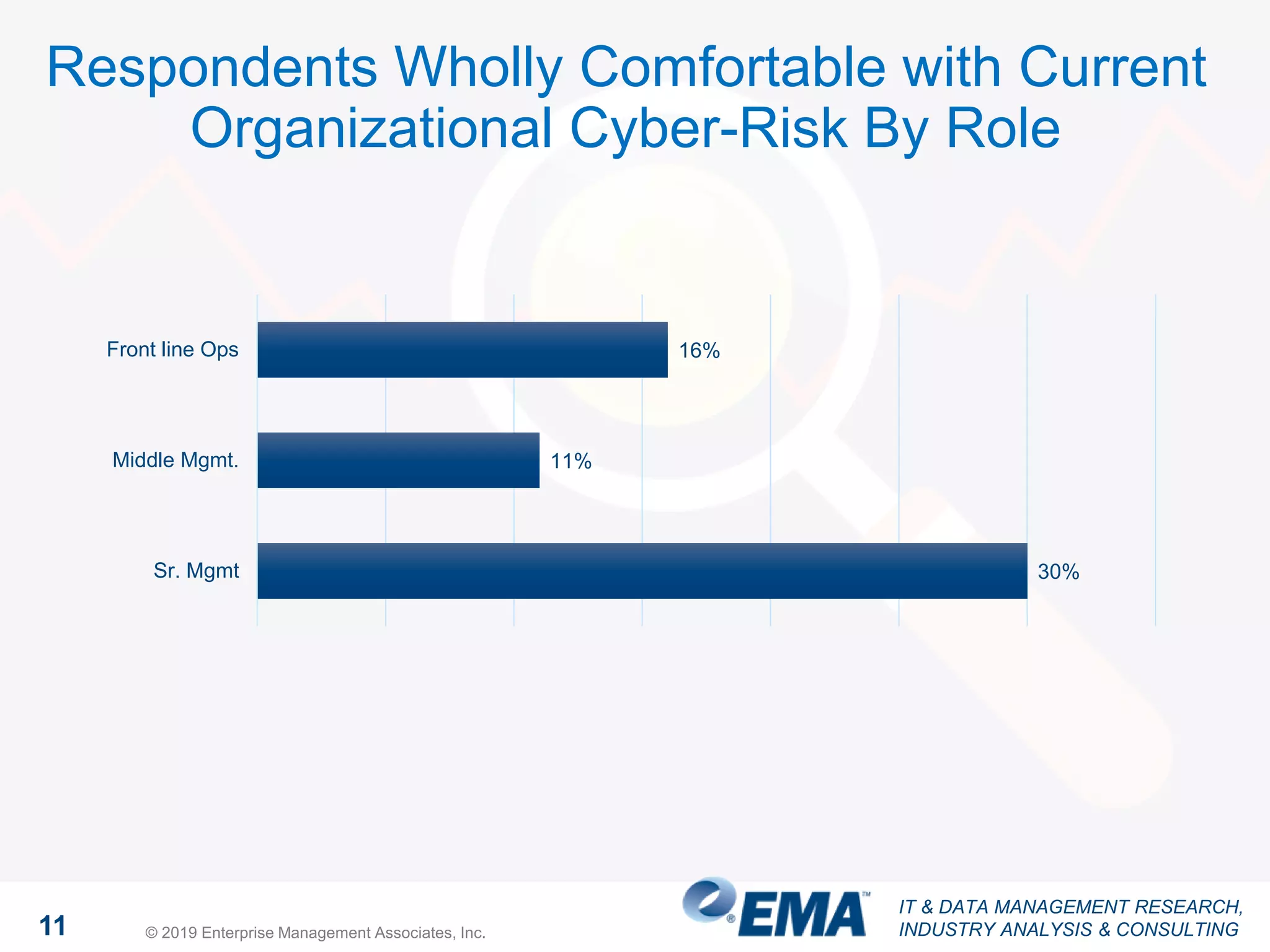
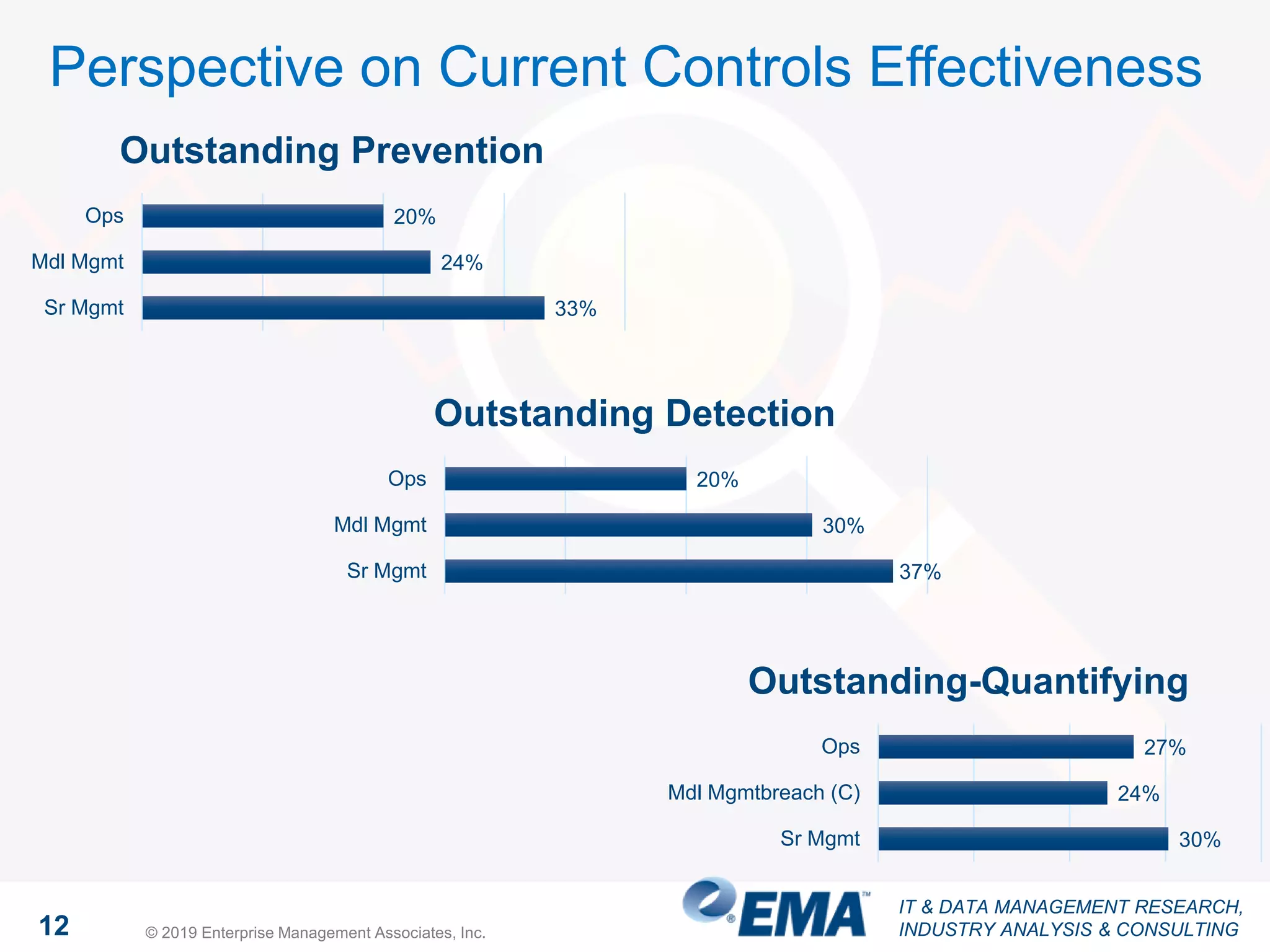
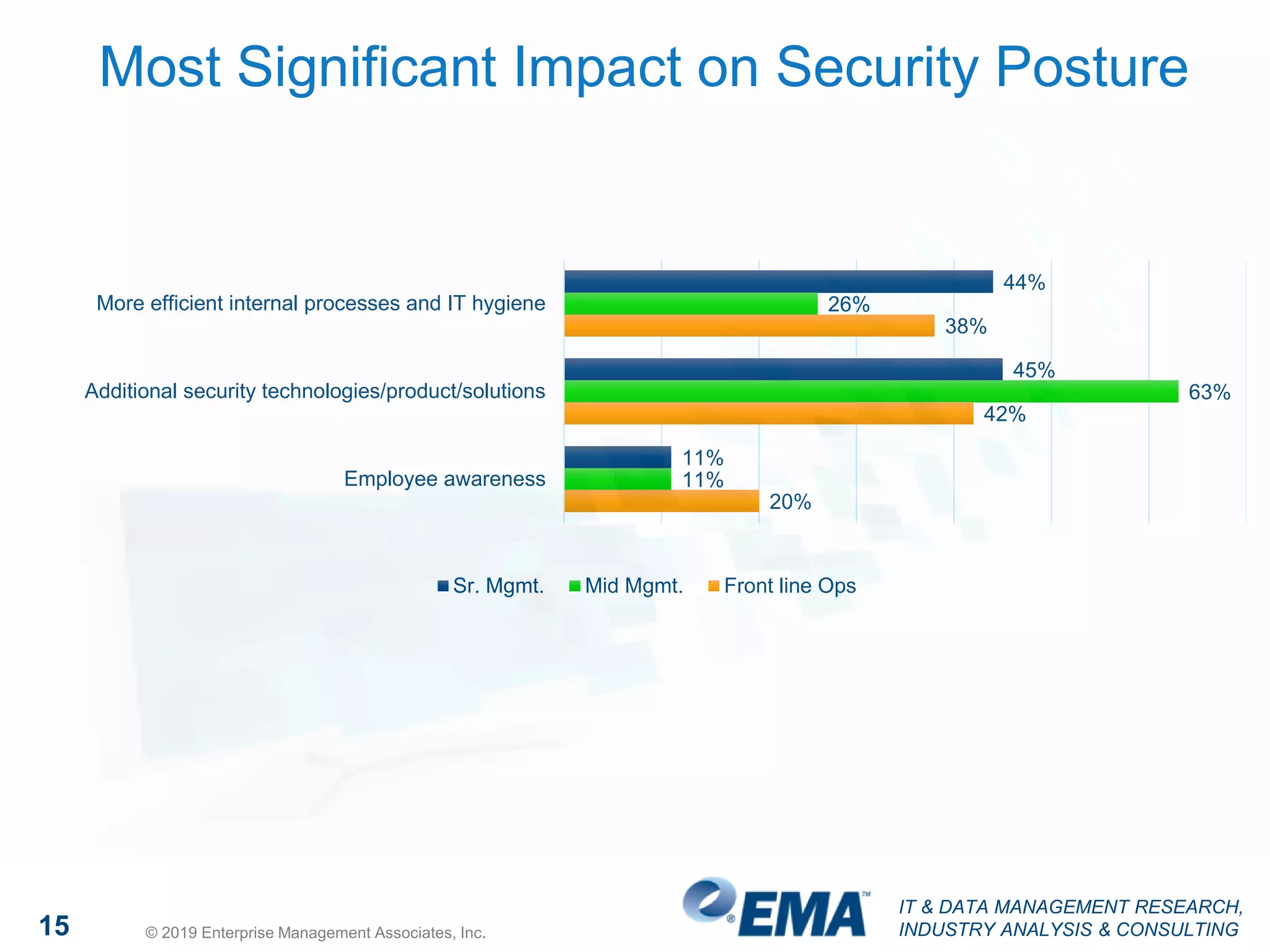
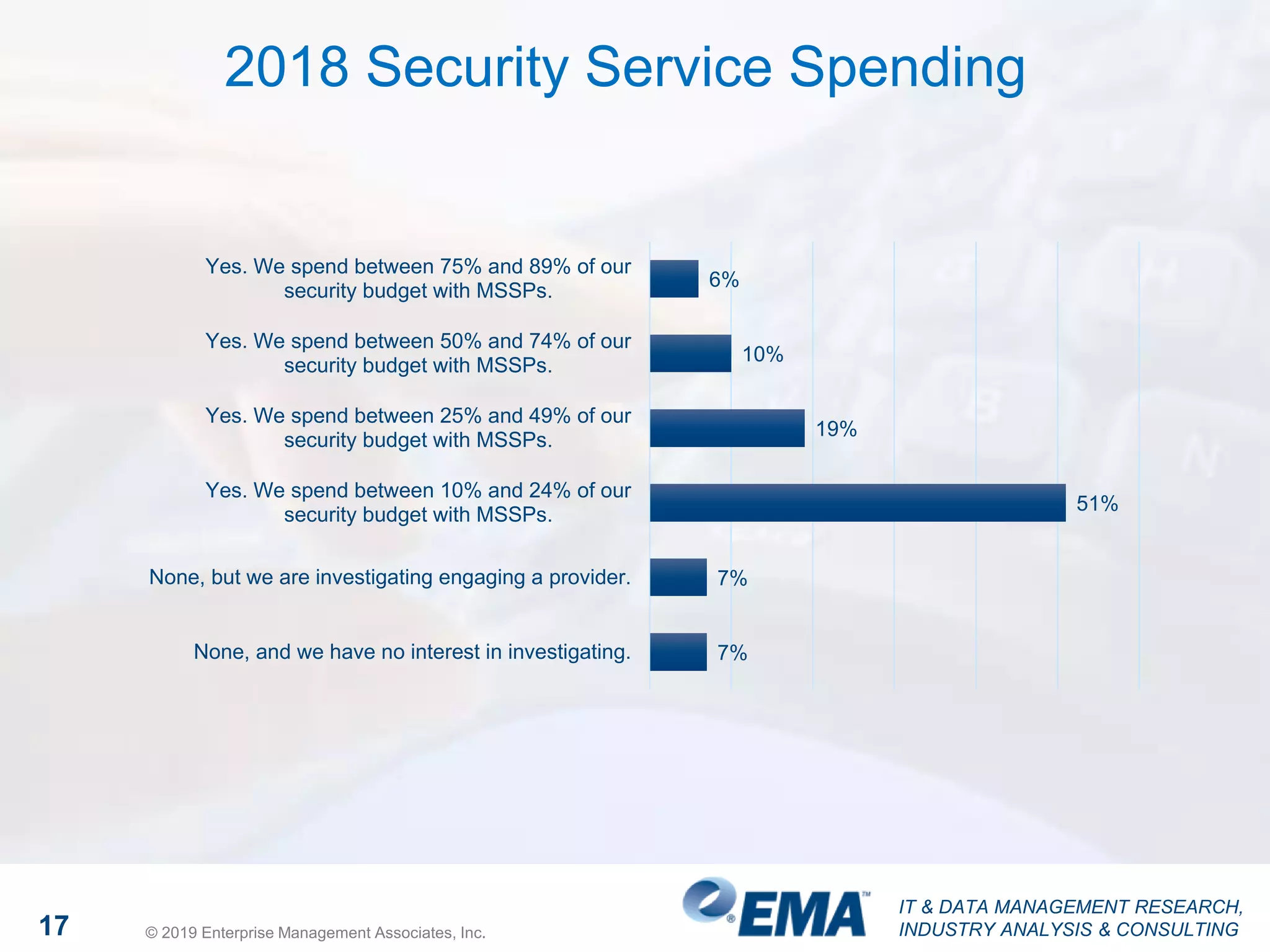
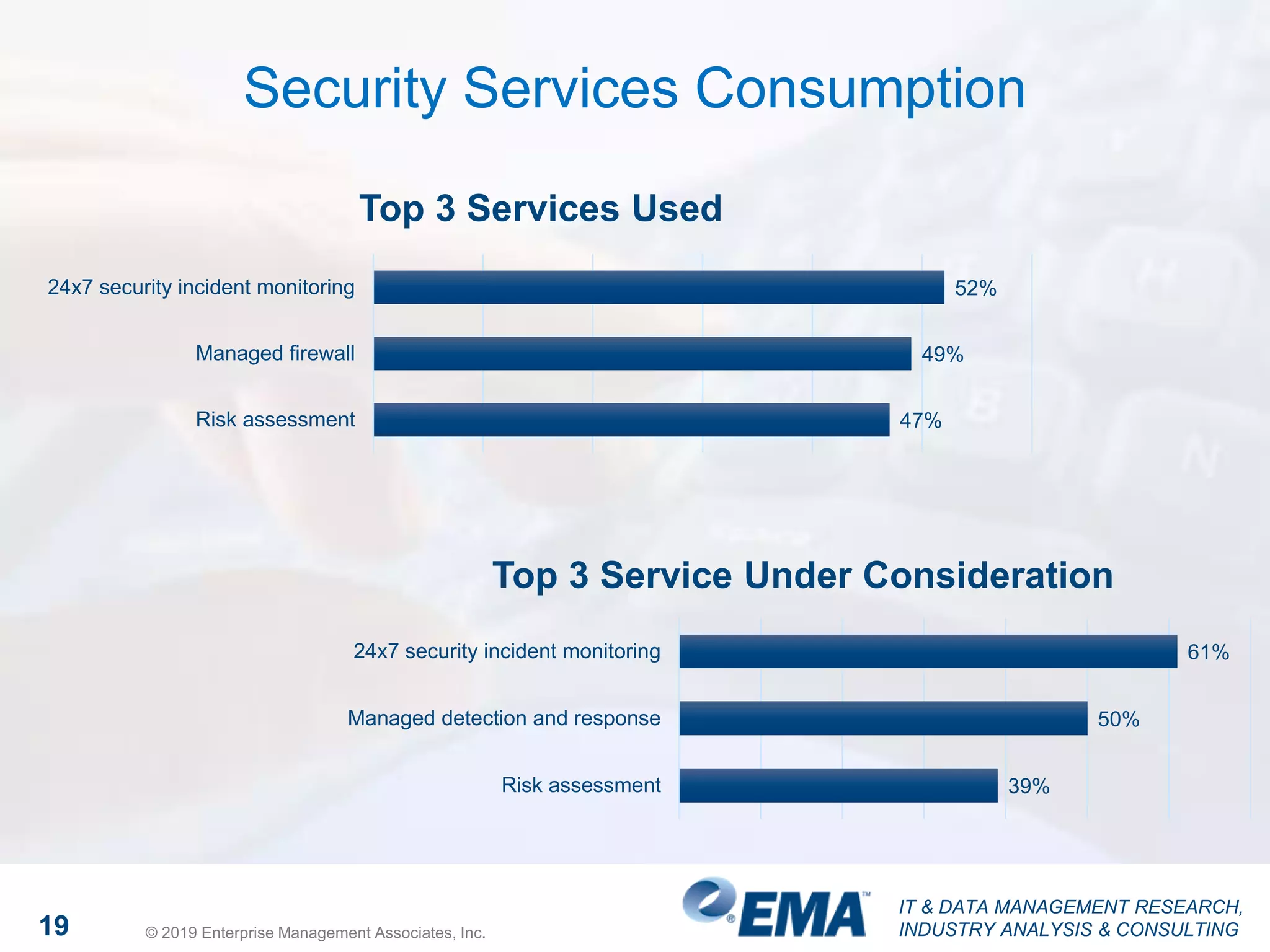
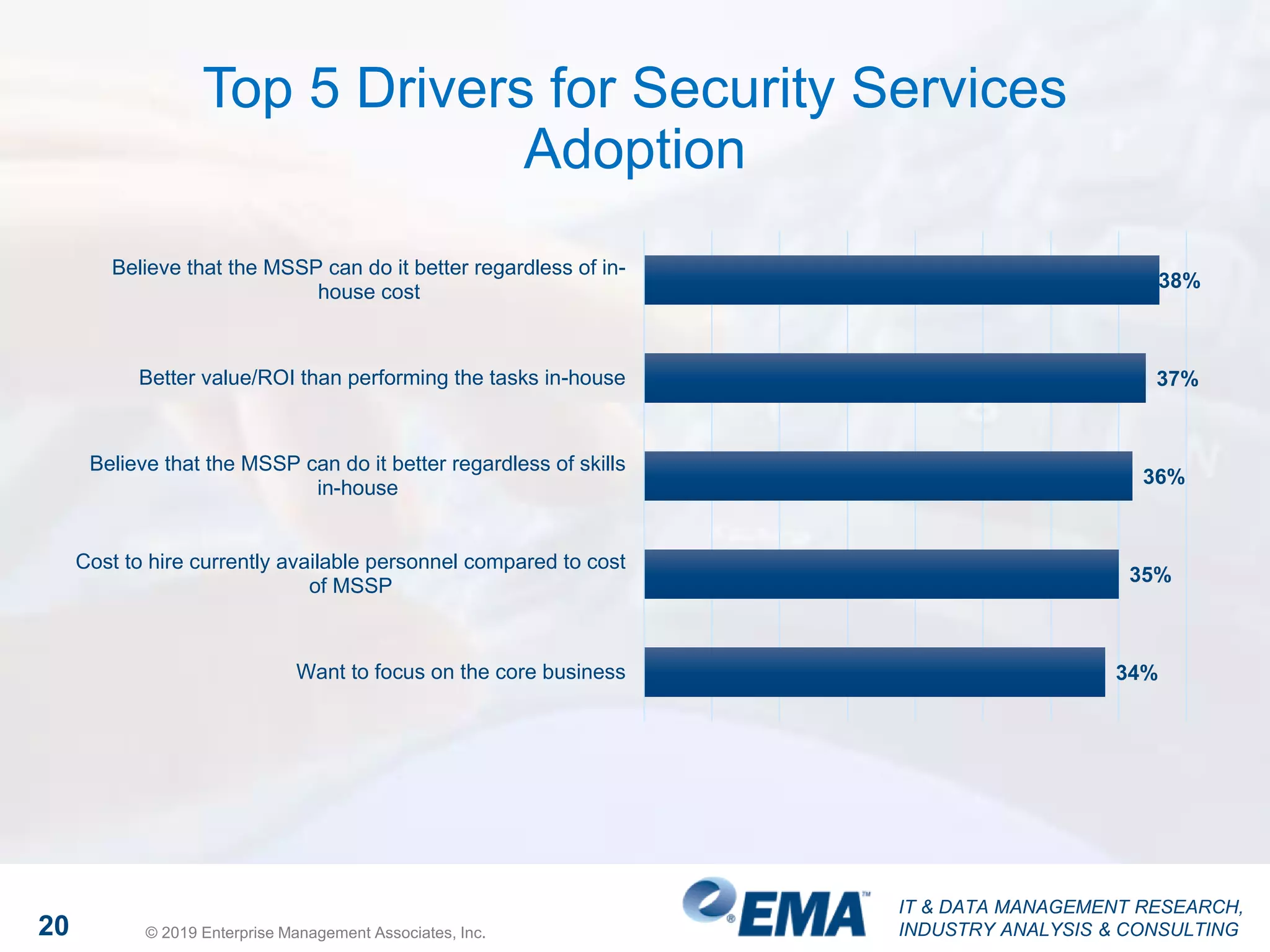
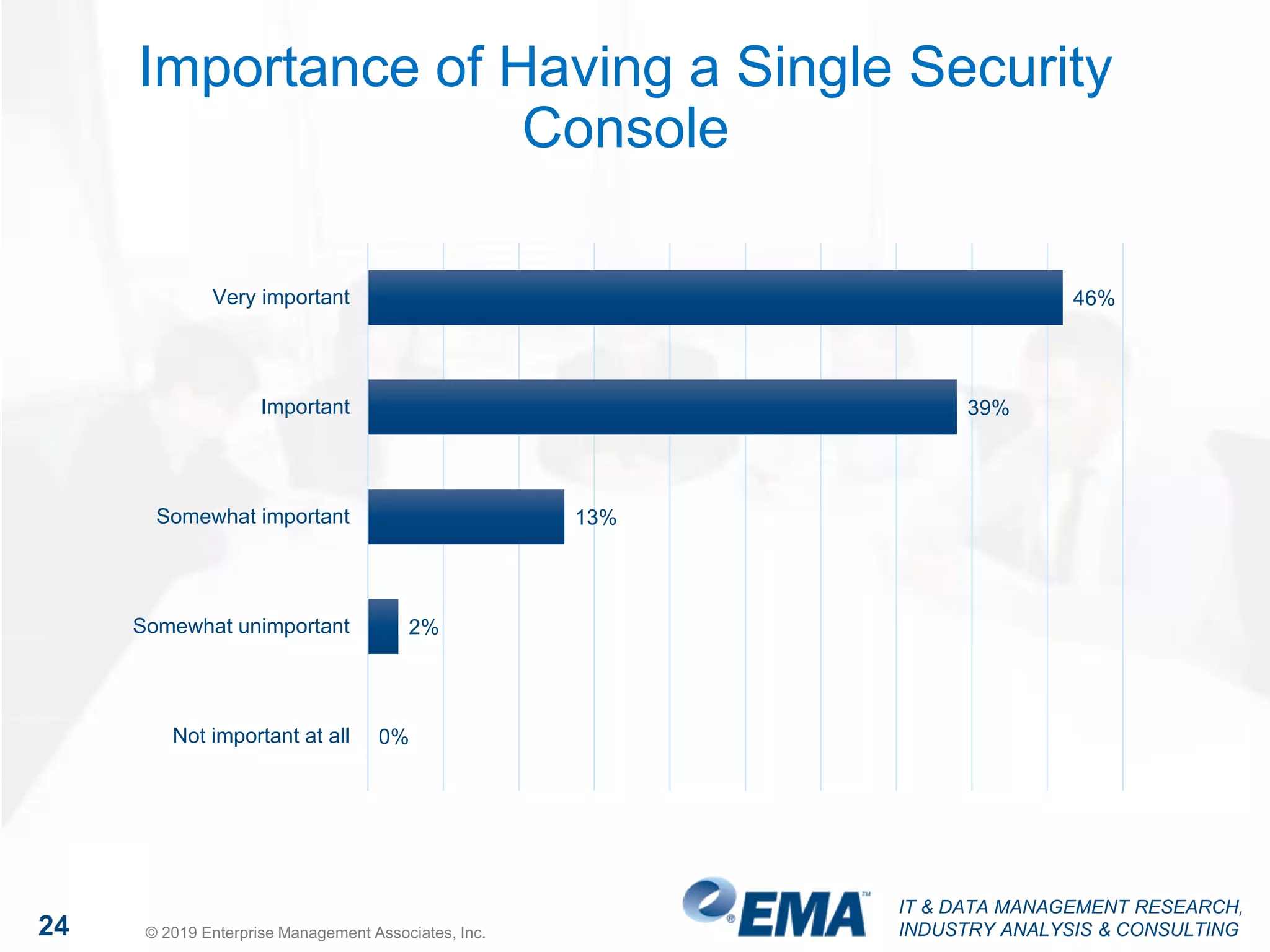
The document discusses a webinar focusing on high fidelity security, featuring insights from David Monahan, a managing research director in security and risk management. It highlights concerns about cybersecurity perceptions, budgets, and the effectiveness of various security measures across different industries. The findings reveal significant gaps in security program maturity and express the importance of automation and data integration in enhancing security operations.