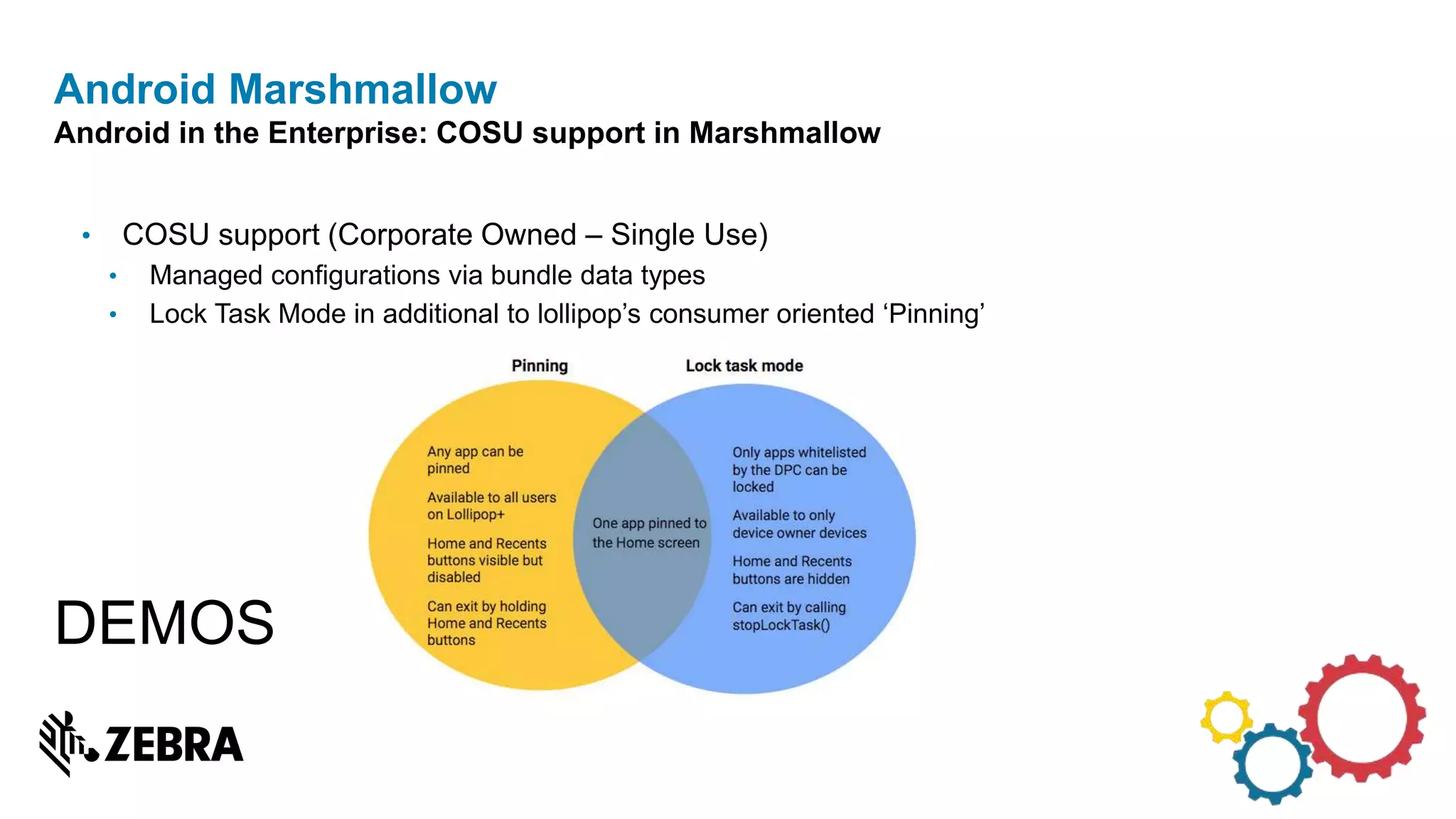
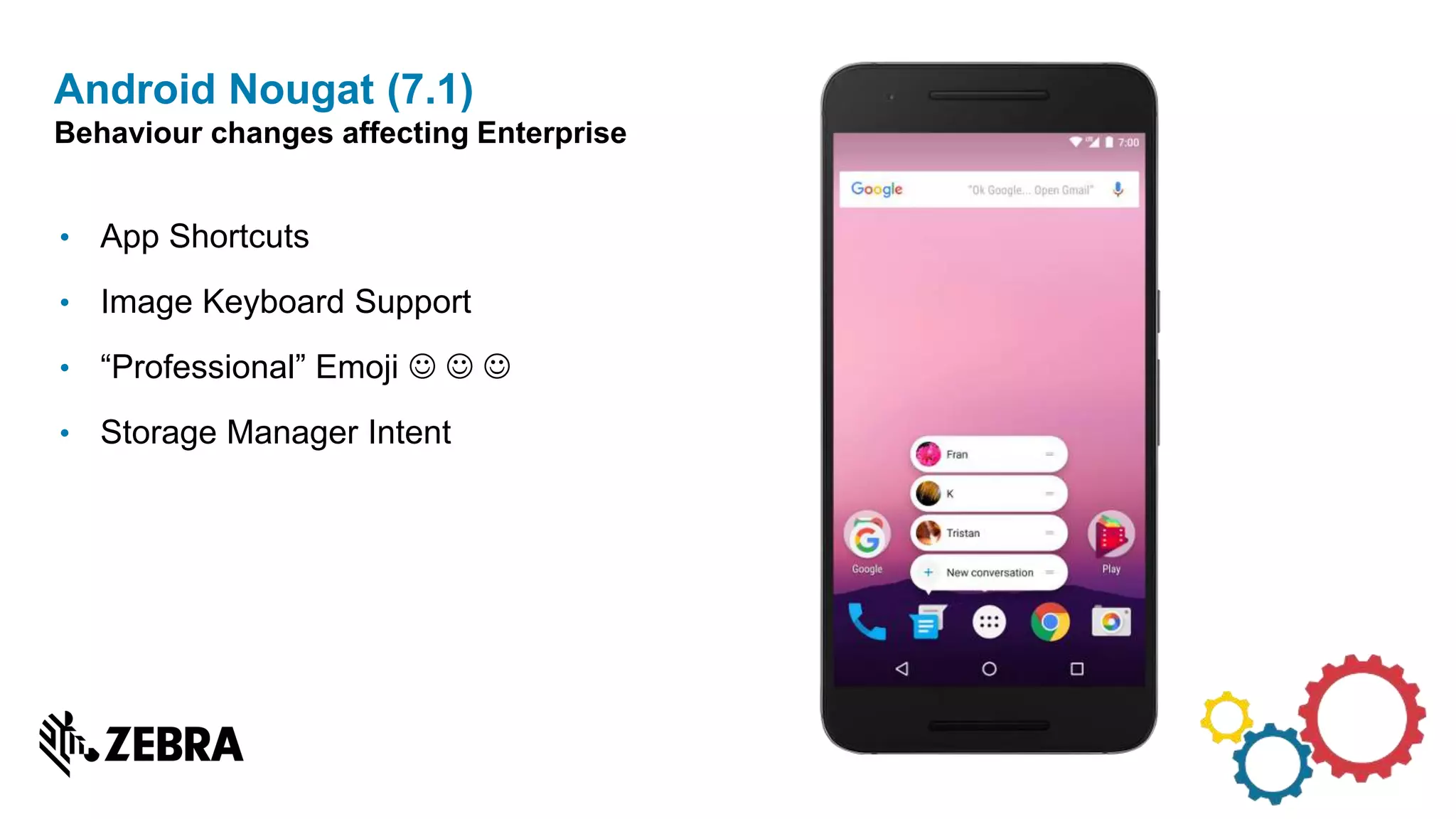
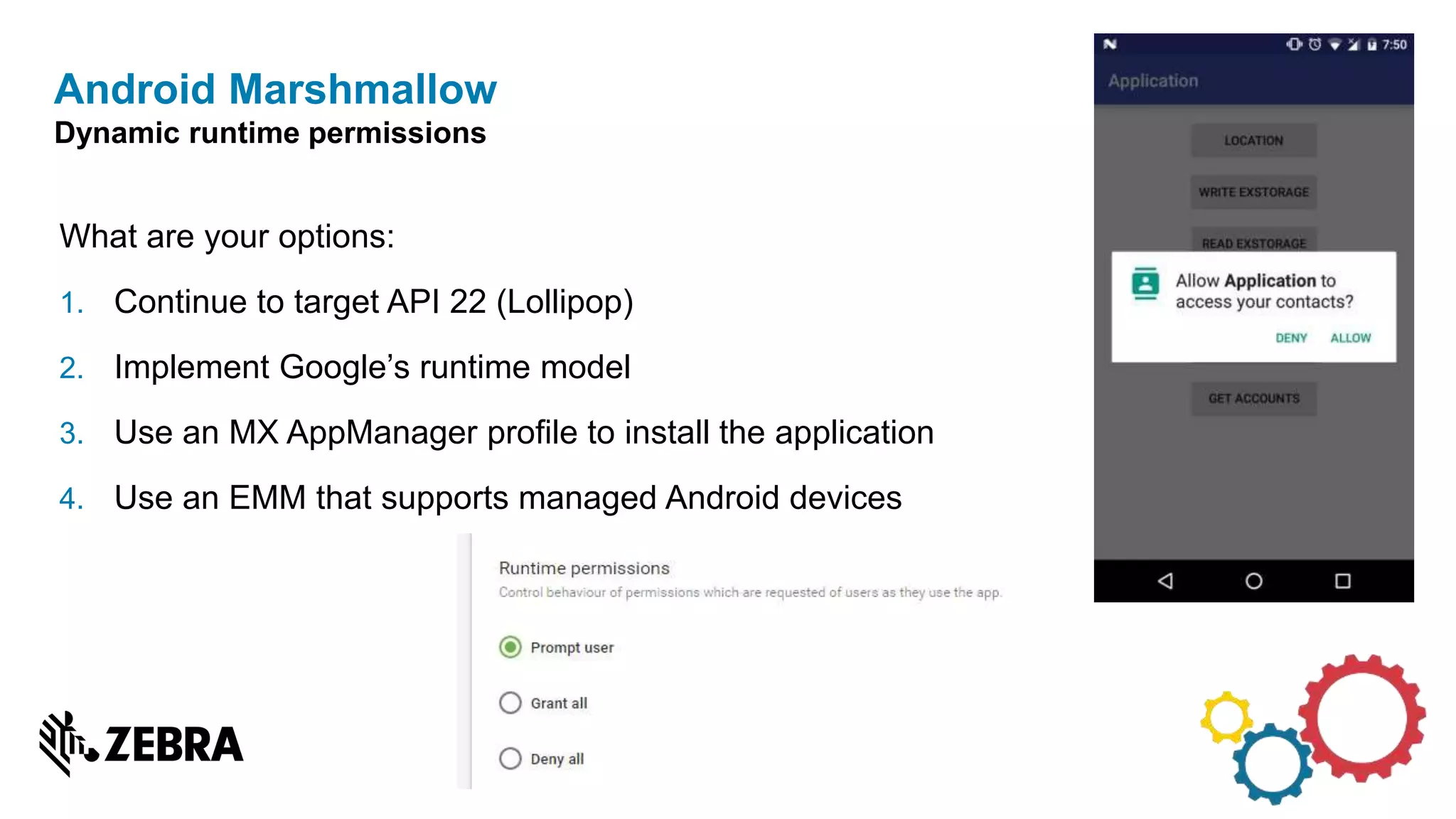
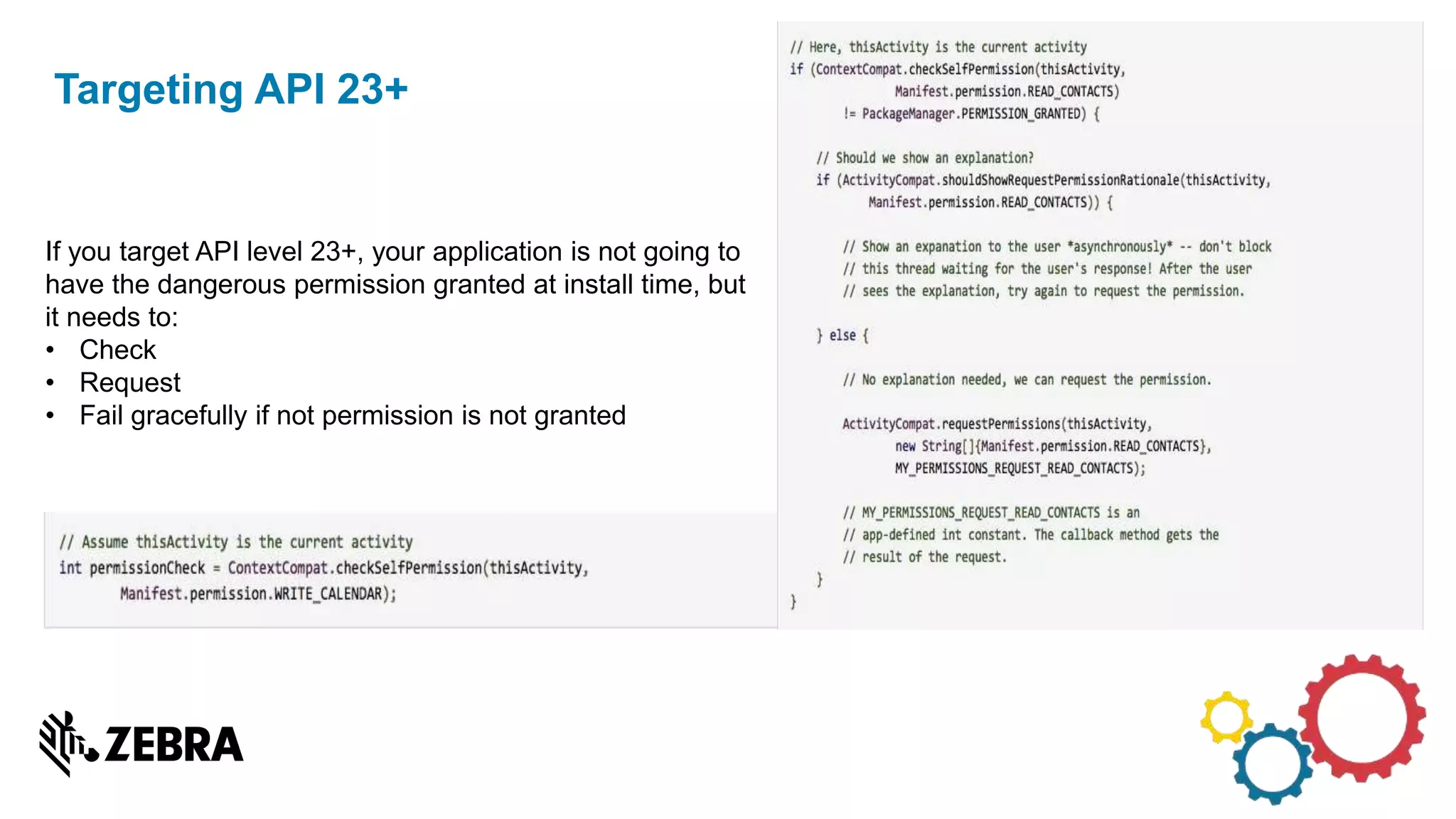
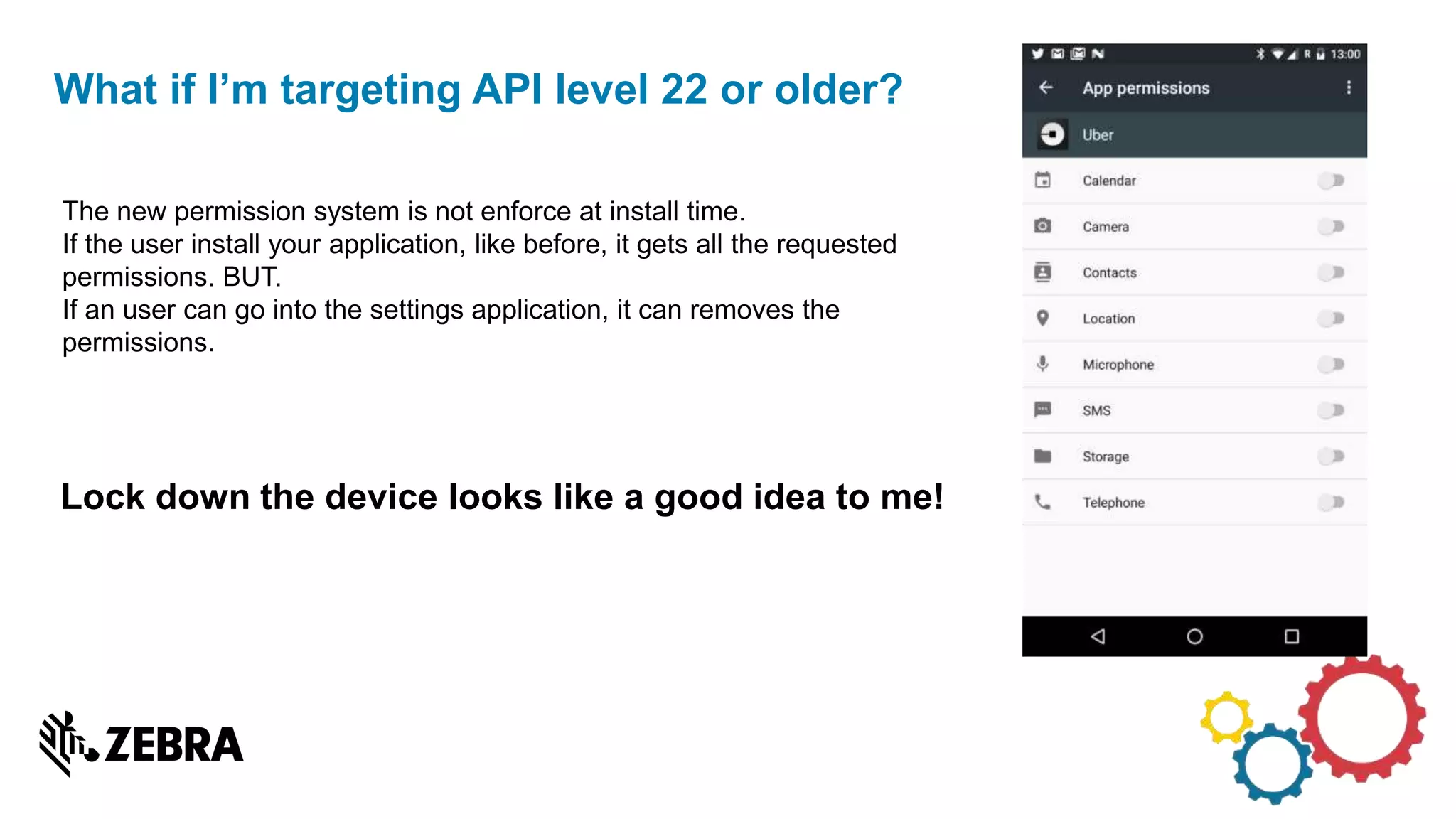
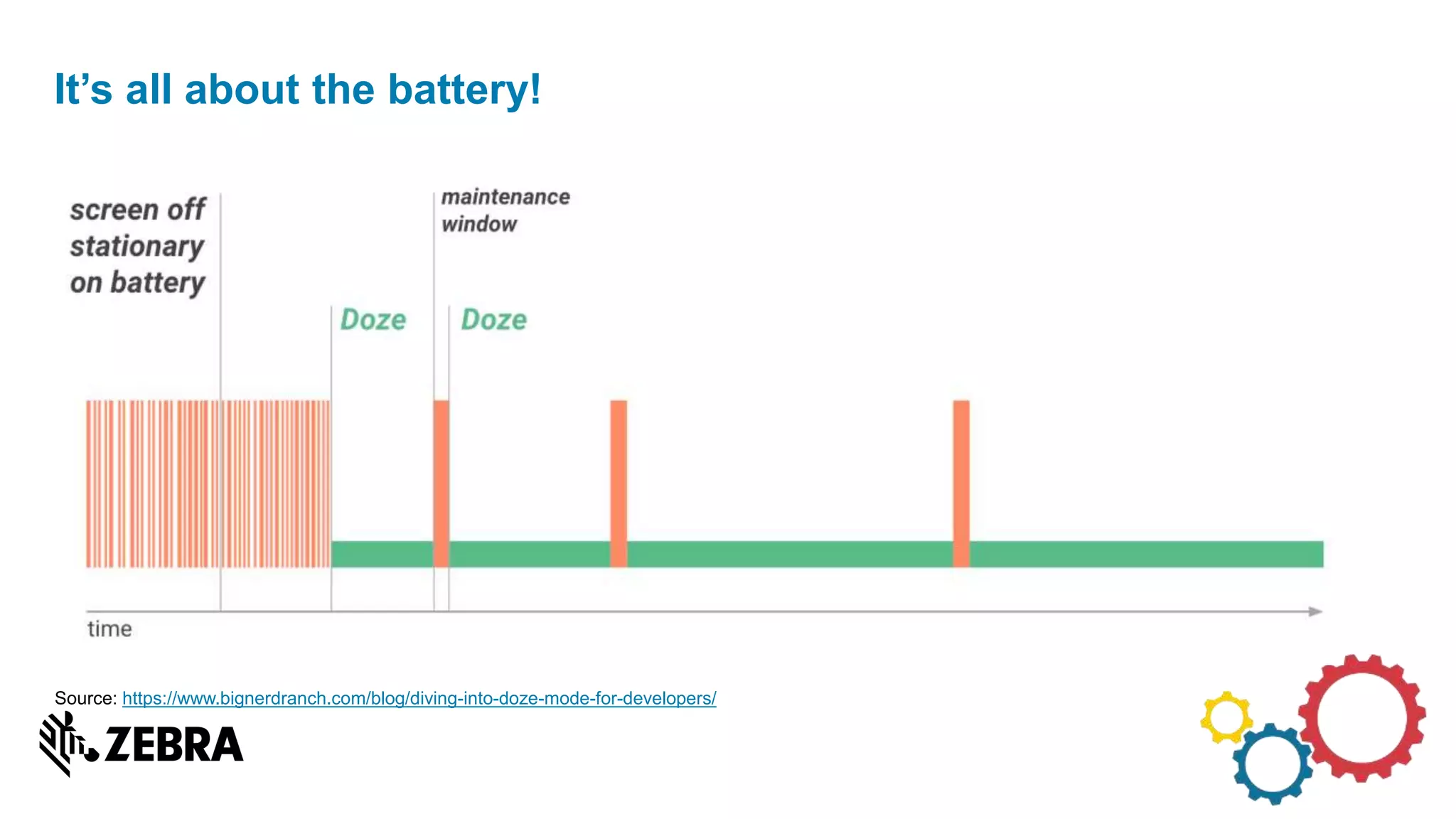
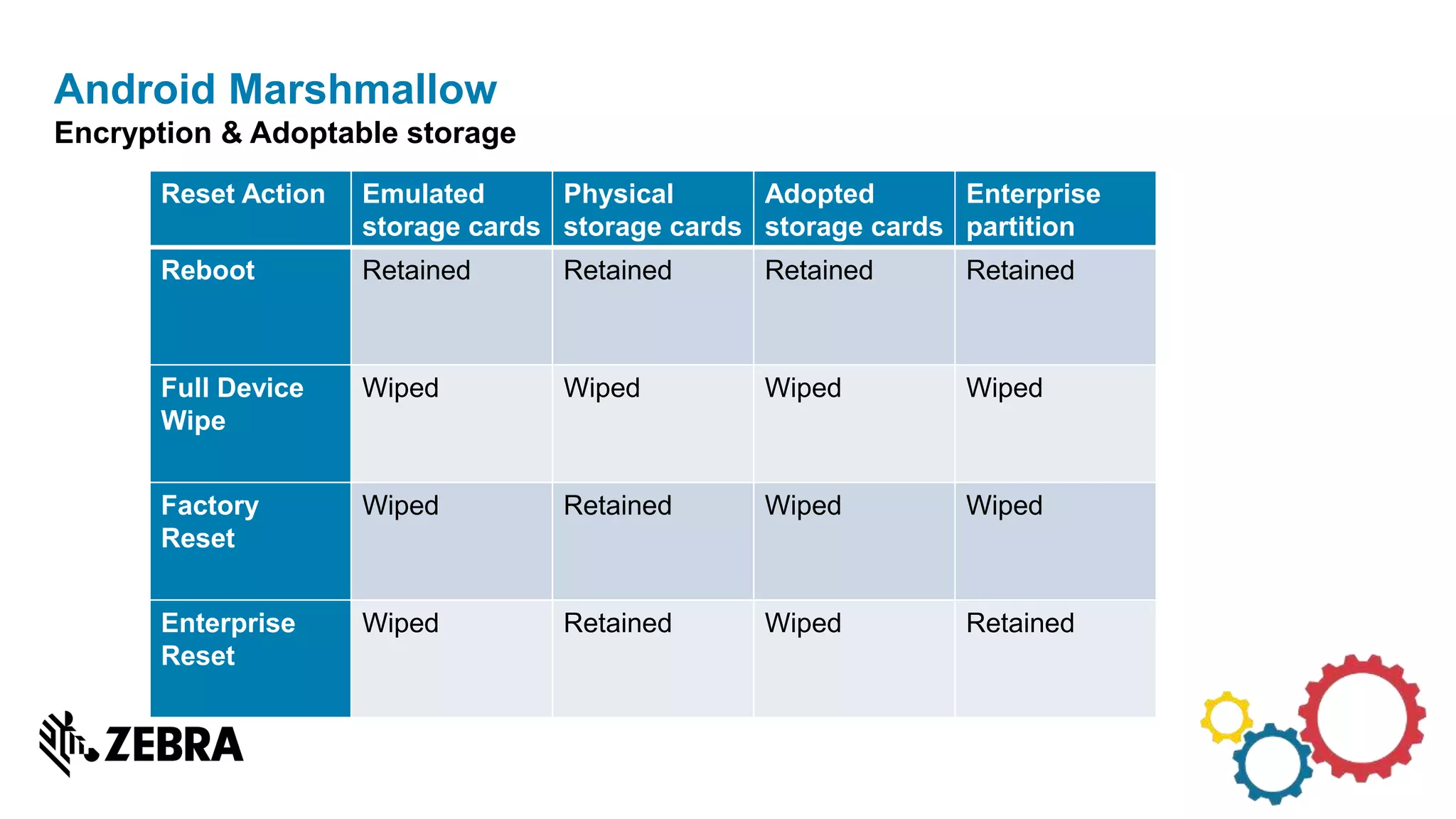
The document discusses the evolution of Android from versions Lollipop to 'O', highlighting notable changes in notifications, permissions, and power management. Key features like dynamic runtime permissions, Doze mode for battery saving, and enterprise support are emphasized across the different Android versions. The information is particularly relevant for developers working with enterprise Android applications and managing device access and security.










![• Applications and services have to call scanner disable when device is suspending [e.g.
onPause/onDestroy callback].
• On Lollipop (Android v5.x) or KitKat (Android v4.4) devices we don't have imager
standby mode supported, in this mode imager would consume lowest power, with
TC51/TC56/TC70x/TC75x, using Marshmallow (Android 6.0), this was a requirement to
have lowest power on suspend.
• With this mode, imager loses all it's configurations which is done in enable, hence user
needs to recall enable again, however after disabling scanner, otherwise scan
framework will not accept another enable due to state machine.
Android Marshmallow
Imager goes into standby mode when devices goes into suspend.](https://image.slidesharecdn.com/whatsdifferentinandroidlmno-170903200201/75/Whats-different-in-android-L-M-N-and-O-22-2048.jpg)
![• Android for Work started with 5.0 (lollipop). Announced at Google I/O 2014
• Initially targeted BYOD (Bring your own device) use cases
• Separation of ‘Work’ mode from personal applications
• ‘Work profile’ owned by a “Profile Owner” which would be a device policy controller (DPC)
• Enhancements for COPE (Corporate owned, personally enabled)
• Expectation that device or profile will owned by a DPC
• DPC is acting as device owner (DO) or profile owner (PO)
• Enhancements for COSU (Corporate owned, single use) [6.0+]
• Expectation that these devices will only have a device owner (DO)
• Typical Zebra device use cases
• Non-Zebra single use Android devices could be a payment terminal or airport check-in.
• DO provisioning via NFC prioritized by Google (also possible via adb)
Android Marshmallow
Android in the Enterprise: Recap](https://image.slidesharecdn.com/whatsdifferentinandroidlmno-170903200201/75/Whats-different-in-android-L-M-N-and-O-23-2048.jpg)