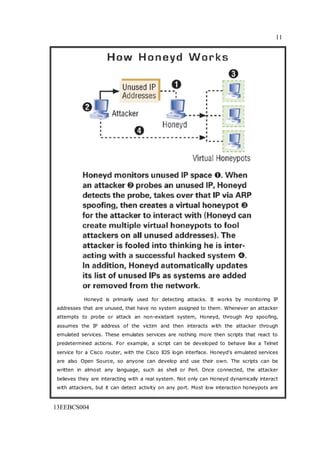
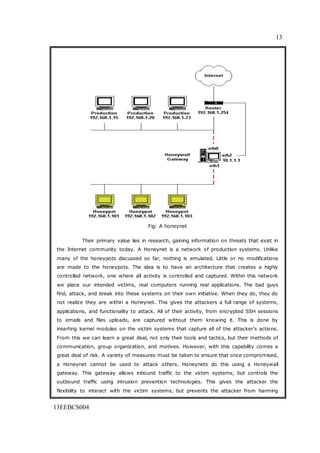
The seminar report on honeypots discusses their definition, types, and relevance in cybersecurity, emphasizing their role in gathering intelligence about attackers. It categorizes honeypots into low-interaction and high-interaction types, highlighting their respective advantages and limitations. The report also explores the legal implications and future potential of honeypots in combating computer crimes.