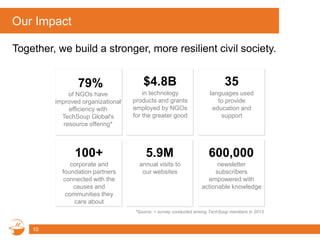
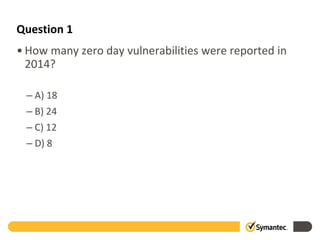
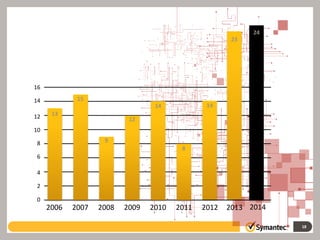
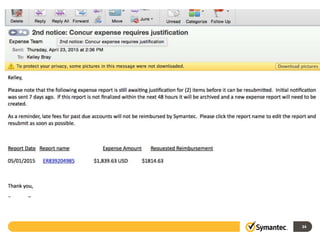
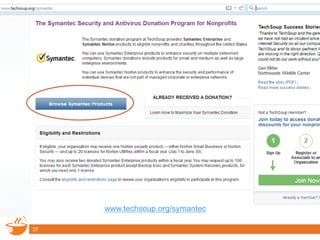
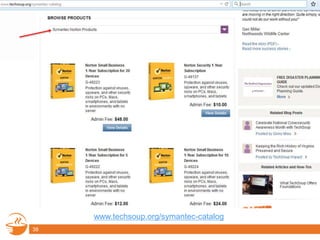
This document provides information about a webinar on keeping nonprofits and libraries secure. The webinar covered introducing TechSoup and their security donation programs, security threats like zero-day vulnerabilities and common causes of data breaches, and basic security practices around passwords, social media, phishing, and more. It also discussed Symantec's security solutions and how to get started with free security resources.