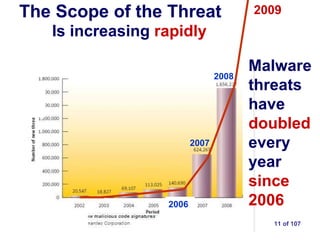
The document provides extensive information on how to protect oneself from various internet security threats, including malware, scams, phishing, and social engineering. It emphasizes the necessity of implementing layered security measures and best practices, such as using strong passwords and regularly updating software. The document also discusses specific tools and strategies for data backup and recovery, as well as the importance of user account management to minimize security risks.