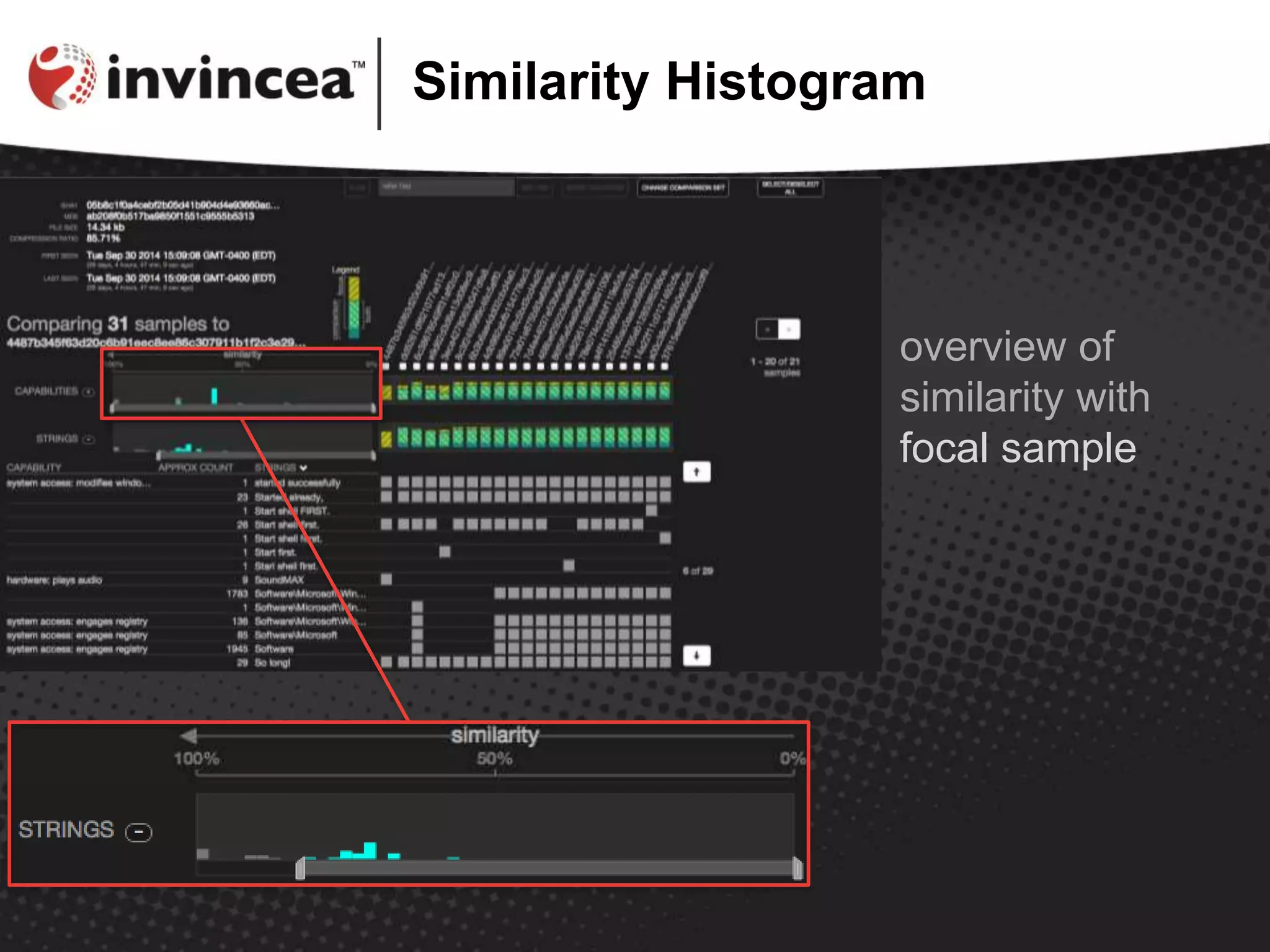
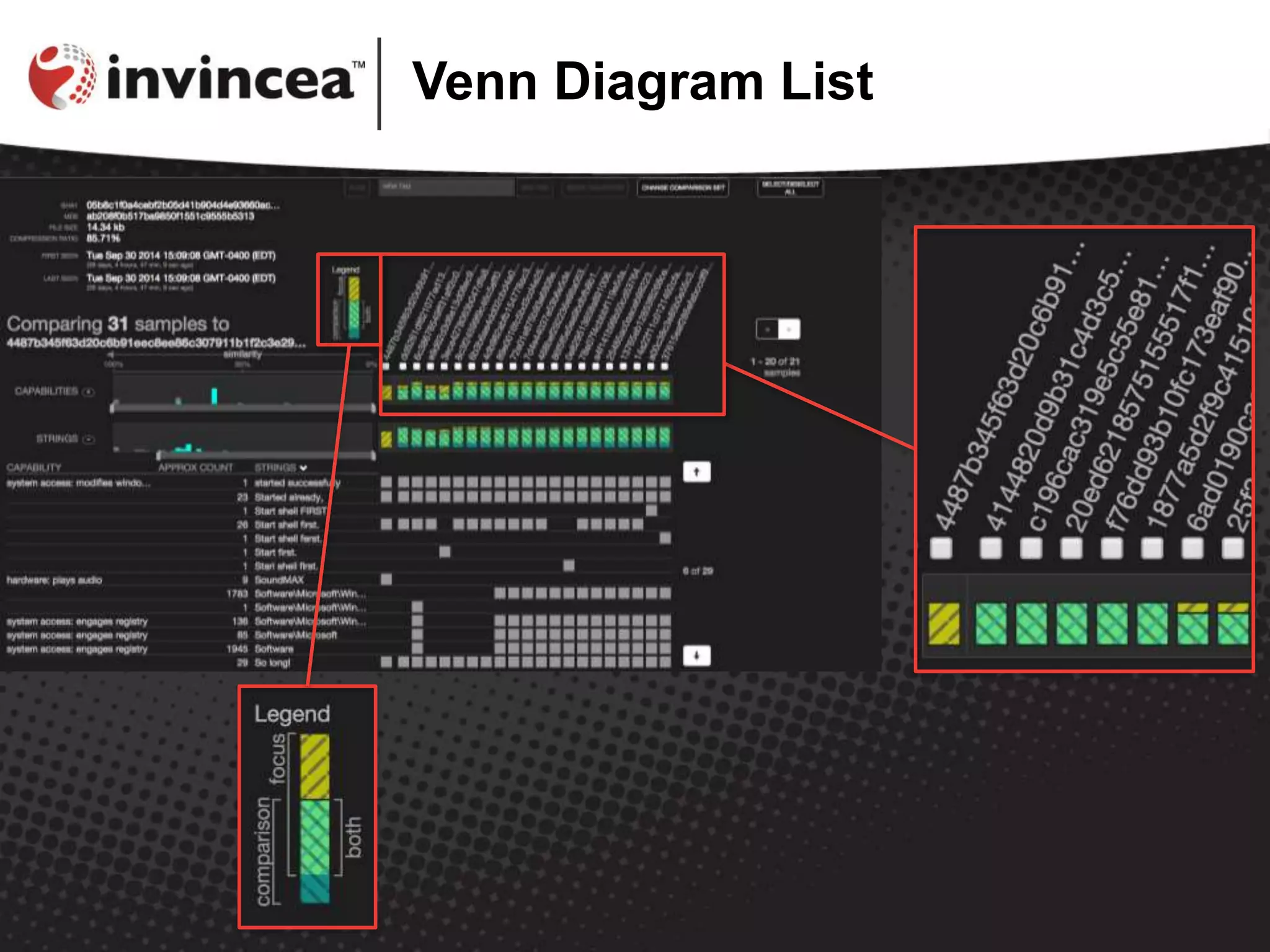
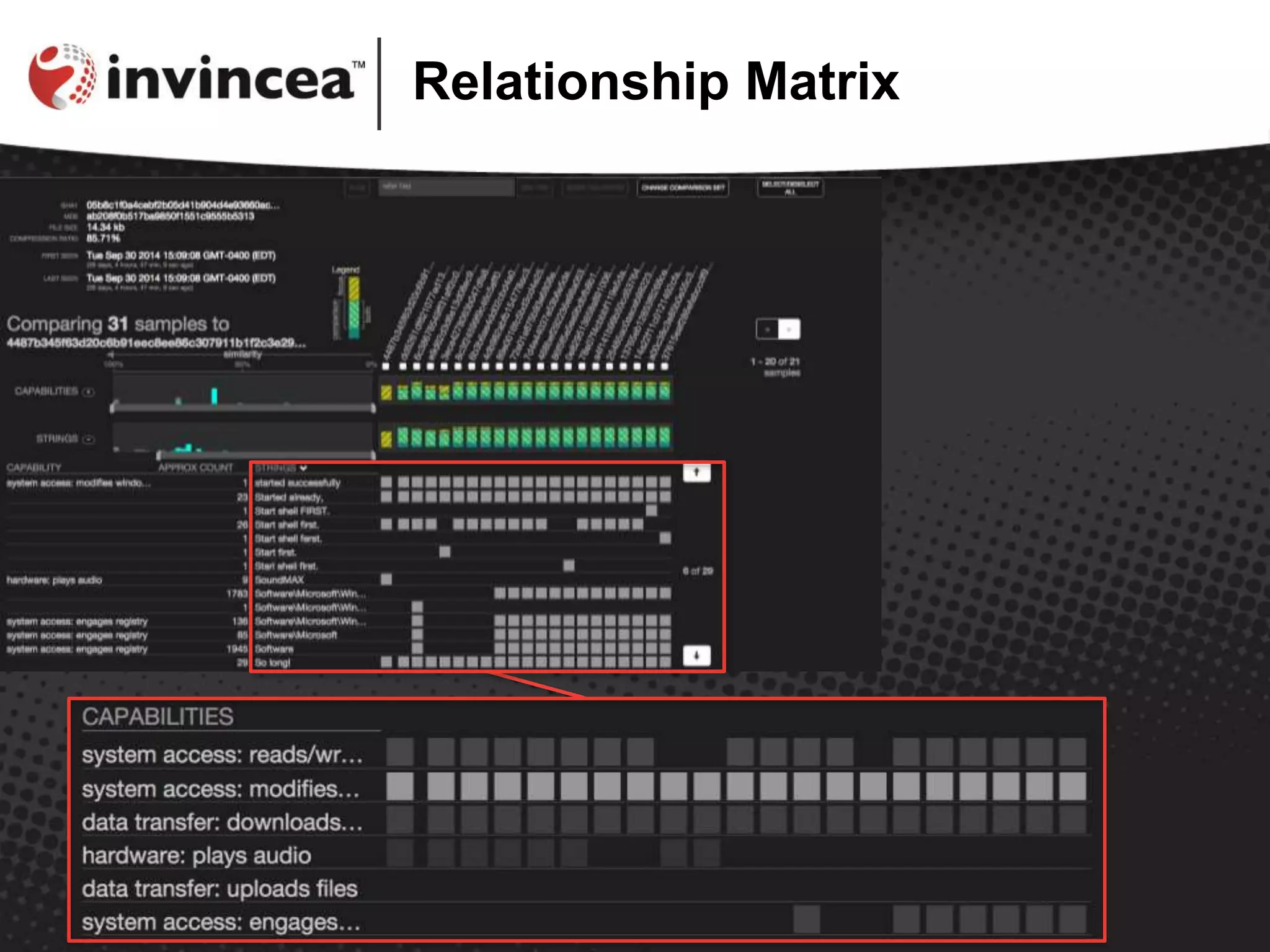
The document discusses the Similarity Evidence Explorer for malware, a data visualization tool developed by Robert Gove, aimed at aiding malware analysts in comparing malware attributes efficiently. The tool enables large-scale comparisons through features like histograms and detailed visualizations, facilitating the analysis of numerous malware samples. For further information and access to the tool, users are directed to the Cynomix website.



![Existing Malware Viz Tools
compare system calls
[Trinius et al, 2009]
[Saxe et al, 2012]
individual malware
[Conit et al, 2008]
[Quist and Lierbrock,
2009]
[Domas, 2012]](https://image.slidesharecdn.com/seem-presentationinvincea2-17-15-150218074745-conversion-gate01/75/Webcast-The-Similarity-Evidence-Explorer-For-Malware-6-2048.jpg)
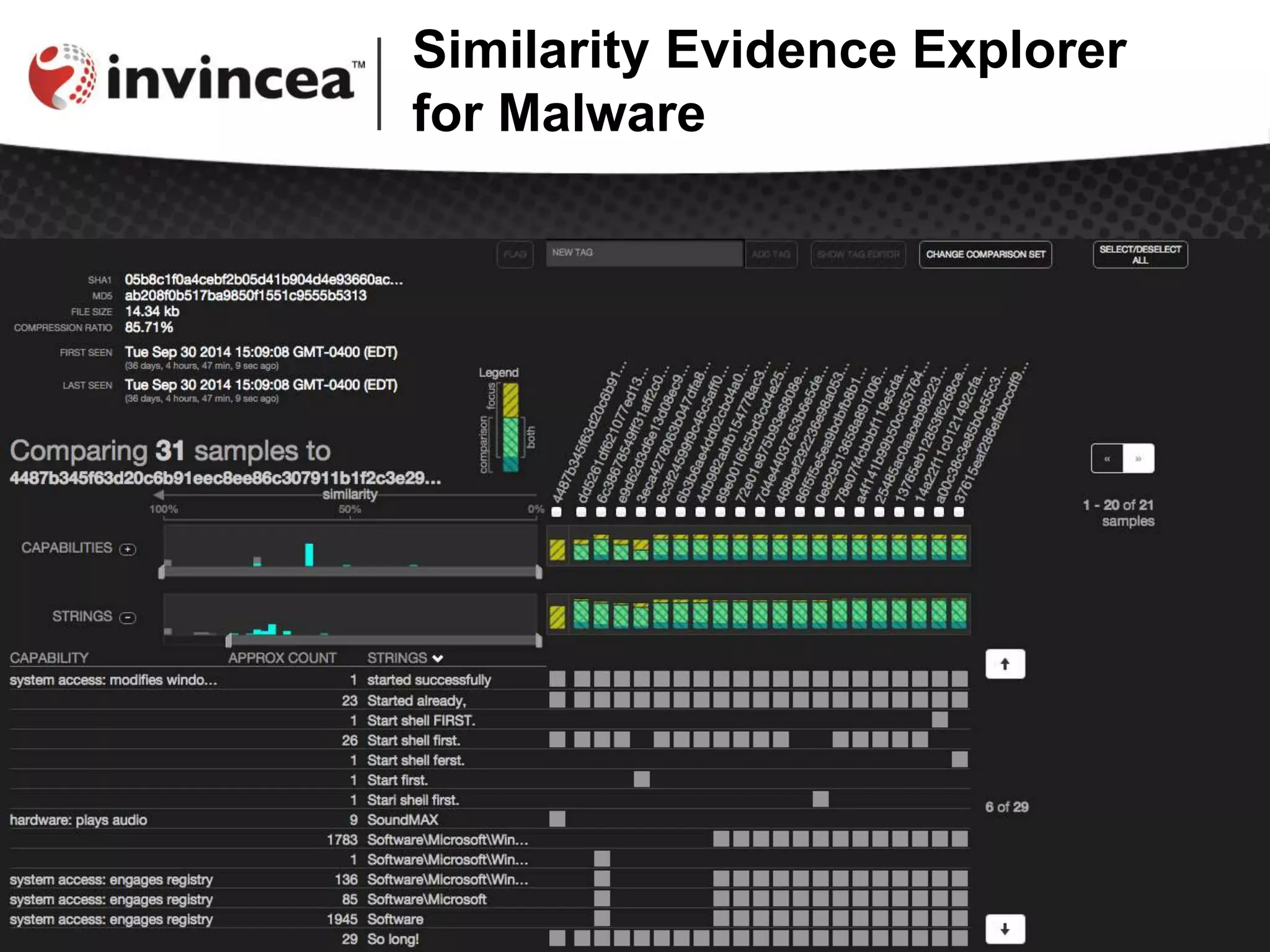
![SEEM Demo
[ DEMO ]
try it yourself: www.cynomix.org](https://image.slidesharecdn.com/seem-presentationinvincea2-17-15-150218074745-conversion-gate01/75/Webcast-The-Similarity-Evidence-Explorer-For-Malware-11-2048.jpg)