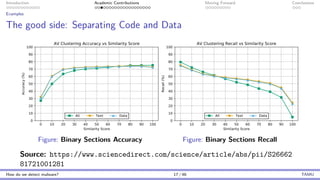
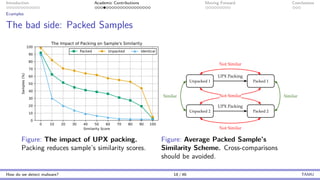
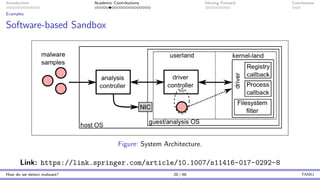
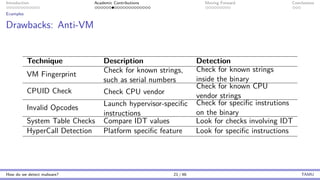
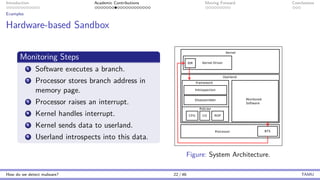
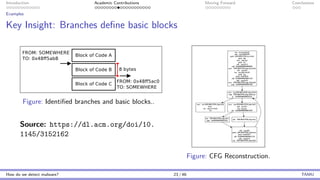
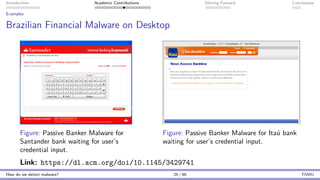
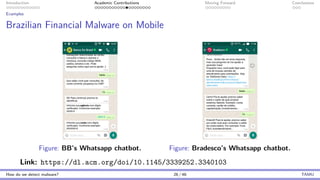
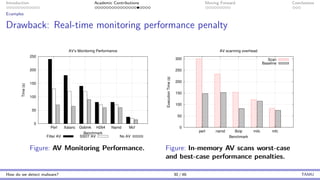
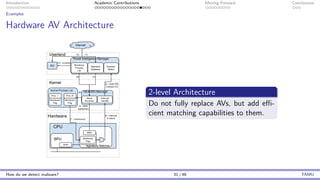
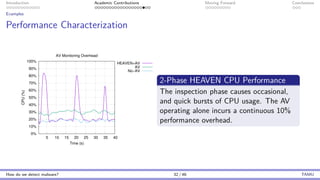
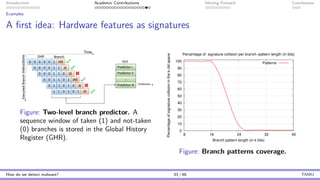
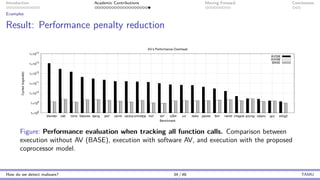
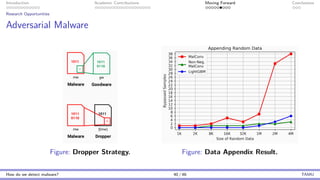
The document presents an overview of malware detection, discussing various methods including collection, triage, sandbox analysis, threat intelligence, and endpoint protection. It highlights challenges, advancements in detection techniques, and opportunities for future research, particularly in deep learning and adversarial machine learning. The author, Marcus Botacin, emphasizes the need for continuous improvements in malware triage and analysis to enhance security measures.