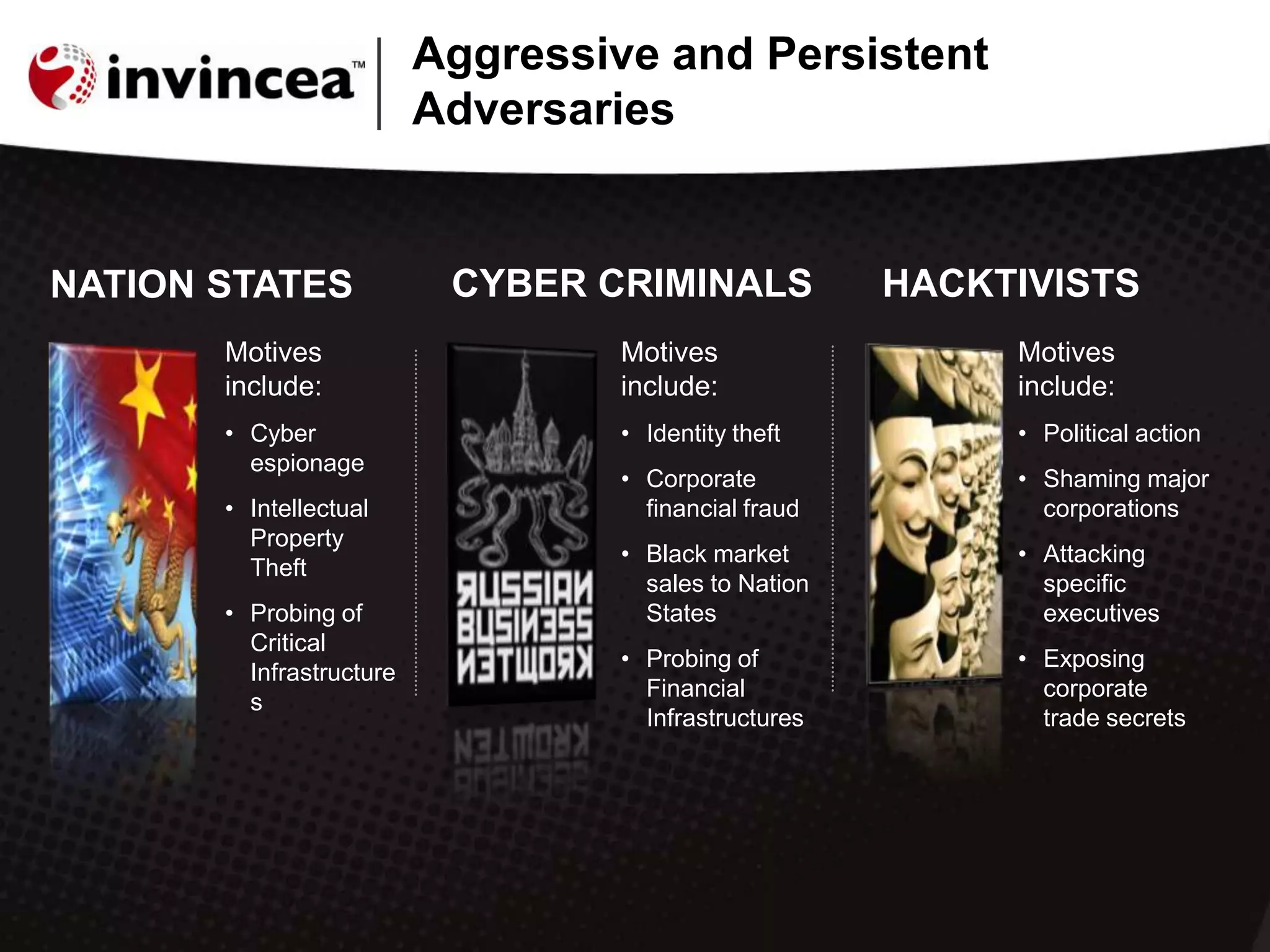
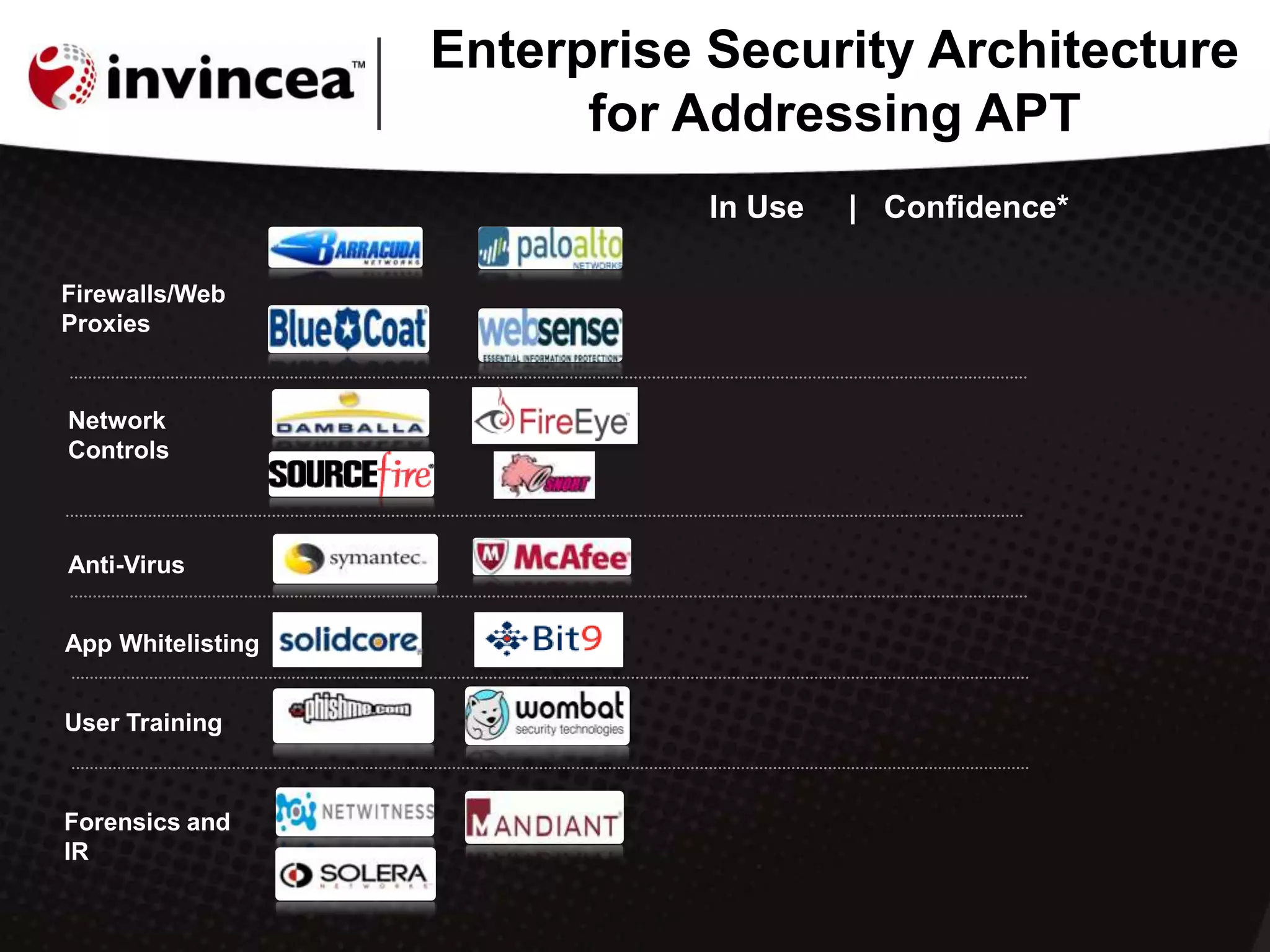
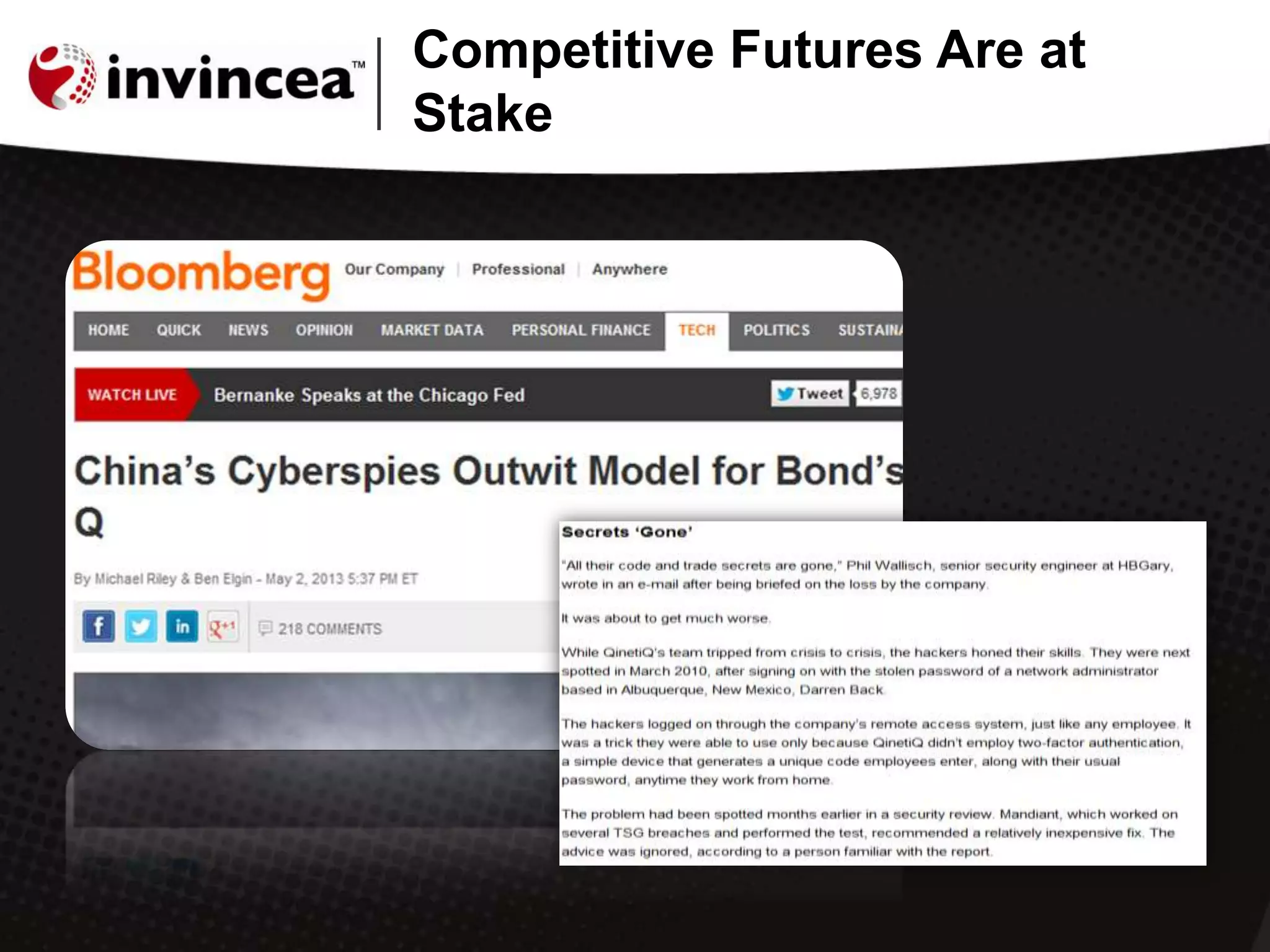
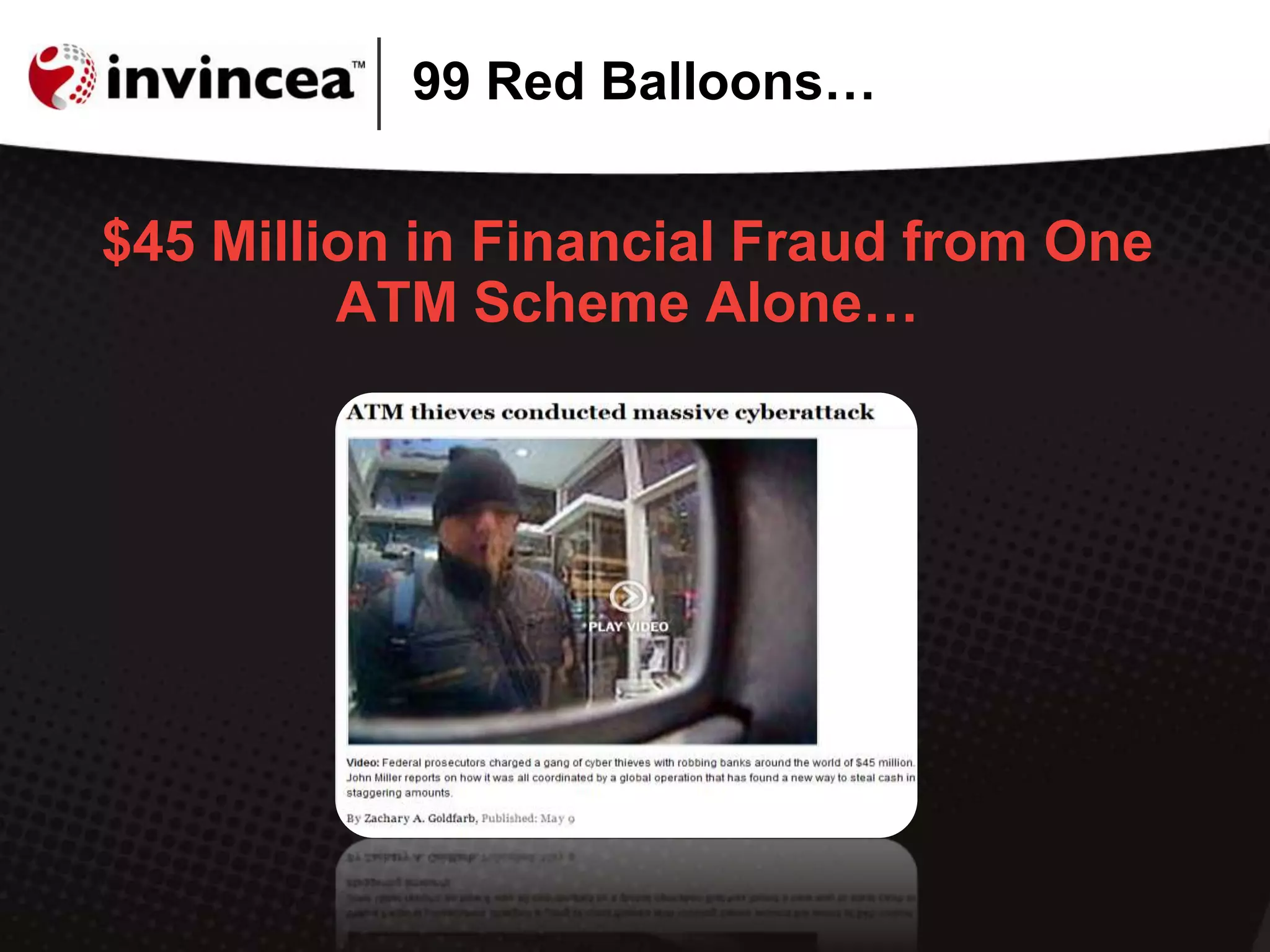
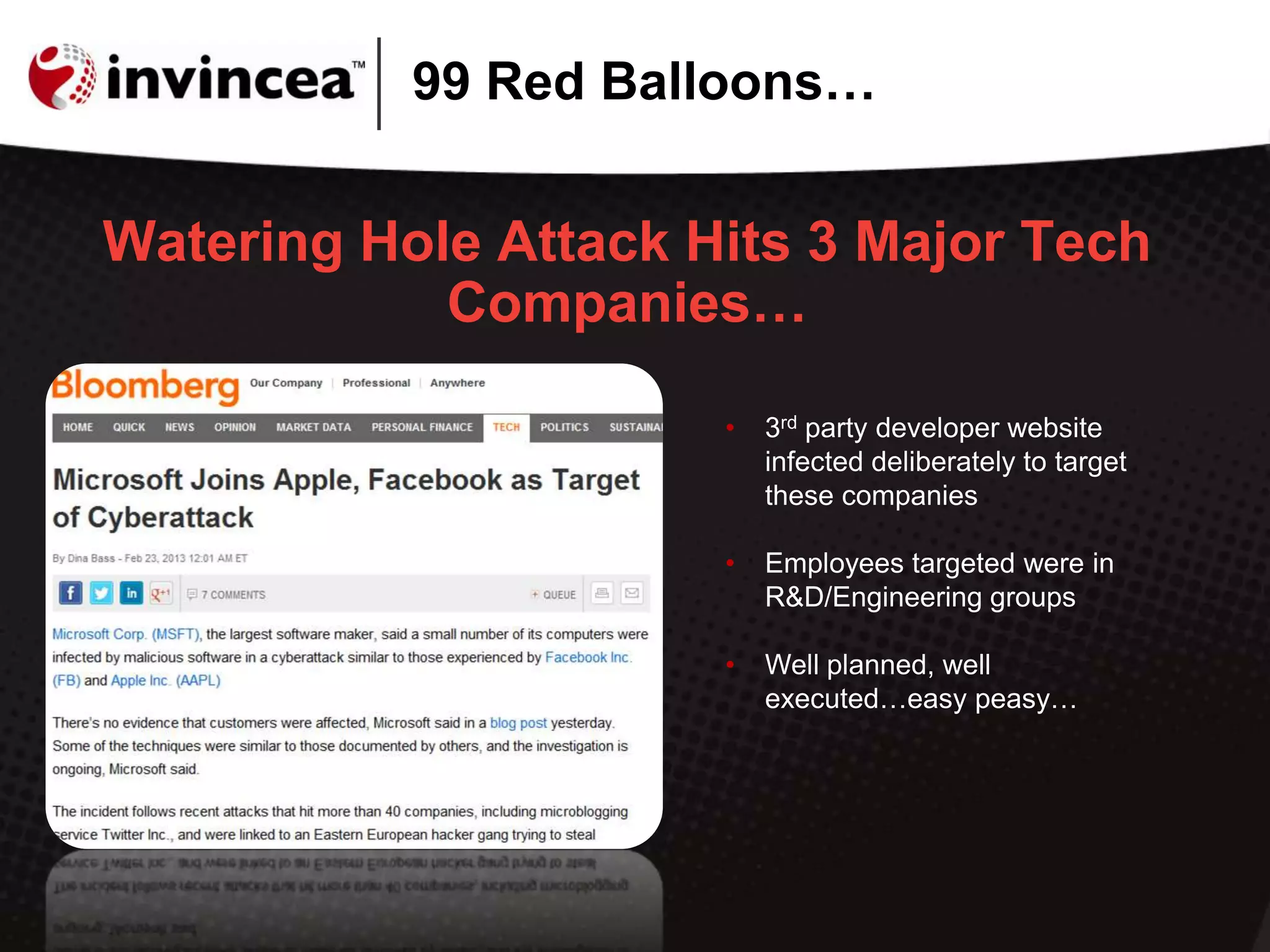
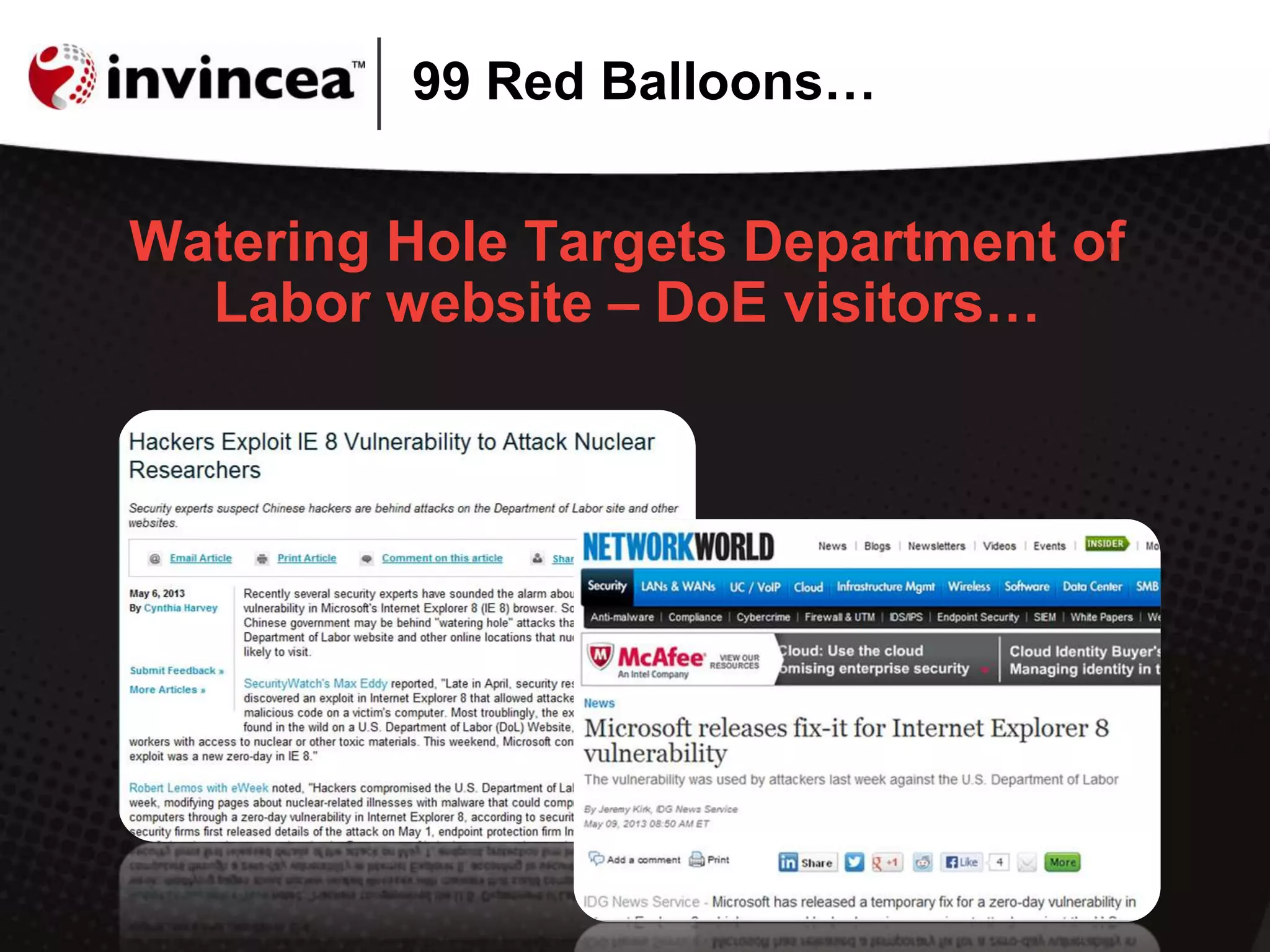
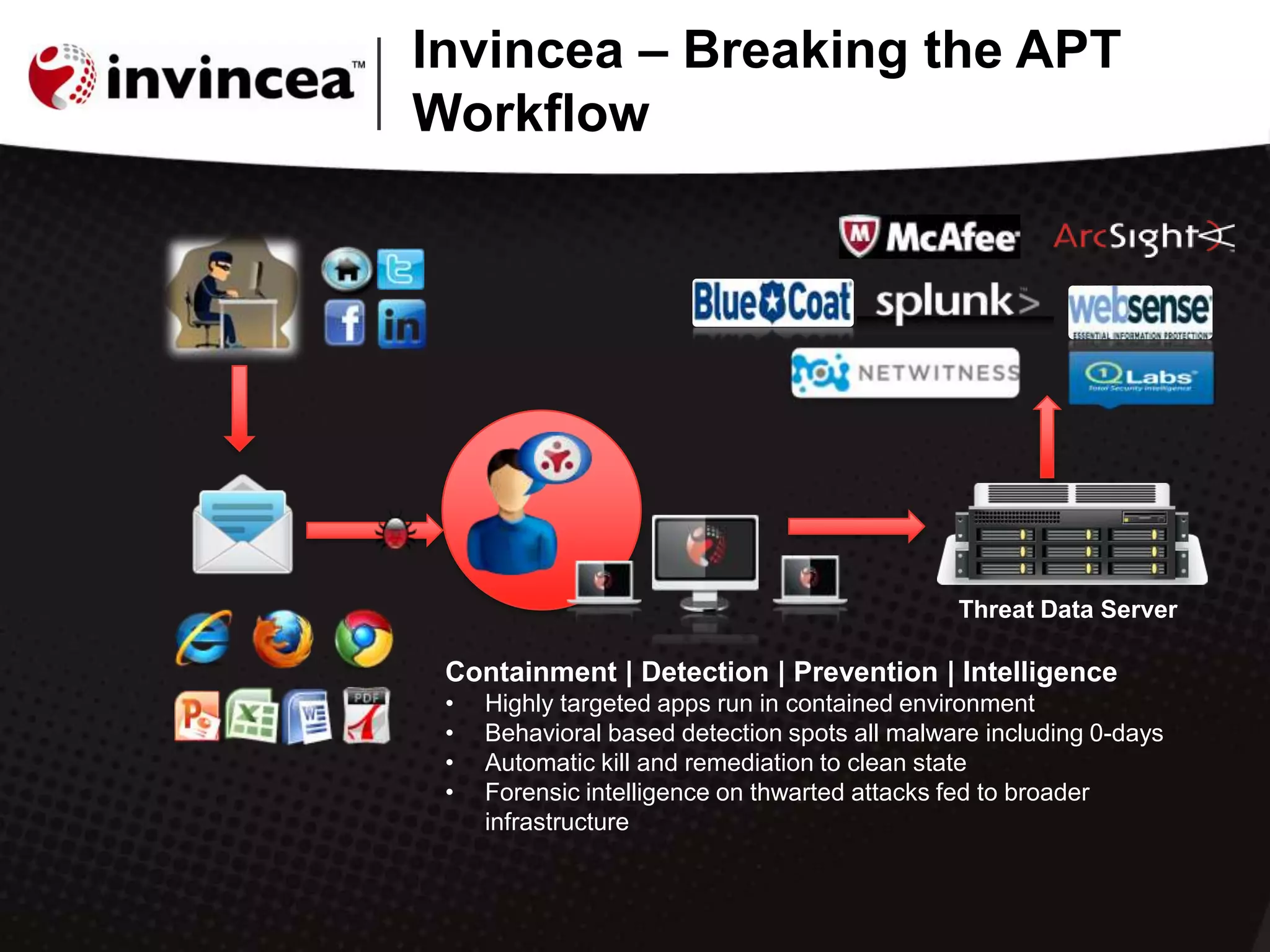
This document discusses advanced persistent threats (APTs) and how they have evolved to target users through spear phishing, watering hole attacks, and drive-by downloads. It outlines the tactics, techniques, and motivations of aggressive adversaries like nation states, cyber criminals, and hacktivists. It argues that current security practices are insufficient and that a new approach is needed to contain malware, detect zero-day attacks without signatures, and prevent APTs by negating user error and containing infections in a virtual environment. It promotes the Invincea security product as a solution to break the APT workflow through containment, detection, prevention, and intelligence capabilities.