This document discusses CORS, authentication, authorization, and connecting a backend to MongoDB. It defines CORS as a security feature that controls cross-origin resource sharing. It explains that authentication verifies a user's identity through credentials, while authorization determines what resources an authenticated user can access. It then provides a detailed guide to building an authentication API with JWT tokens in Node.js, including creating routes for registration, login, and protected resources. Finally, it outlines the steps to connect a backend framework like Node.js to MongoDB, including installing drivers and performing operations like data insertion.







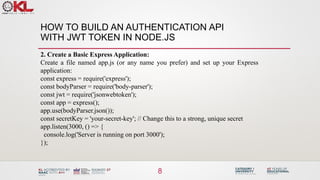
![HOW TO BUILD AN AUTHENTICATION API
WITH JWT TOKEN IN NODE.JS
9
3. Create User Model:
Create a simple user model (you can use a database for a real application, but for simplicity,
we'll use an array here):
const users = [
{ id: 1, username: 'user1', password: 'password1' },
{ id: 2, username: 'user2', password: 'password2' },
];](https://image.slidesharecdn.com/23003470814ppt-240216074649-295a33c5/85/MSWD-MERN-STACK-WEB-DEVELOPMENT-COURSE-CODE-9-320.jpg)








