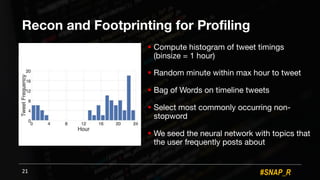
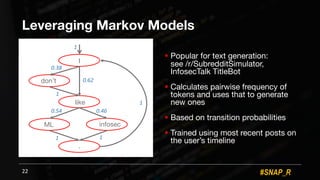
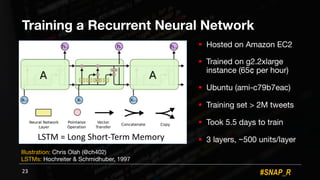
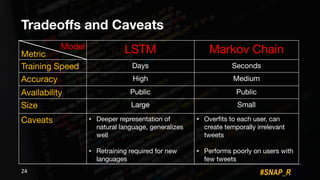
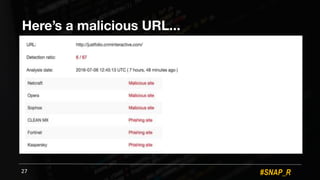
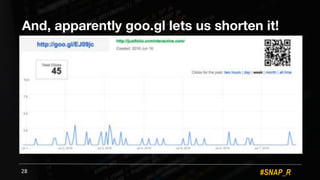
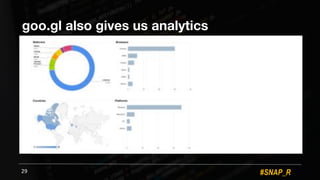
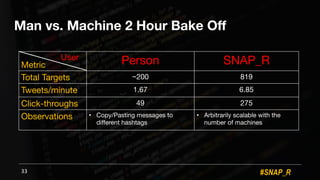
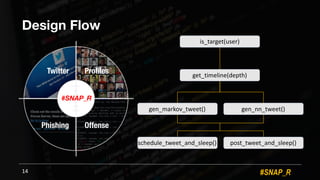
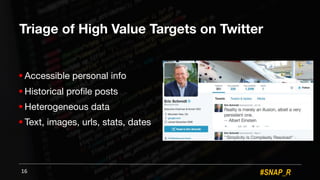
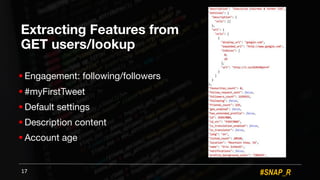
The document discusses the use of automated data science techniques for spear phishing on Twitter, highlighting the effectiveness of these methods in phishing attacks with success rates of over 30% for fully automated approaches. It details the design and implementation of a machine learning tool that generates convincing tweets for phishing and analyzes target profiles for high engagement potential. The authors emphasize the implications for social engineering and the importance of security awareness, noting that while their work is intended for defense, similar tools could easily be weaponized by malicious actors.










![#SNAP_R
Selecting the
Best
Clustering
Model
19
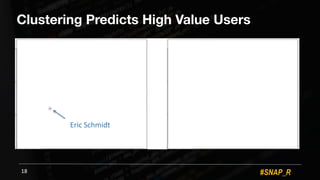
! Many algorithms
! Many hyperparameters
! Max avg. score [-1,..,1]
! 0.5-0.7 reasonable structure](https://image.slidesharecdn.com/weaponizing-data-science-for-social-engineering-automated-e2e-spear-phishing-on-twitter-161124071059/85/Weaponizing-data-science-for-social-engineering-automate-E2E-spear-phishing-on-twitter-19-320.jpg)