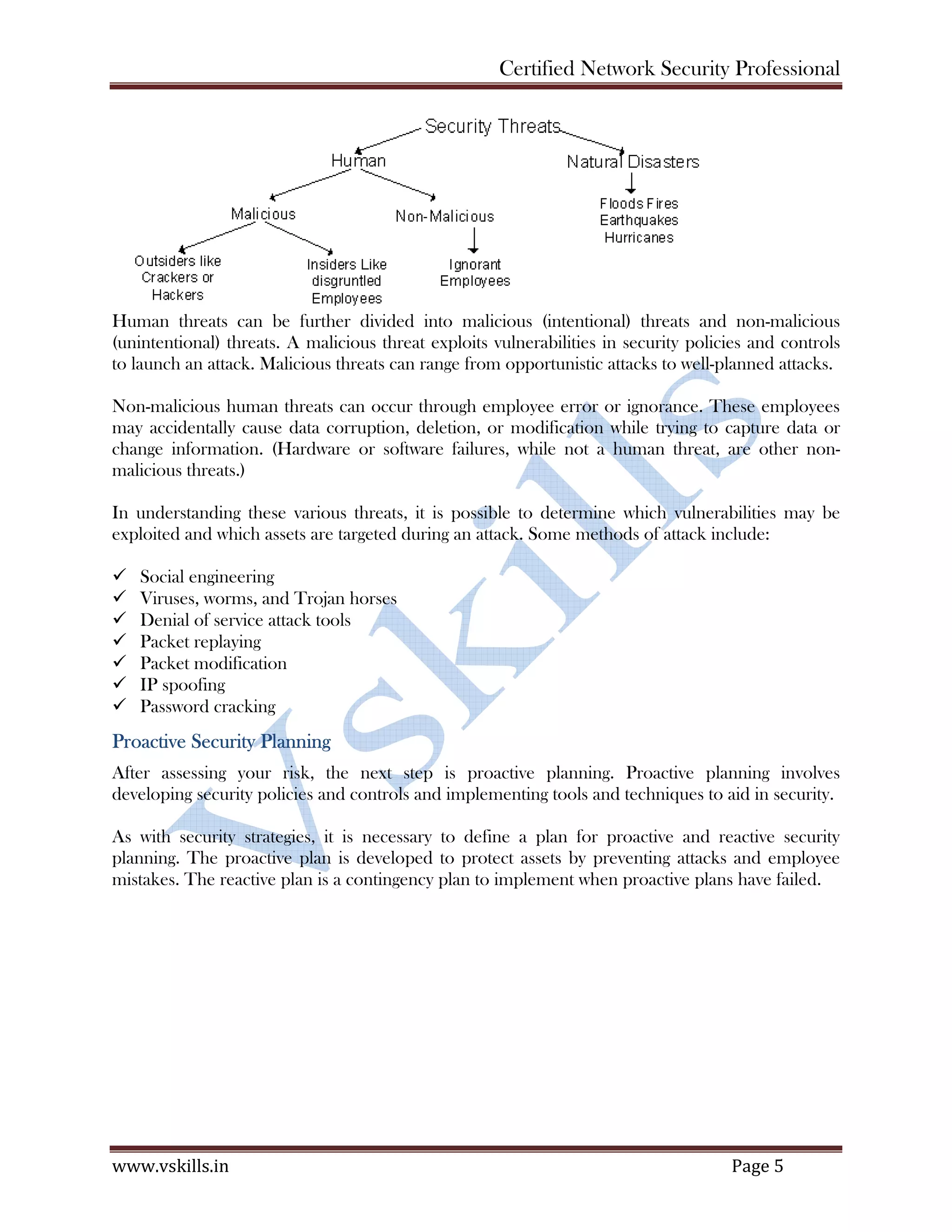
The document discusses security planning and policies. It begins by defining a security policy and information security management system (ISMS). It then discusses the importance of security planning, which involves risk assessment to identify assets, threats, and risks. The key aspects of risk assessment covered are identifying assets, risks to assets, and risk sources. It also discusses identifying security threats and contingency planning. Finally, it discusses different types of security policies an organization can implement, including password, email, internet, backup and access policies. The overall document provides guidance on developing a comprehensive security program through planning, policies and procedures.