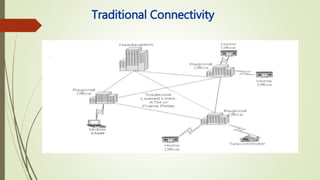
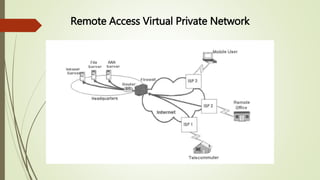
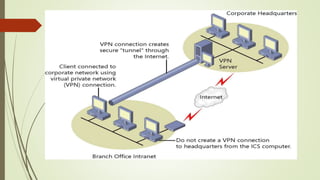
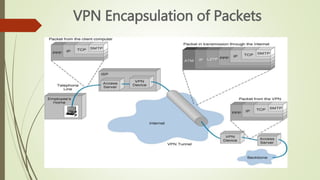
Virtual private networks (VPNs) allow employees to securely access a company's network from remote locations using public networks like the Internet. VPNs use encryption, authentication, and tunneling protocols to create secure connections between devices. There are different types of VPN implementations including intranet, extranet, and remote access VPNs used by employees to connect to their company network. VPNs can be set up using hardware devices like routers, firewalls, or software installed on devices.