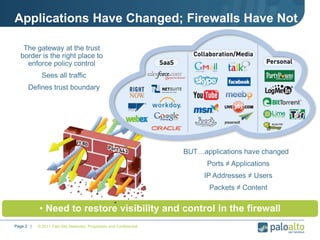
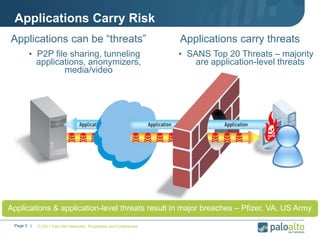
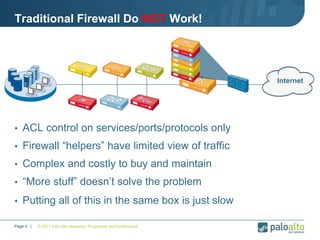
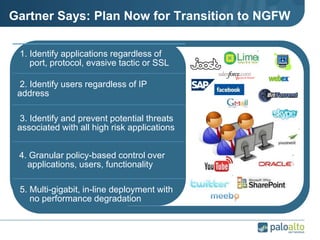
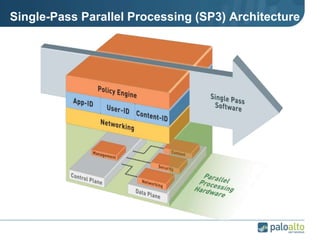
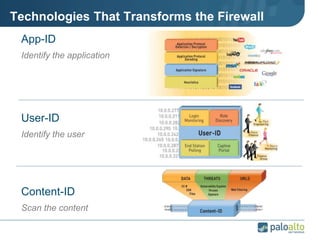
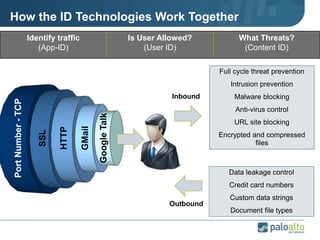
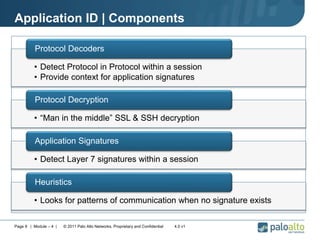
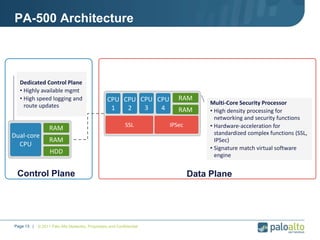
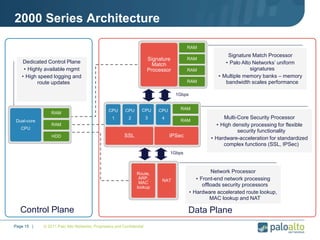
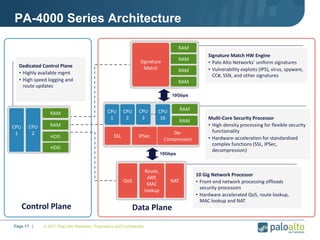
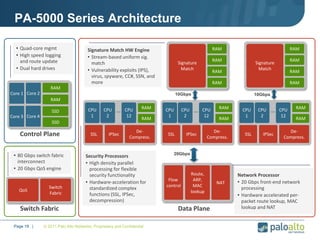
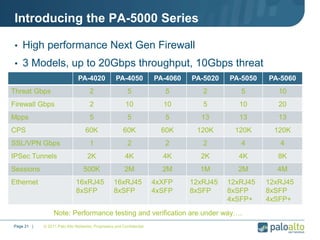
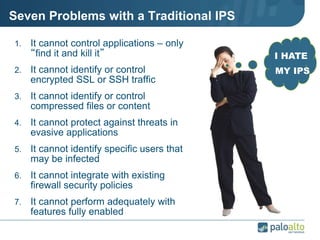
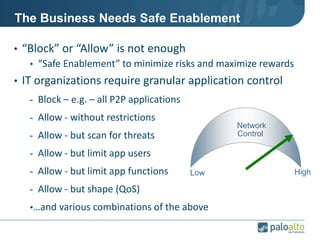
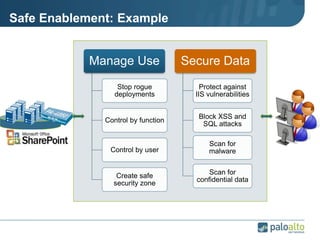
This document provides an overview of Palo Alto Networks next-generation firewall technology. It discusses how traditional firewalls do not provide visibility and control over applications. Next-gen firewalls can identify applications, users, and threats within encrypted traffic using techniques like App-ID, User-ID, and Content-ID. The document also describes Palo Alto Networks hardware models and their performance capabilities for handling firewall and threat prevention workloads. It highlights key next-gen firewall features like real-time threat analysis, application control, and safe enablement of network applications.