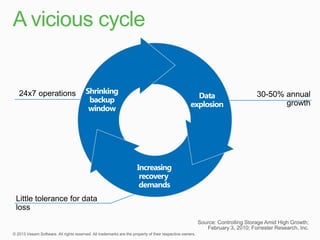
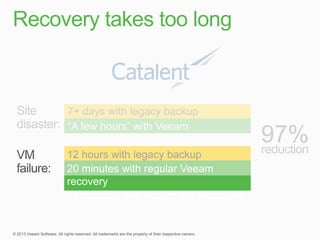
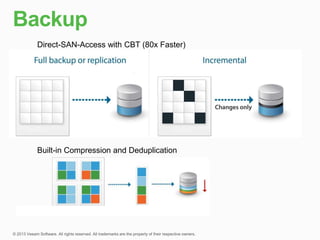
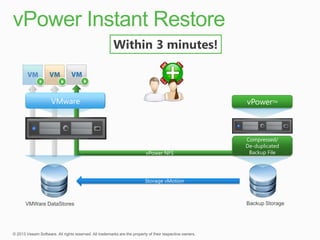
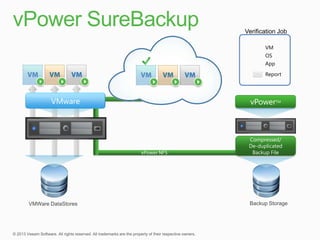
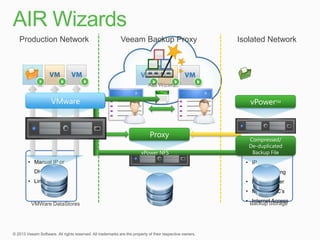
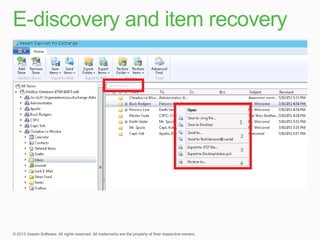
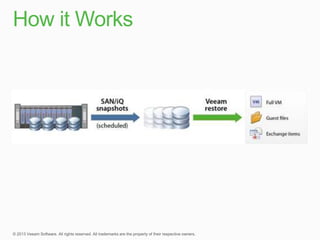
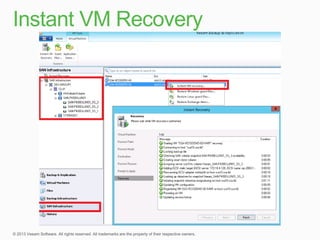
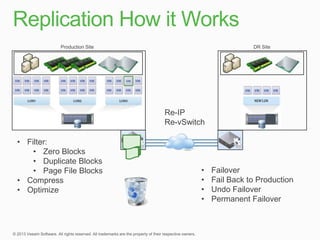
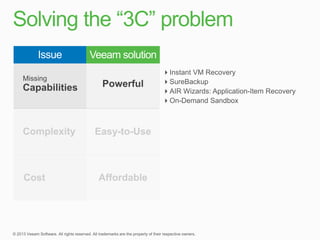
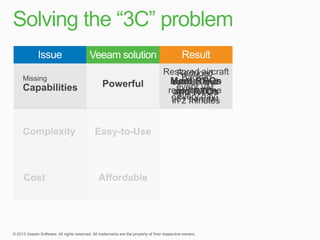
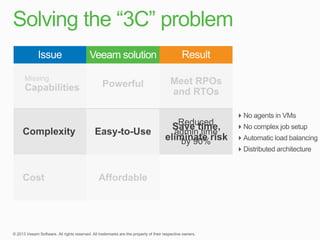
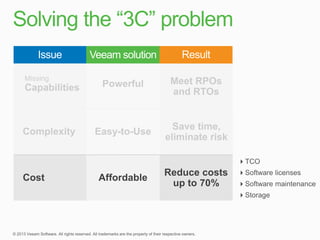
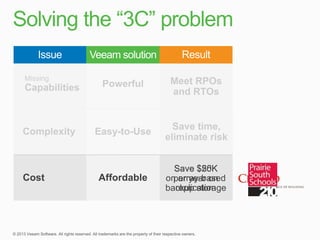
This document describes traditional backup methods for Exchange Server that require expensive agents, staging backups in a separate location, and a multi-step restore process. It then outlines Veeam's direct-SAN-access backup method that is 80x faster, uses built-in compression and deduplication, and allows restores to be completed within 3 minutes without agents or a staging area.