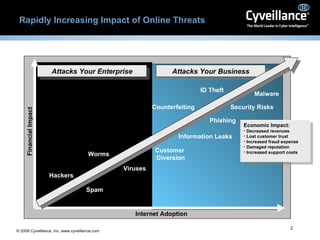
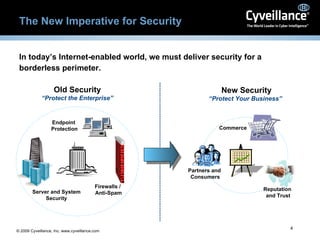
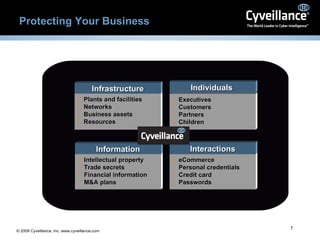
The document discusses cyber threats facing enterprises and the need for effective cyber intelligence and security. It introduces Cyveillance as offering a suite of online risk modules and intelligence services to help protect businesses, their assets, customers, and partners from a range of online threats. Key services mentioned include continuous internet monitoring, detection of risks like fraud and information leaks, and helping customers address threats faster than other systems. Testimonials from customers highlight how Cyveillance has helped them recapture lost revenues, identify compromised accounts, and detect planned actions by groups targeting their facilities.





![Contact Brent Peacher Senior Manager, Business Development (703)312-1203 [email_address]](https://image.slidesharecdn.com/osintoverview-12665119119785-phpapp02/85/Open-Source-Intelligence-Overview-11-320.jpg)