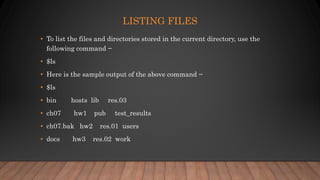
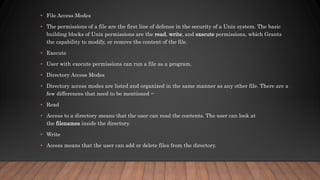
The document is a comprehensive tutorial on Unix/Linux, detailing its functionalities, file management, directory management, and permissions. It also covers the Unix environment, the use of pipes and filters, and process management. Starting from its development in 1969, the tutorial provides insights and commands necessary for understanding and using the Unix operating system effectively.