The document discusses topics related to UNIX including regular expressions, grep commands, UNIX shells, shell environment variables, and shell scripting. The agenda covers regular expressions and grep, UNIX shells, shell environment, and shell scripting. It provides examples and explanations of regular expressions, grep family commands, popular UNIX shells like Bourne shell, Korn shell, C shell, and Bourne-Again shell. It also discusses shell environment variables and how to set them as well as an introduction to shell scripting.


![CONFIDENTIAL© Copyright 2008
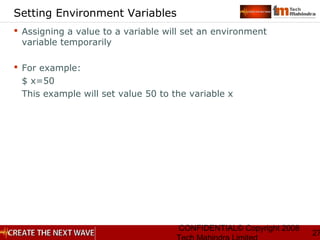
7
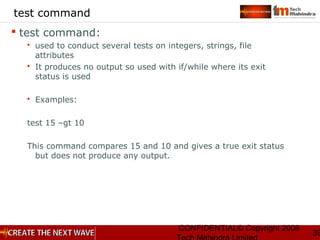
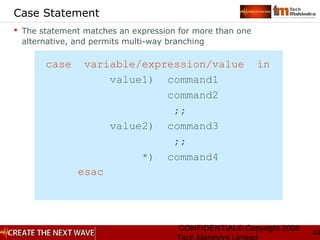
Basic Regular Expression
Quote the next metacharacter
^ Match the beginning of the line
. Match any character
$ Match the end of the line
[] Character class
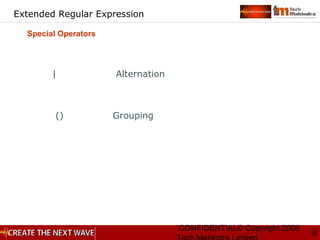
Special Operators](https://image.slidesharecdn.com/unixday2v1-151119173857-lva1-app6891/85/Unix-day2-v1-3-7-320.jpg)
![CONFIDENTIAL© Copyright 2008
9
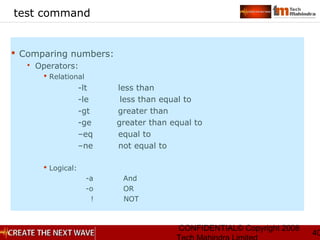
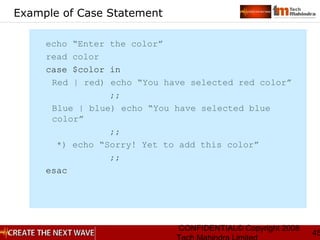
Examples
“a.g” matches aag, abg, a1g, etc
“a[pmt]g” matches apg, amg or atg
“a[^pmt]g” matches aag, abg but not apg or amg or atg
“^ftp” matches ftp at the beginning of a line
“tle$” matches tle at the end of a line
“^$” matches a line with nothing in it
“jelly|cream” matches either jelly or cream
“(eg|pe)gs” matches either eggs or pegs](https://image.slidesharecdn.com/unixday2v1-151119173857-lva1-app6891/85/Unix-day2-v1-3-9-320.jpg)

![CONFIDENTIAL© Copyright 2008
11
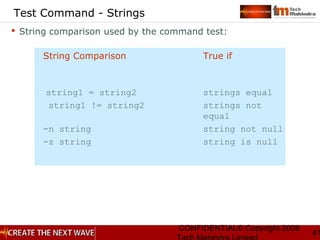
Examples
“adg*” ad followed by zero or more g characters
“.*” Any character, any number of times
“[qjk]” Either q or j or k
“[^qjk]” Neither q nor j nor k
“[a-z]” Anything from a to z inclusive
“[^a-z]” No lower case letters
“[a-zA-Z]” Any letter
“[a-z]+” Any non-zero sequence of lower case letters
“(da)+” Either da or dada or dadada or...](https://image.slidesharecdn.com/unixday2v1-151119173857-lva1-app6891/85/Unix-day2-v1-3-11-320.jpg)
![CONFIDENTIAL© Copyright 2008
13
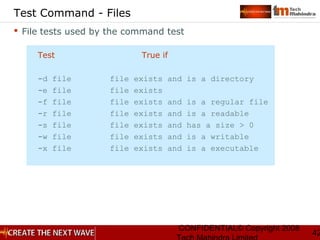
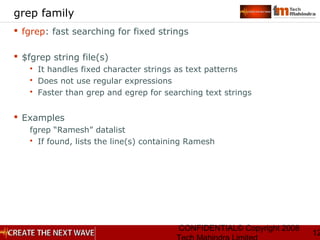
grep family
grep: is called as a global regular expression printer
It searches for a given pattern in a file(s)
$ grep -[cvnl] [pattern] [files]
Option Description
-c counts the total no of lines containing the pattern
-v displays all the lines not containing the pattern
-n displays lines with line number
-l displays file names containing the pattern
Example:
grep “Agg*[ra][ra]wal” datalist
It lists all lines where the pattern matches some text
The possible matches for the text are:
Agrawal, Agarwal, Aggarwal, Aggrawal
(and many more combinations possible)](https://image.slidesharecdn.com/unixday2v1-151119173857-lva1-app6891/85/Unix-day2-v1-3-13-320.jpg)









![CONFIDENTIAL© Copyright 2008
38
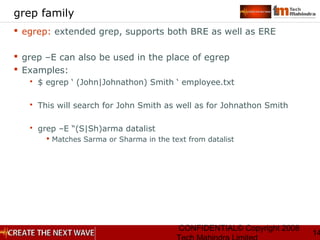
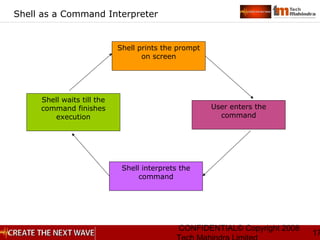
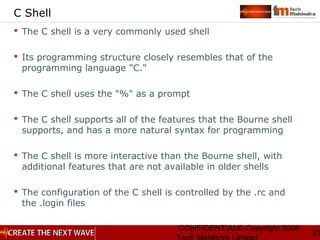
Shell Meta Characters
Wildcard substitution: * ? []
Redirection: >, >>, <, 2>, <<
Piping: |
Command substitution: ` `
Sequential commands: semicolon (;)
Inserting comment: #
Command grouping: () parenthesis](https://image.slidesharecdn.com/unixday2v1-151119173857-lva1-app6891/85/Unix-day2-v1-3-38-320.jpg)