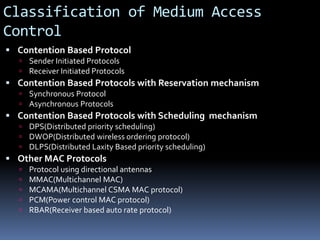
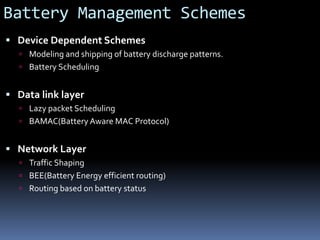
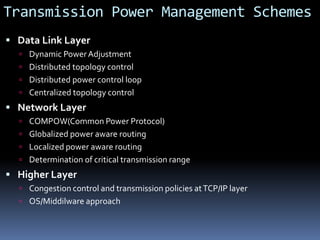
This document discusses various topics related to ad-hoc wireless networks including wireless network concepts, radio propagation mechanisms, characteristics of wireless channels, cellular networks, ad hoc networks, medium access control, routing protocols, multicasting, and transport layer protocols for ad hoc networks. It provides classifications and examples of different types of network architectures, protocols, and issues/challenges in ad hoc wireless networks.