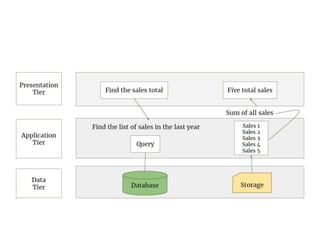
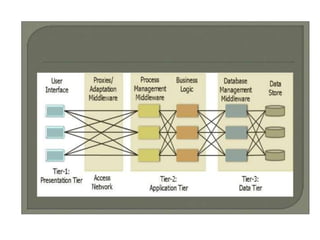
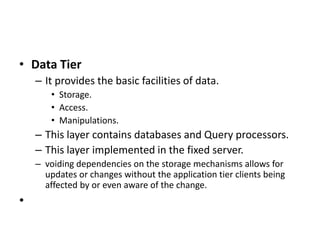
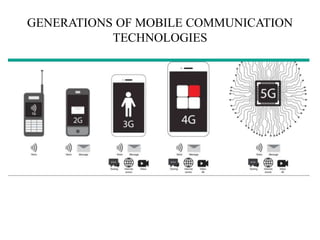
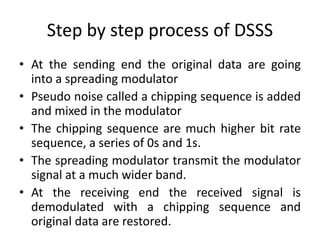
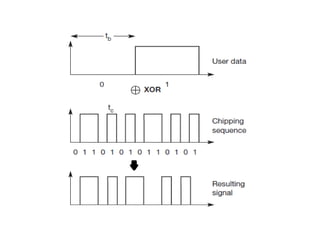
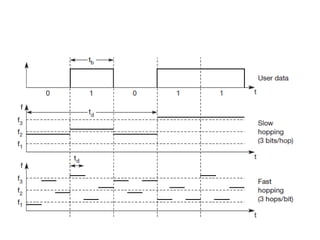
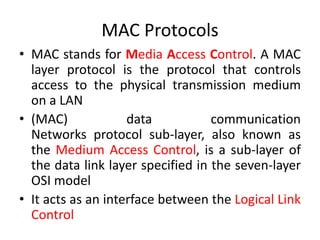
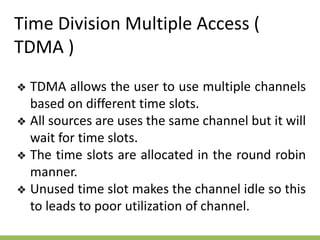
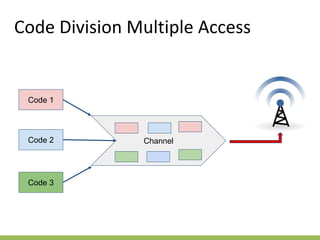
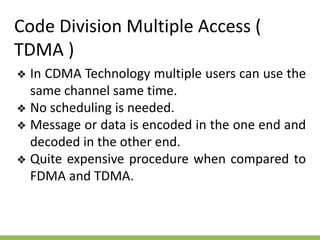
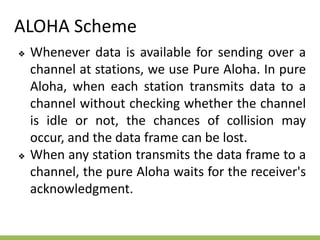
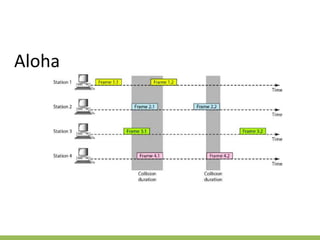
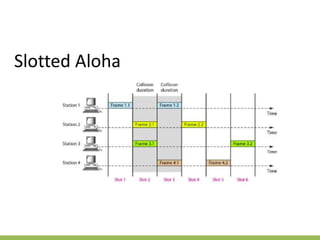
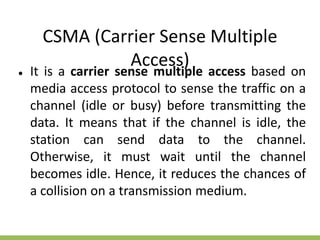
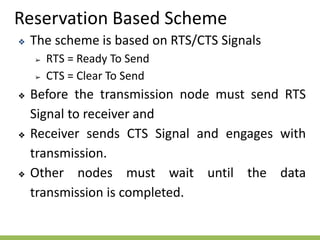
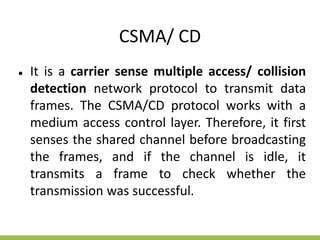
The document discusses the key concepts of mobile computing including:
1. It defines mobile computing and distinguishes it from wireless networking, noting that mobile computing allows transmission of data, voice and video via wireless enabled devices without a fixed link.
2. It covers the main components of mobile computing including mobile communication, mobile hardware like smartphones and tablets, and mobile software like operating systems.
3. It provides examples of applications of mobile computing in various domains like vehicles, emergencies, and business. It also discusses location-dependent and location-aware services.