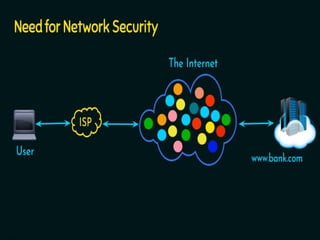
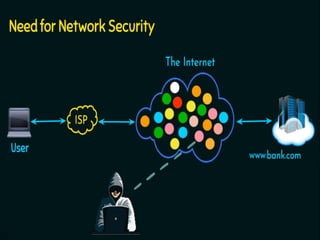
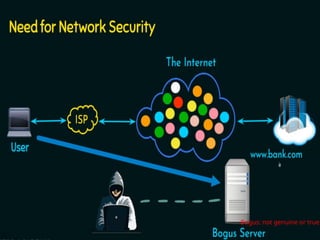
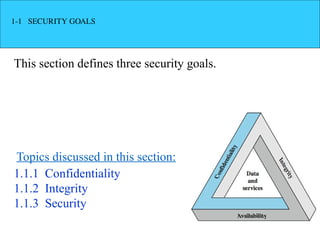
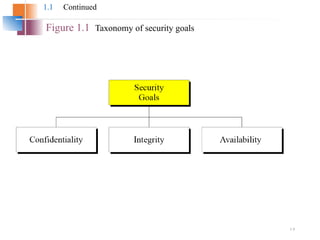
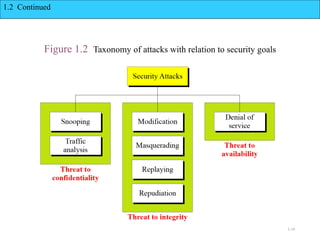
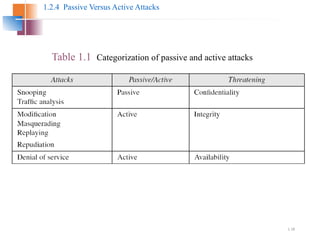
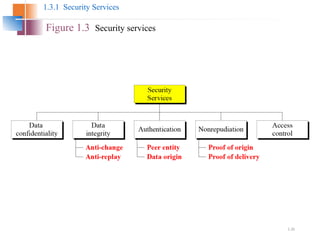
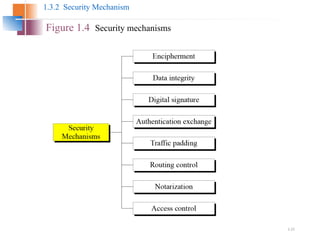
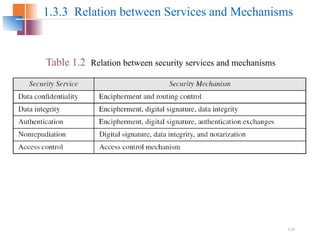
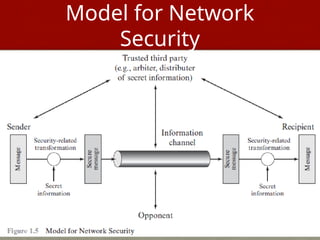
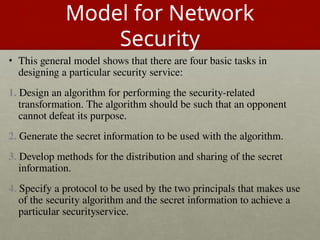
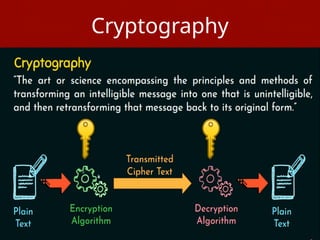
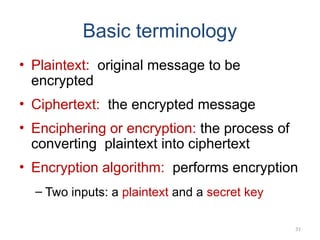
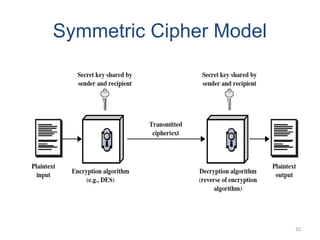
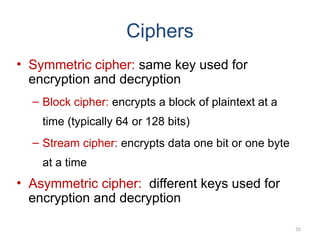
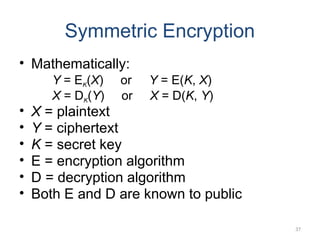
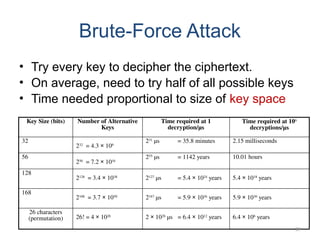
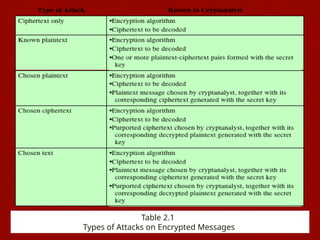
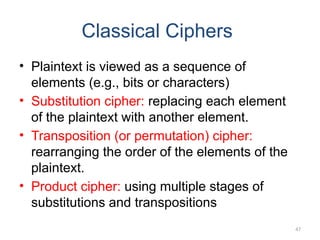
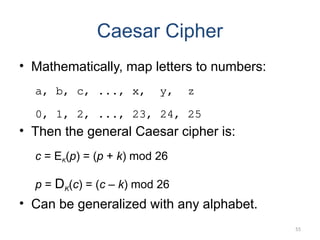
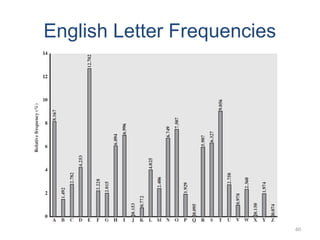
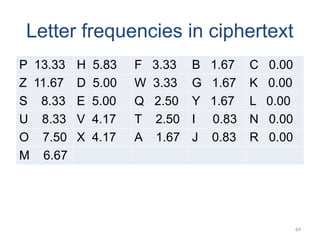
The document introduces basic concepts and terminology of information security, focusing on the three primary security goals: confidentiality, integrity, and availability. It discusses various security attacks that threaten these goals, as well as services and mechanisms to counteract them, including cryptography and steganography as key techniques for information security. Additionally, it covers different types of cryptographic methods, encryption algorithms, and the principles of cryptanalysis to protect information integrity.