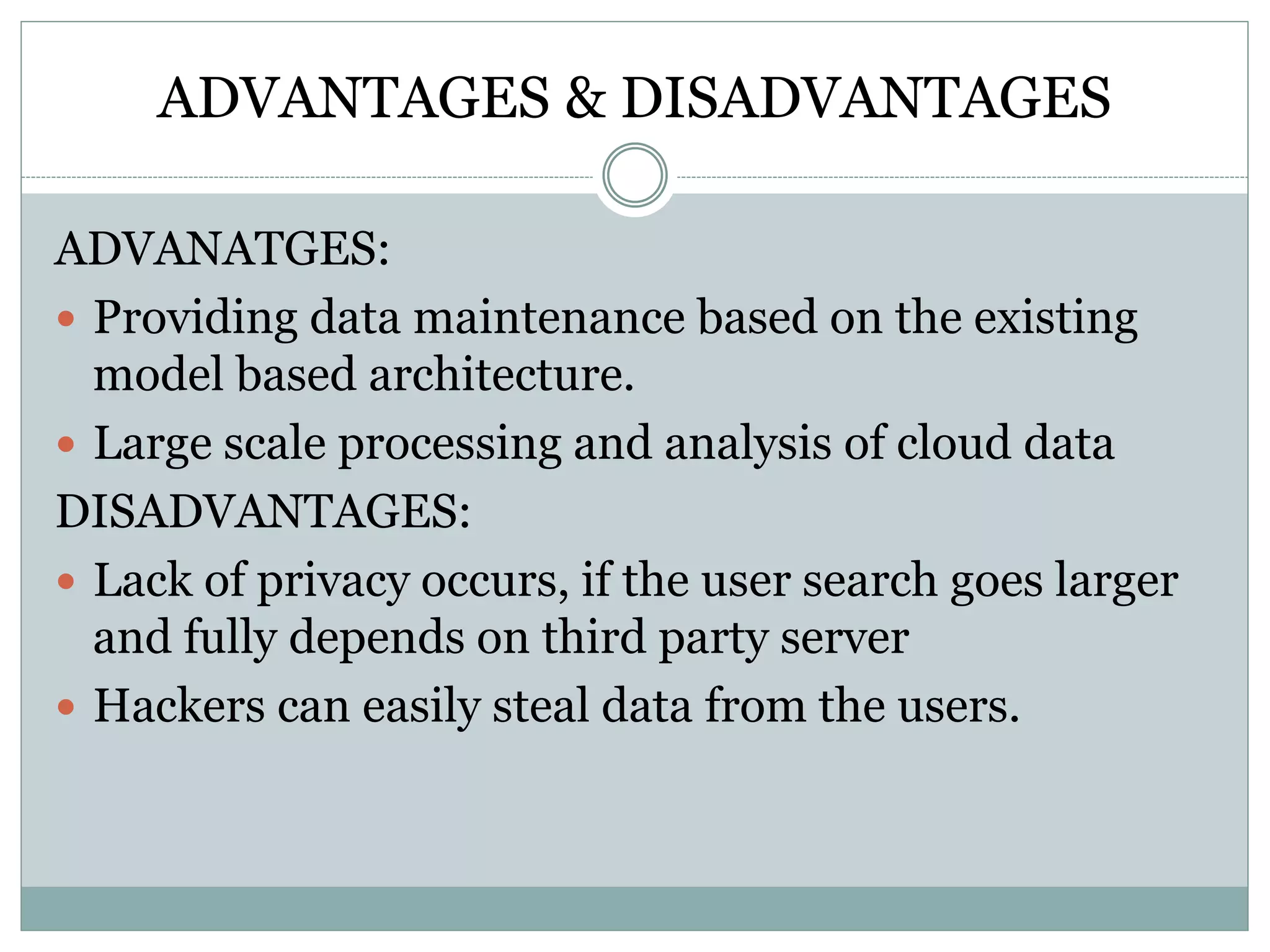
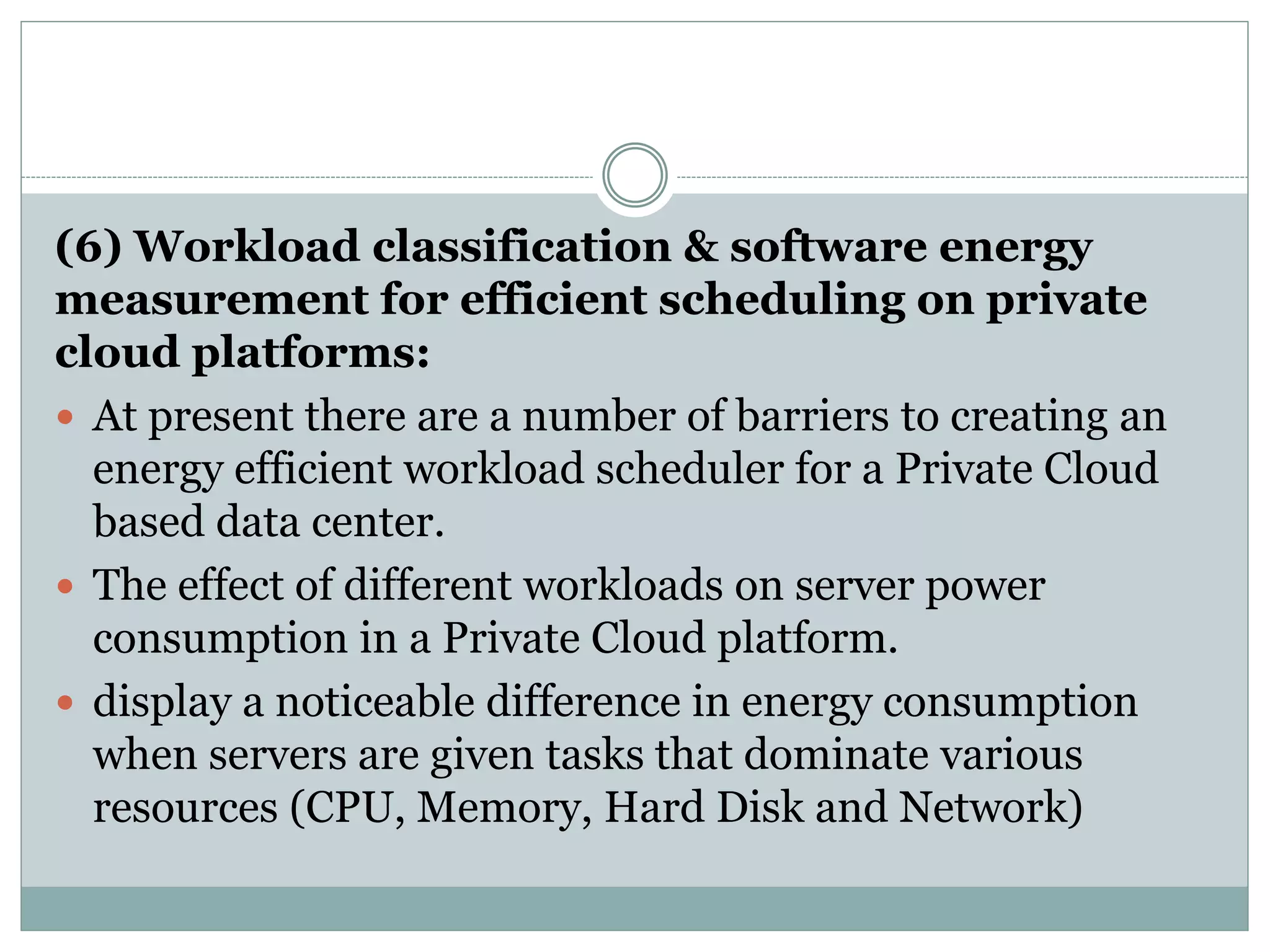
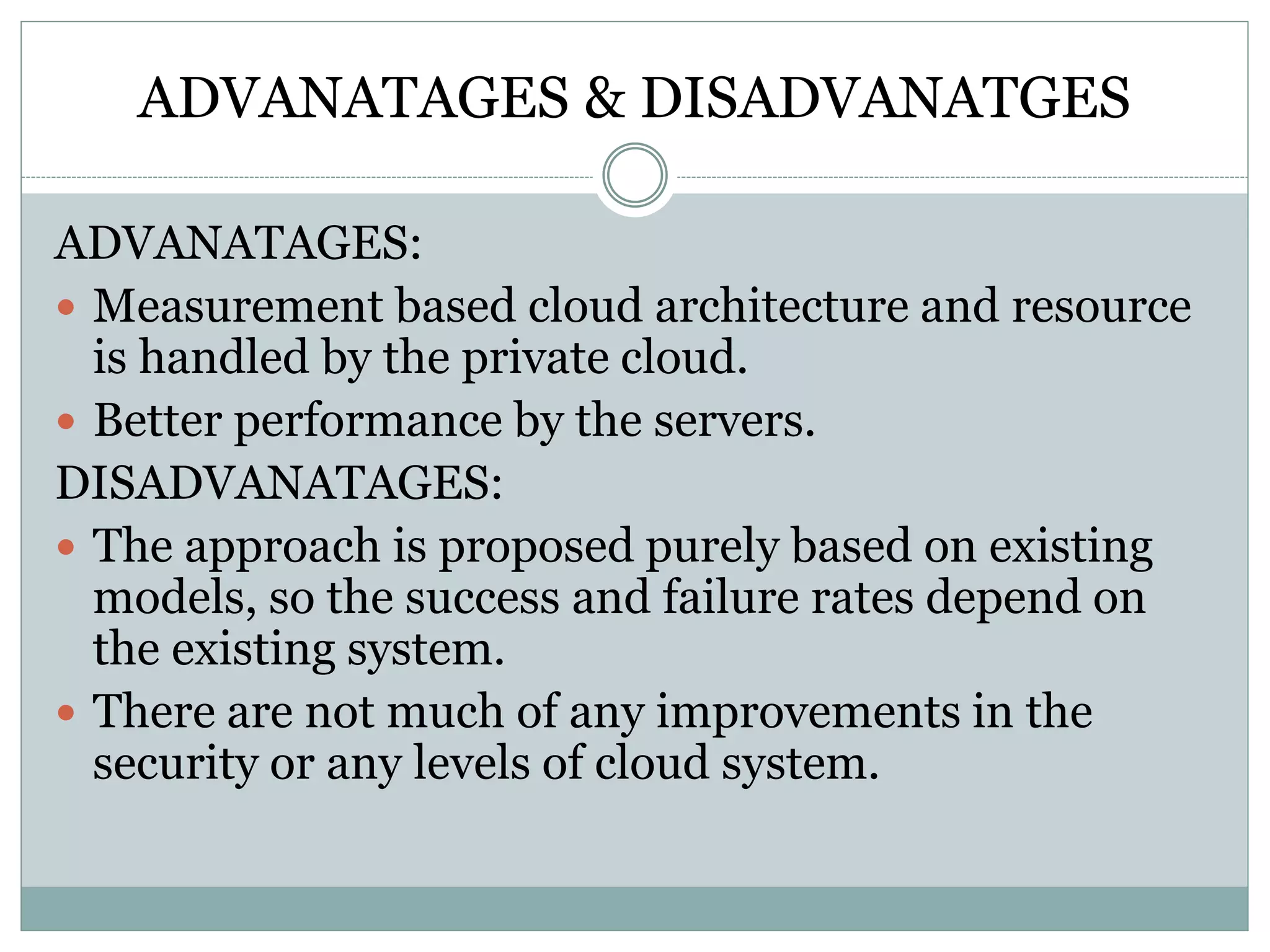
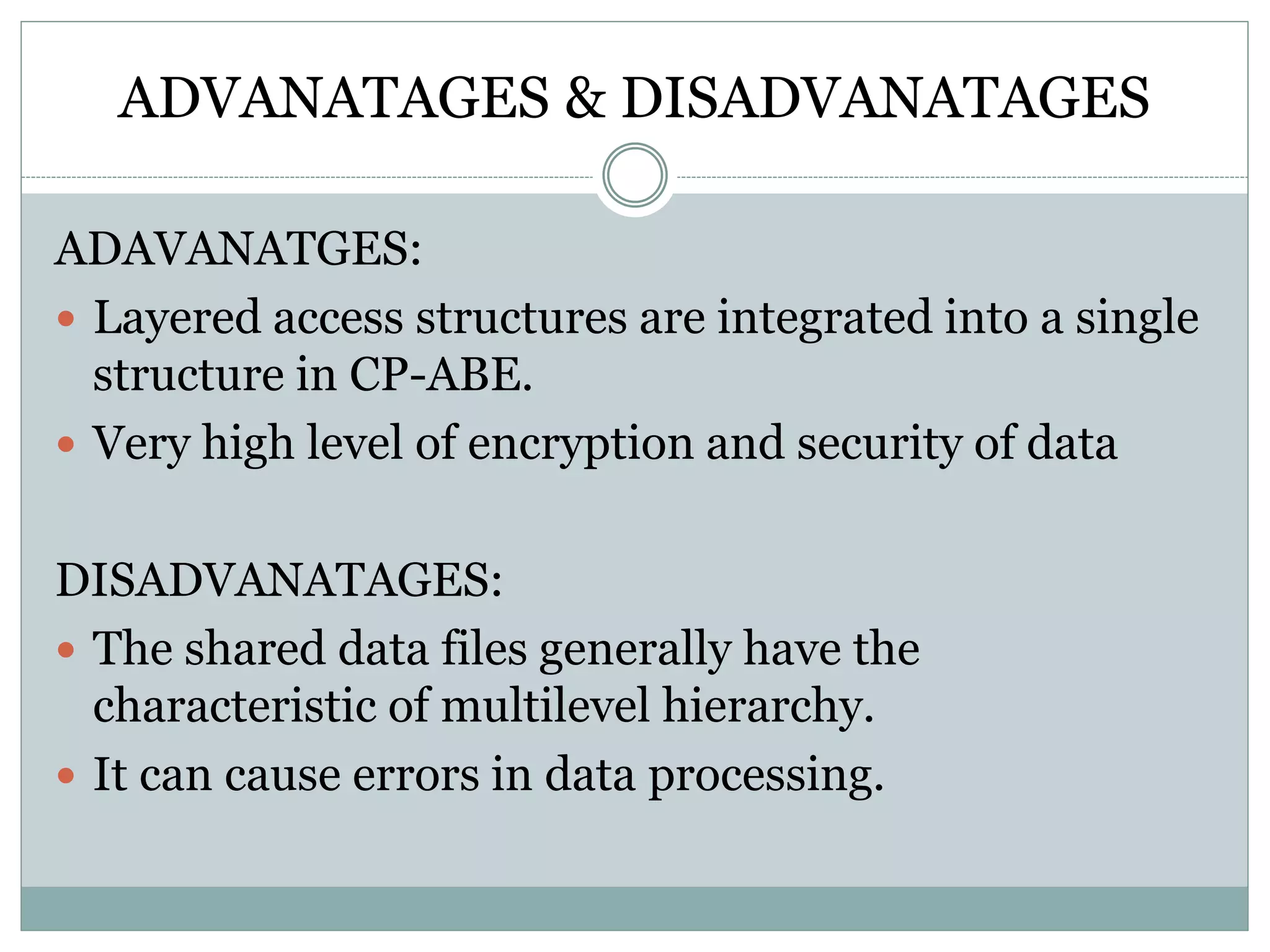
The document discusses various approaches for enhancing security in cloud computing and web services, including fine-grained two-factor authentication, workload characterization, and encryption schemes. It presents both advantages, such as improved security measures and scalable architectures, and disadvantages, including complexity and potential privacy risks. Overall, it emphasizes the need for robust security protocols to counteract threats like phishing and unauthorized access.