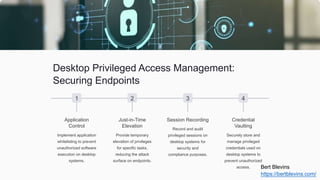
The document provides a comprehensive guide on various aspects of cybersecurity, including password management, privileged access management, the role of chatbots, and identity security. It emphasizes the importance of centralized solutions, automated processes, and proactive monitoring to protect digital assets. Additionally, it covers best practices for incident response, cyber insurance, and managing third-party vendor access.