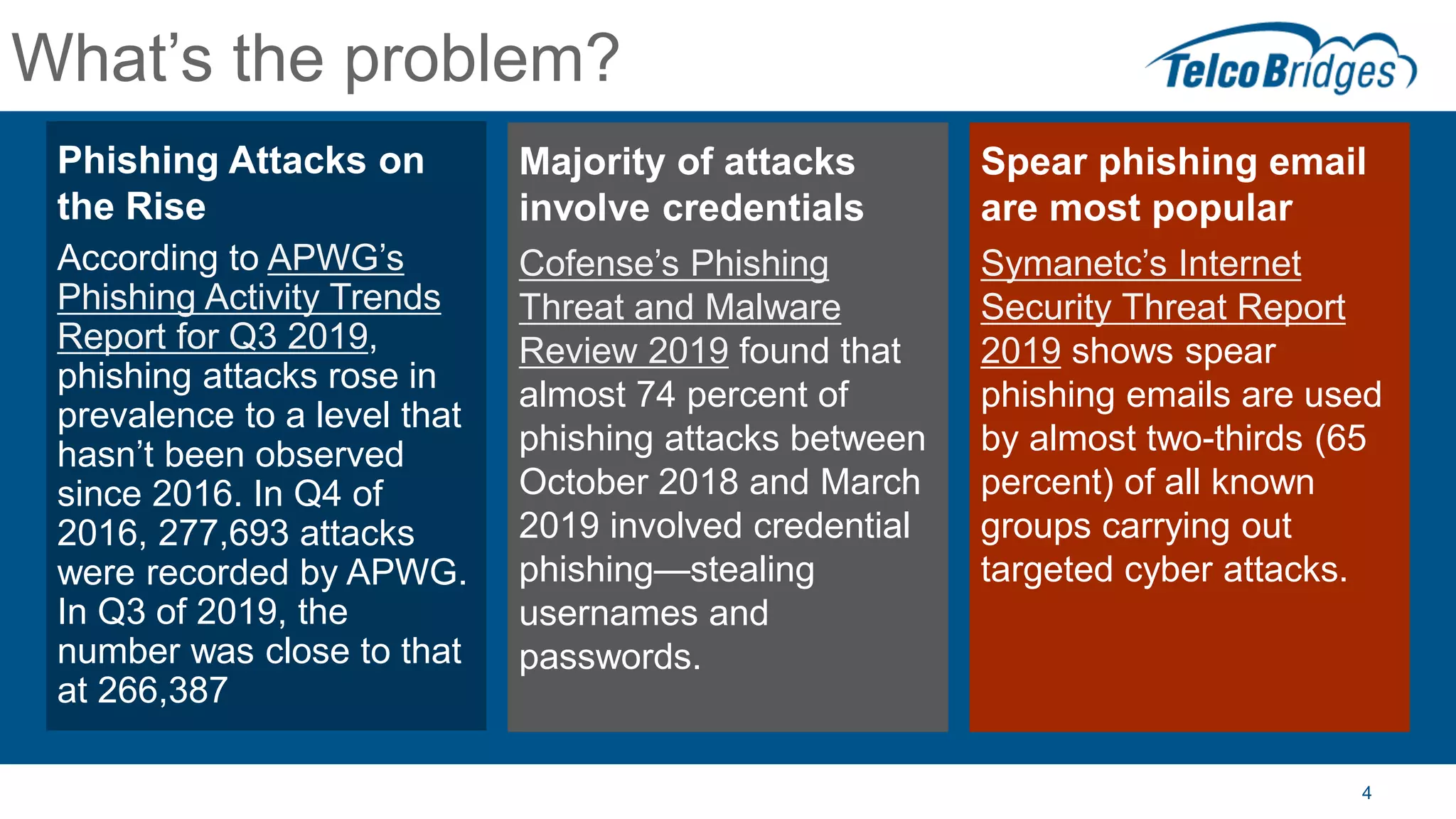
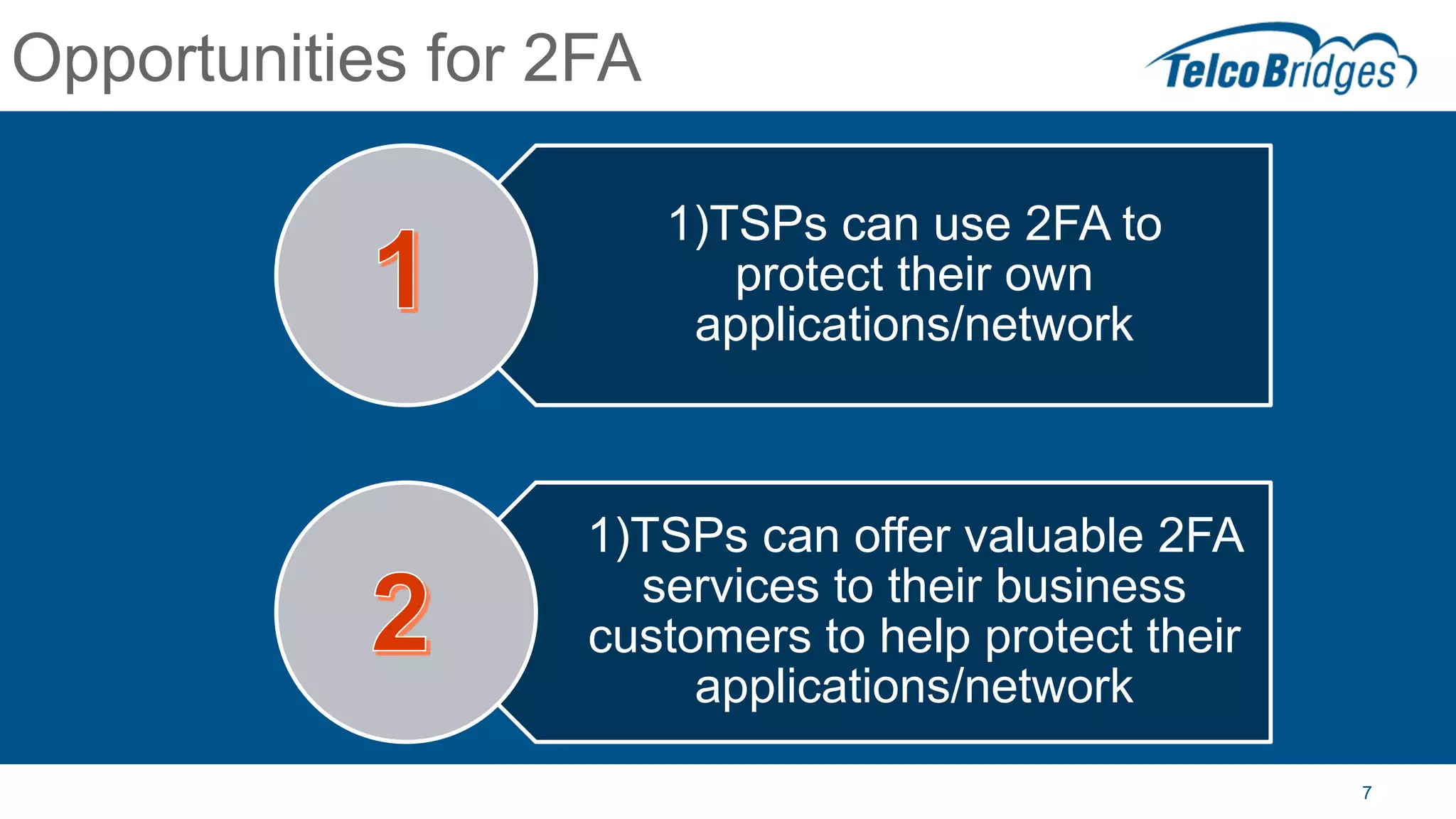
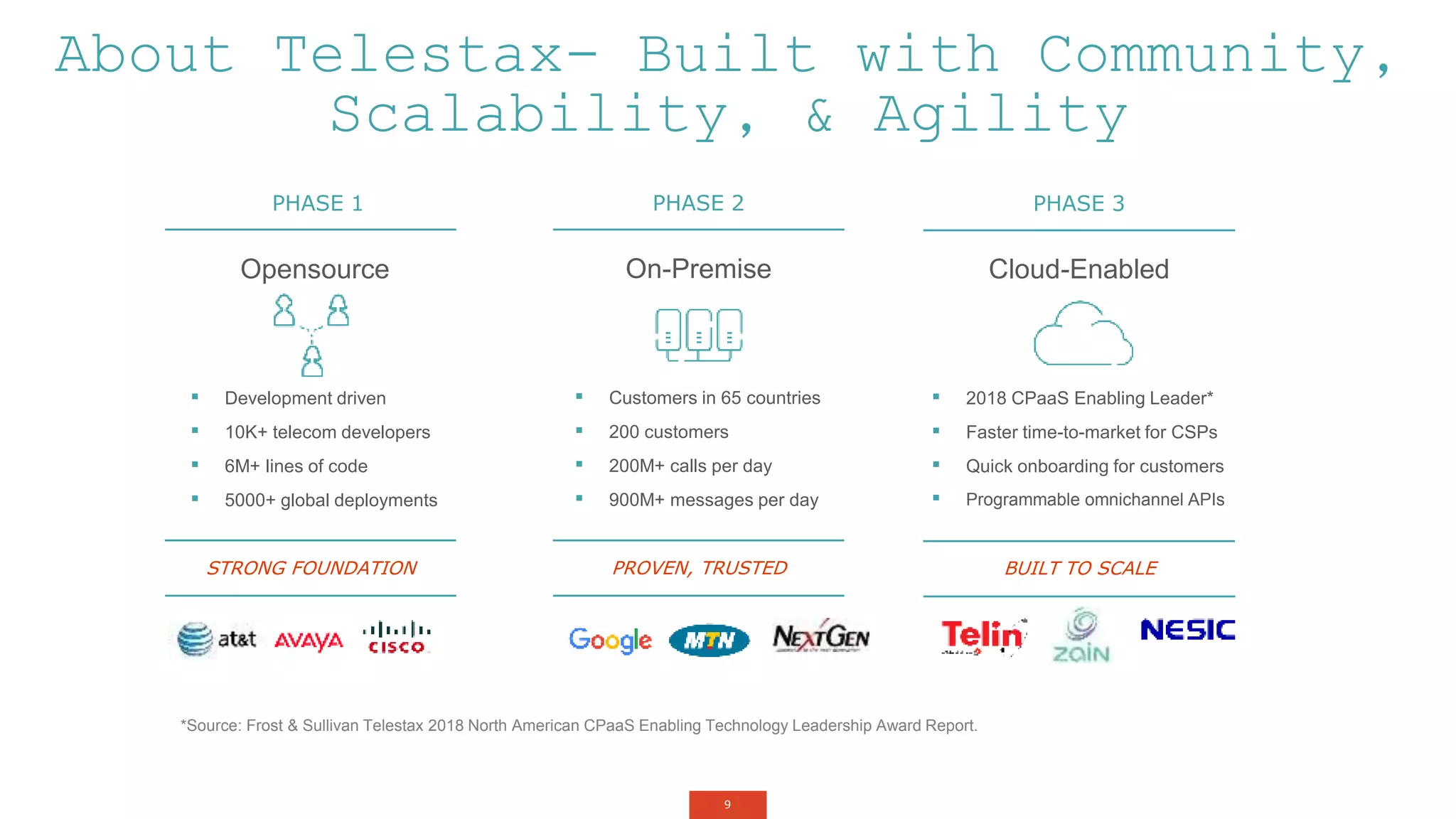
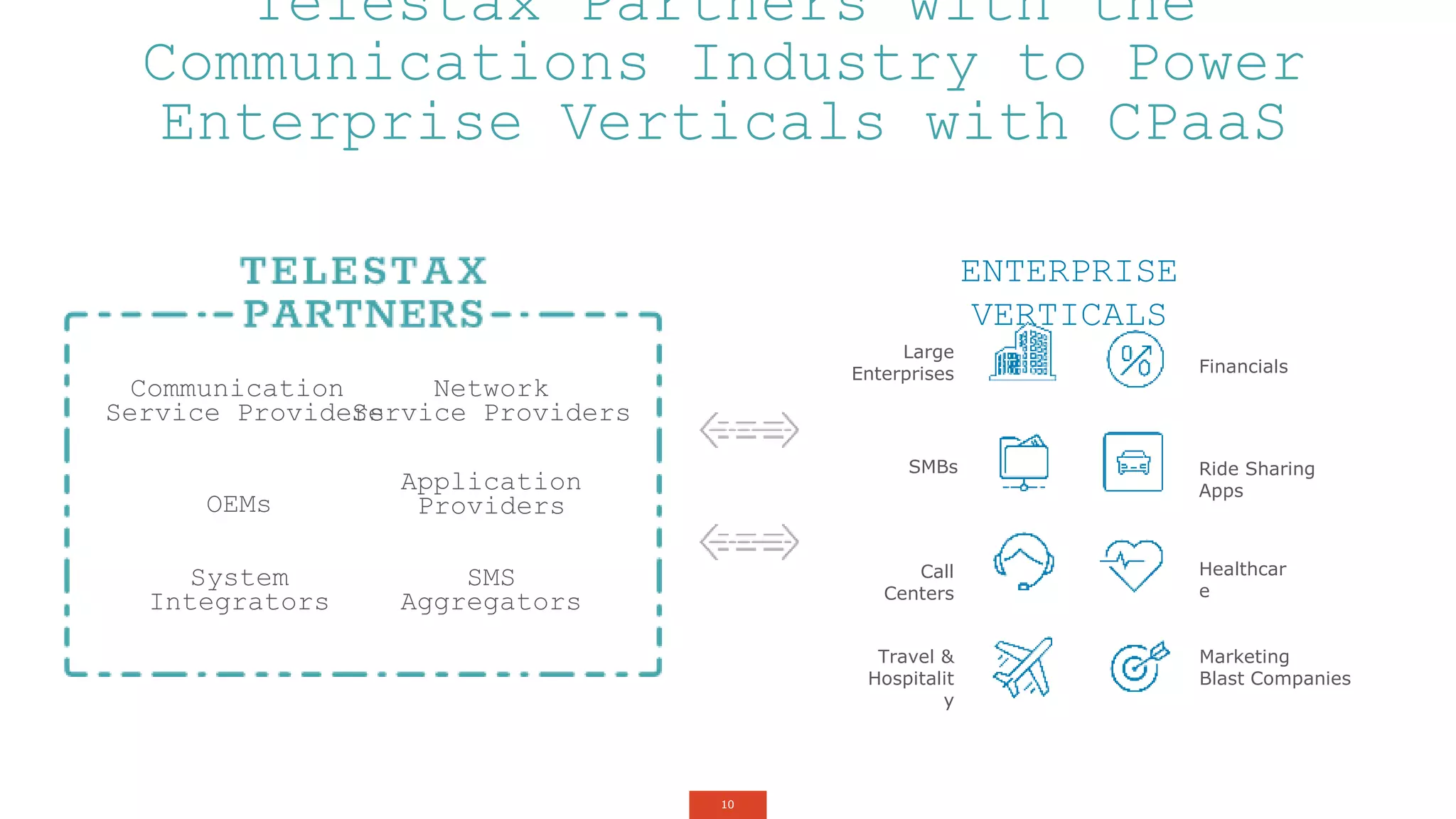
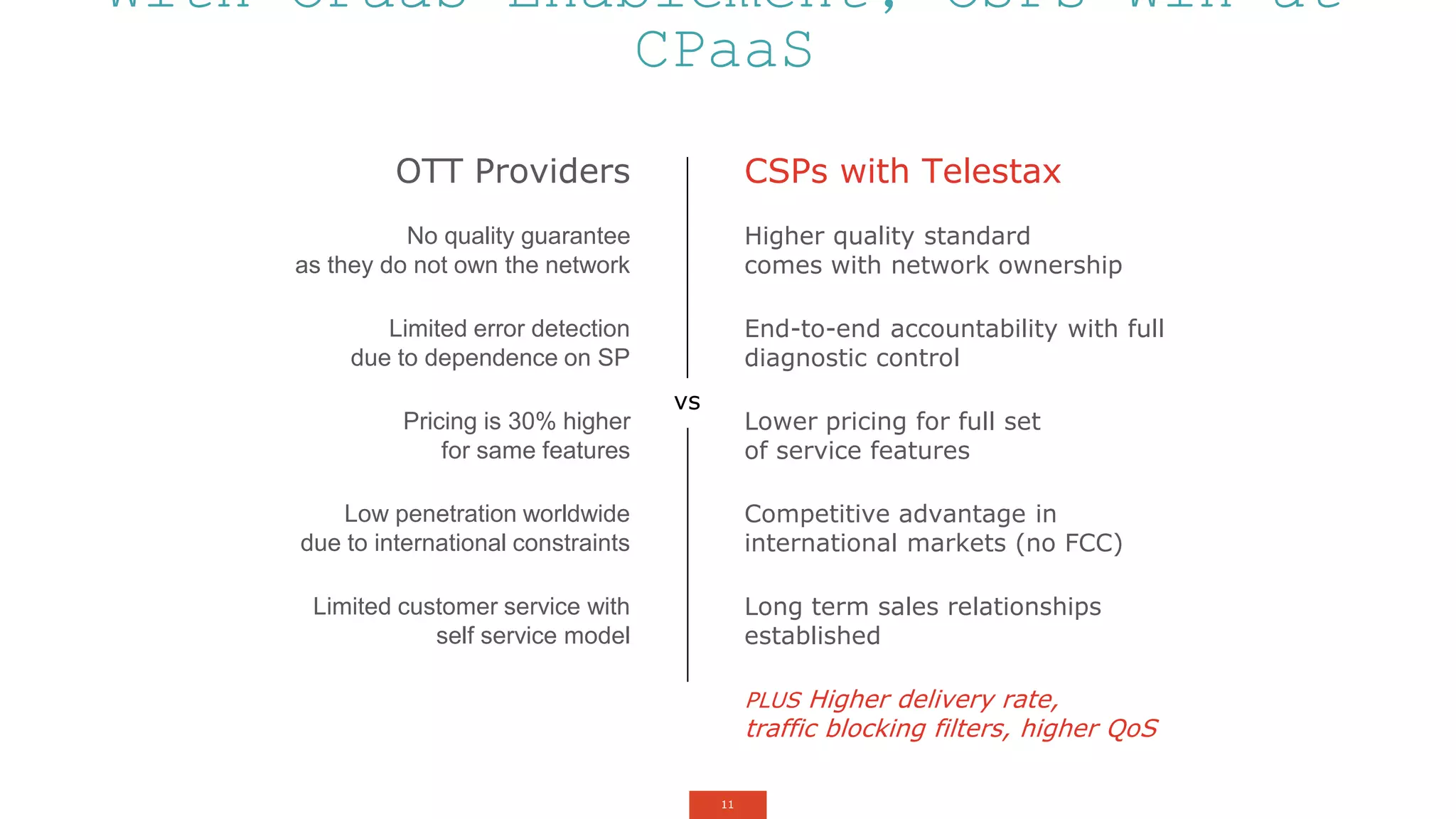
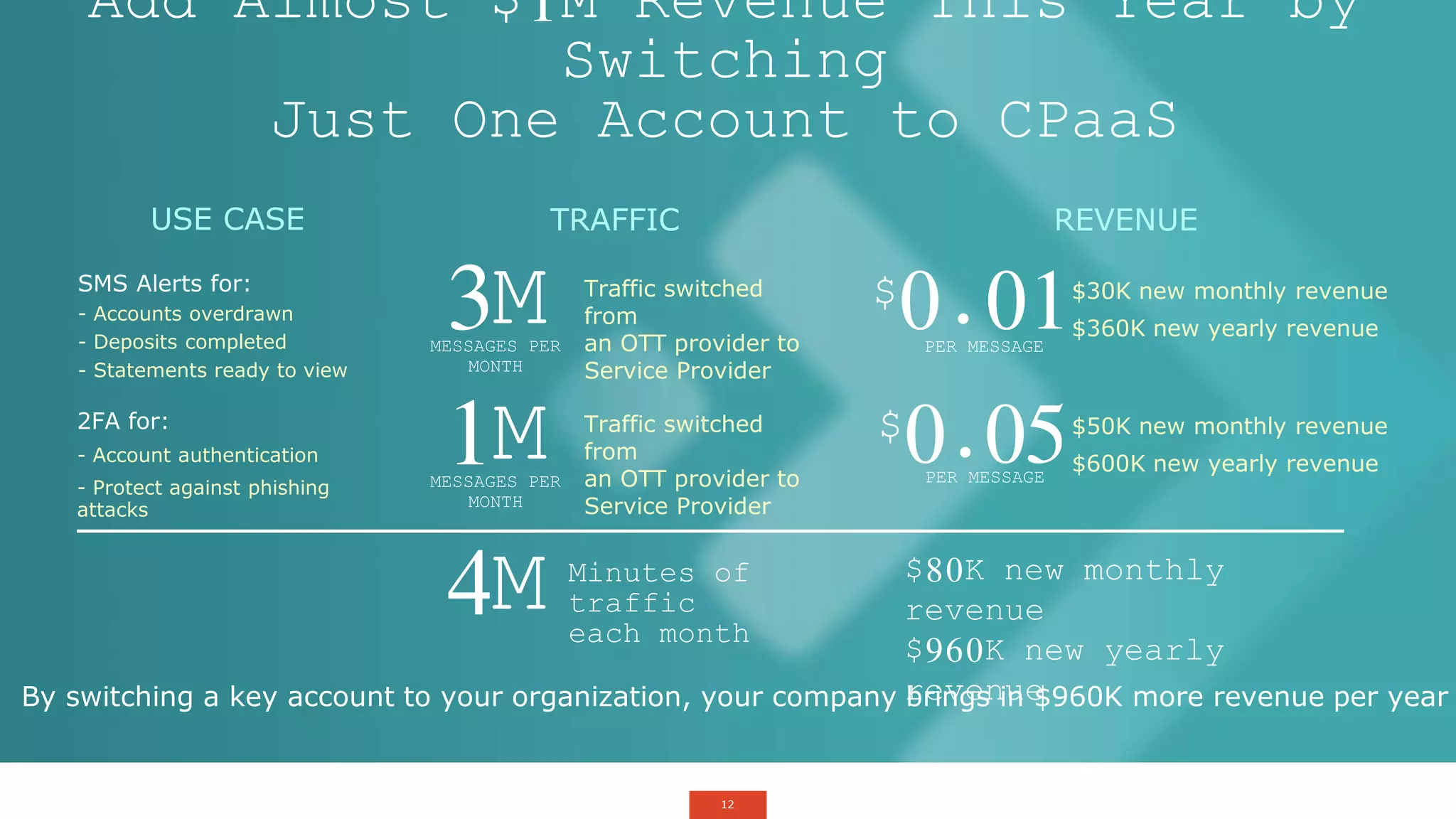
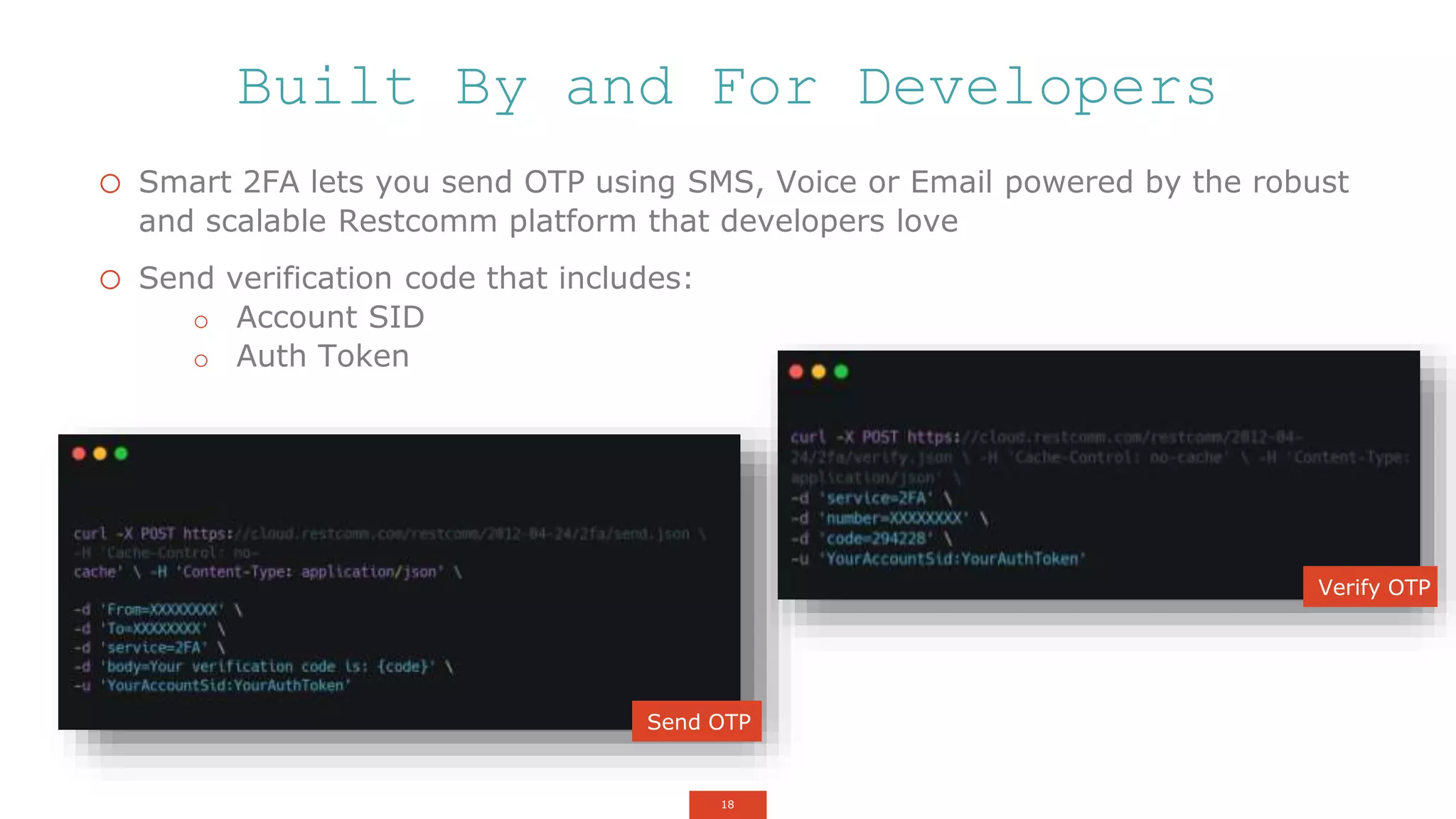
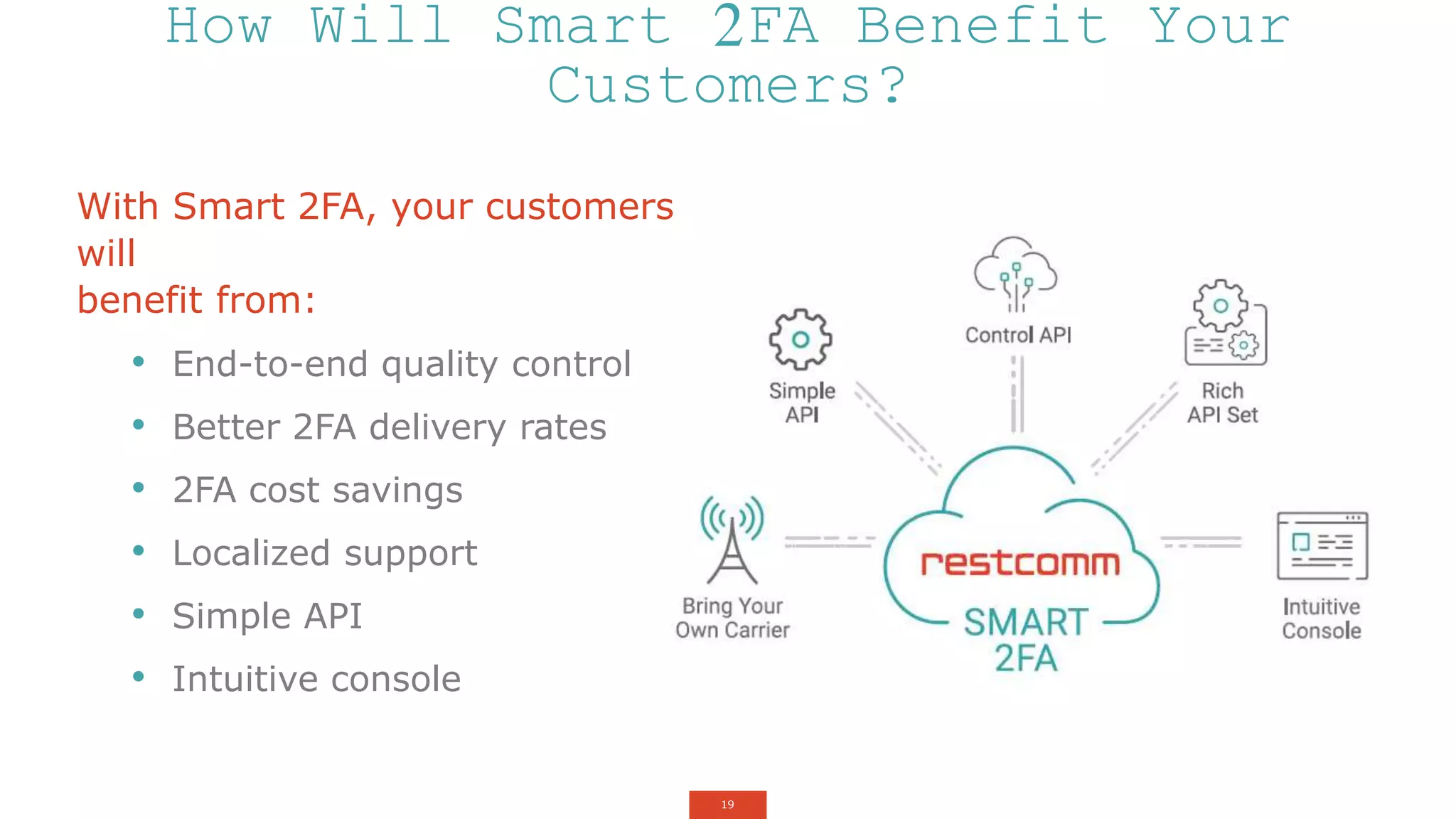
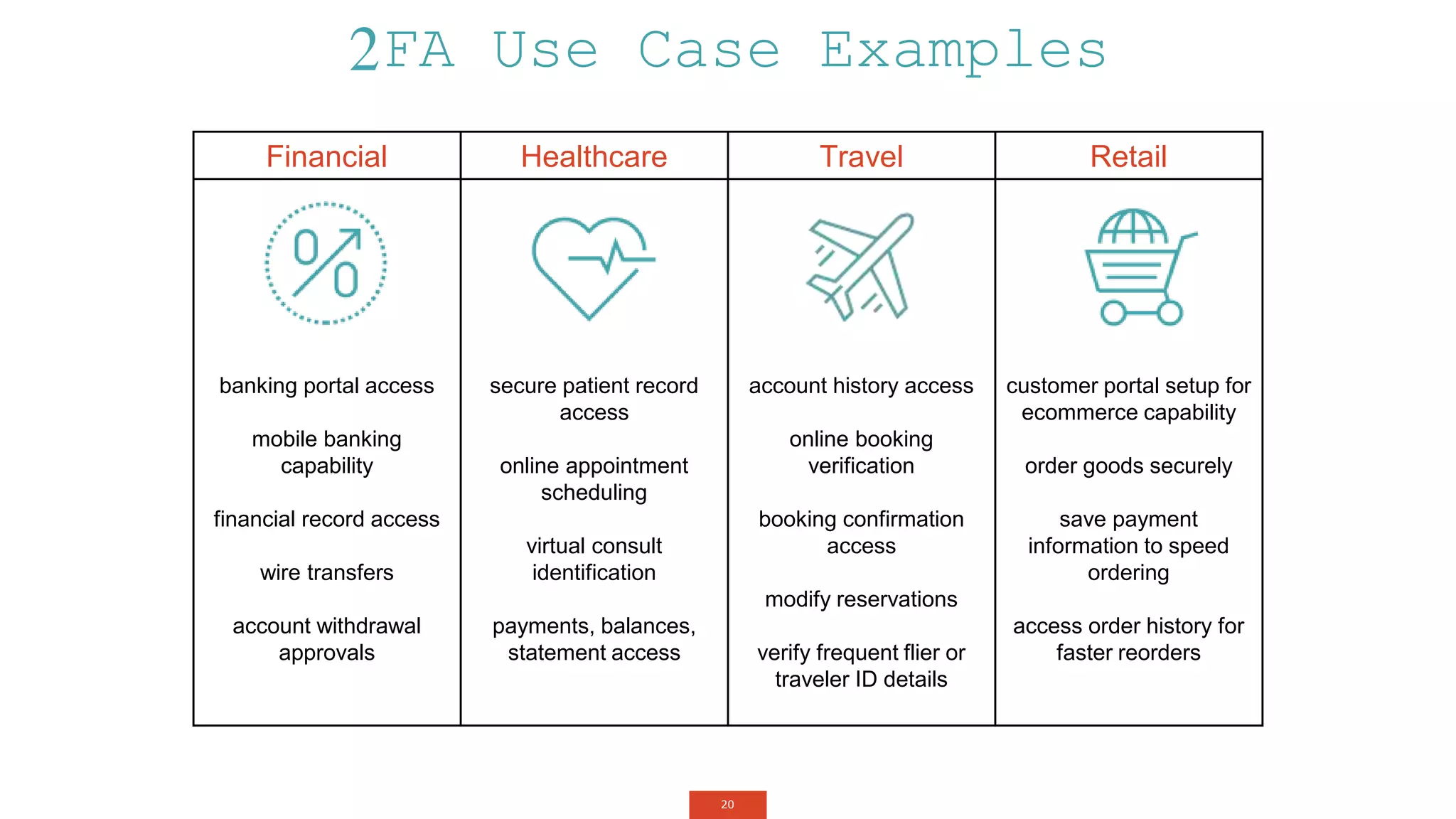
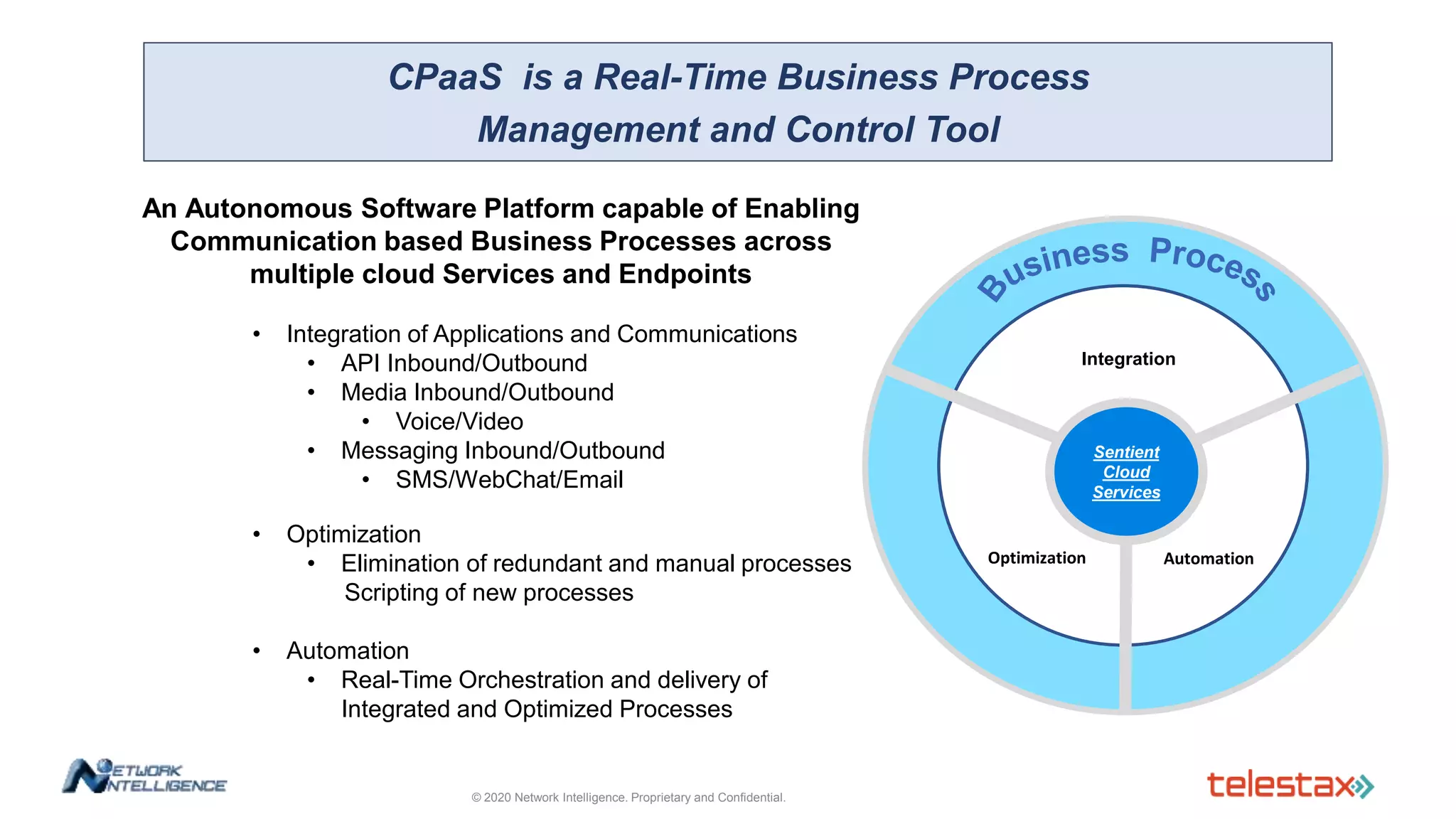
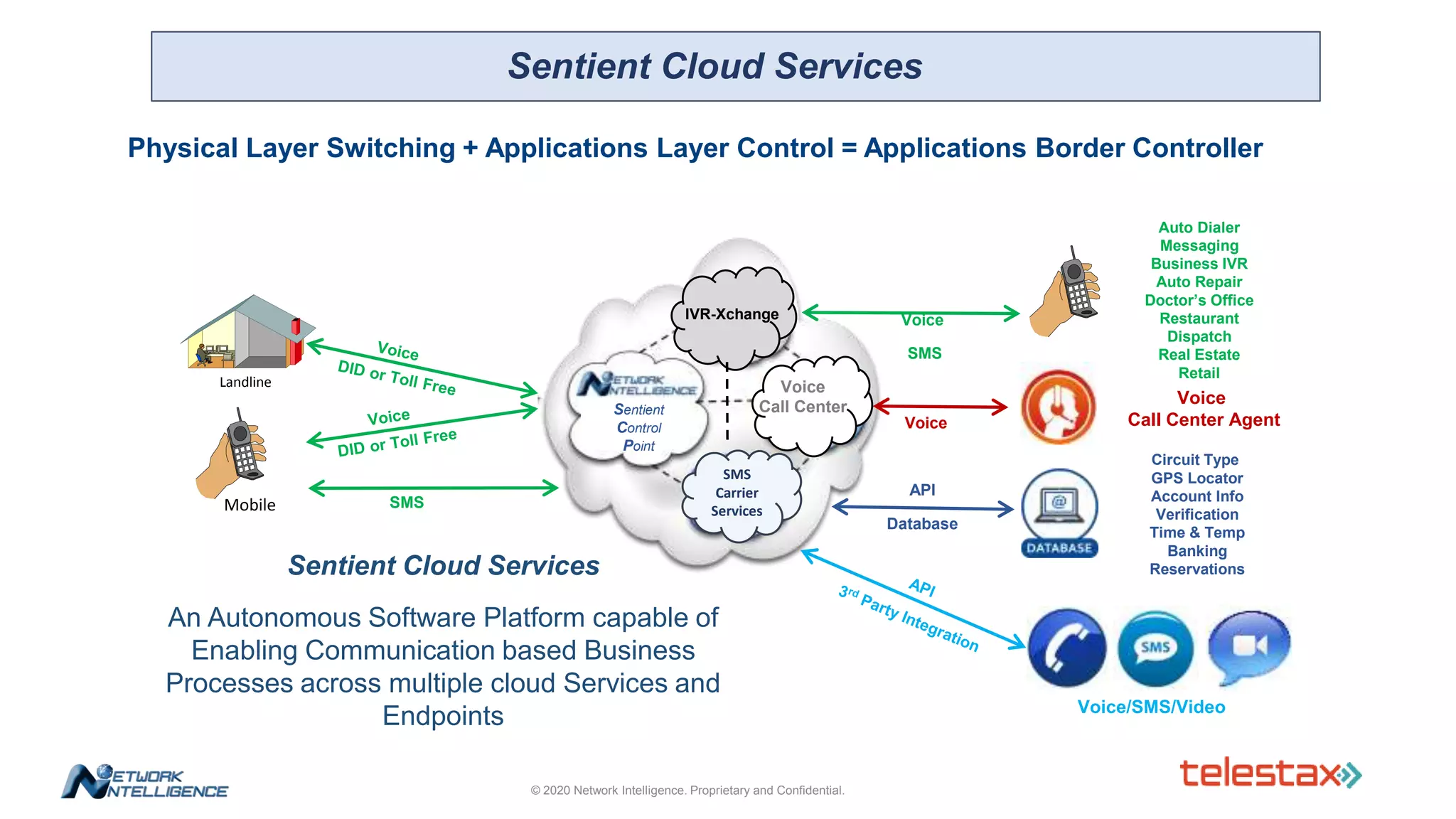
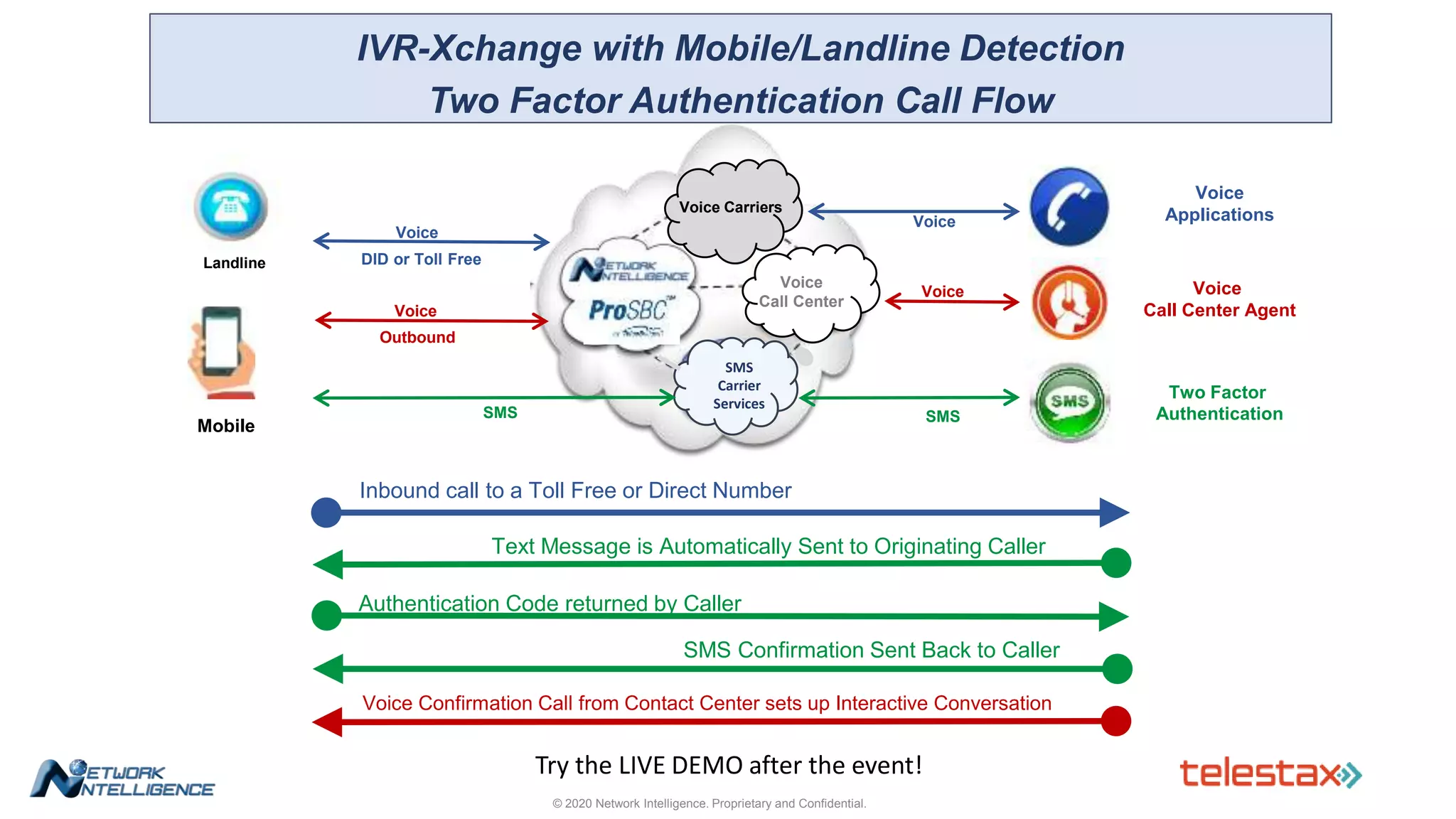
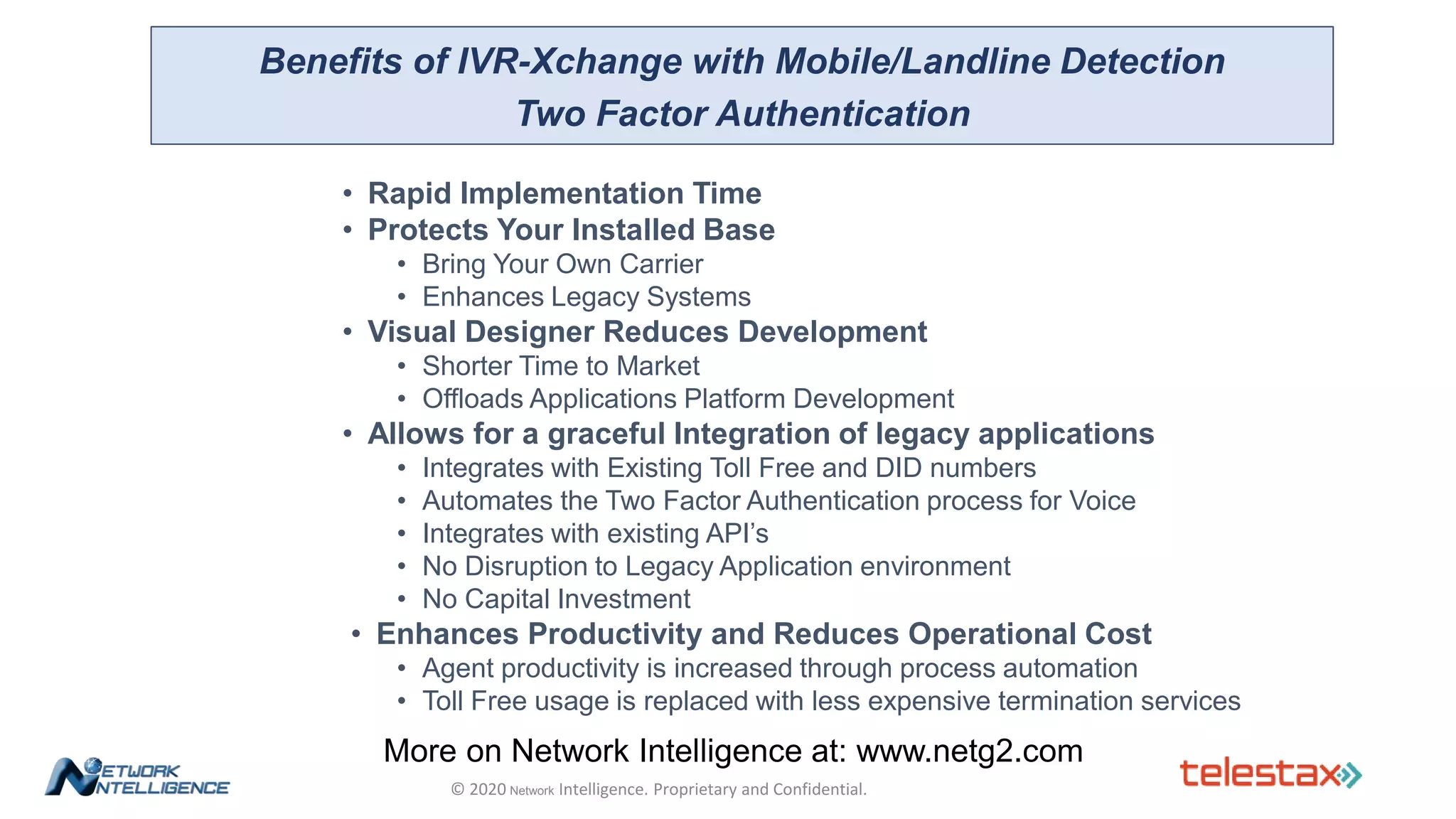
The document outlines a webinar about two-factor authentication (2FA) and its commercial opportunities, highlighting its importance in combating rising phishing attacks. Presenters discuss various aspects of 2FA, including use cases, implementation strategies, and its benefits for businesses and customers within the communications industry. Key points emphasize the need for enhanced security and the role of telecommunications service providers in delivering 2FA solutions.