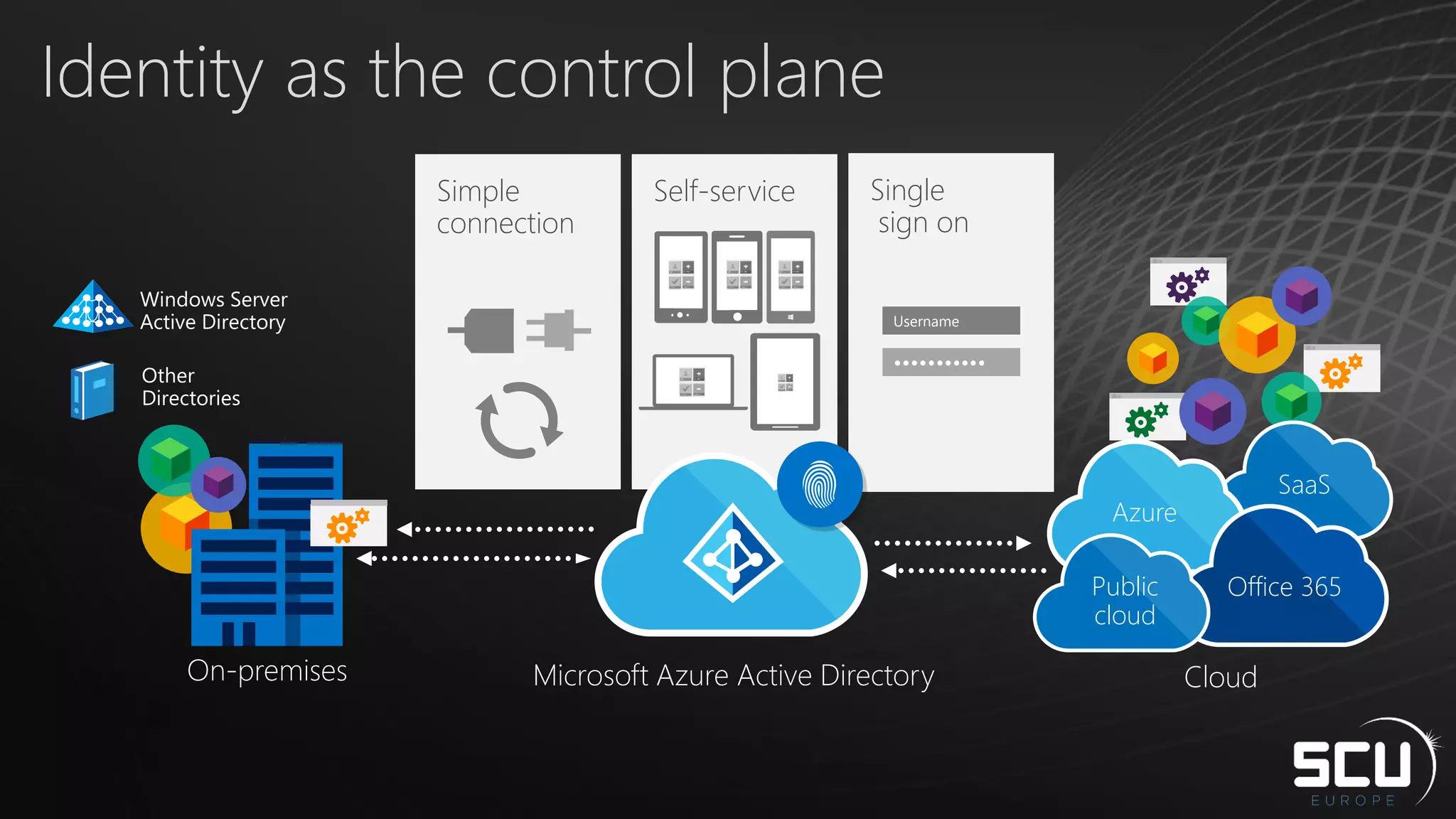
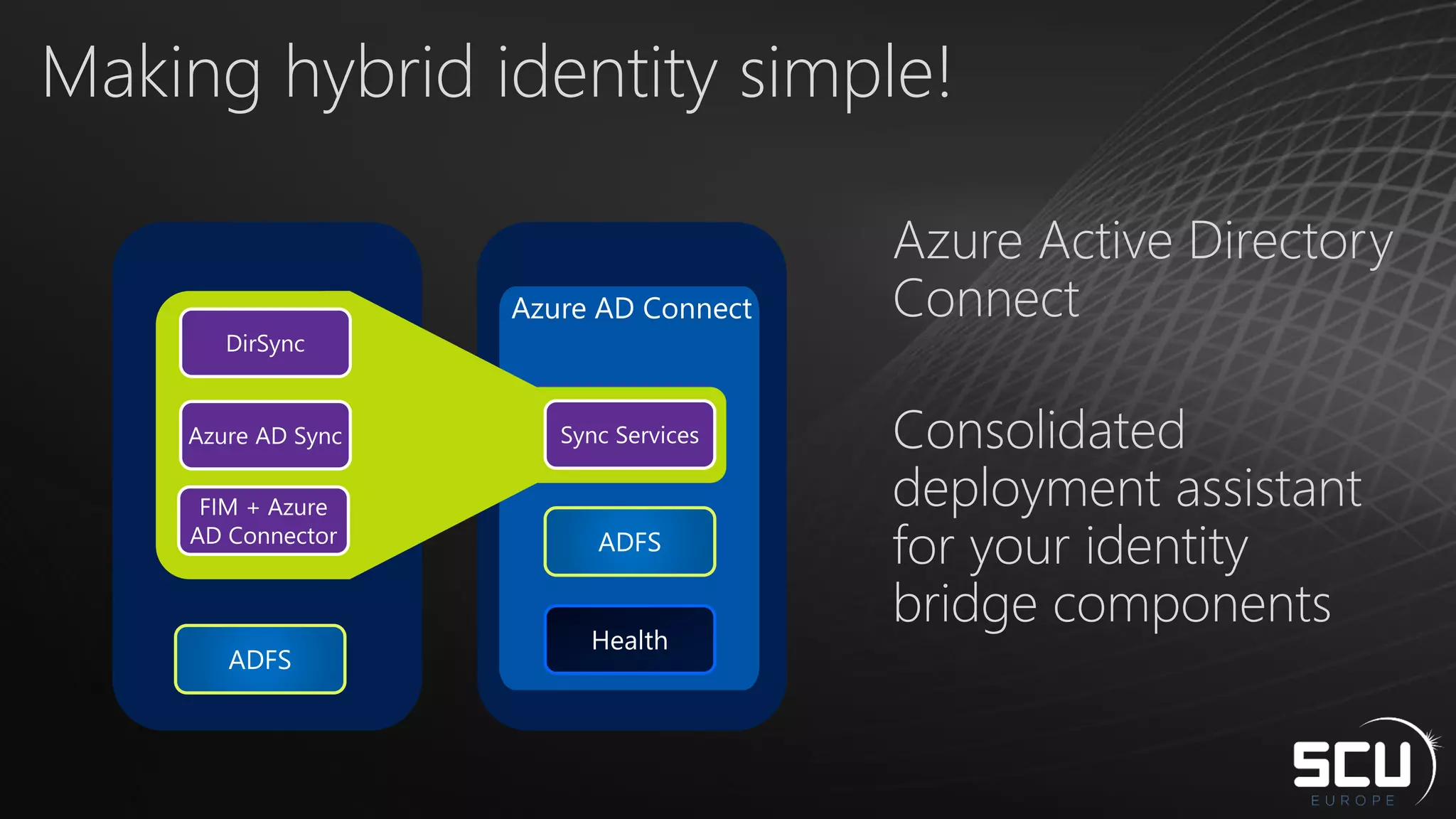
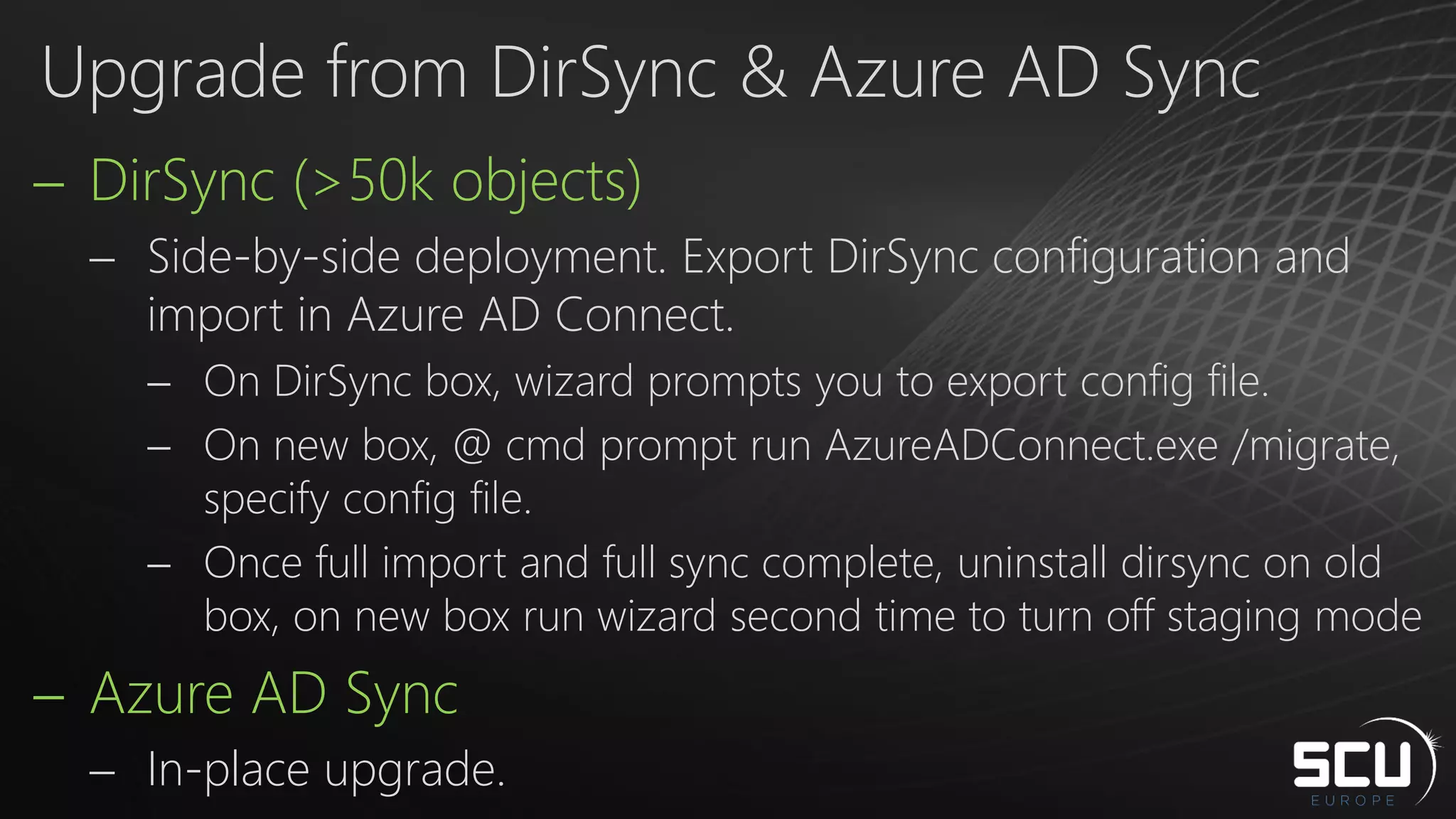
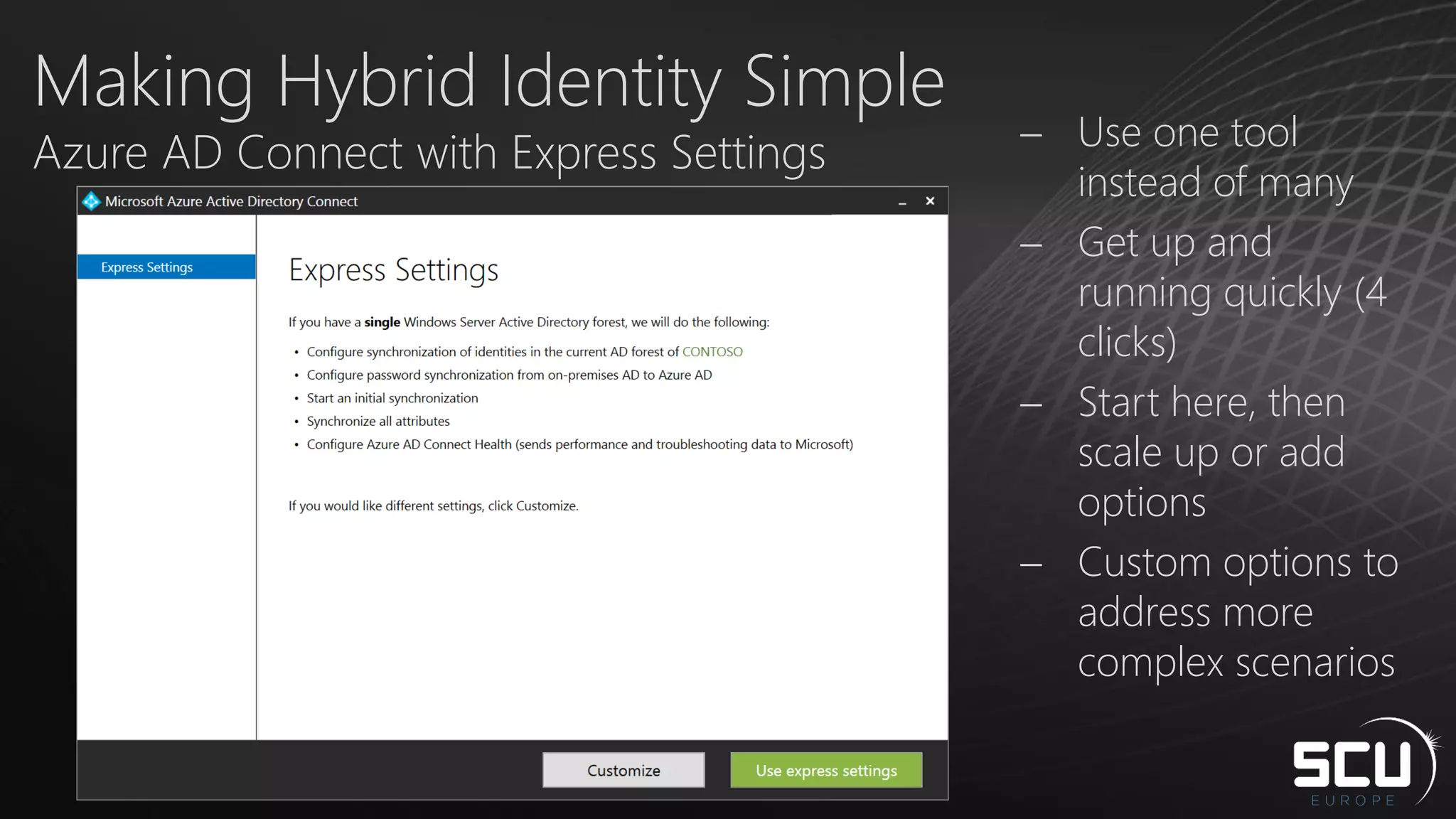
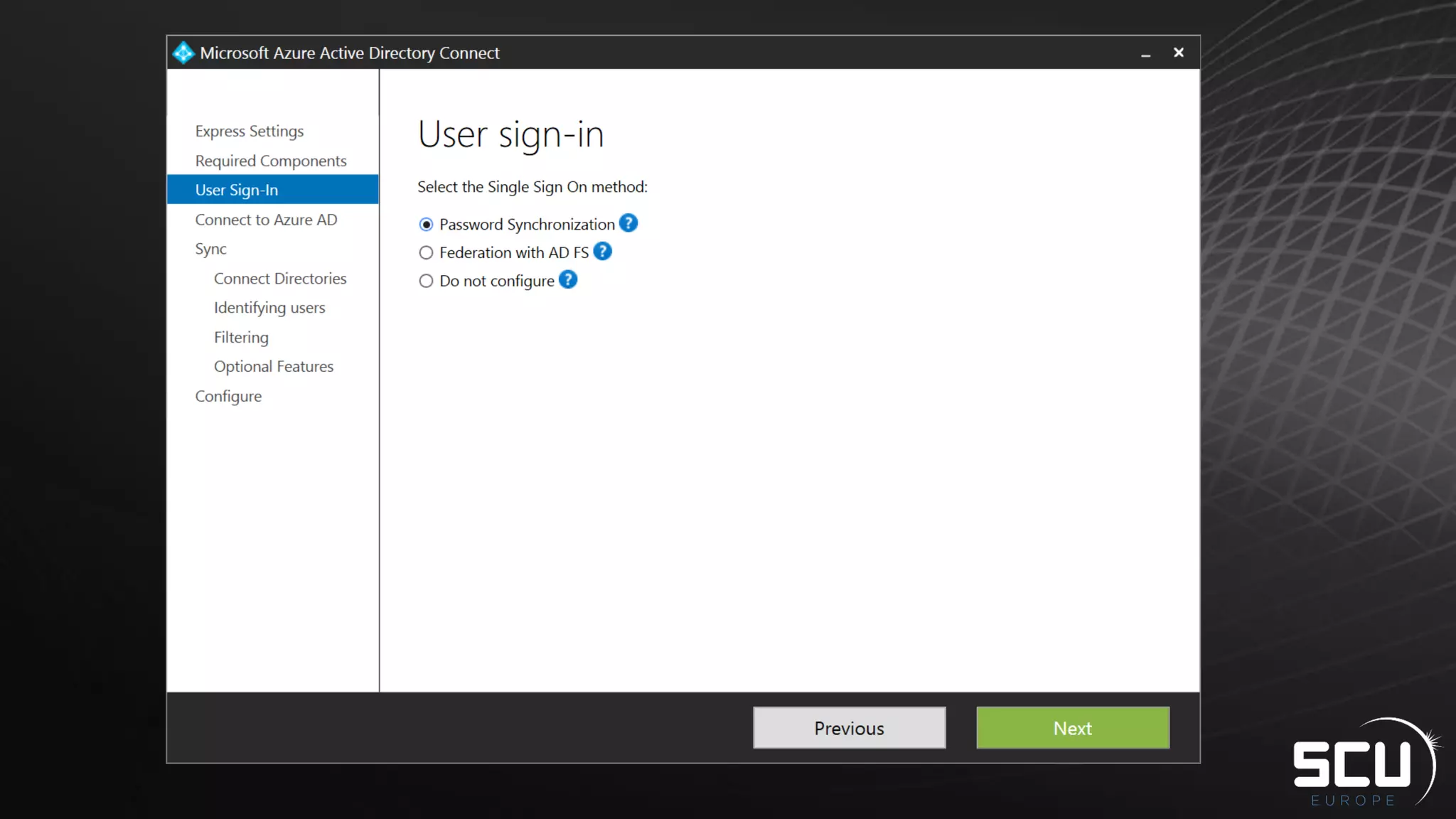
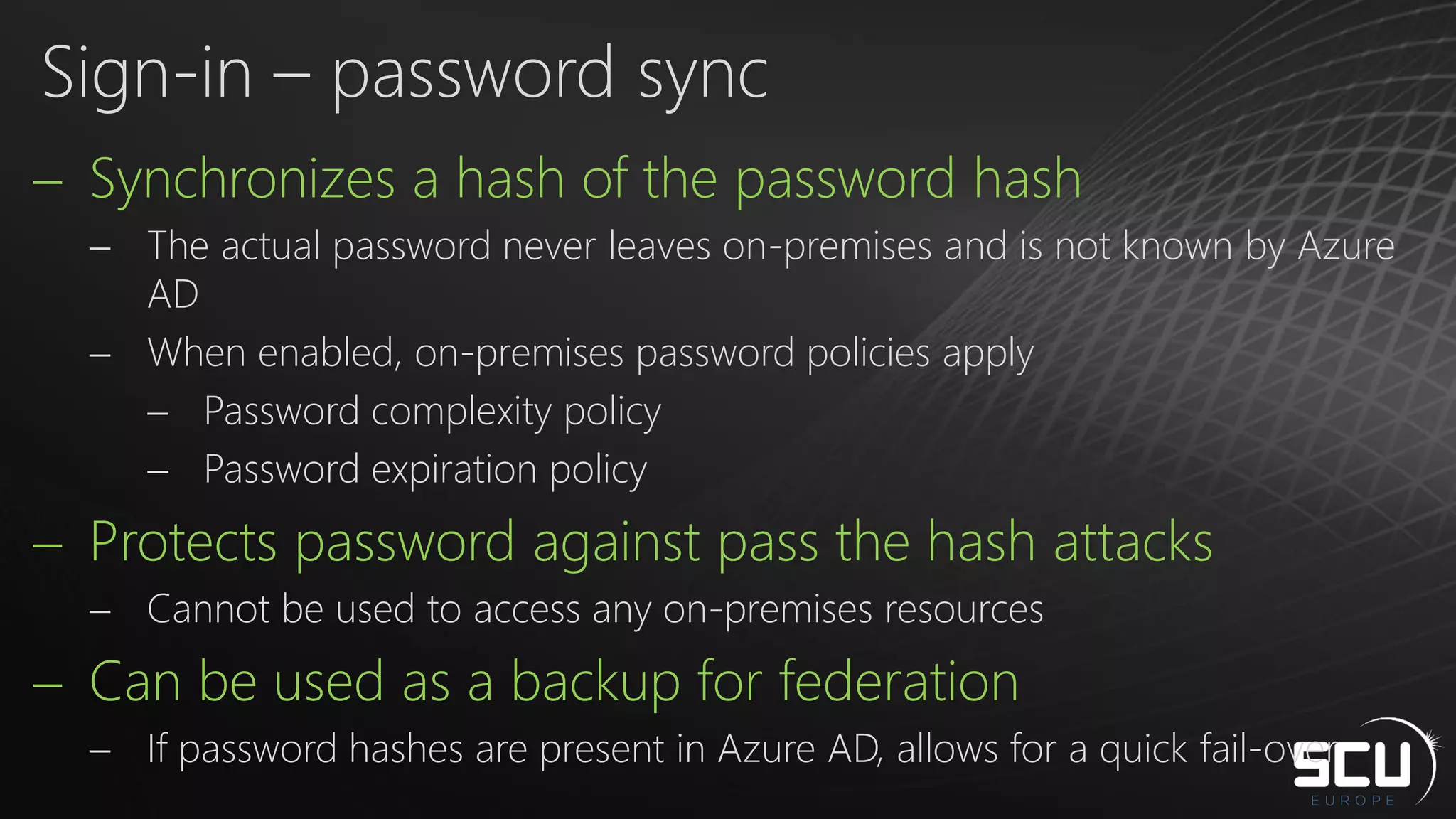
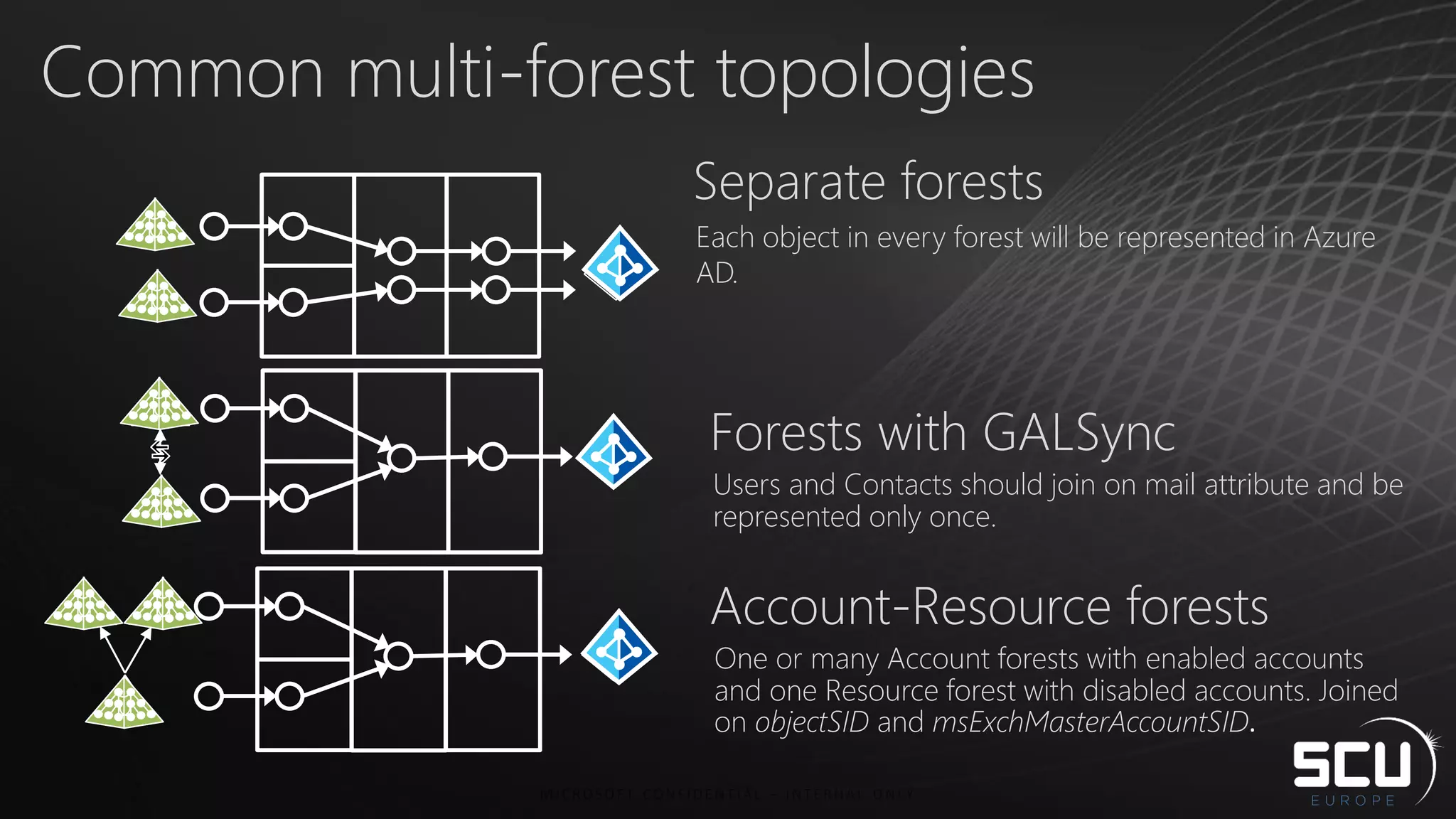
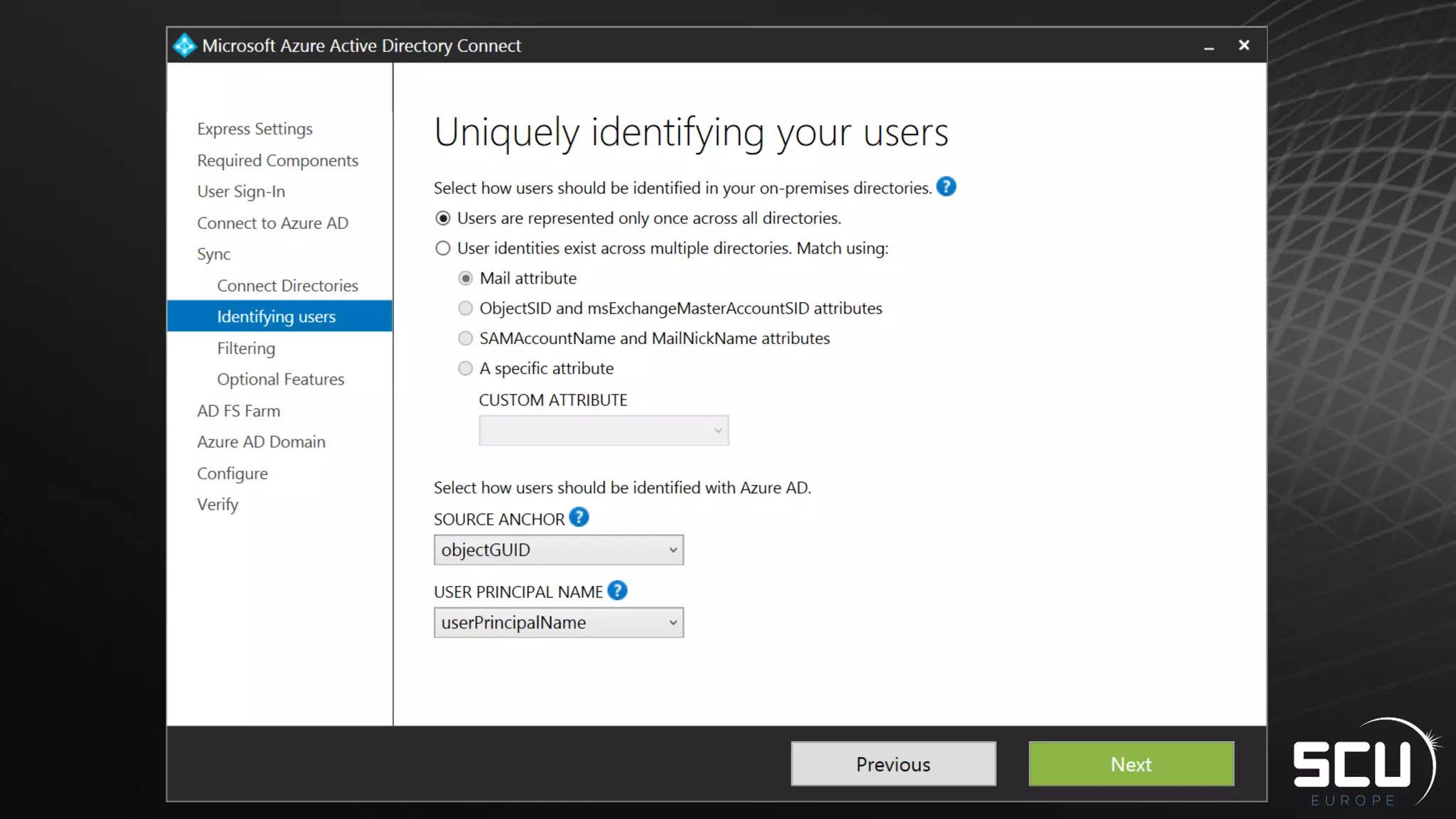
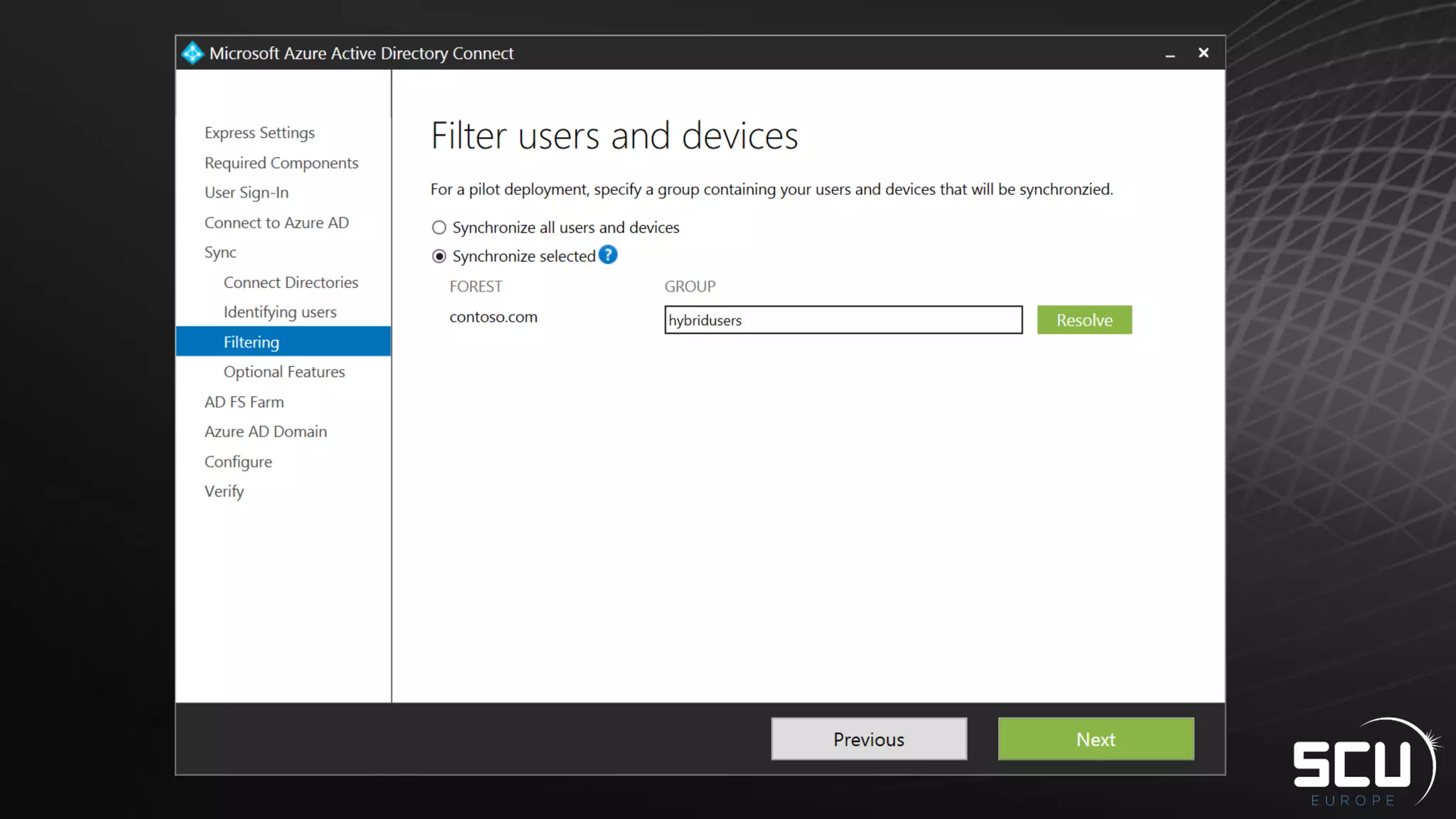
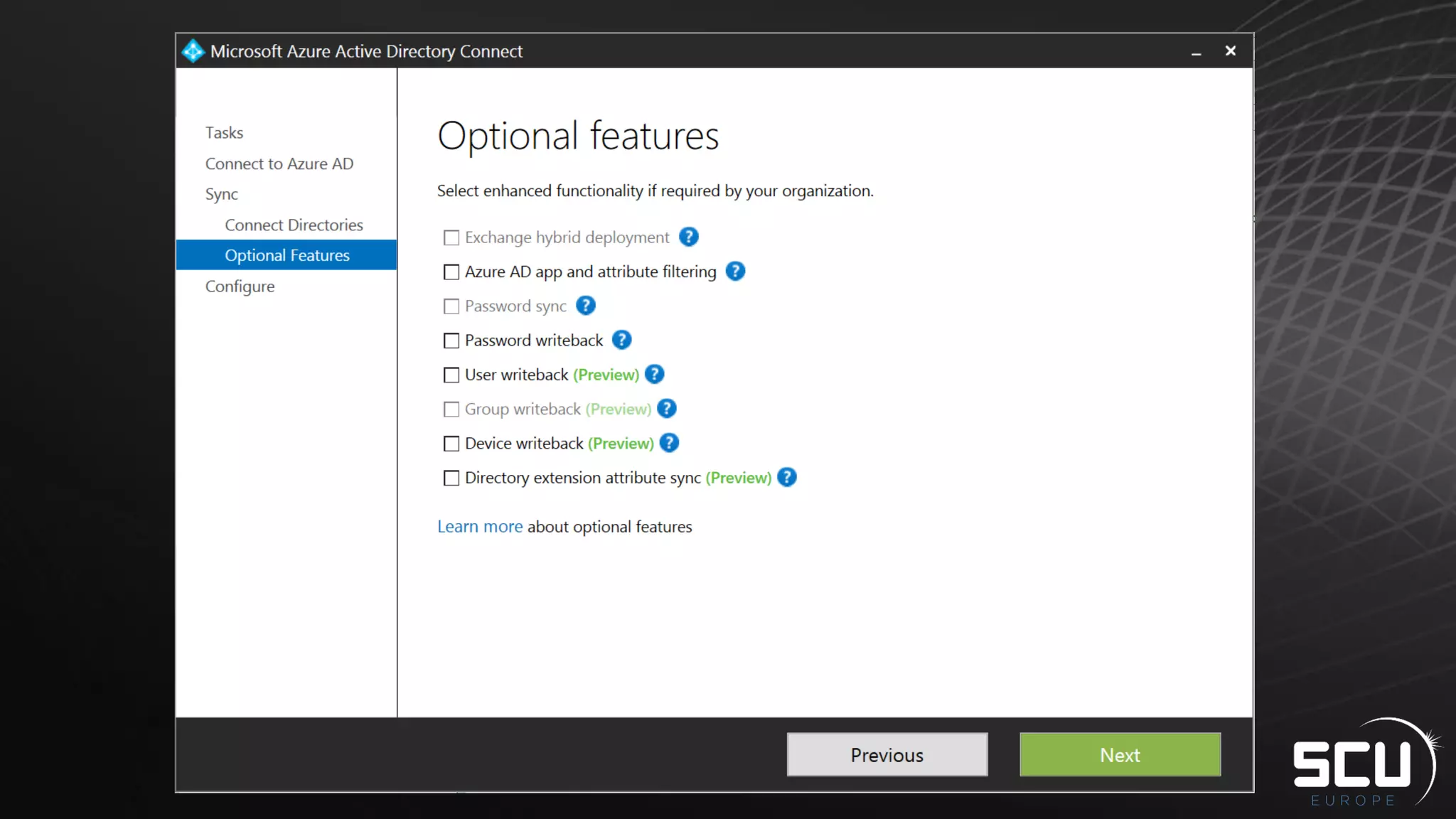
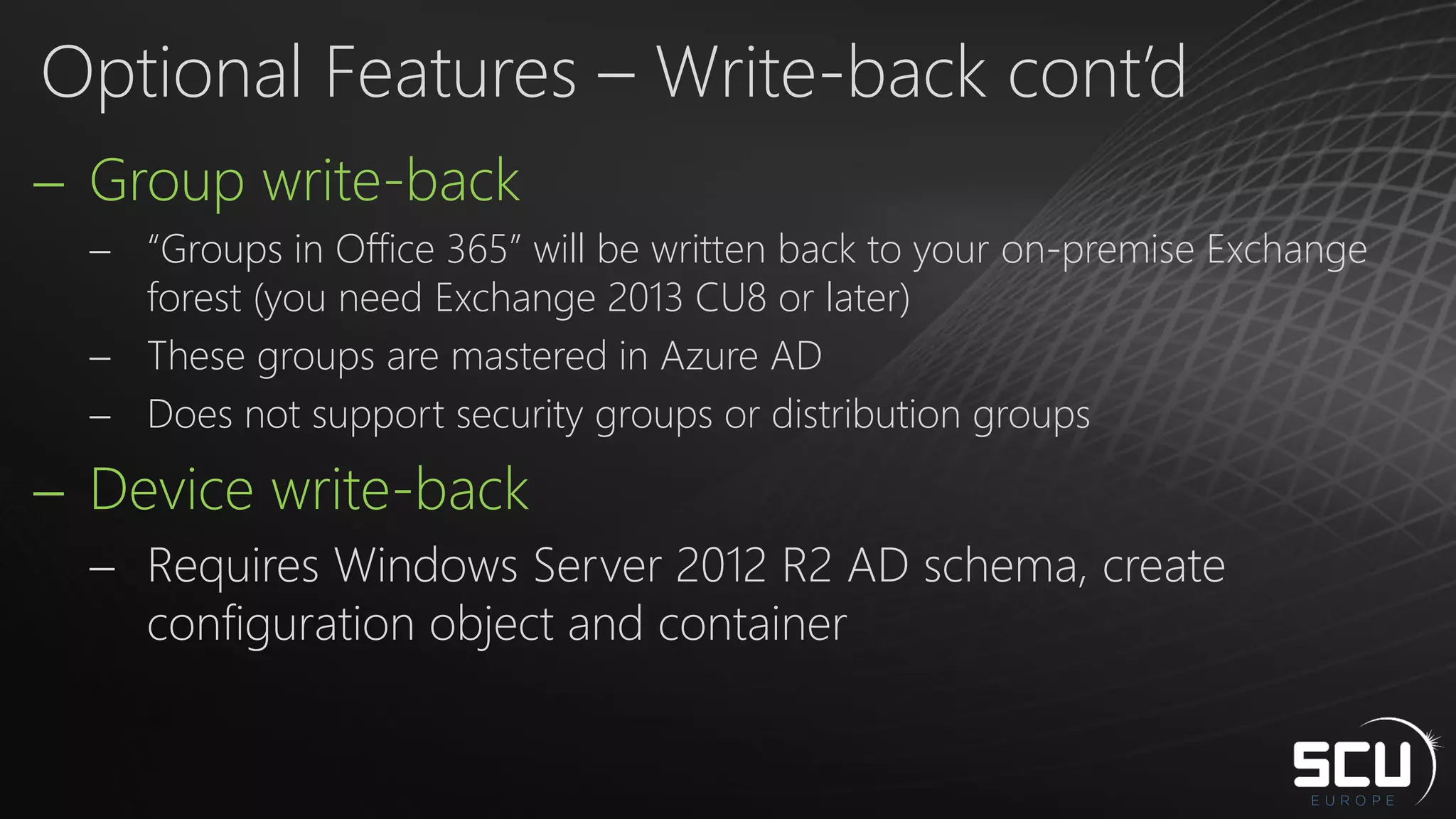
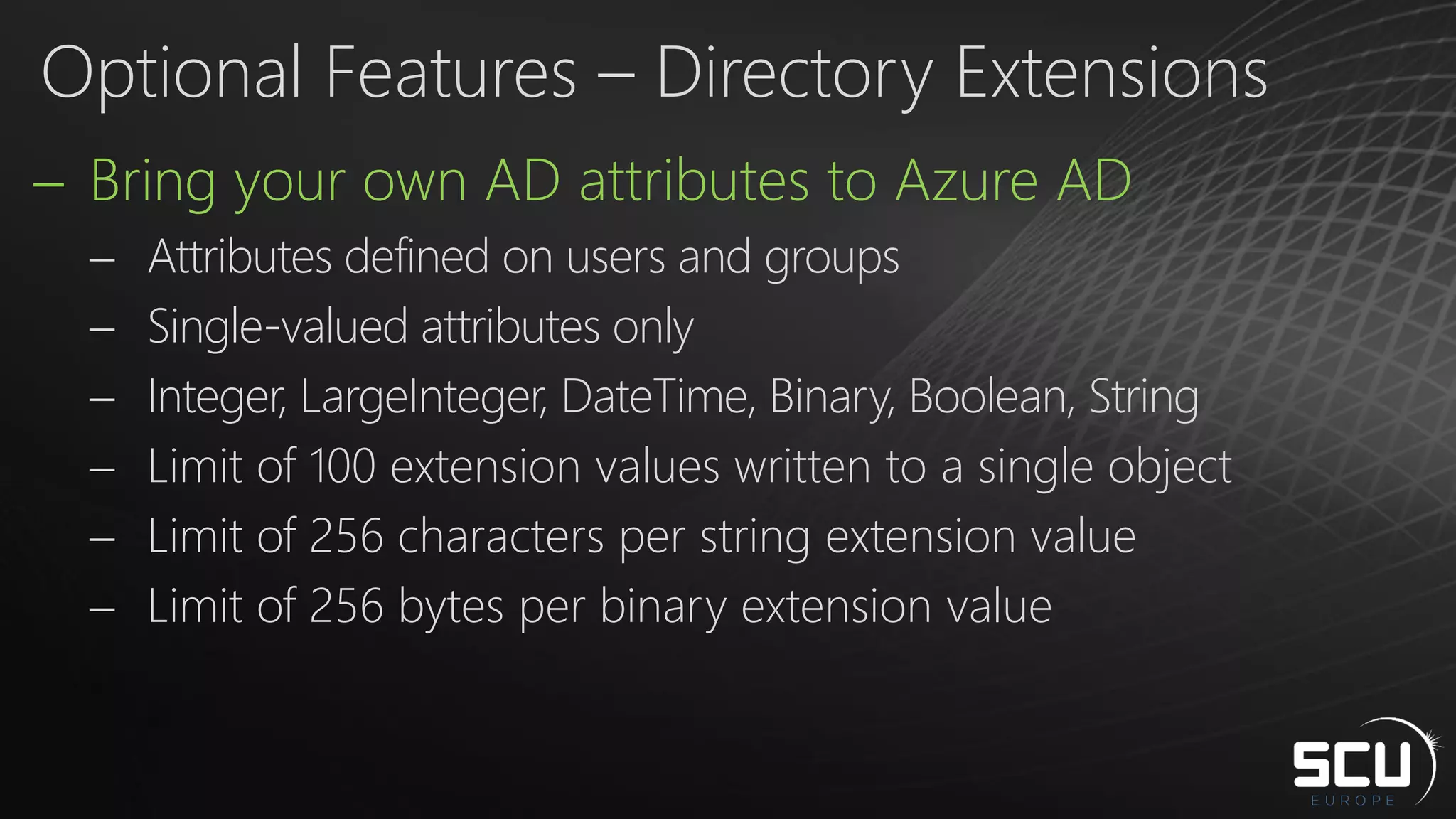
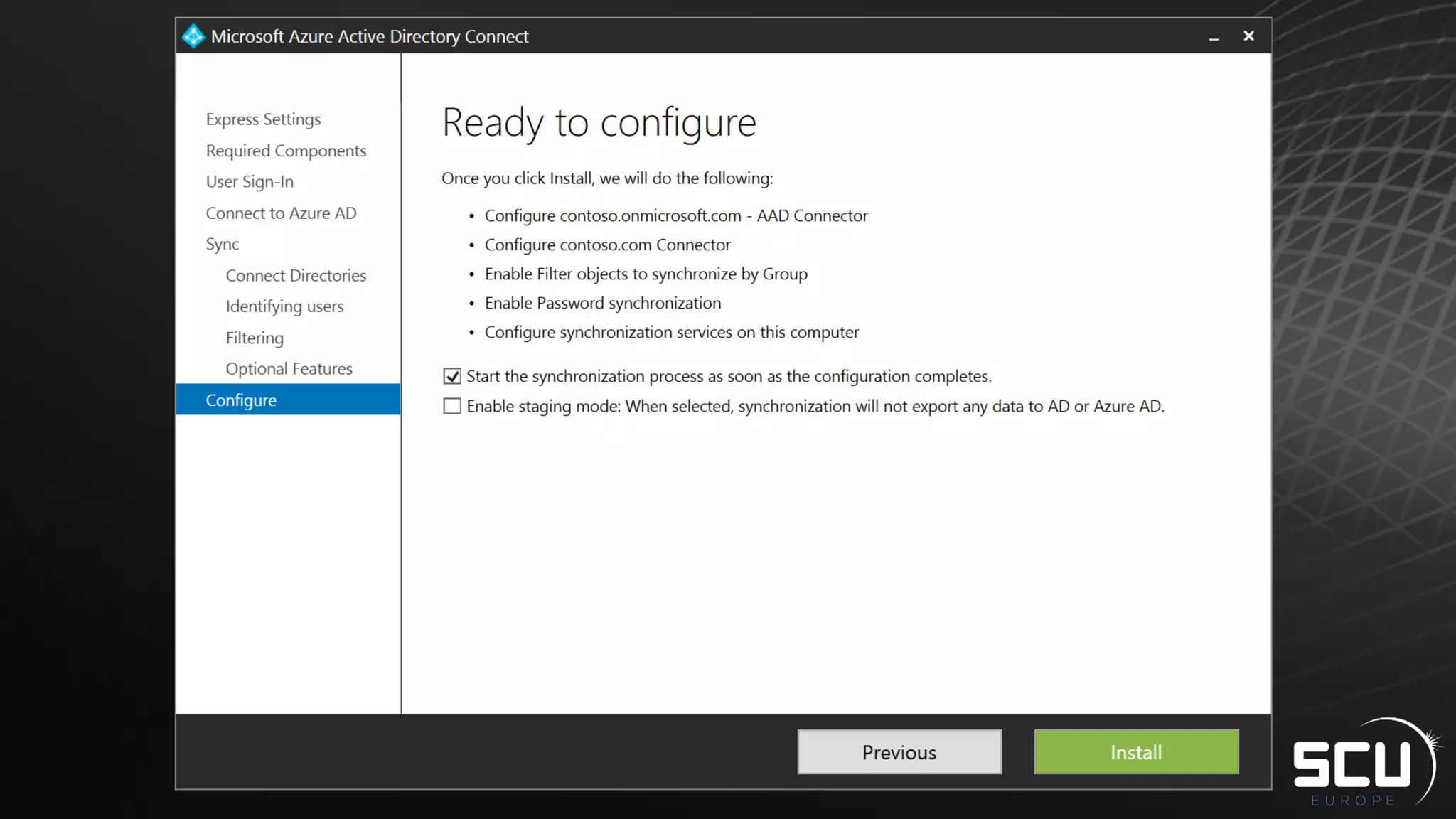
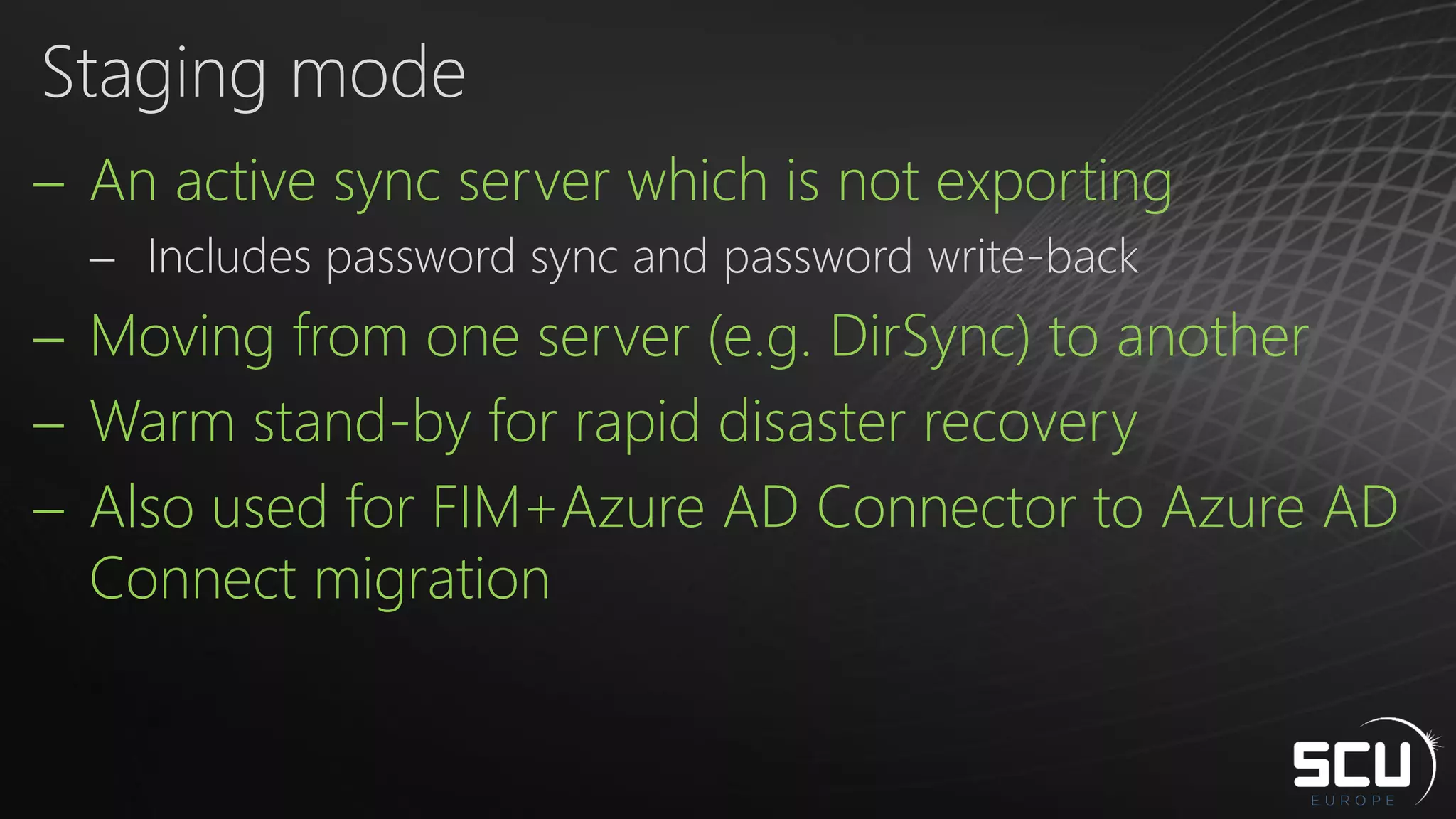
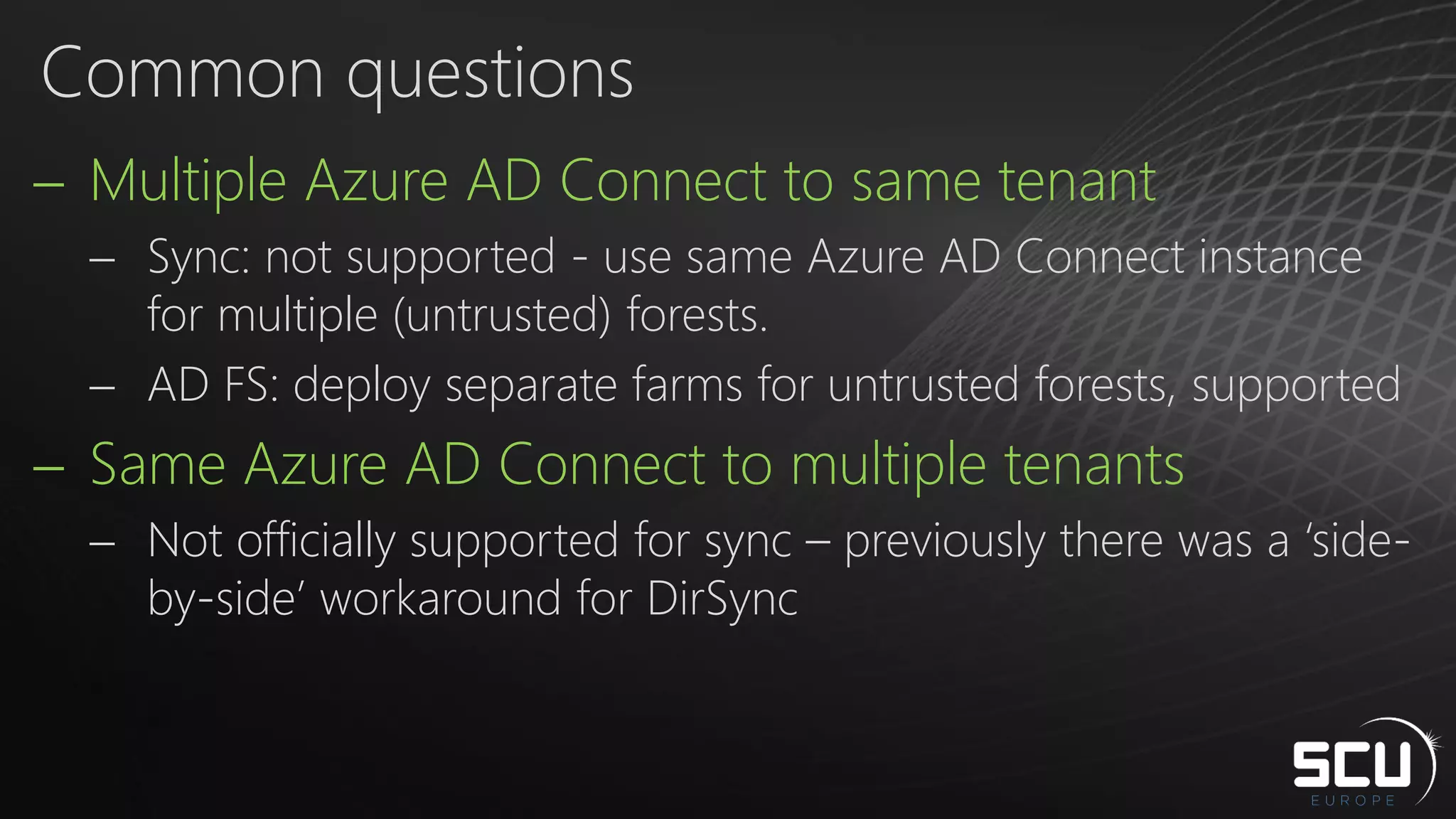
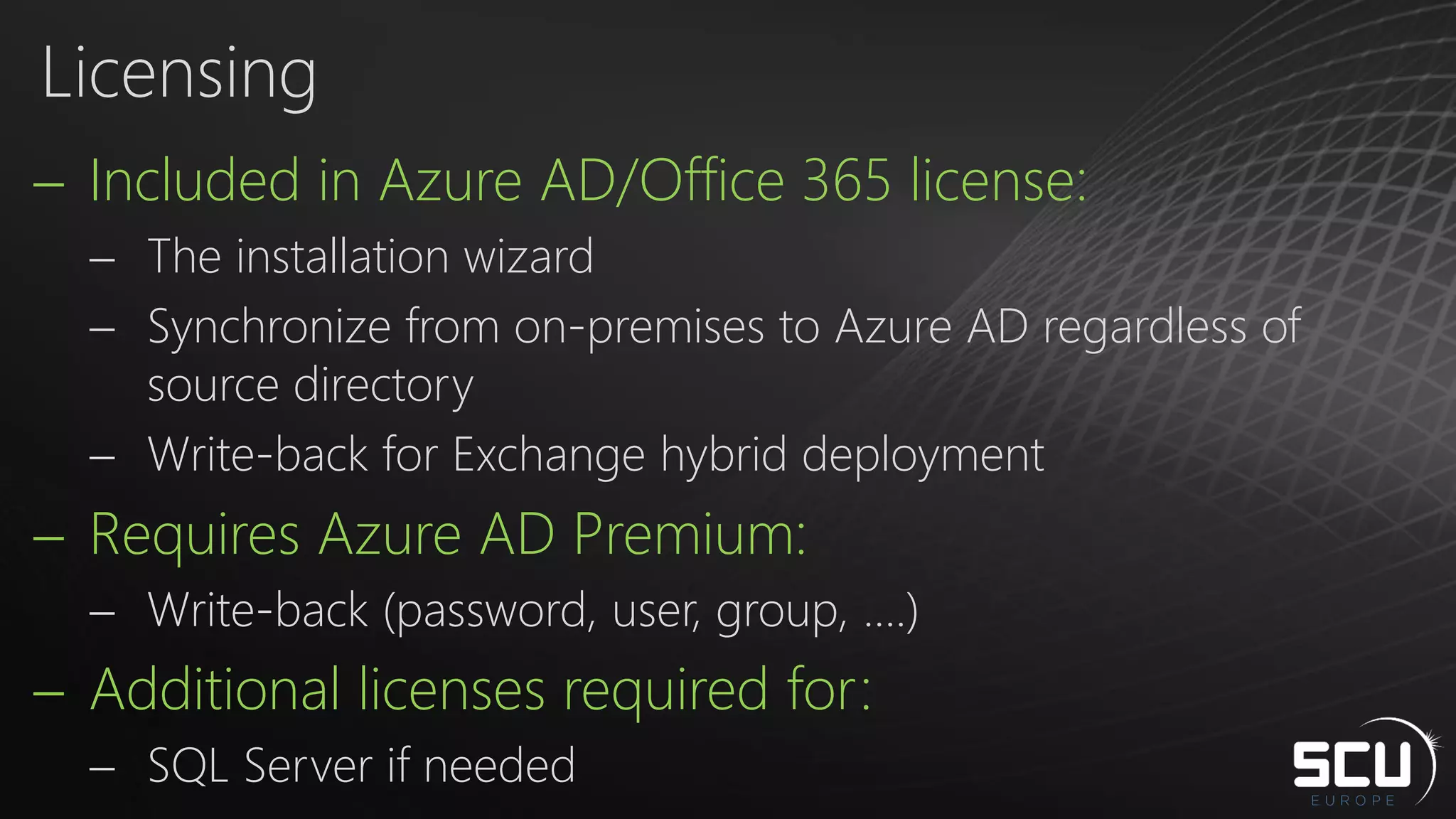
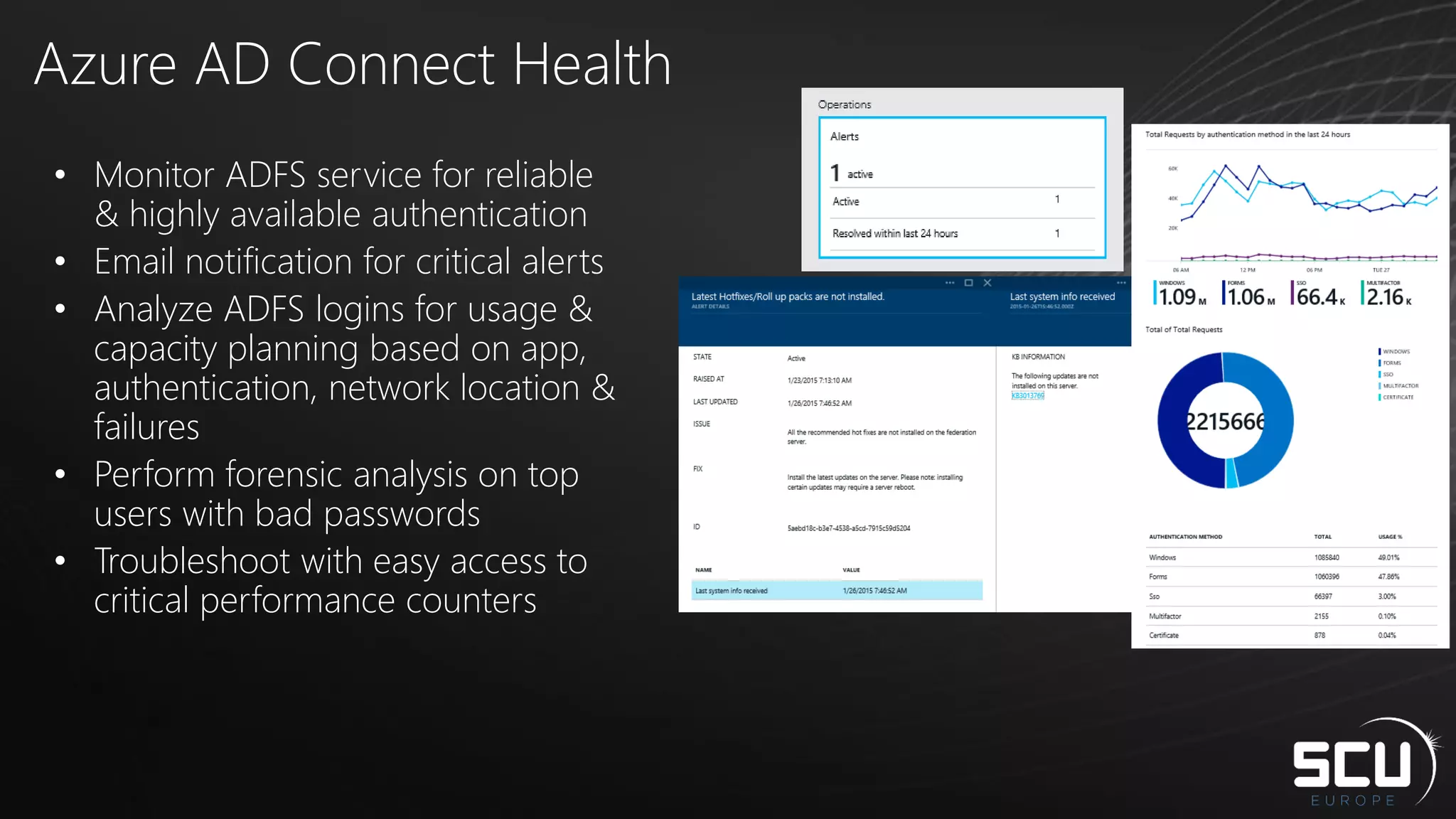
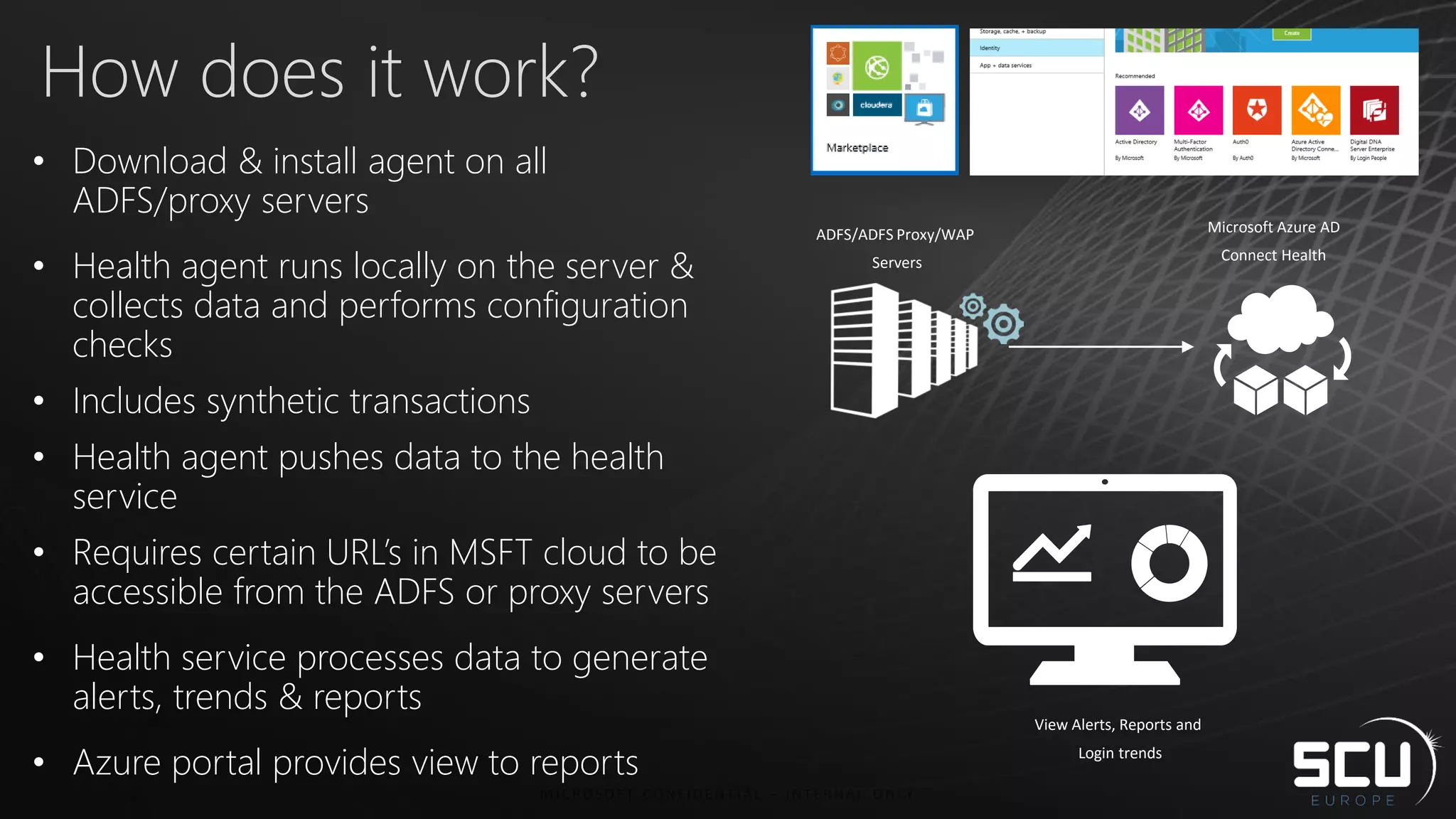
Azure AD Connect provides a simplified way to set up hybrid identity between on-premises Active Directory and Azure Active Directory. It can be configured using Express settings for a quick setup in four steps, or using Custom settings to address more complex scenarios. The tool consolidates previous identity bridge components like DirSync and Azure AD Sync. It also allows enabling additional features like password synchronization, device writeback, and extending directories with custom attributes. Admins can monitor their hybrid identity configuration using Azure AD Connect Health.