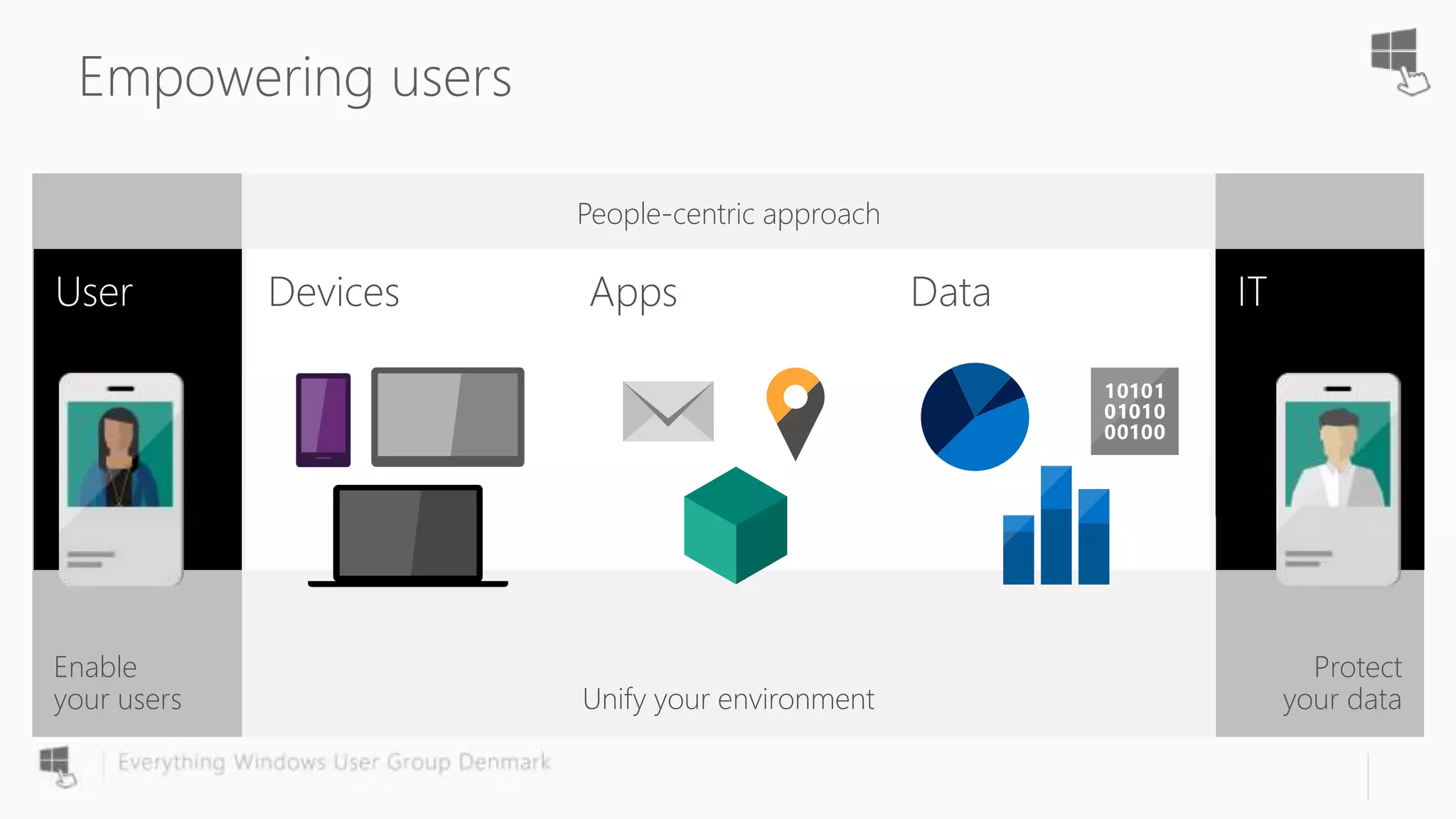
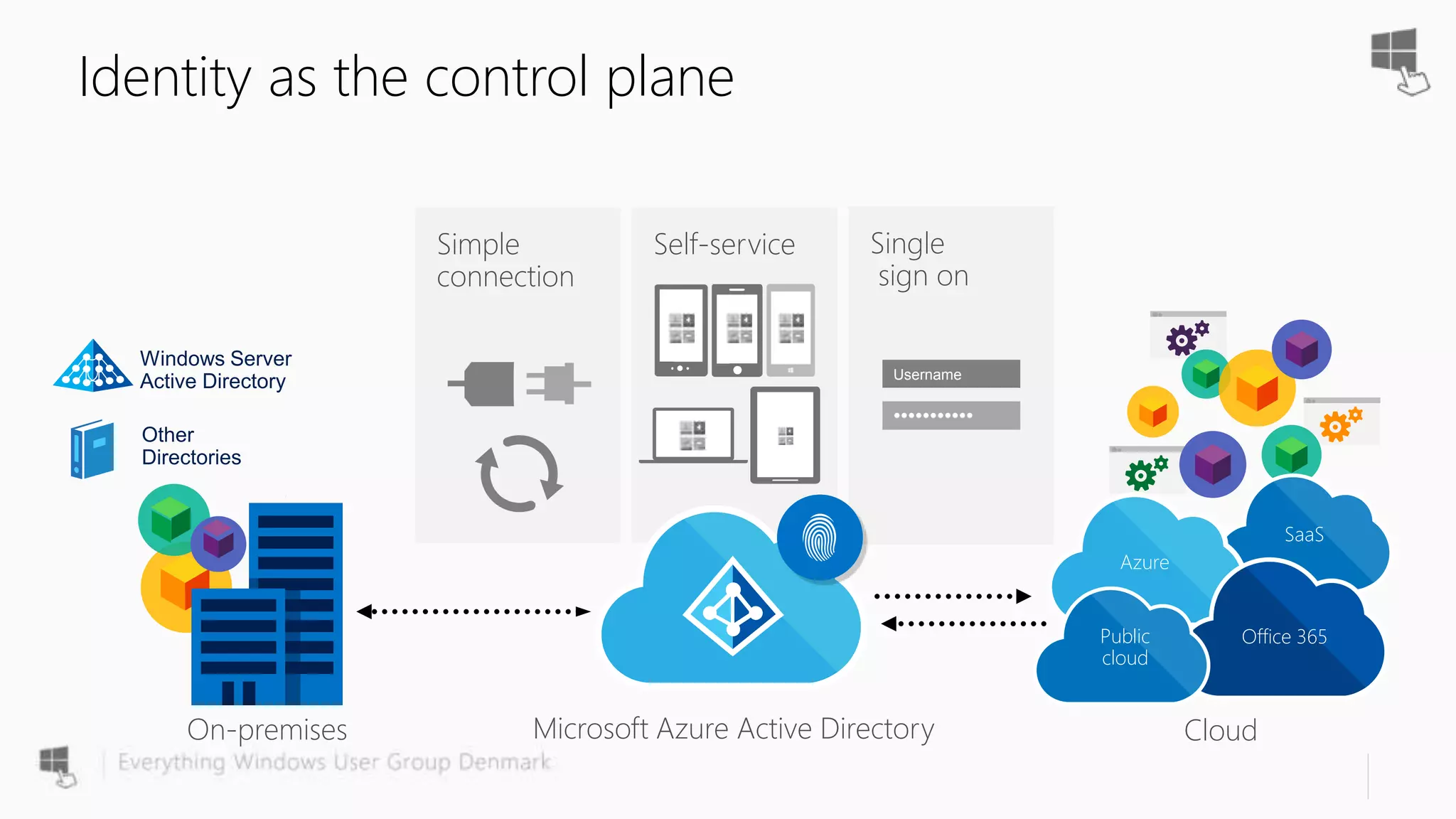
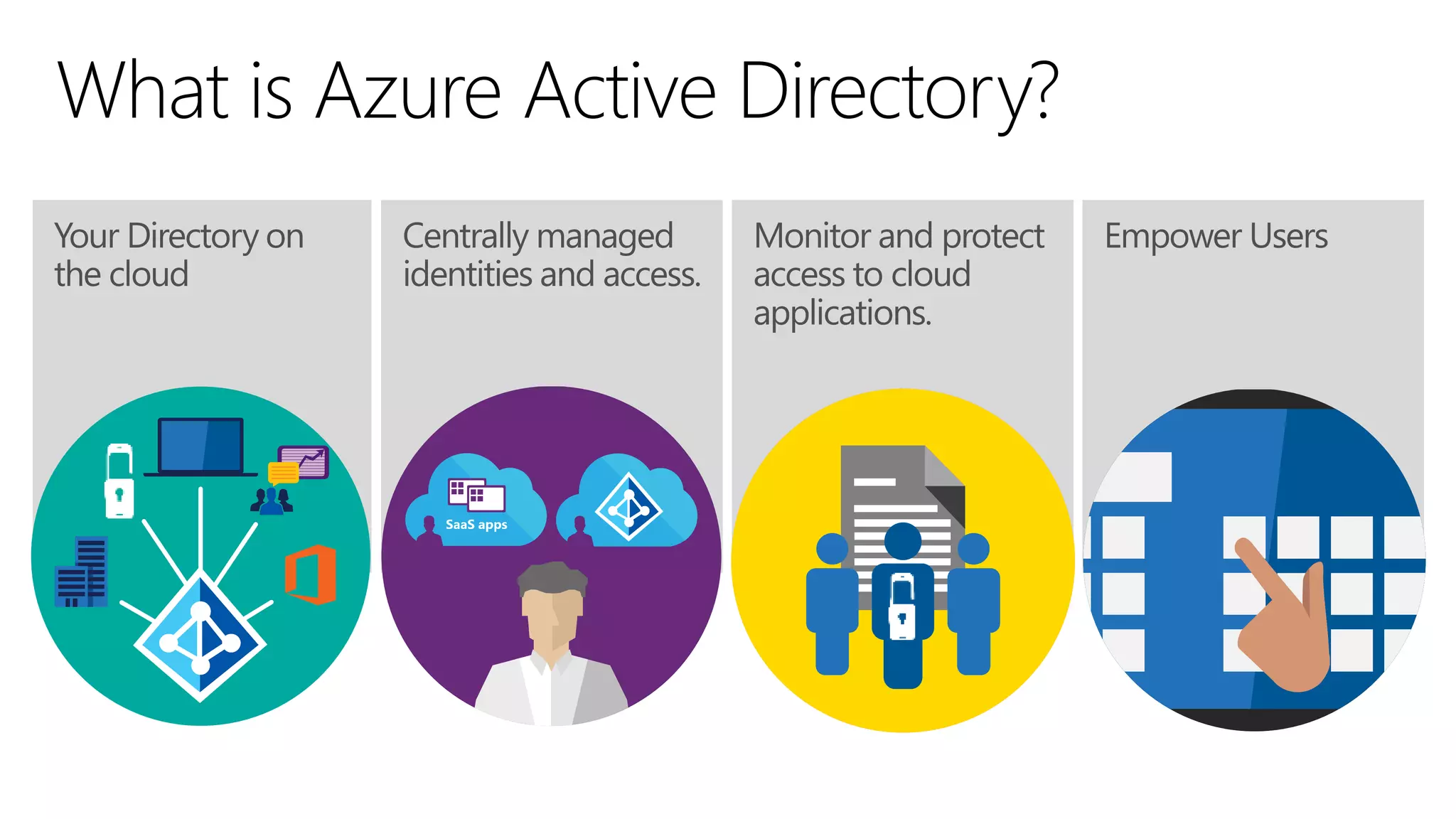
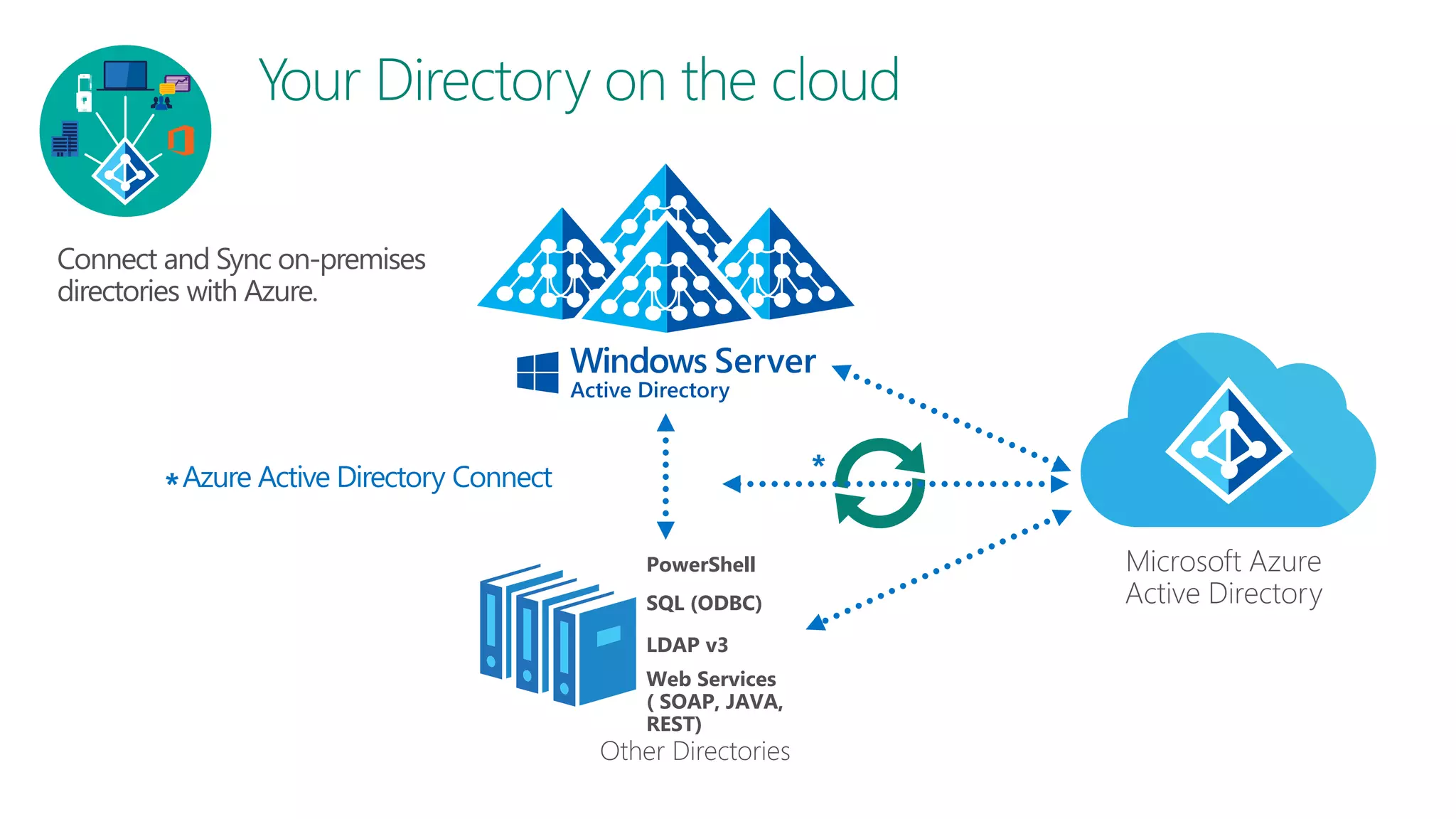
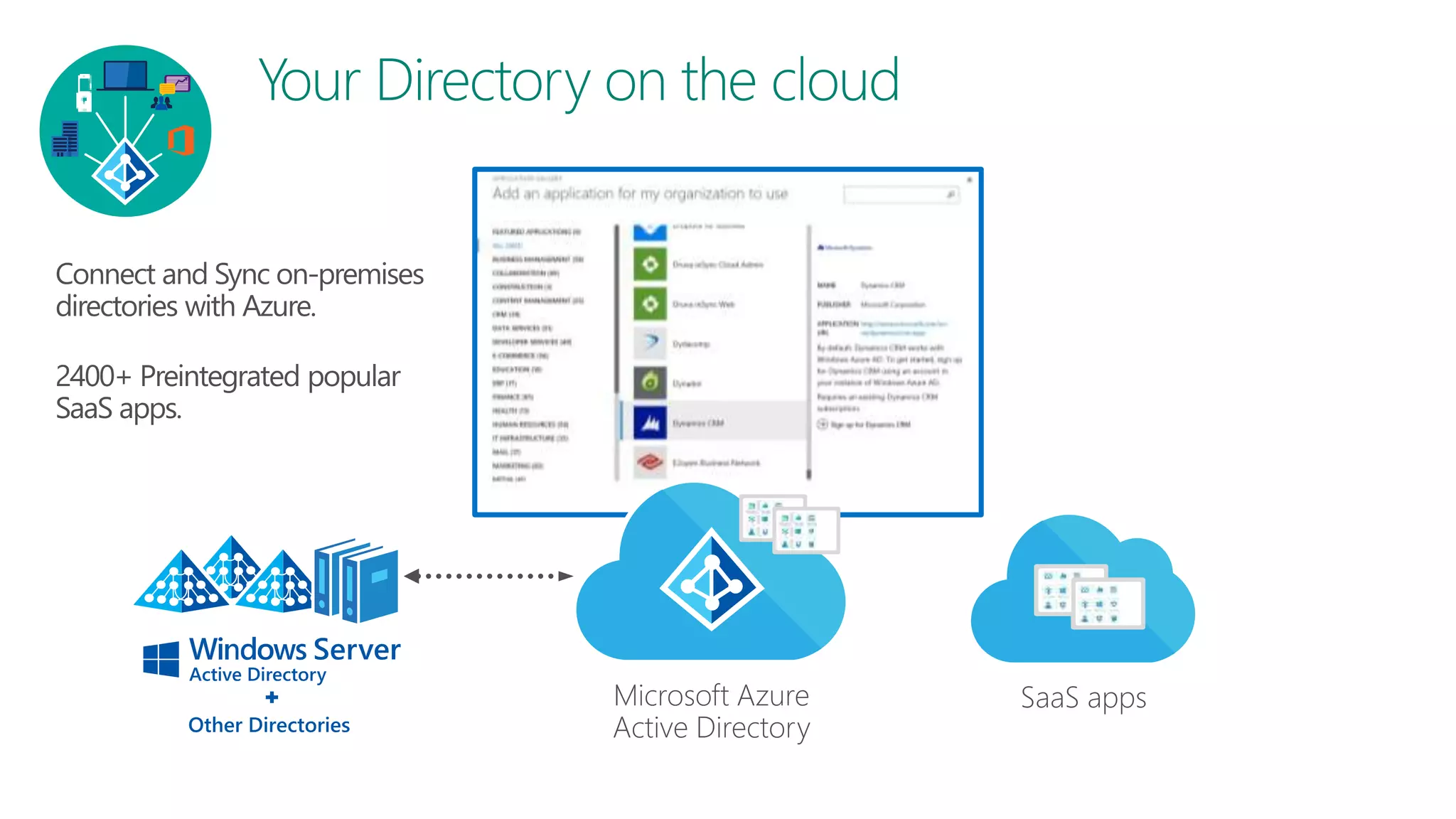
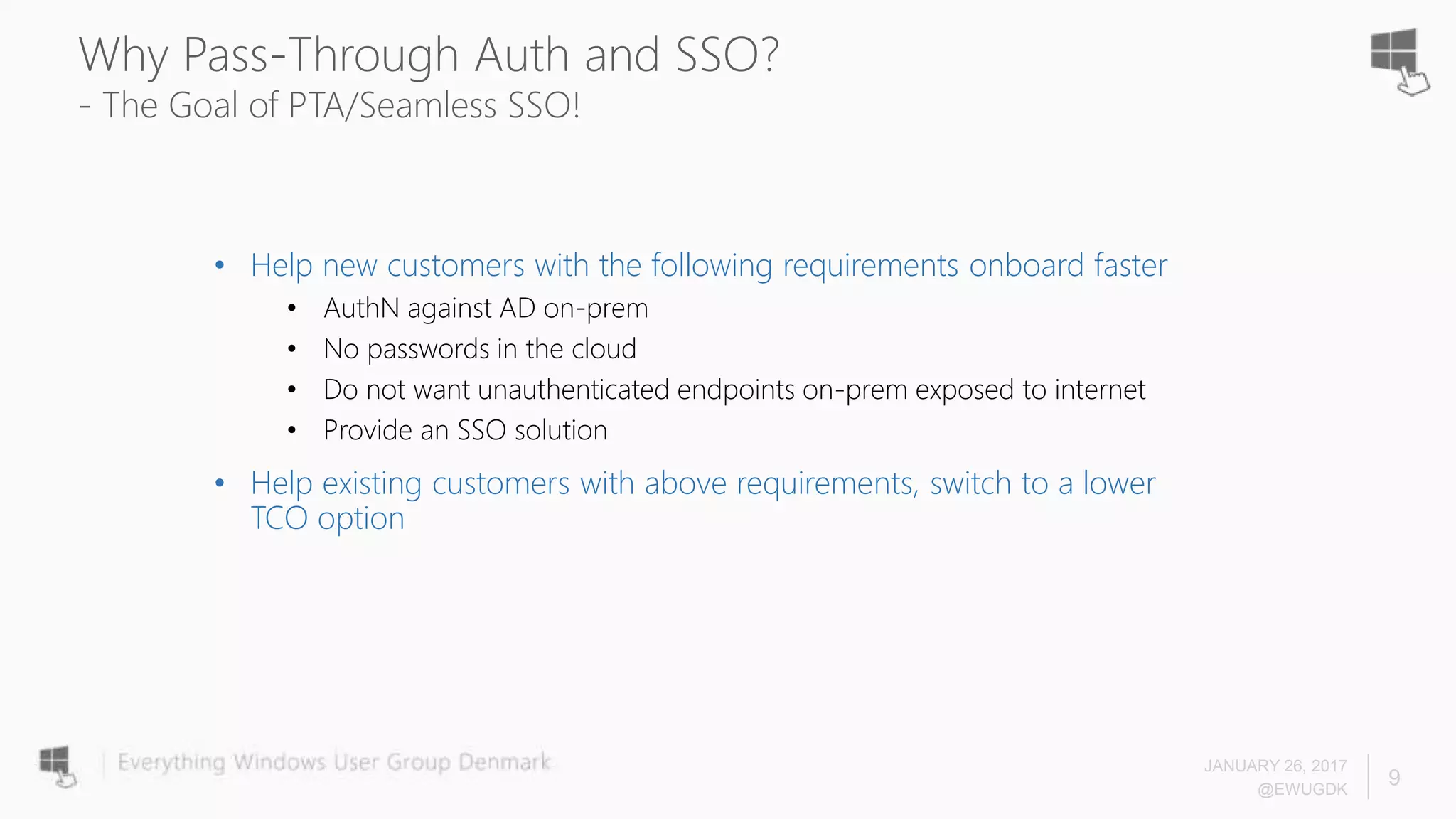
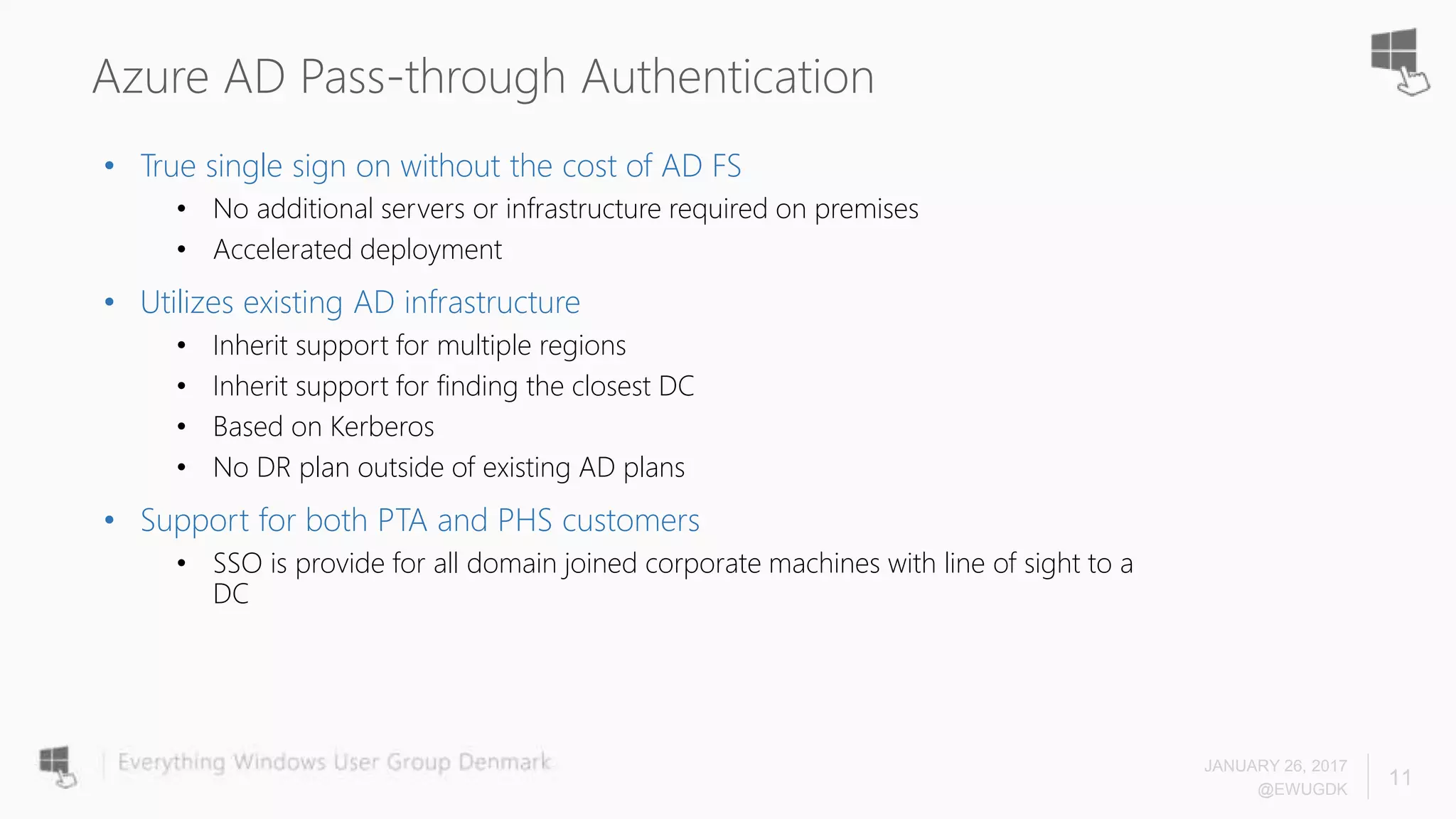
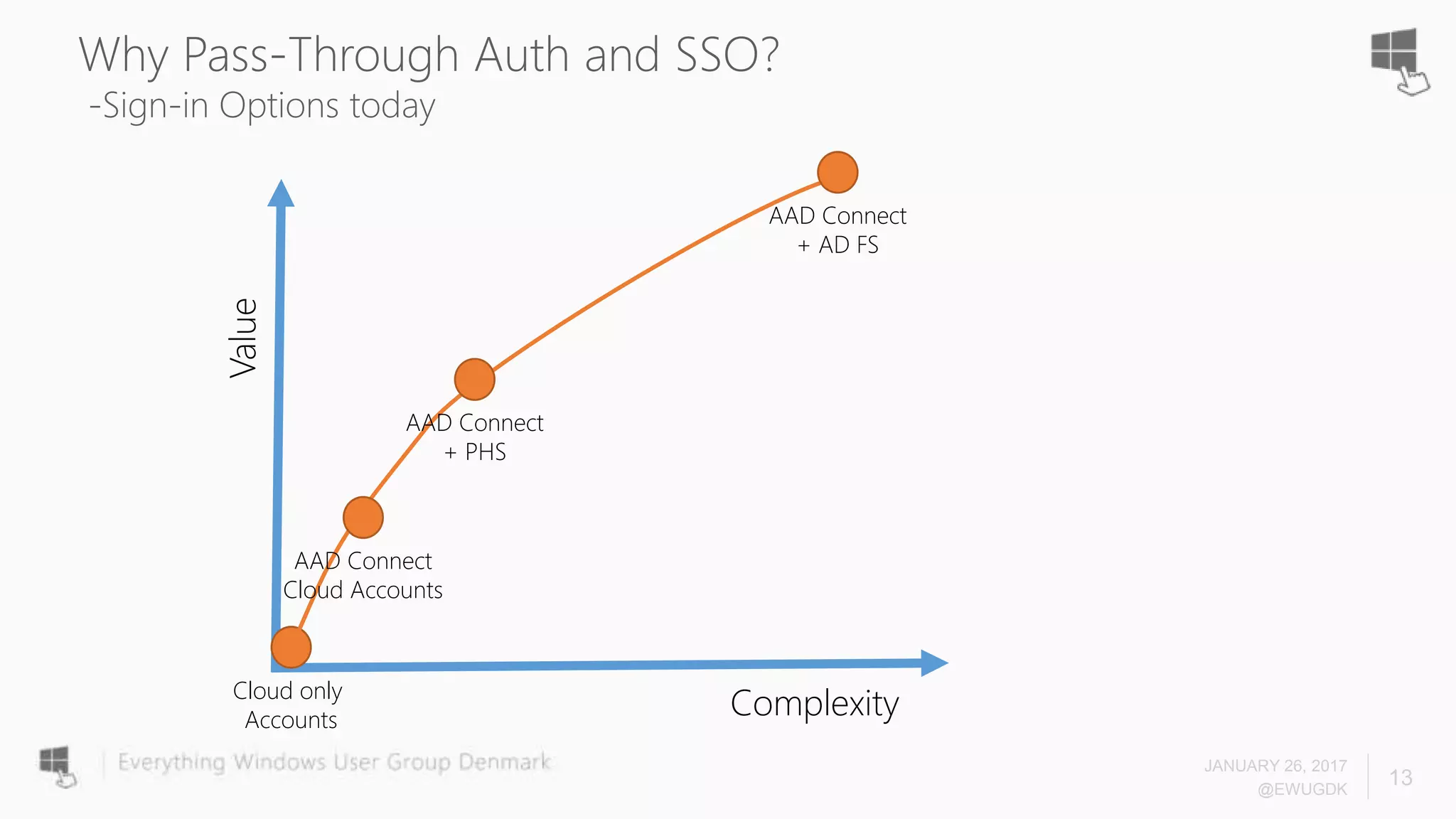
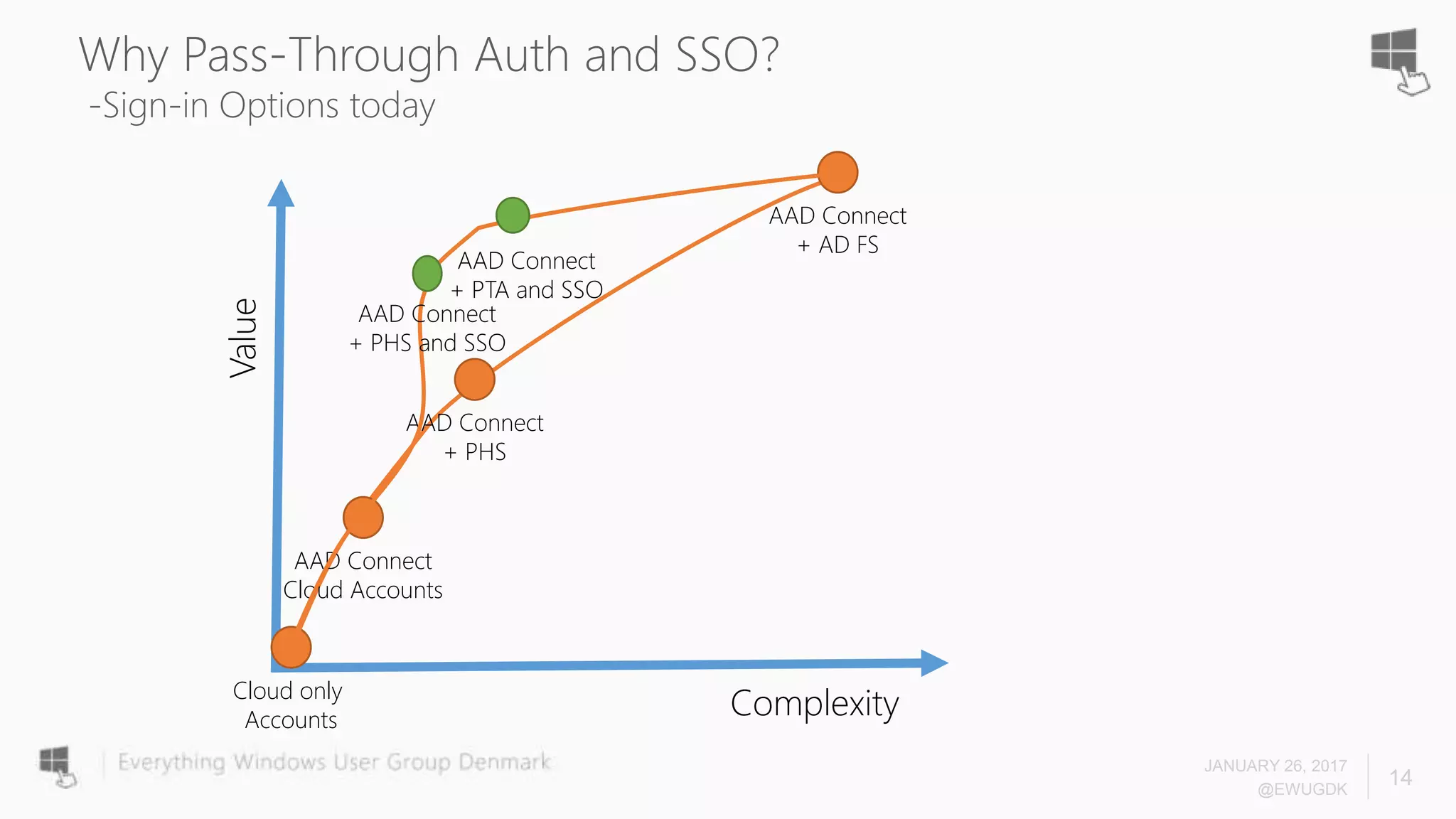
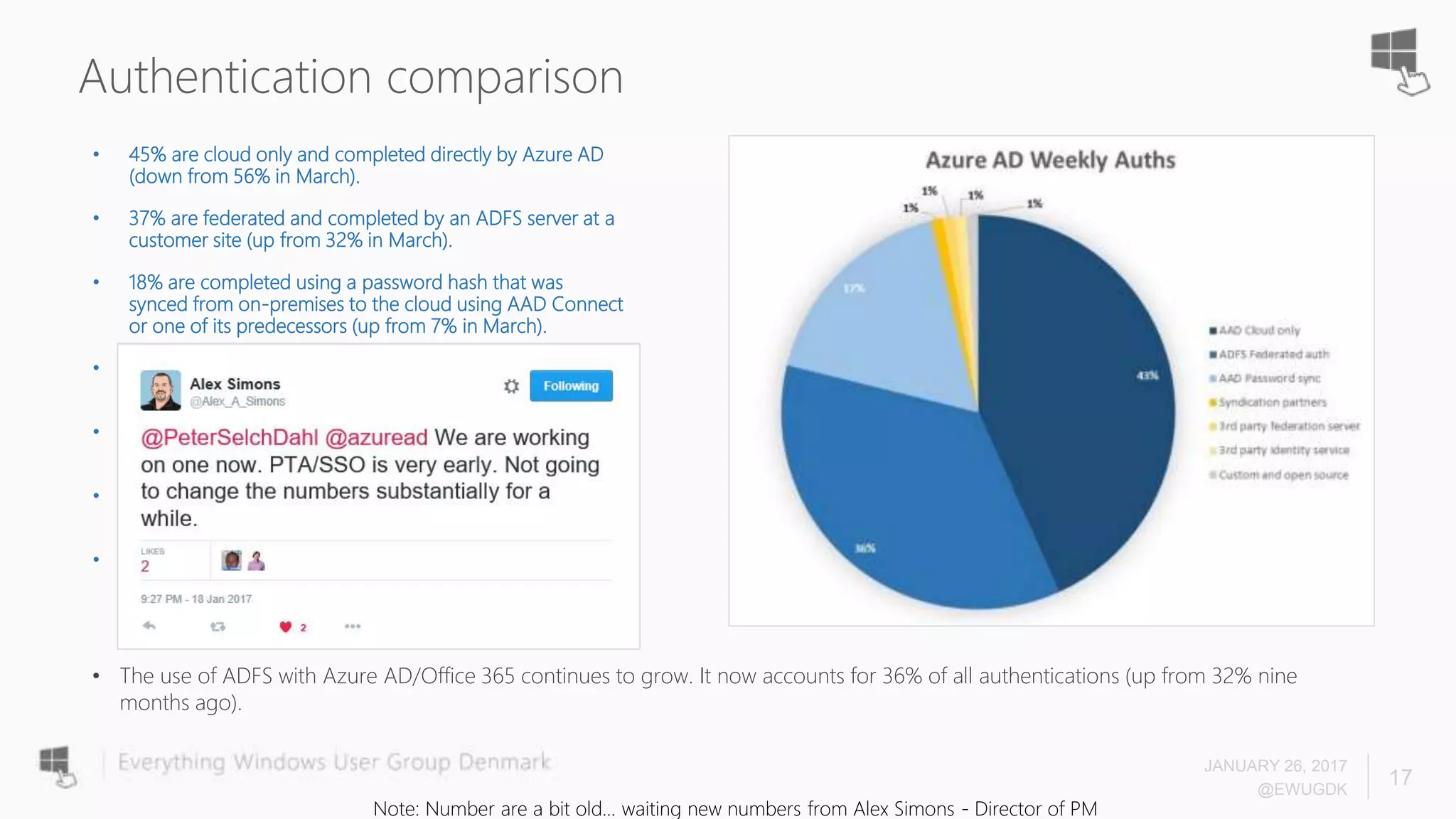
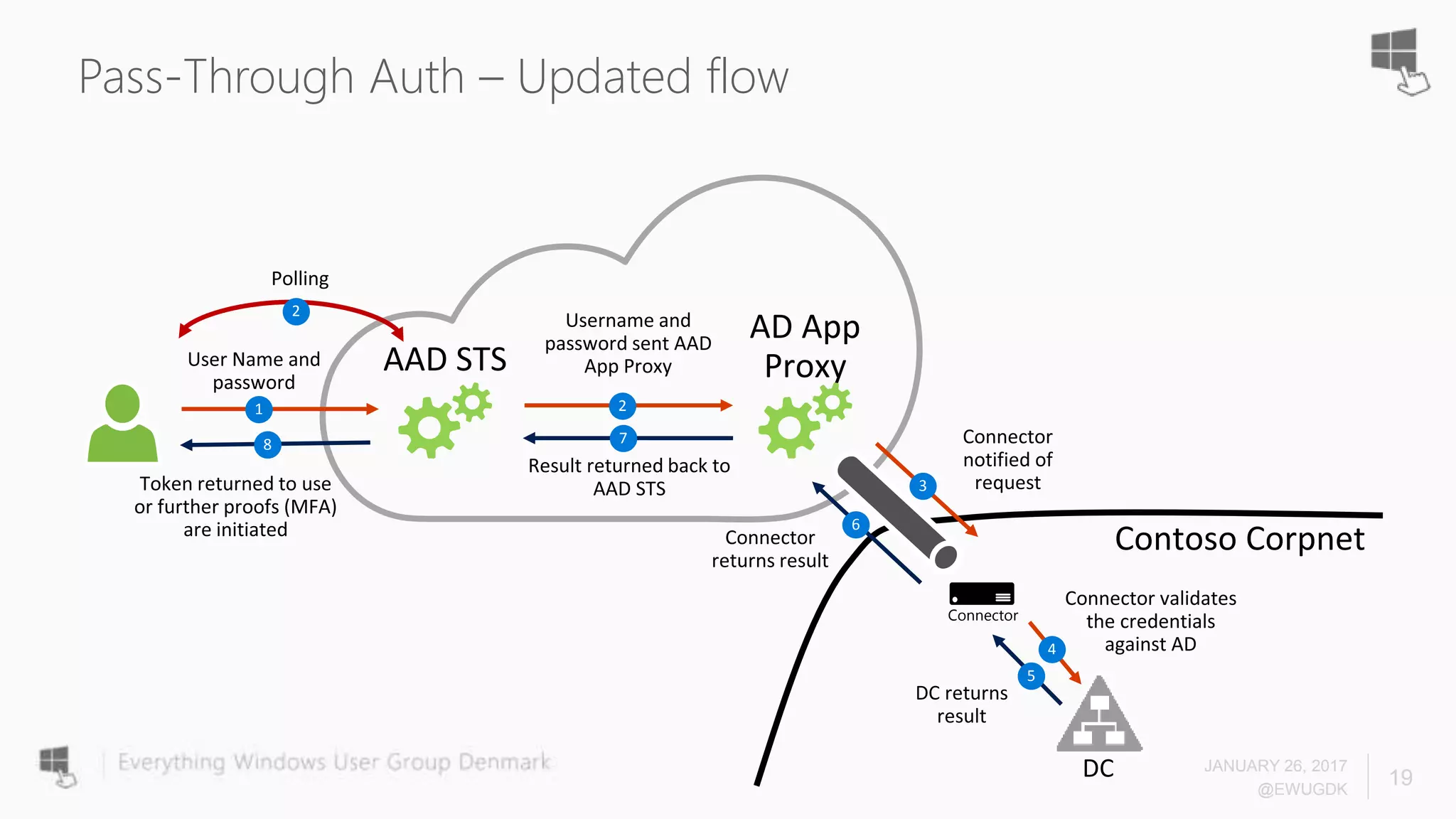
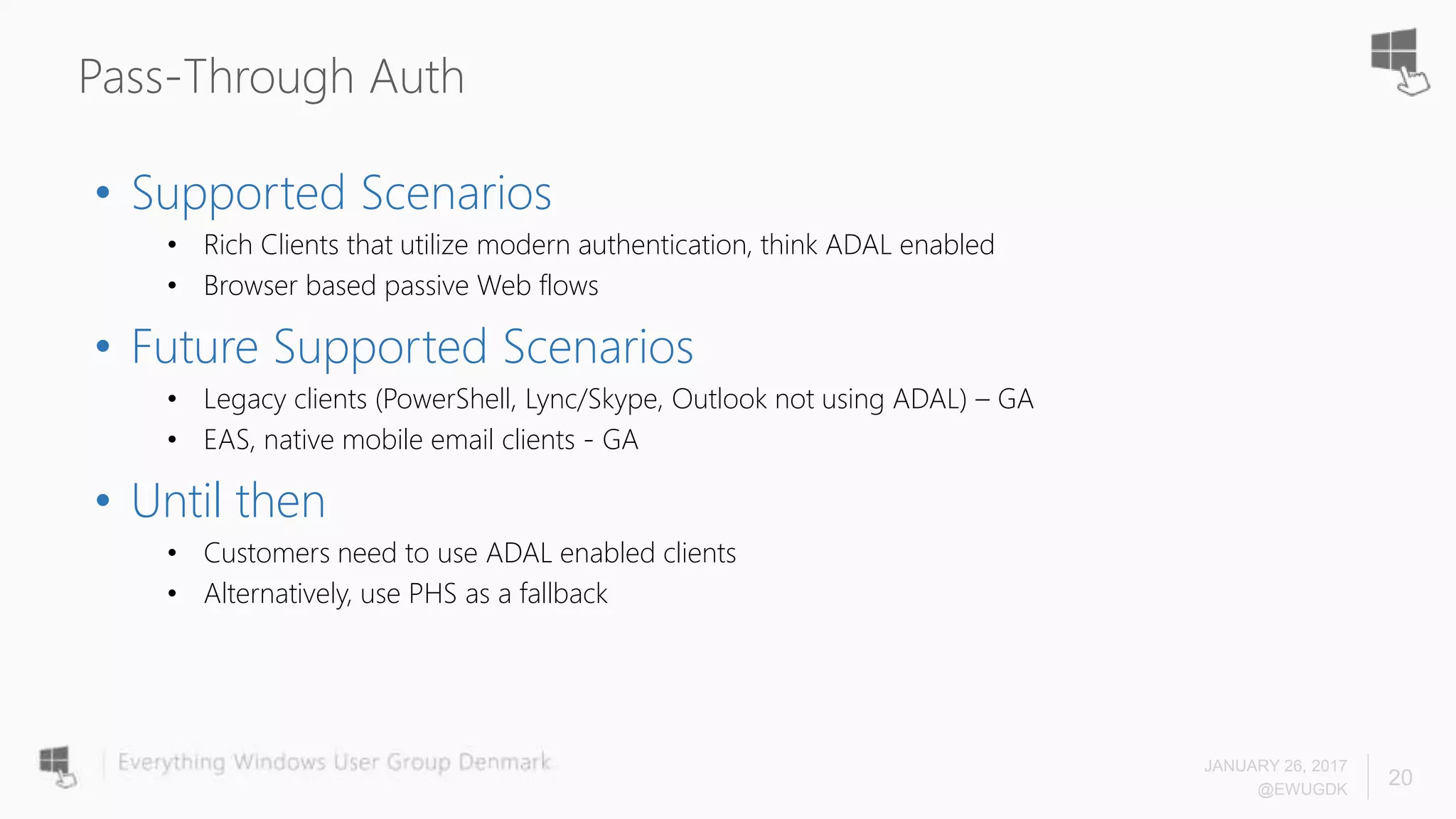
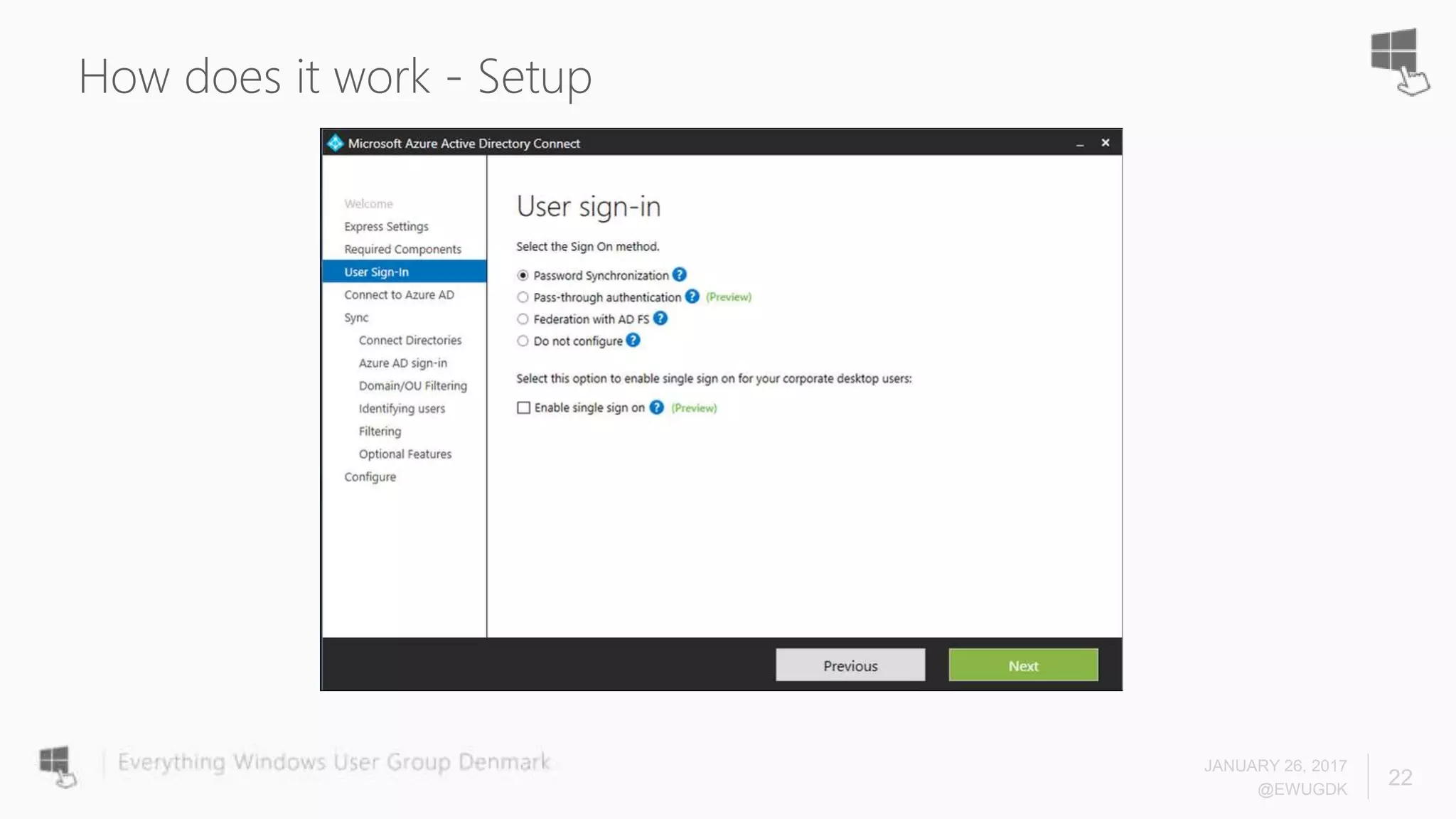
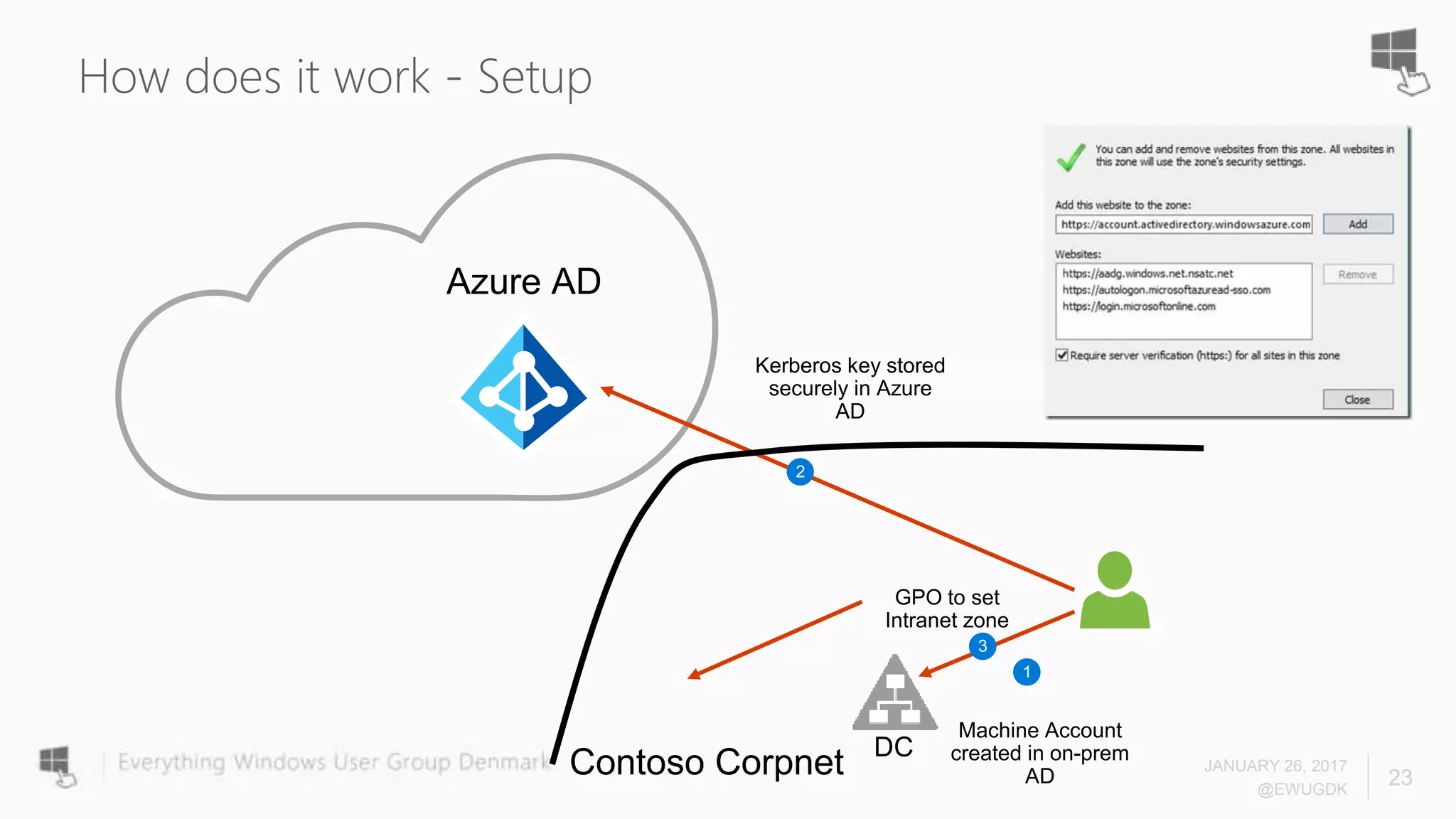
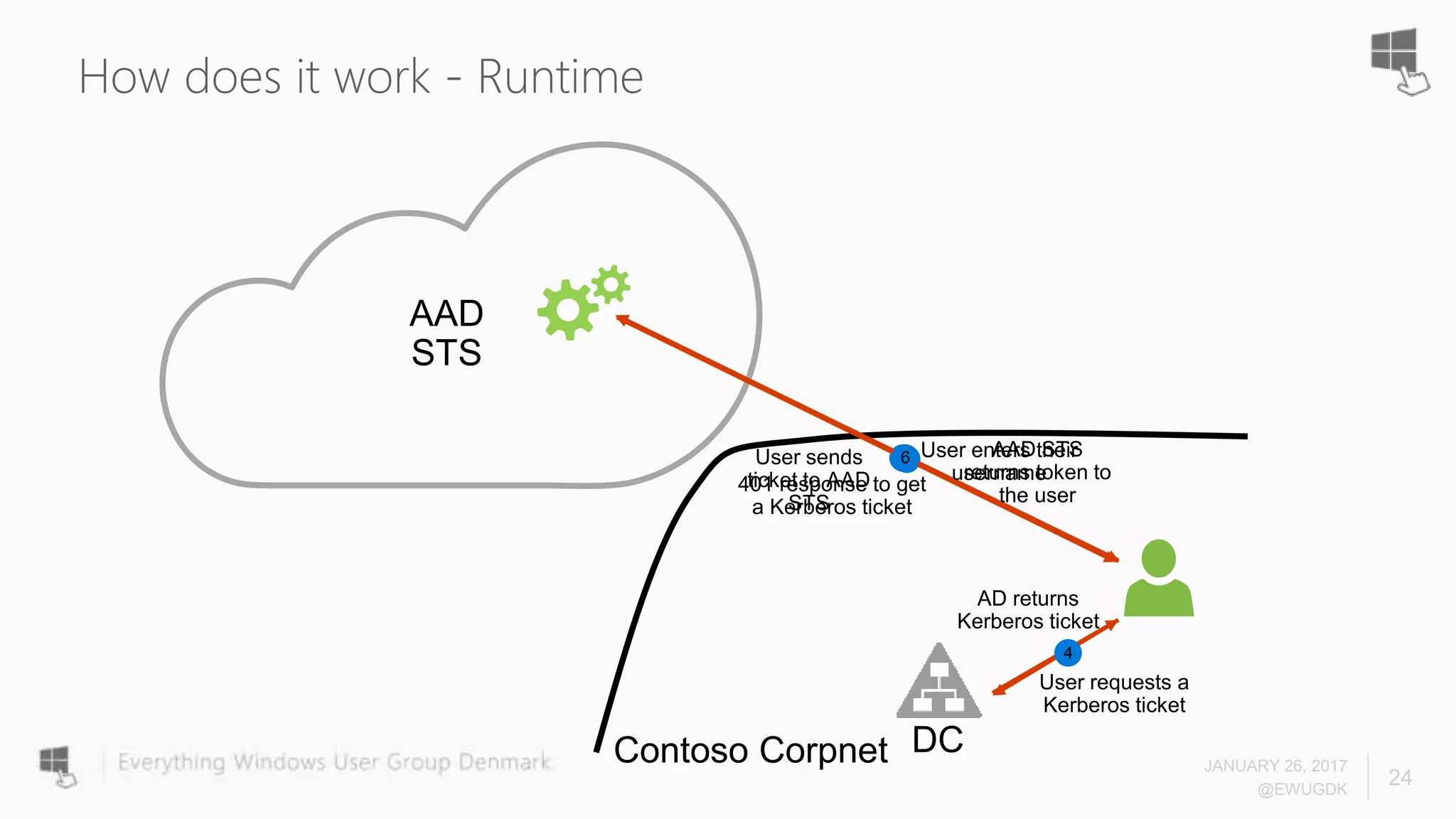
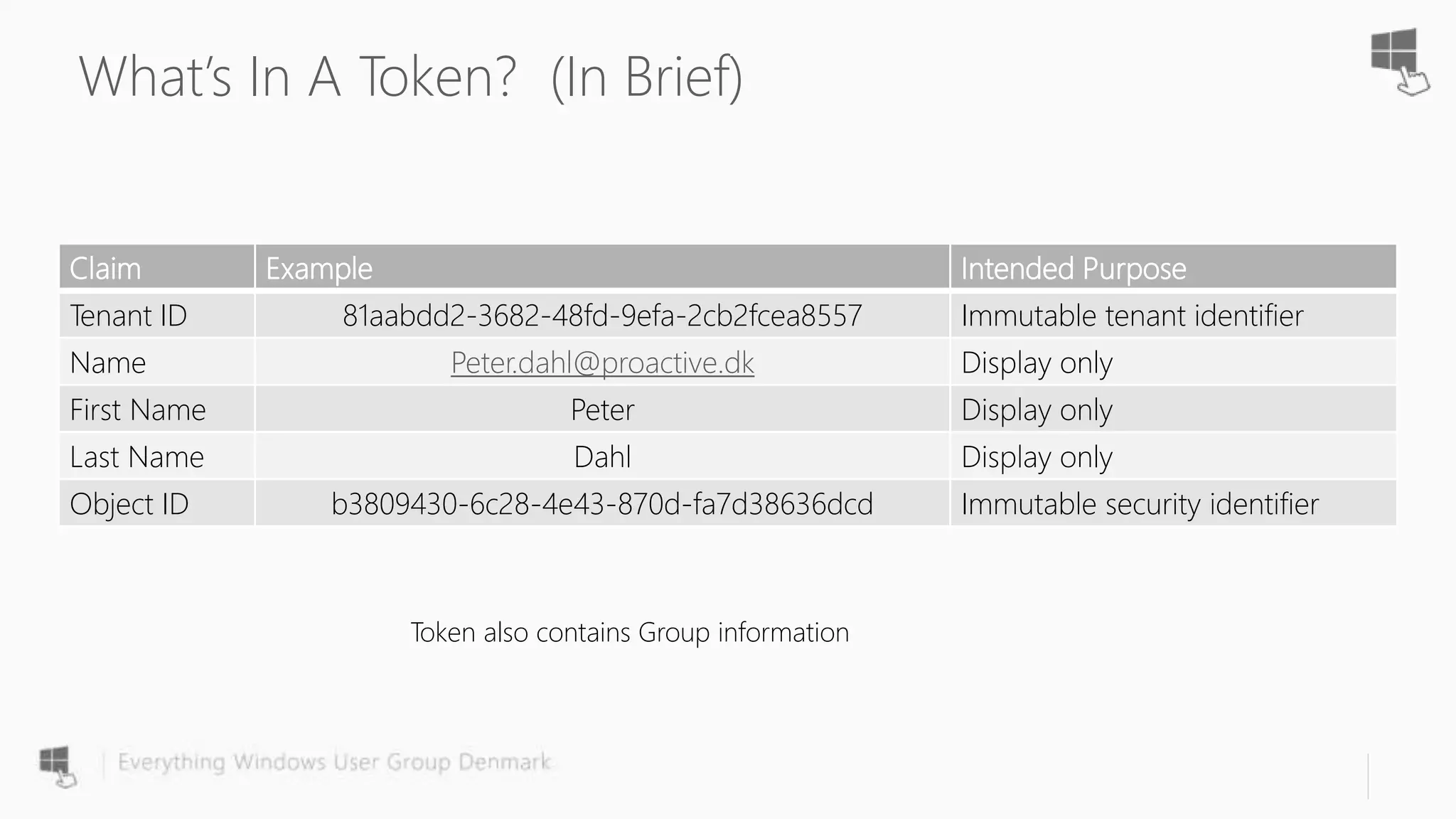
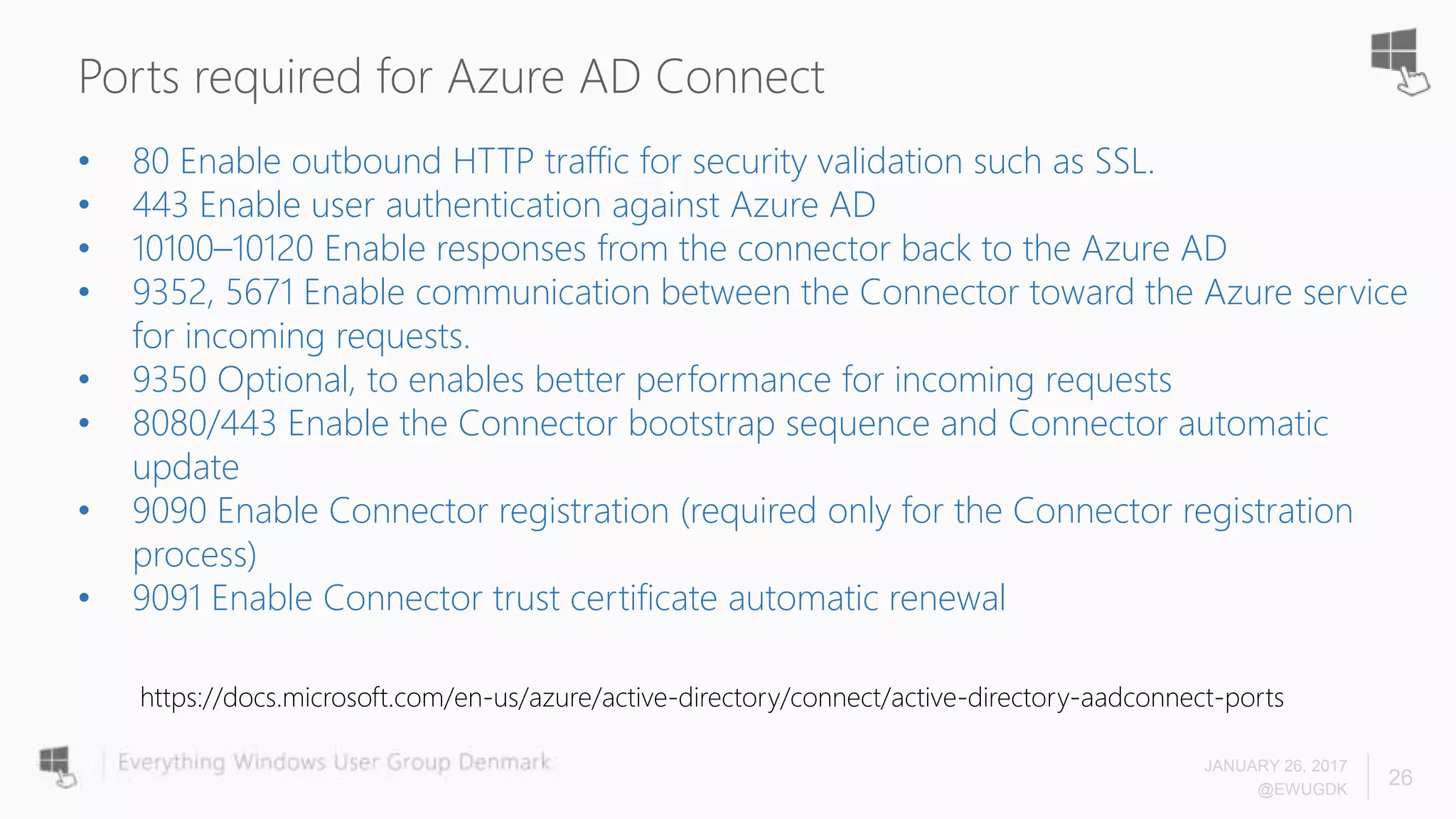
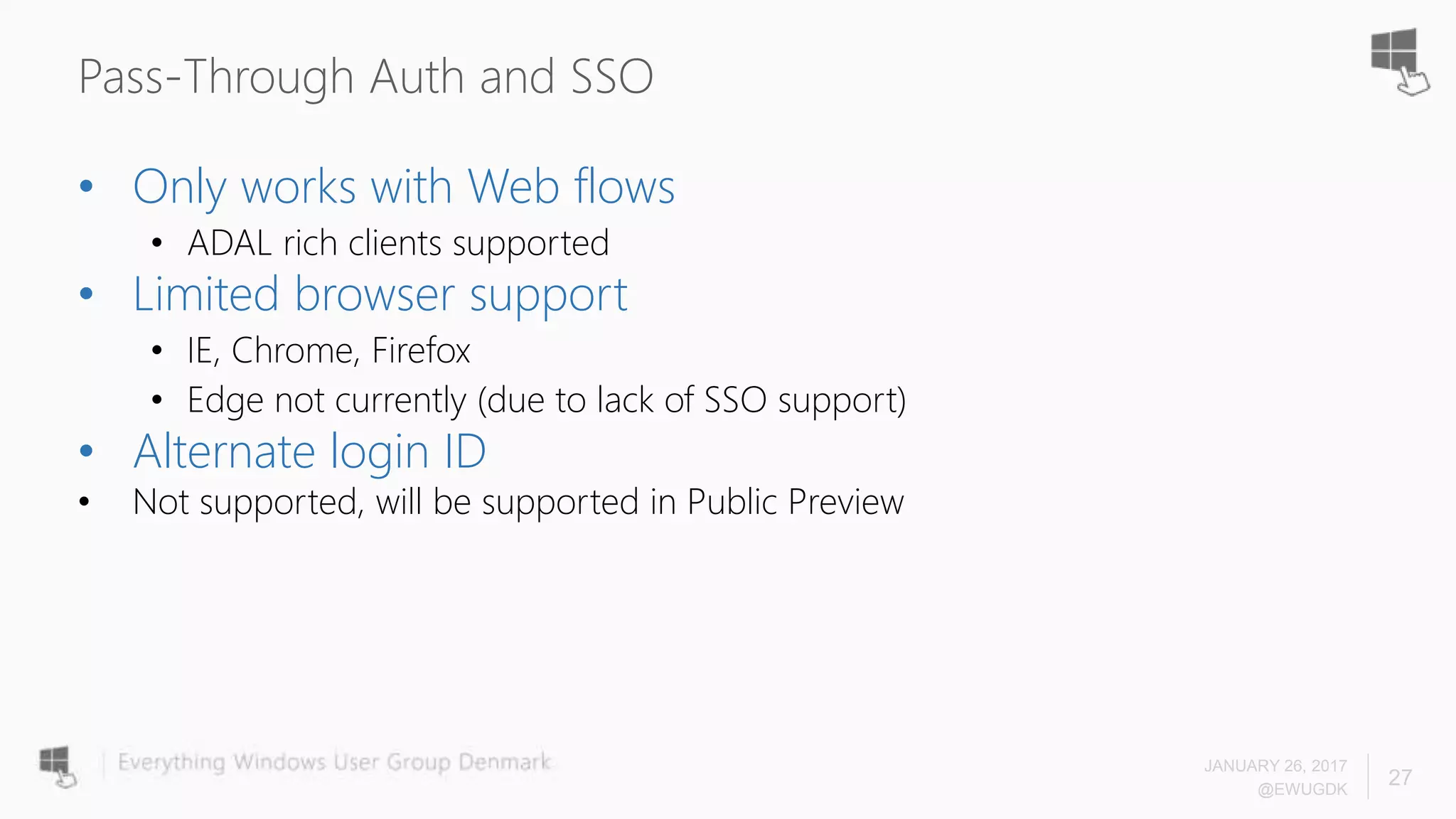
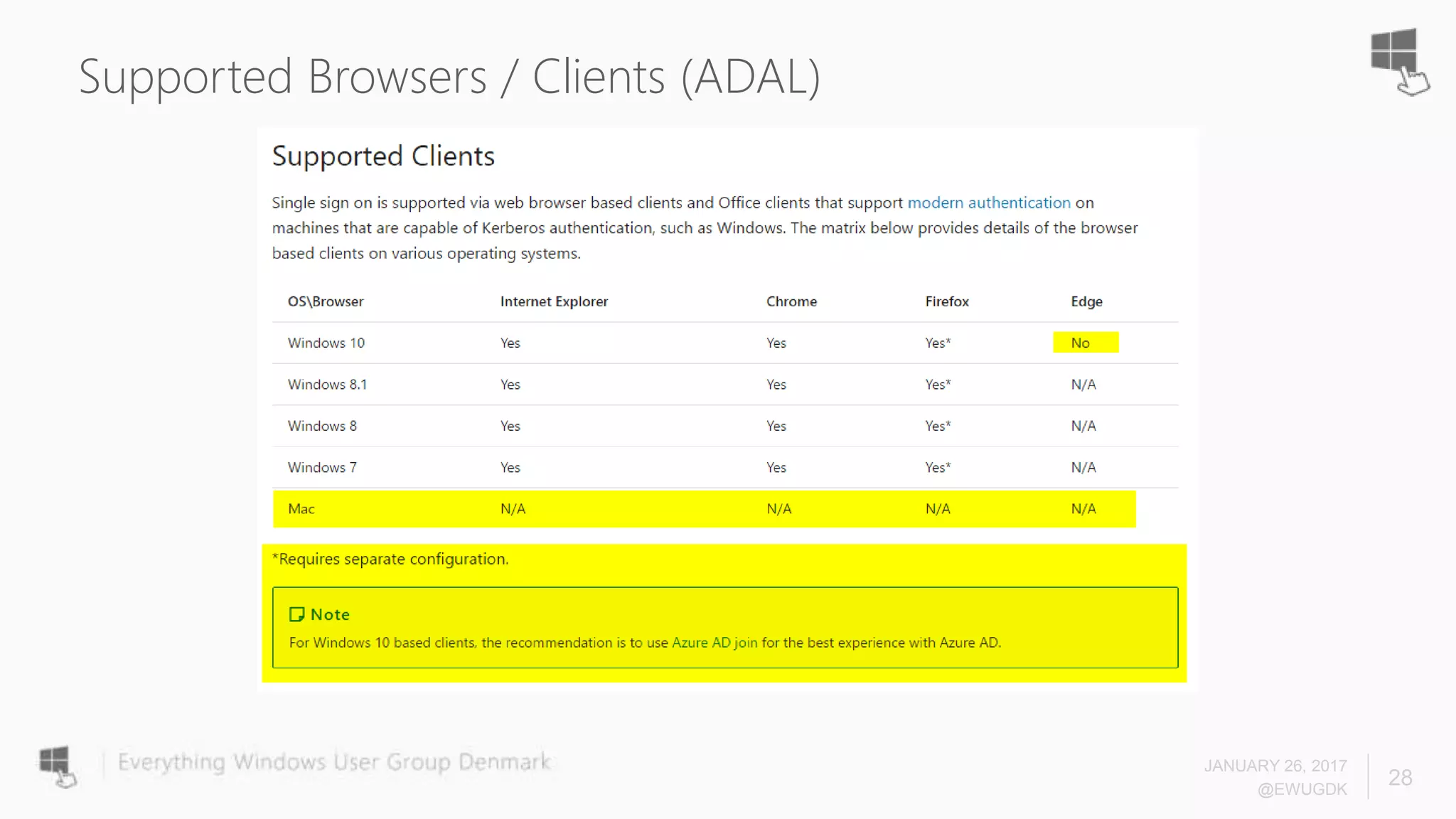
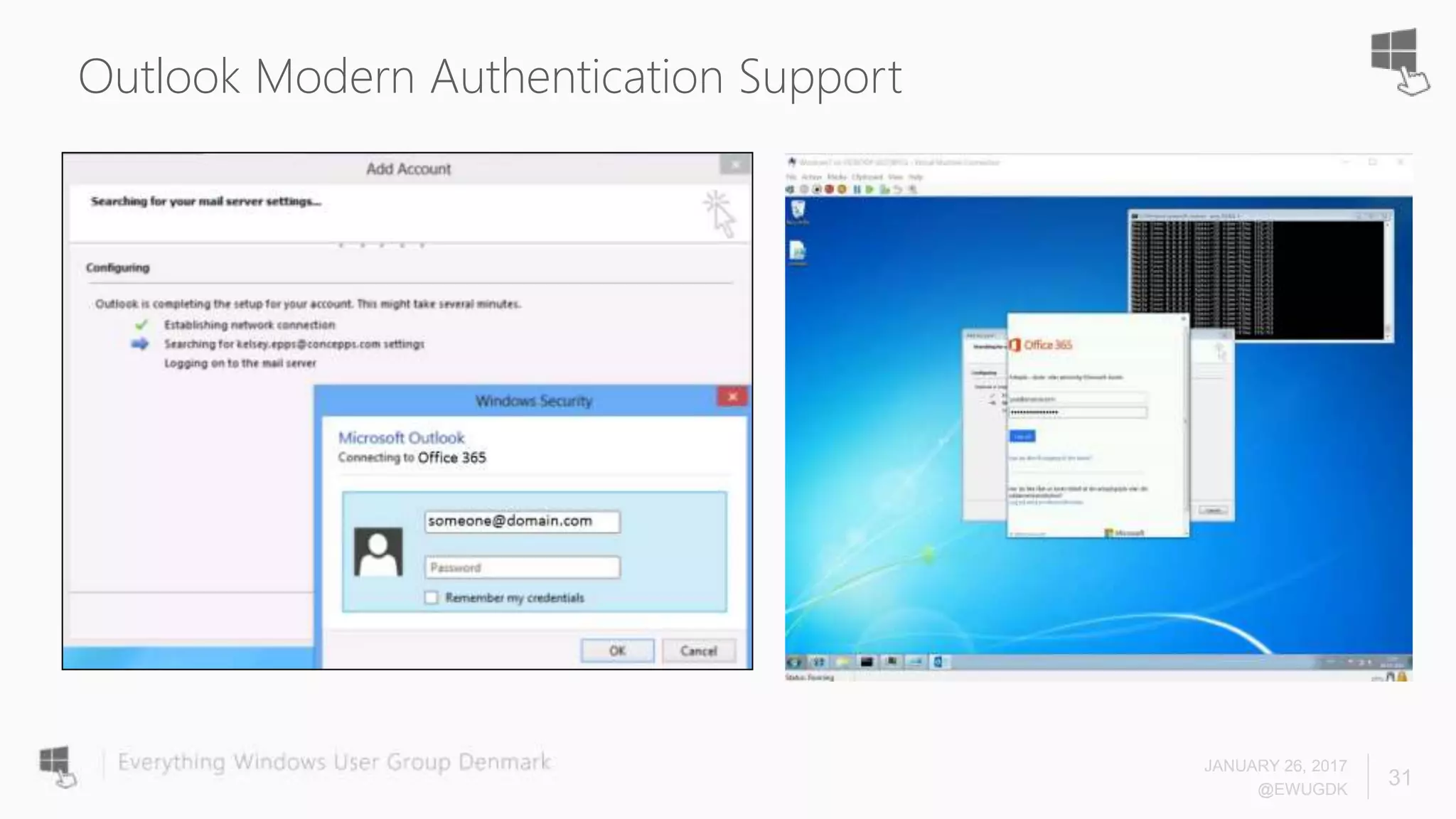
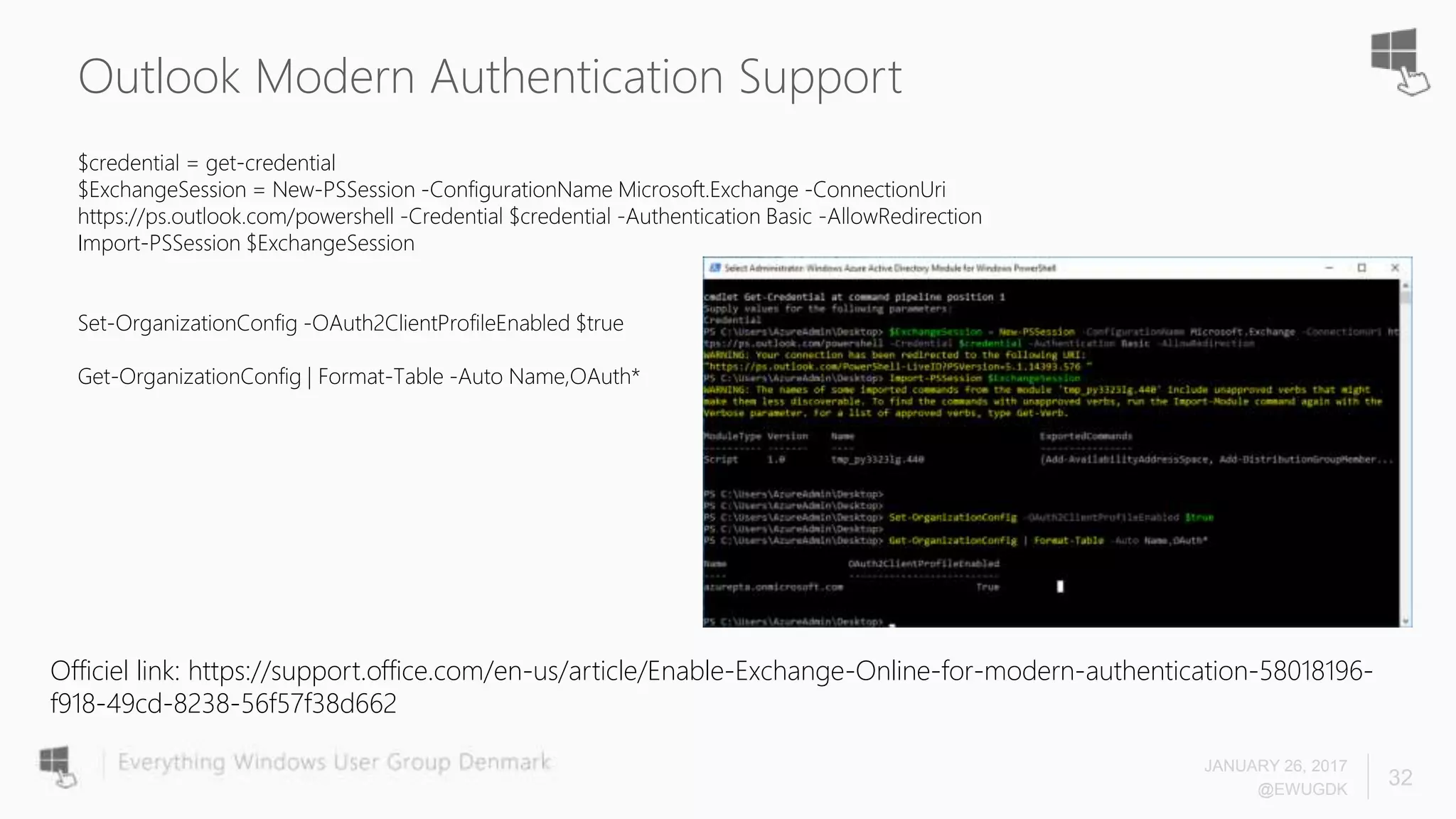
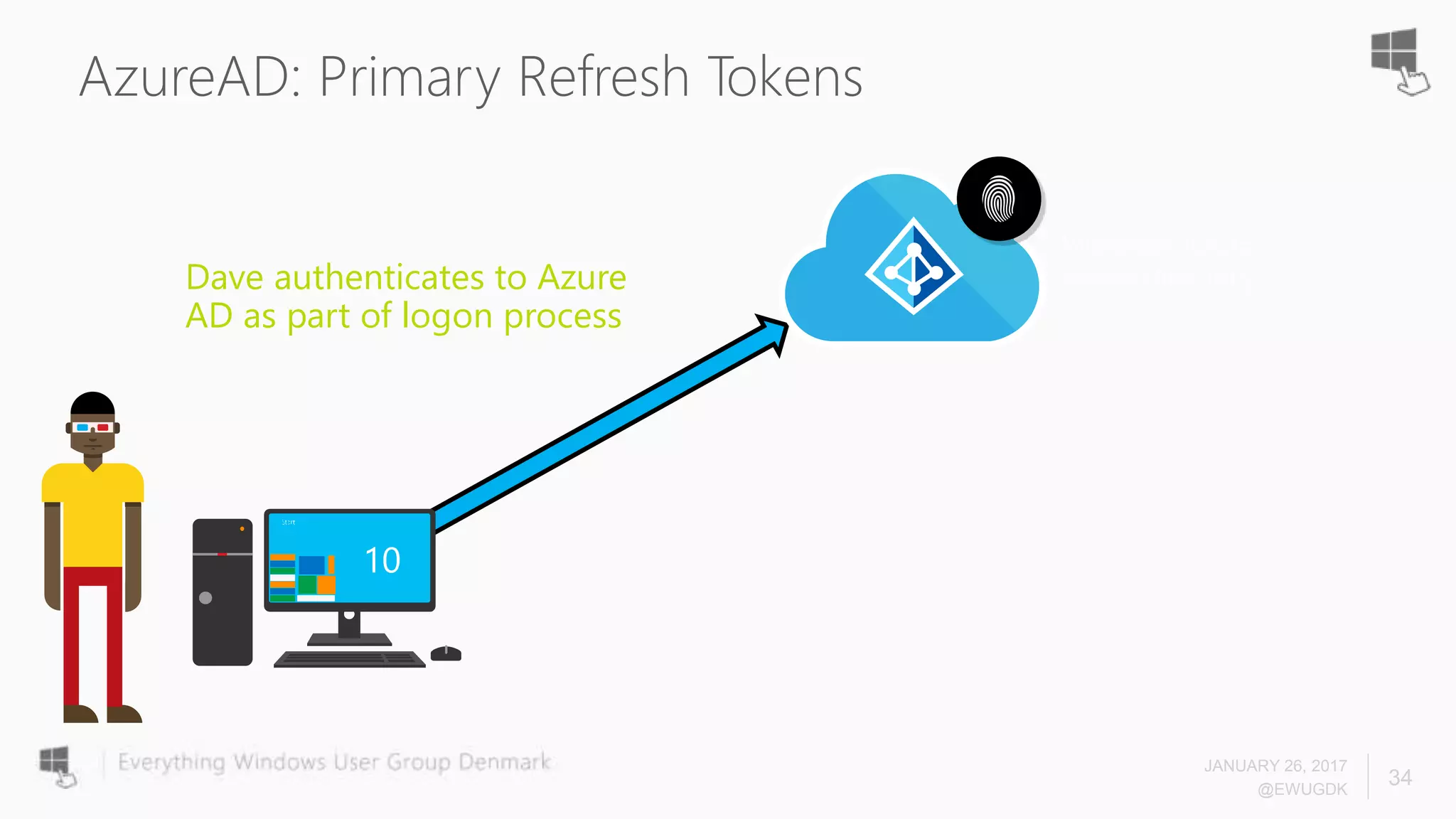
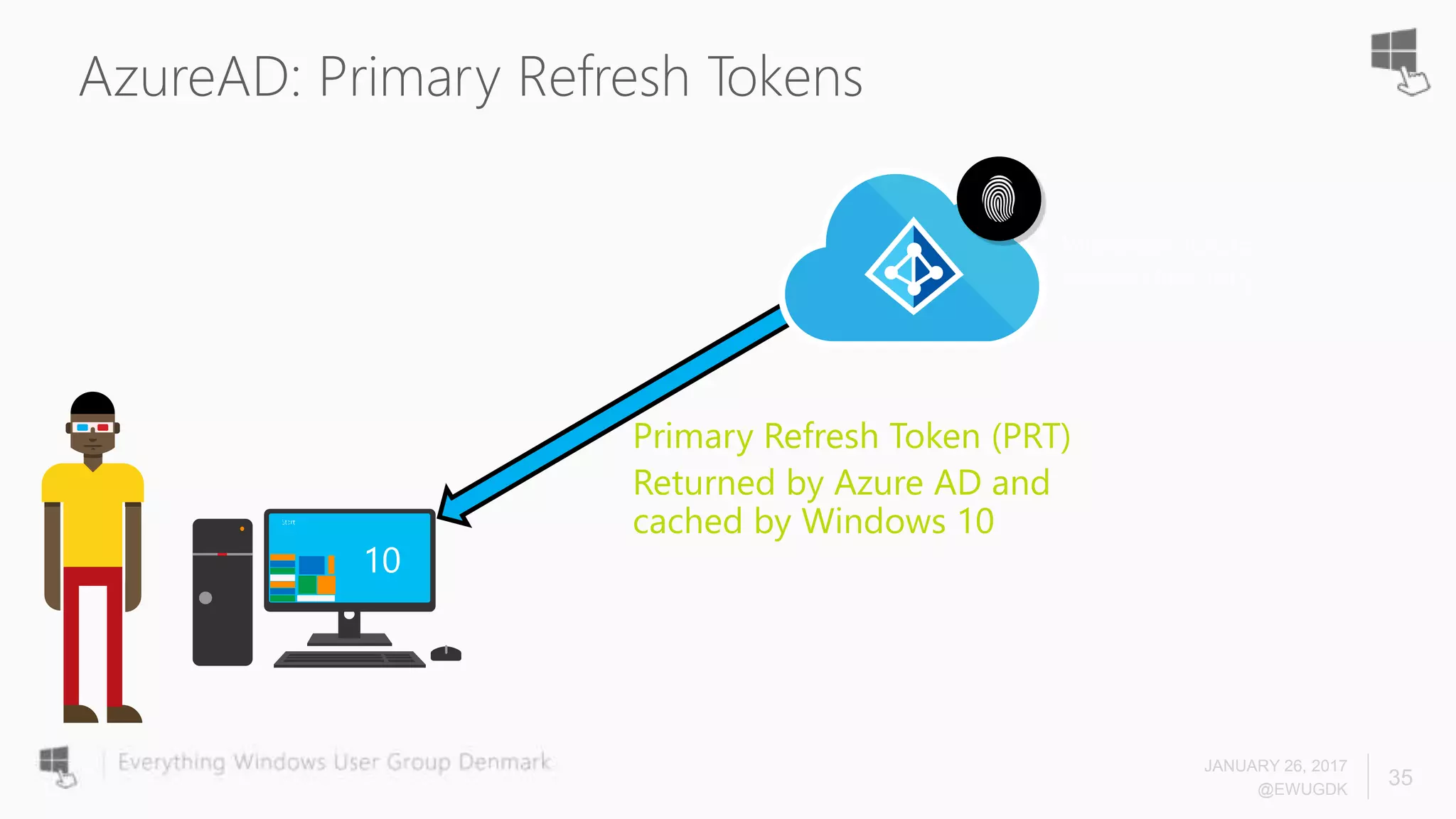
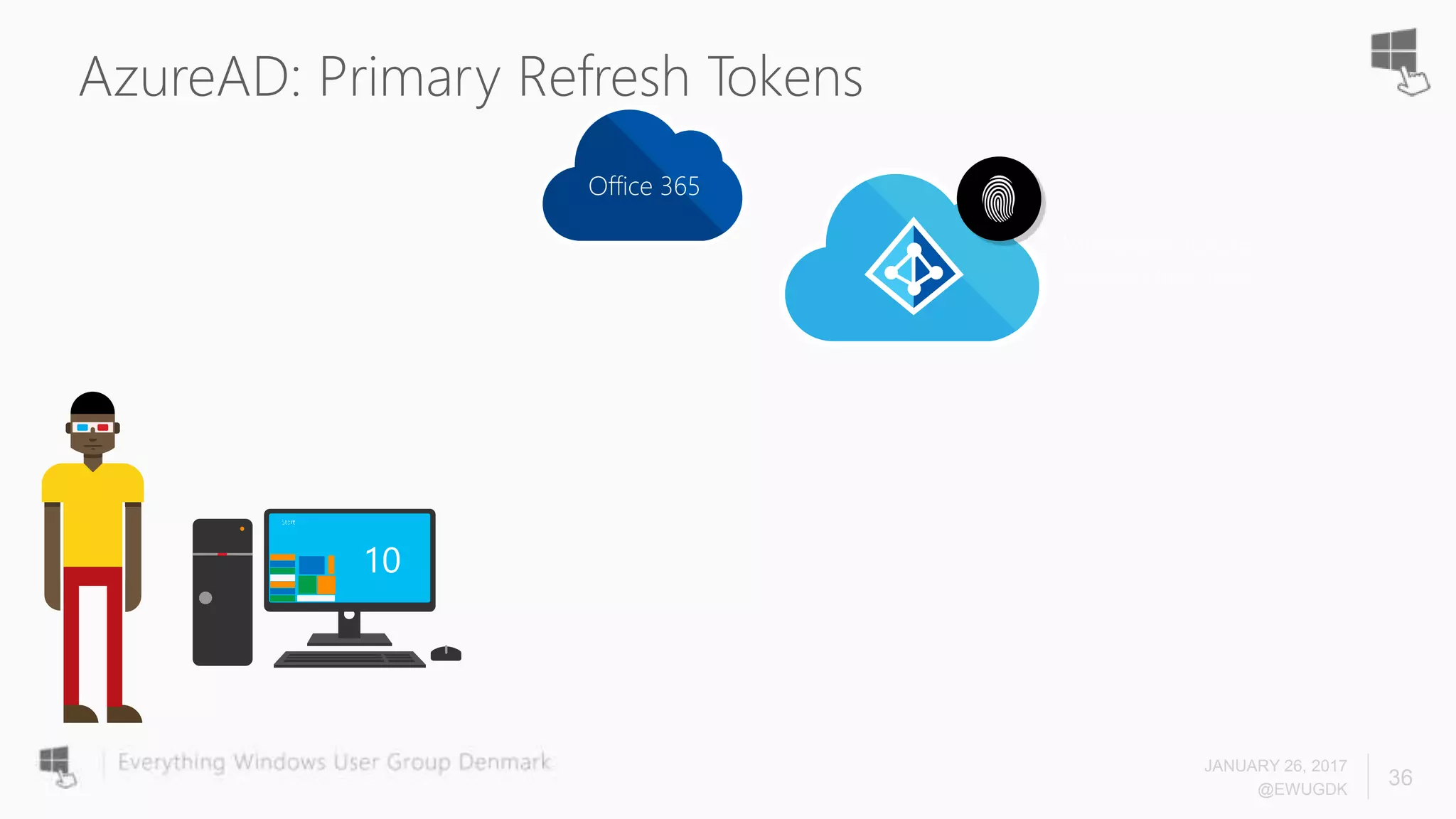
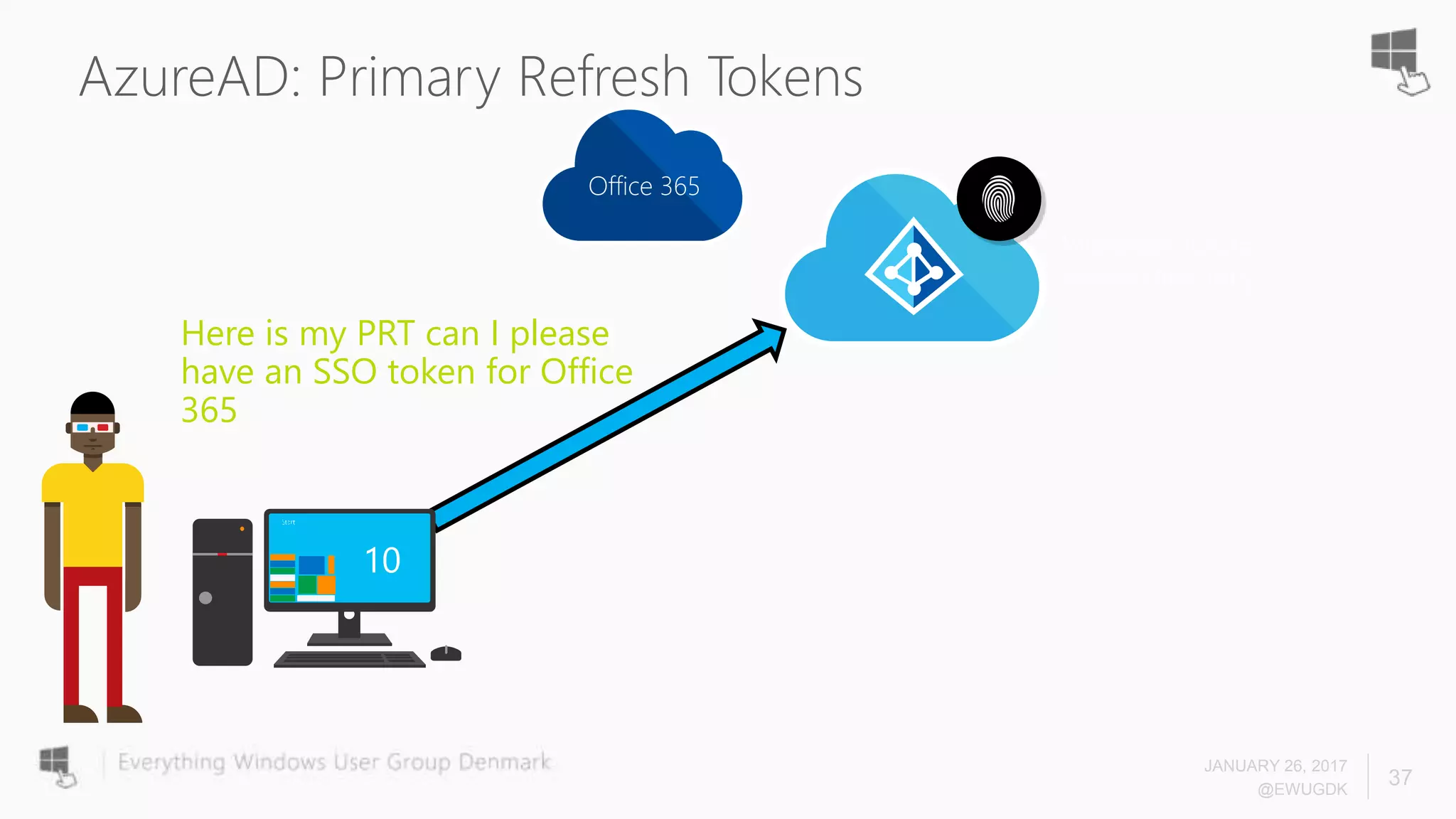
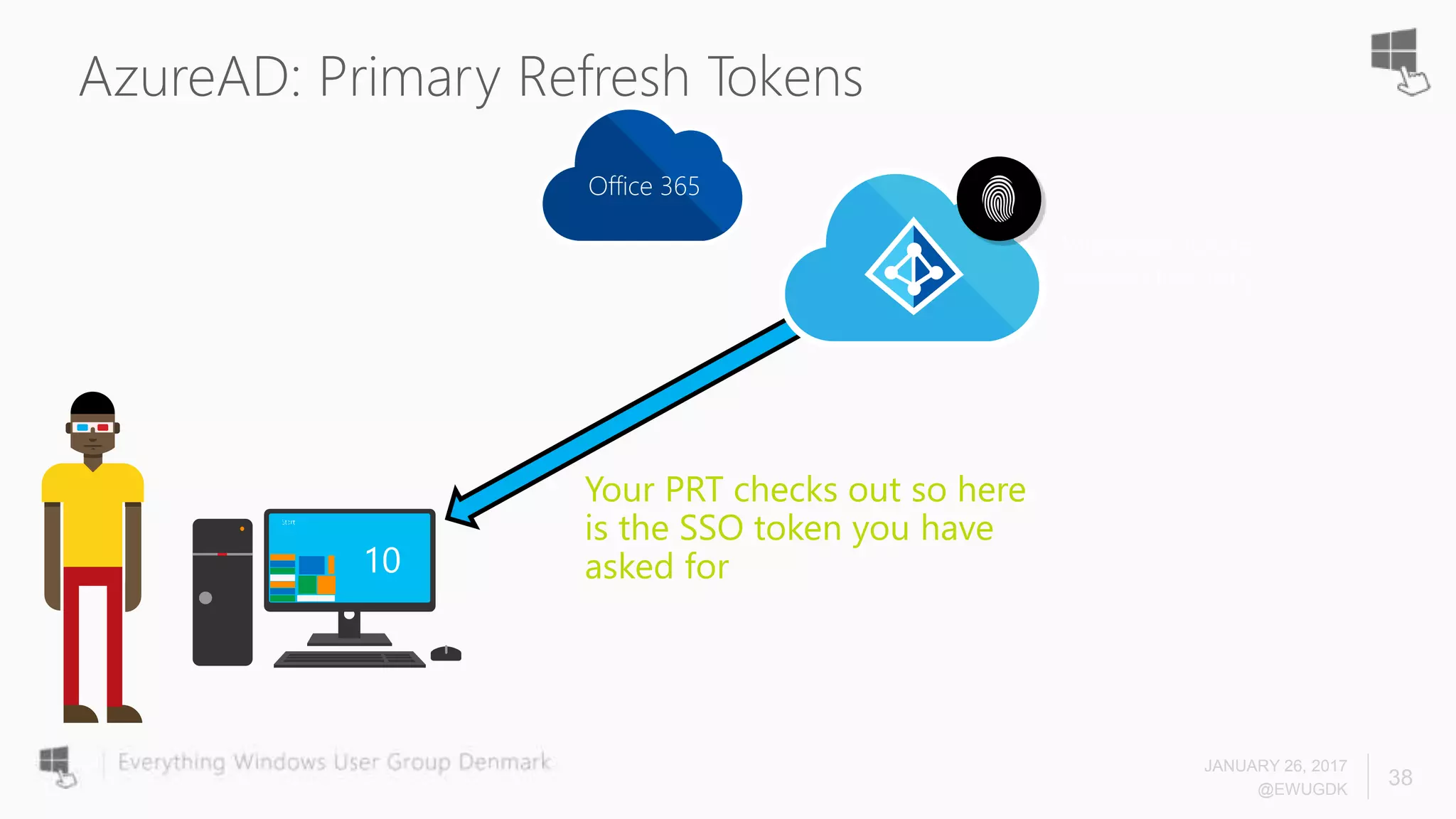
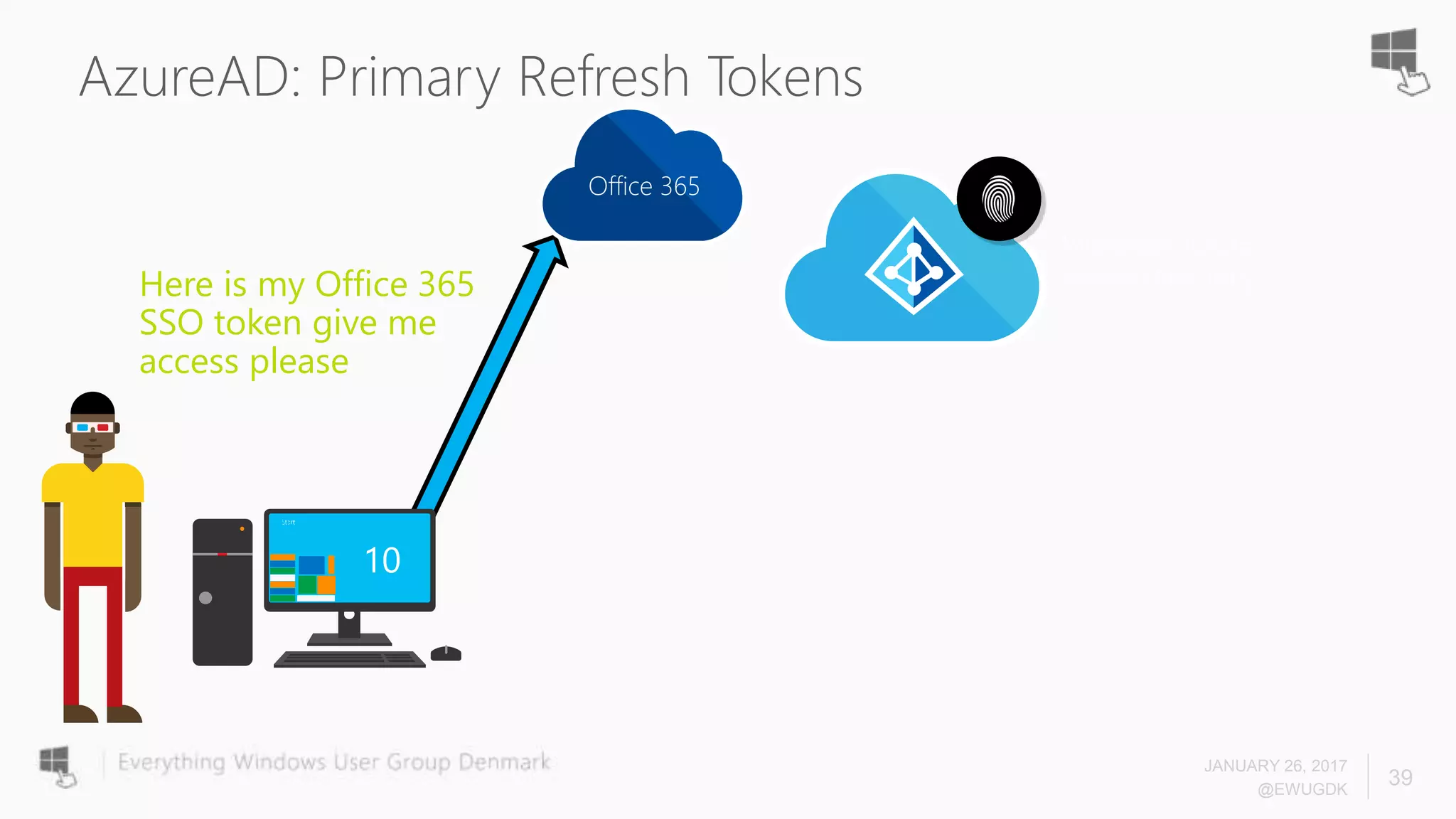
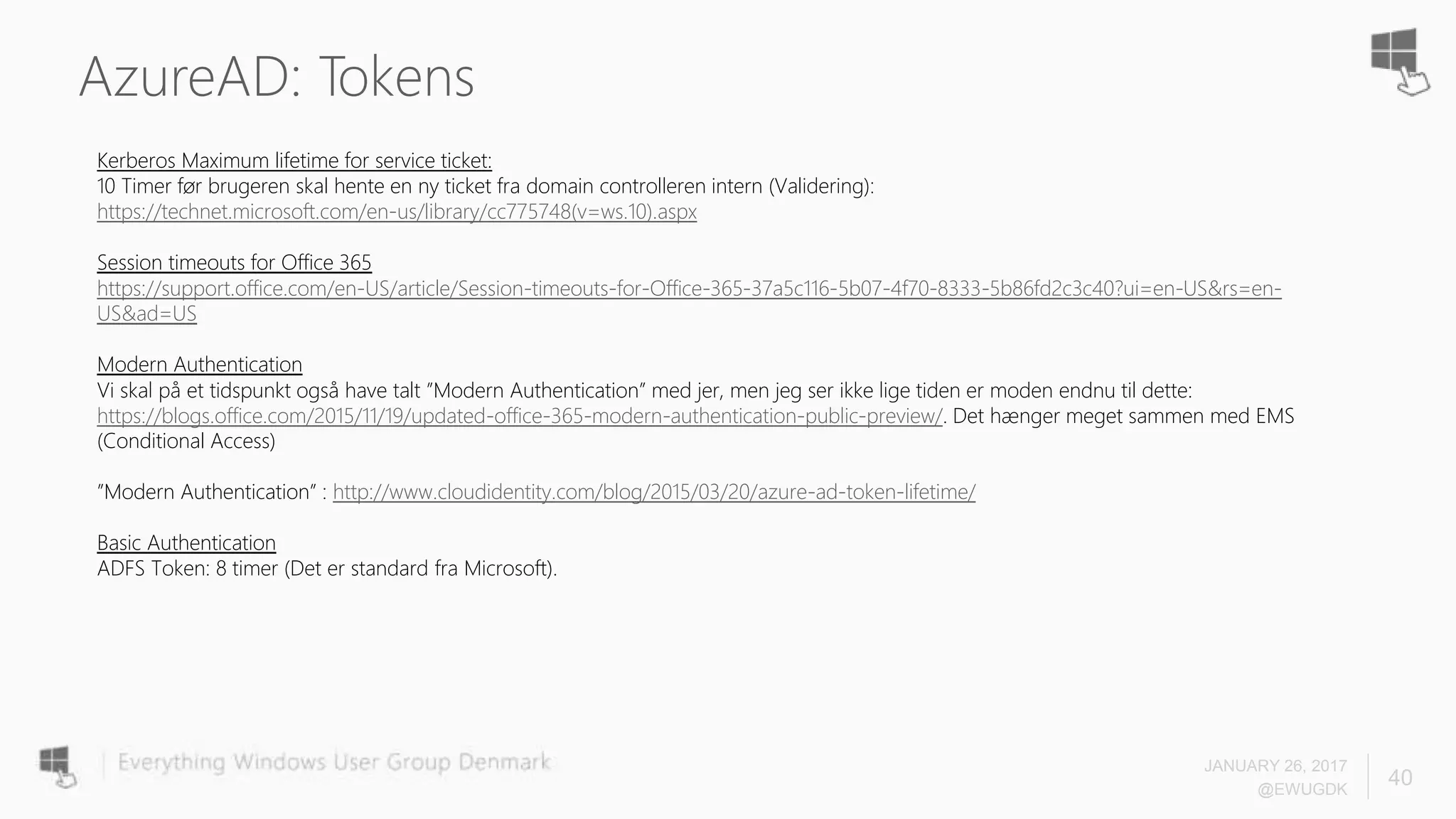
The document discusses Azure AD Pass-Through Authentication (PTA) and Seamless Single Sign-On (SSO), emphasizing their benefits such as simplified deployment, cost-effectiveness, and the ability to validate users' passwords on-premises without needing complex infrastructure. It outlines the differences between PTA and Active Directory Federation Services (AD FS), highlighting that PTA allows for common authentication for both cloud and on-prem users, while AD FS supports smartcard and third-party MFA. Additionally, the text includes insights on usage statistics and the configuration requirements for Azure AD Connect, showcasing the evolving landscape of authentication in cloud services.