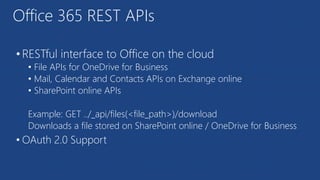
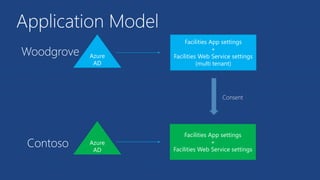
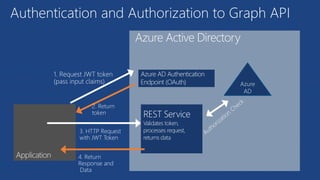
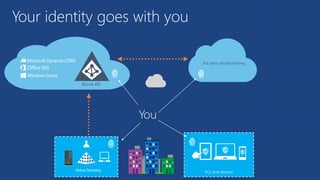
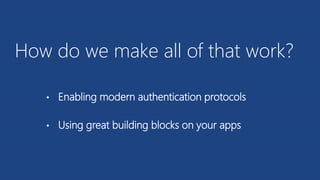
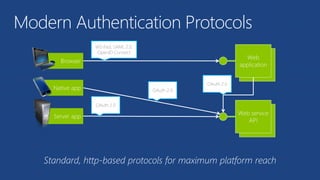
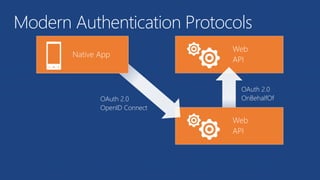
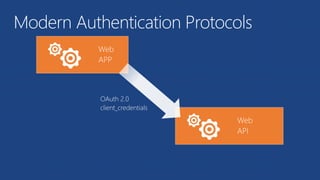
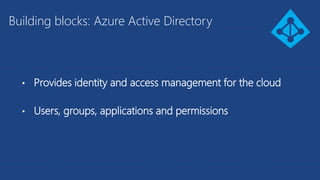
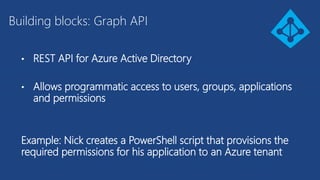
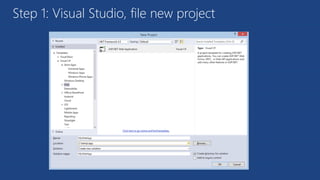
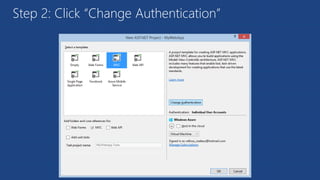
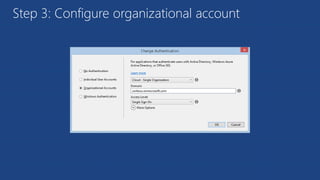
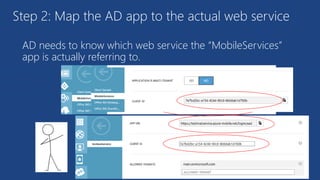
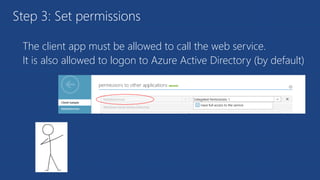
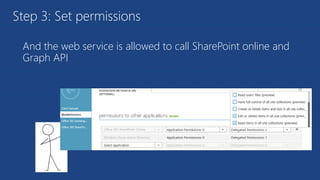
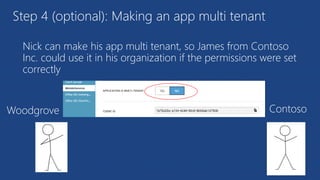
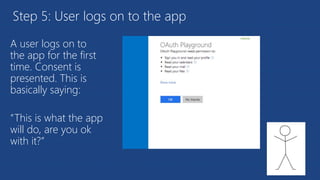
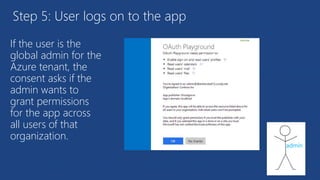
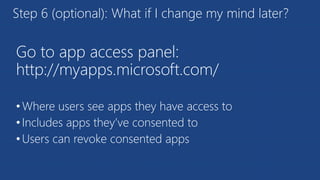
The document discusses the integration of Azure and Office 365 with a focus on authentication protocols such as OAuth 2.0 and their application in building cloud-based applications. It details how to set up Azure Active Directory for identity and access management, and provides examples of using REST APIs for Azure services including Graph API and Office 365. The document includes step-by-step instructions for developers on utilizing these tools to create multi-tenant applications with appropriate permissions.







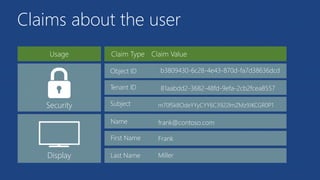








![Active Directory Authentication Library (ADAL)
string clientId = "[Enter client ID as obtained from Azure Portal]";
string authority = "https://login.windows.net/[your tenant name]";
string myURI = "[Enter App ID URI of your service]";
AuthenticationContext authContext = new AuthenticationContext(authority);
AuthenticationResult result = await authContext.AcquireTokenAsync(myURI, clientId);](https://image.slidesharecdn.com/identityando365-150424182519-conversion-gate01/85/Microsoft-Azure-Identity-and-O365-36-320.jpg)