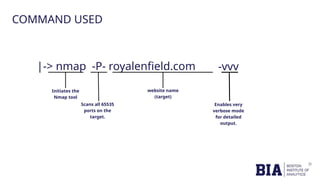
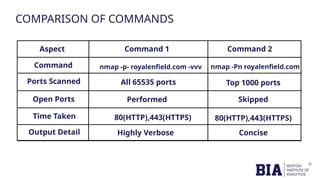
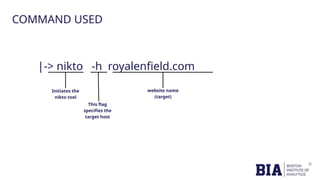
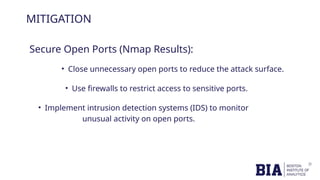
The document outlines a cybersecurity capstone project focused on scanning the website www.royalenfield.com to identify open ports and vulnerabilities. Tools like Burp Suite, Nmap, and Nikto were employed to uncover issues such as a critical OTP bypass vulnerability and missing security headers. Recommendations include strengthening OTP validation, closing unnecessary open ports, and adding security headers to enhance overall web security.