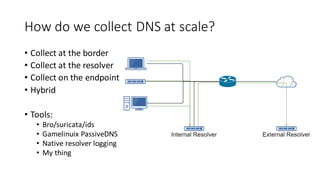
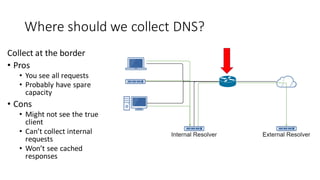
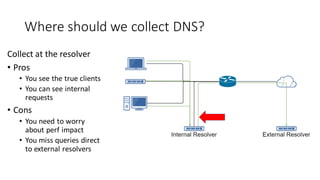
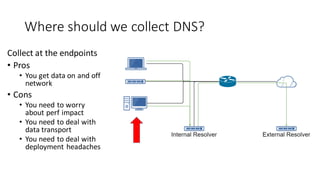
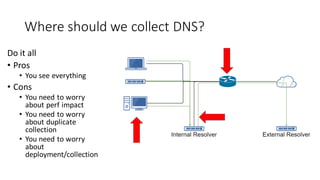
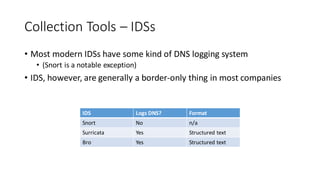
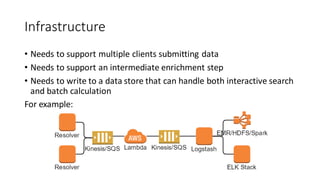
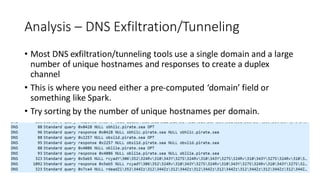
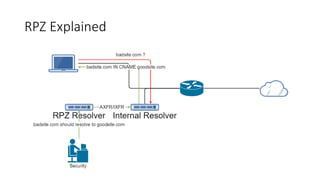
This document discusses DNS monitoring and analysis for incident response. It begins by explaining why DNS is important to monitor, as it underpins all network activity and malware frequently uses DNS. It then discusses collecting DNS data at the border, resolver, and endpoint levels. Common collection tools include IDSes, passive DNS loggers, and native resolver logging. The document outlines enriching DNS data with information like WHOIS and blacklists. It provides examples of DNS analysis like detecting fast flux domains, tunneling, DGA, and low prevalence domains. It notes common false positives and discusses response actions like using RPZ (Response Policy Zones) to block or redirect malicious DNS queries.