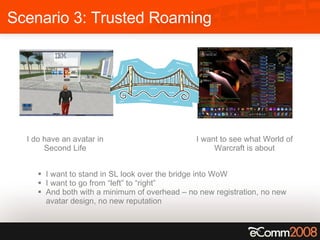
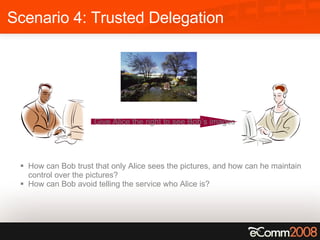
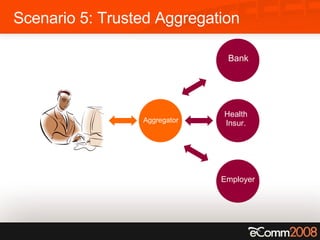
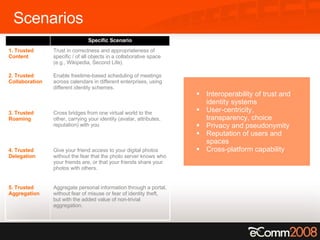
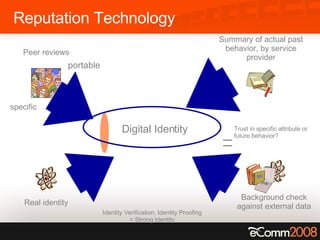
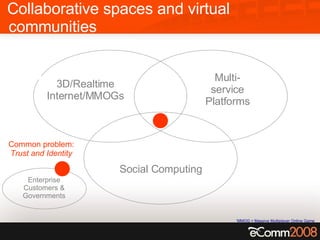
The document discusses the critical role of trust and identity in virtual worlds and collaborative spaces, emphasizing the challenges posed by anonymity and potential threats such as online harassment and reputation fraud. It highlights the historical context of digital identity, the evolution of trust mechanisms, and the increasing demand for user-centric identity management. Additionally, it outlines five scenarios for trusted interactions and calls for improved practices and technologies to enhance privacy and security in online environments.





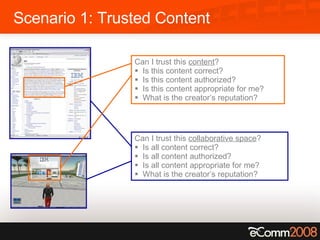
![Scenario 2: Trusted Collaboration [email_address] [email_address] Request freetime How can Patrick locate Paul’s calendar? Can Paul trust this request ? Is this request legitimate? Who is this requestor? Patrick Paul](https://image.slidesharecdn.com/tonynadalinecomm2008-1207737346064808-8/85/Tony-Nadalin-presentation-at-eComm-2008-9-320.jpg)