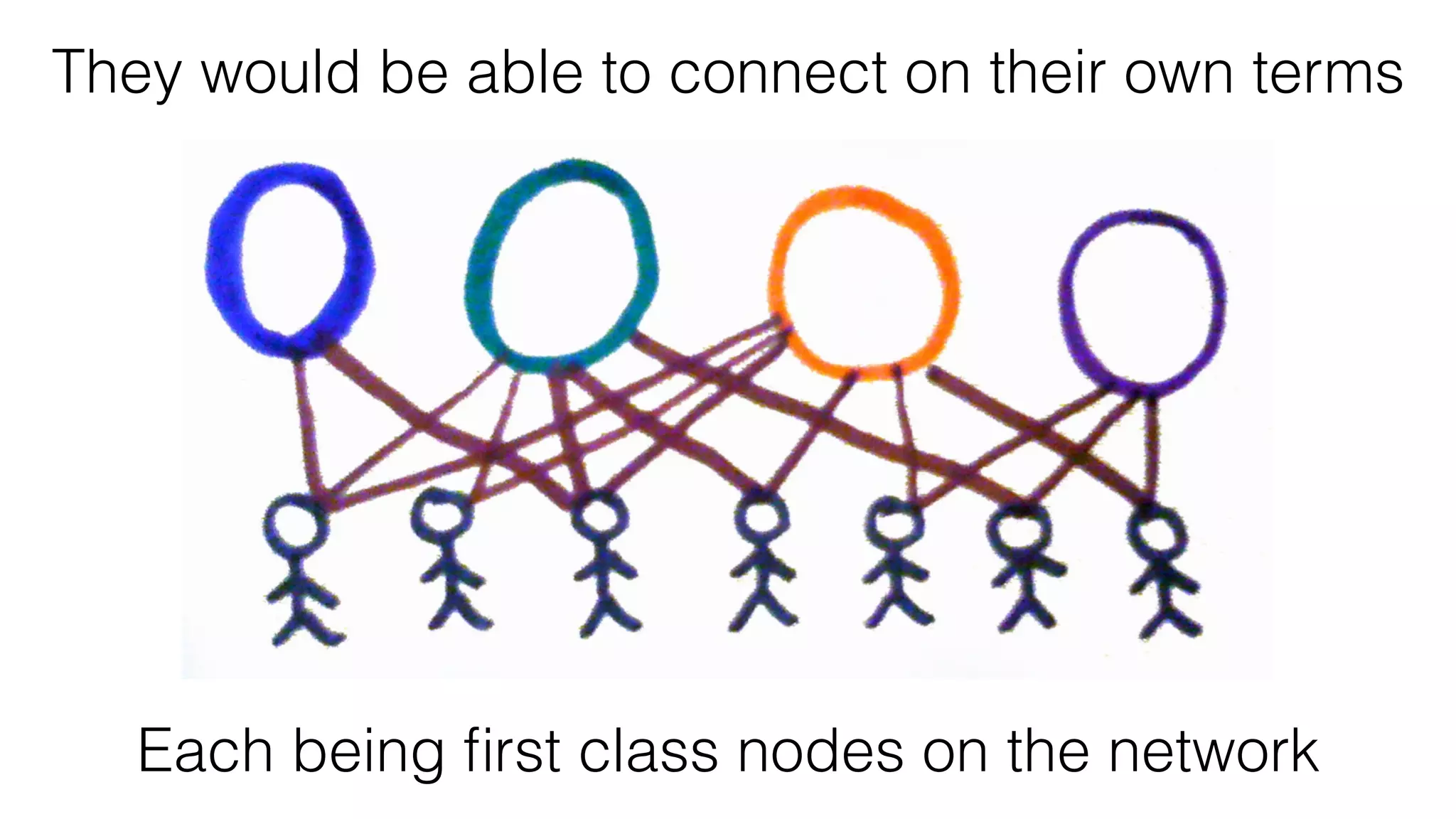
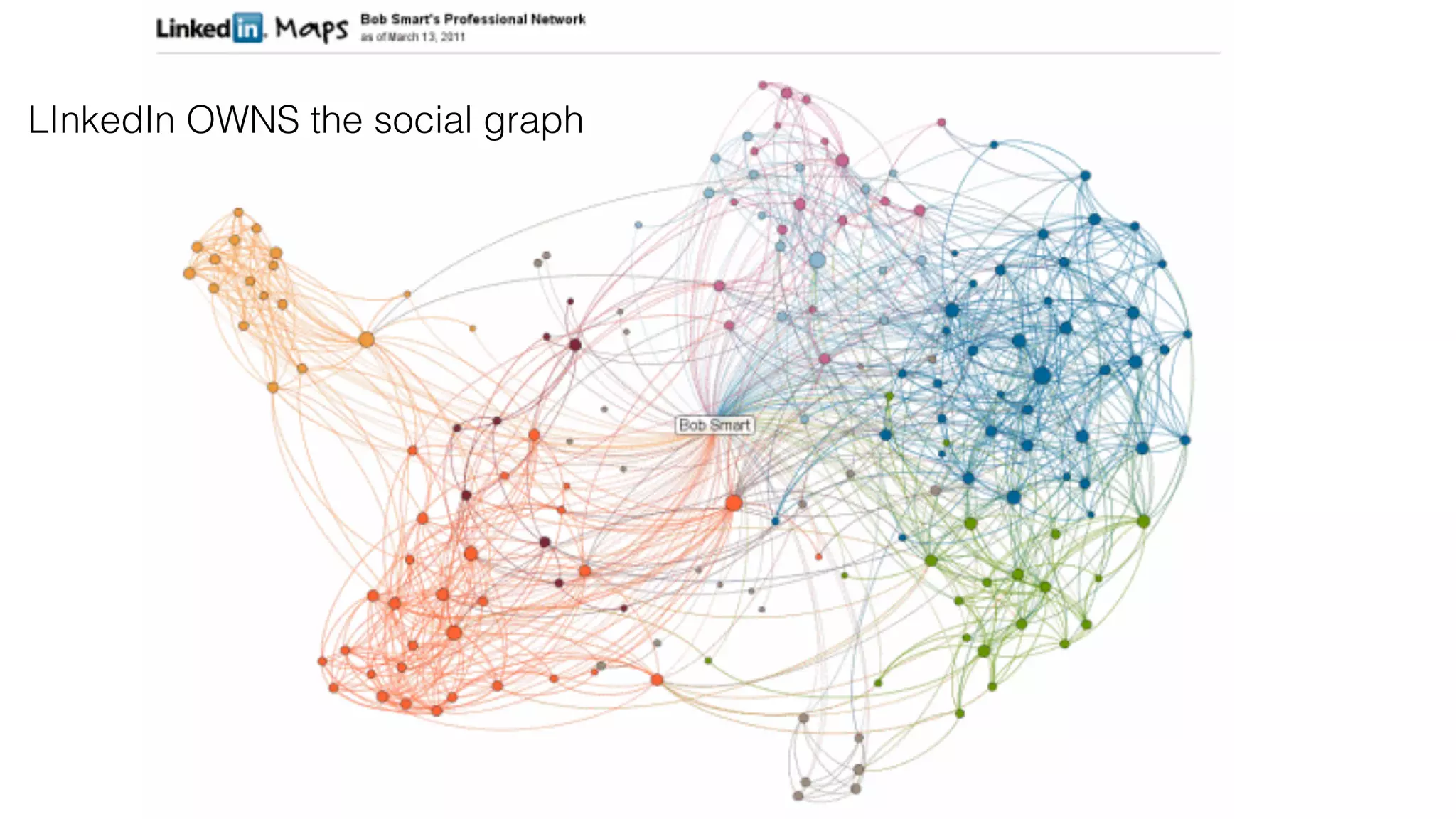
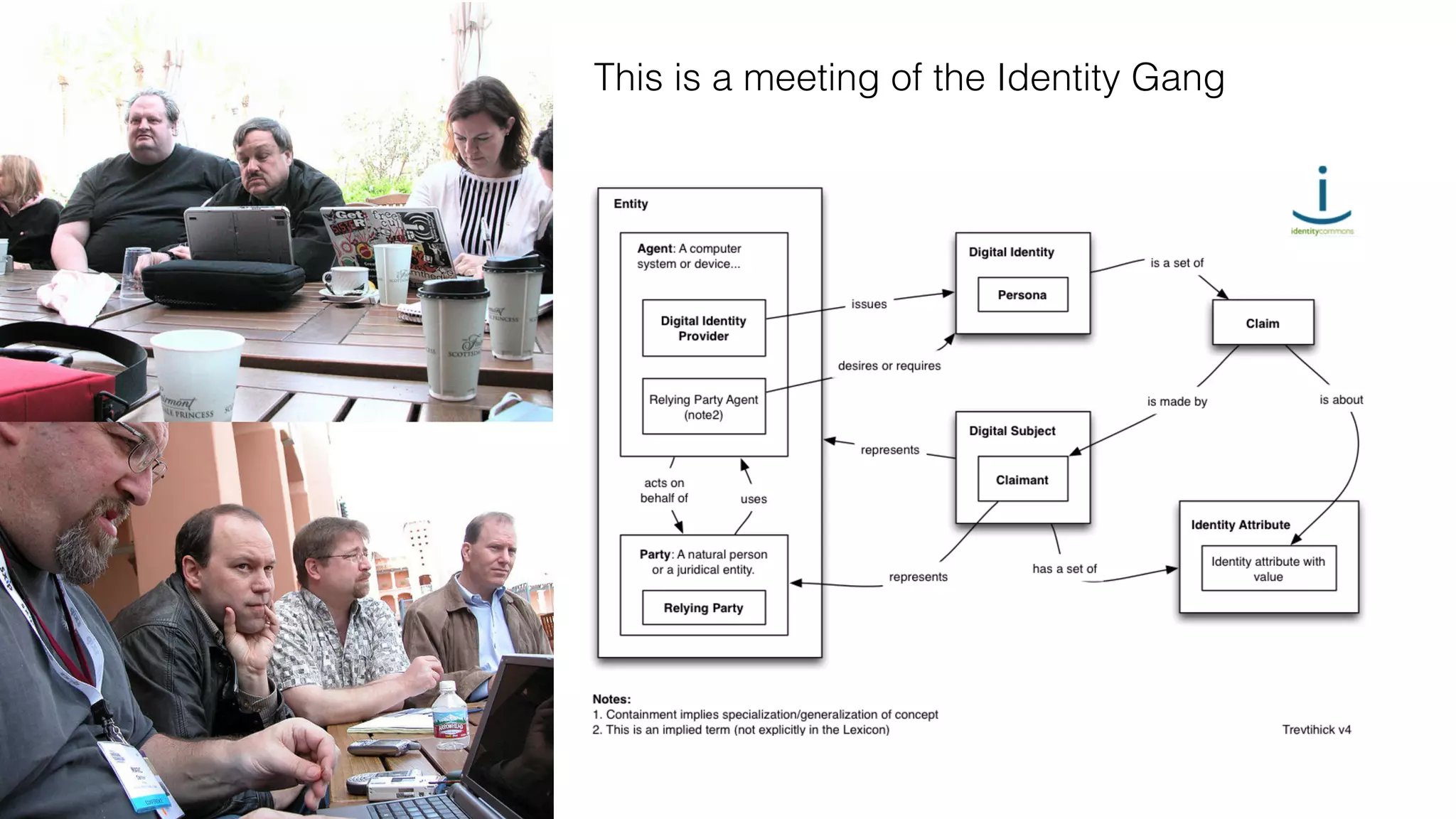
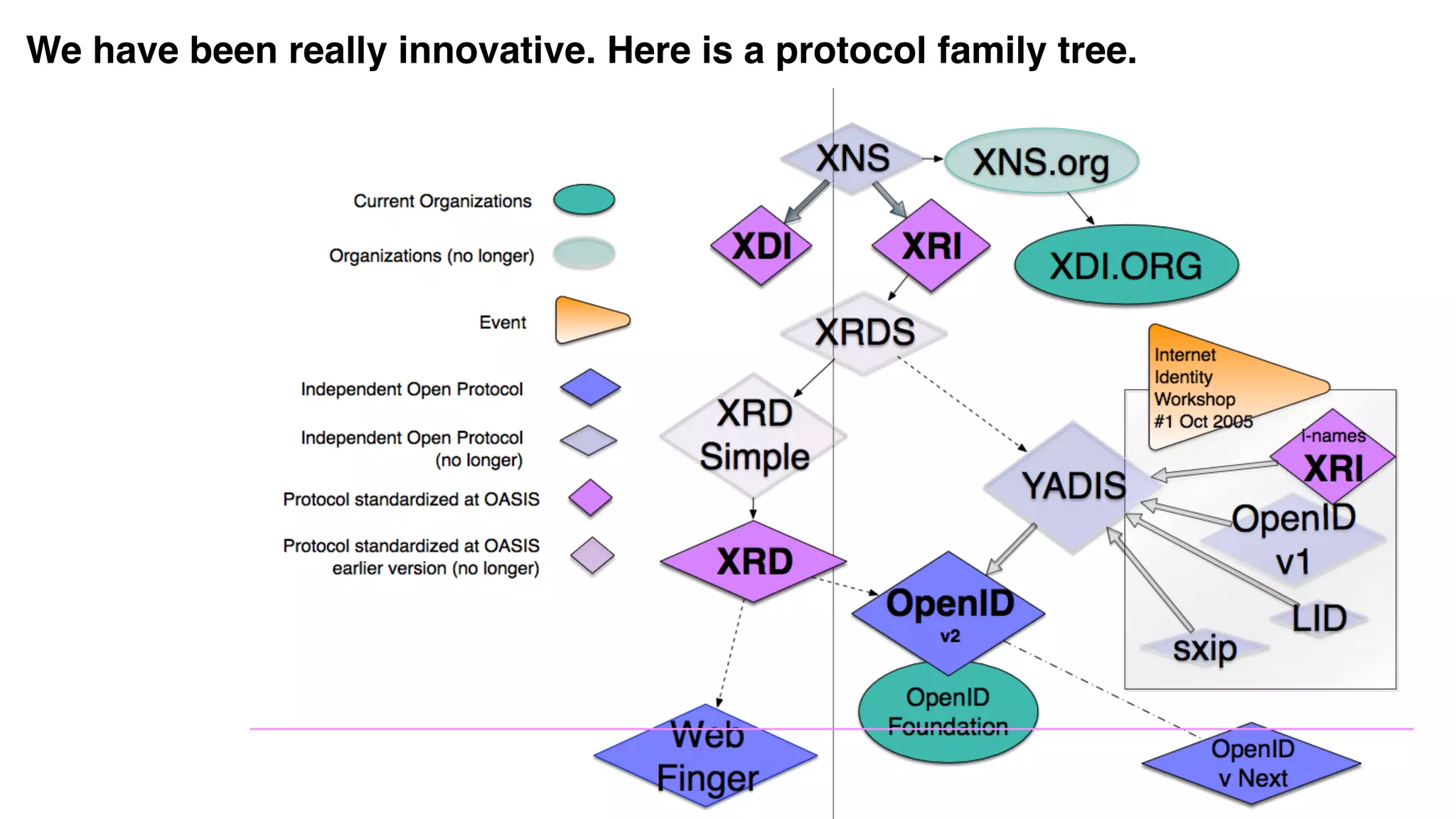
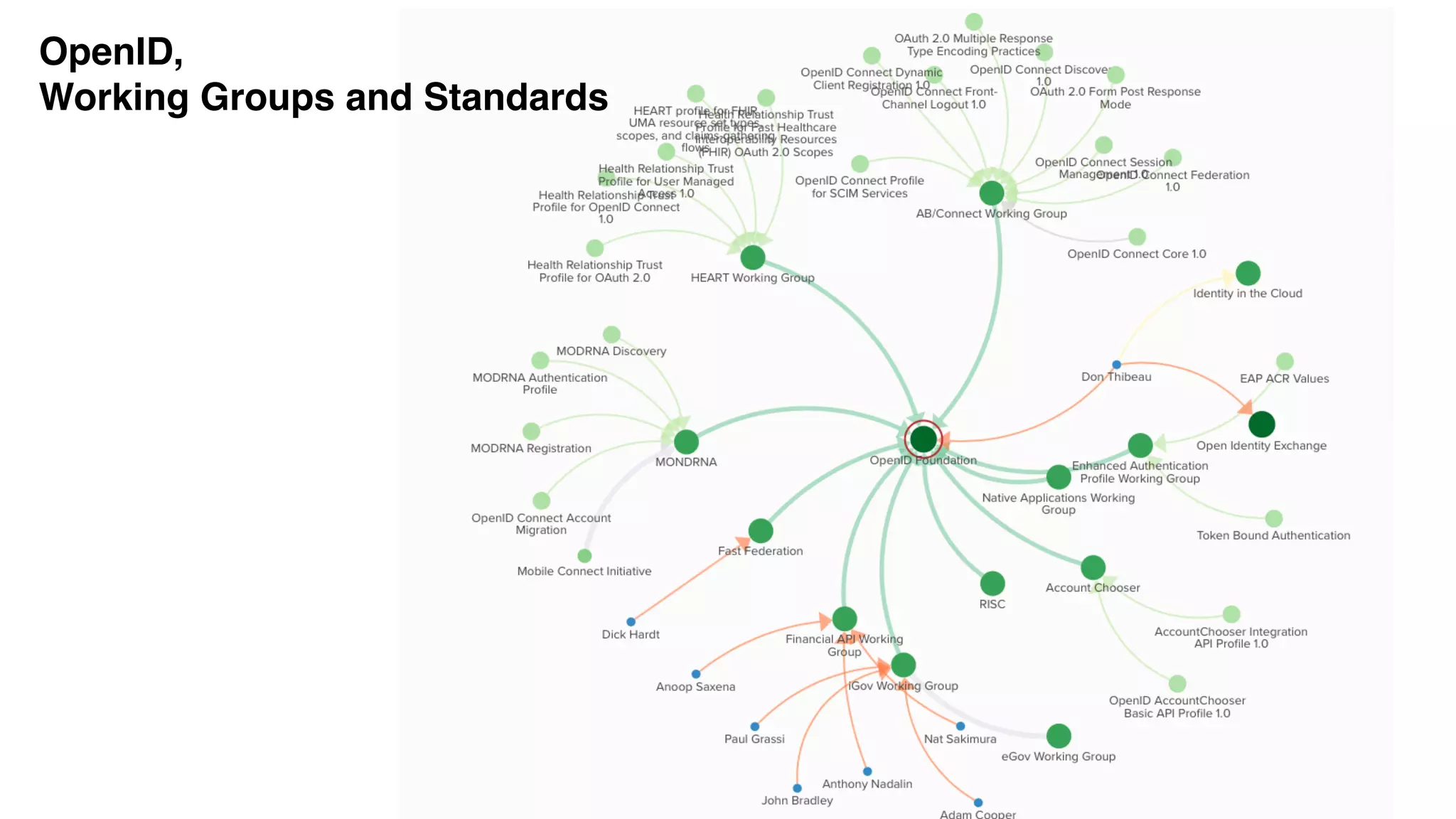
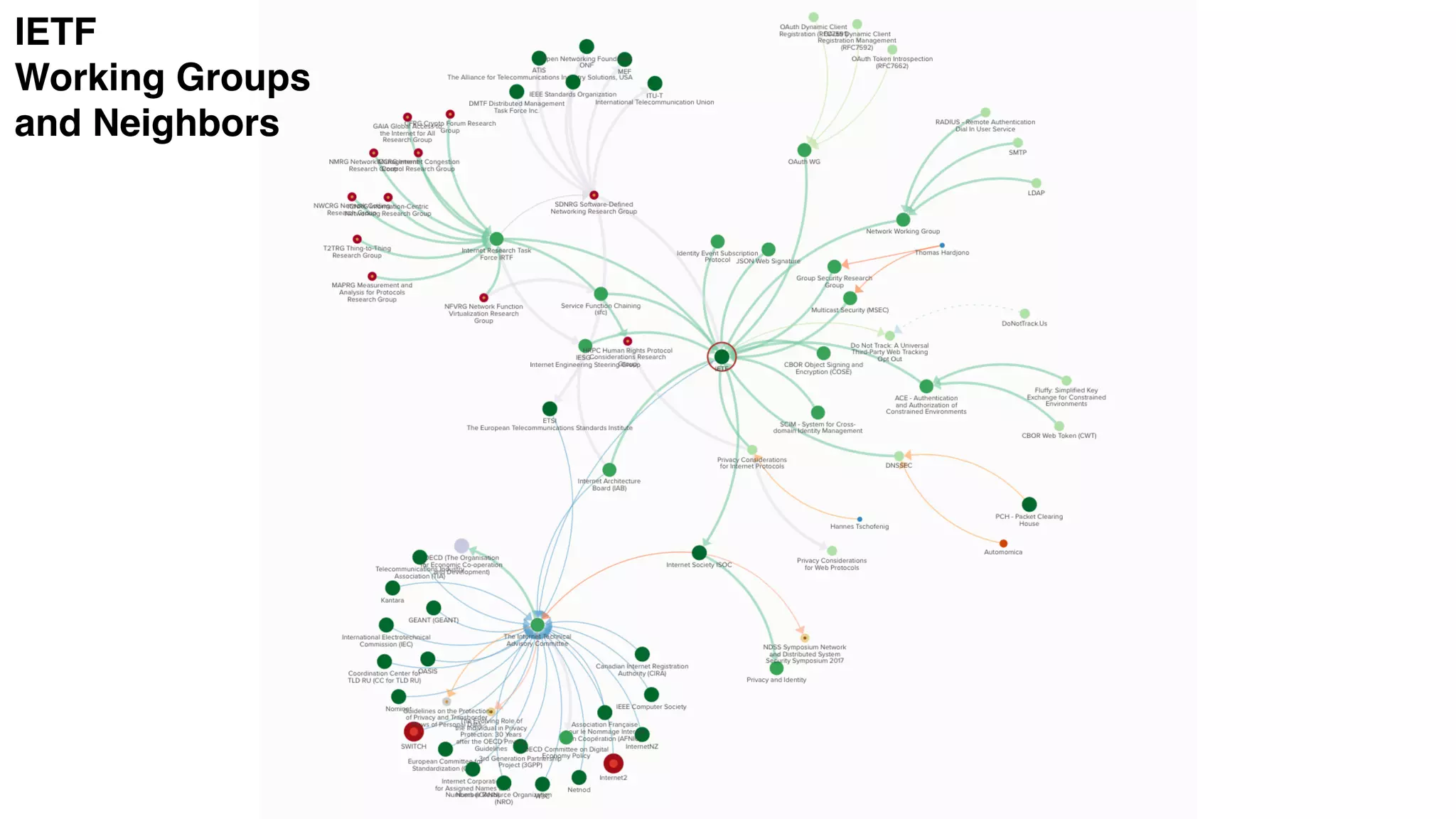
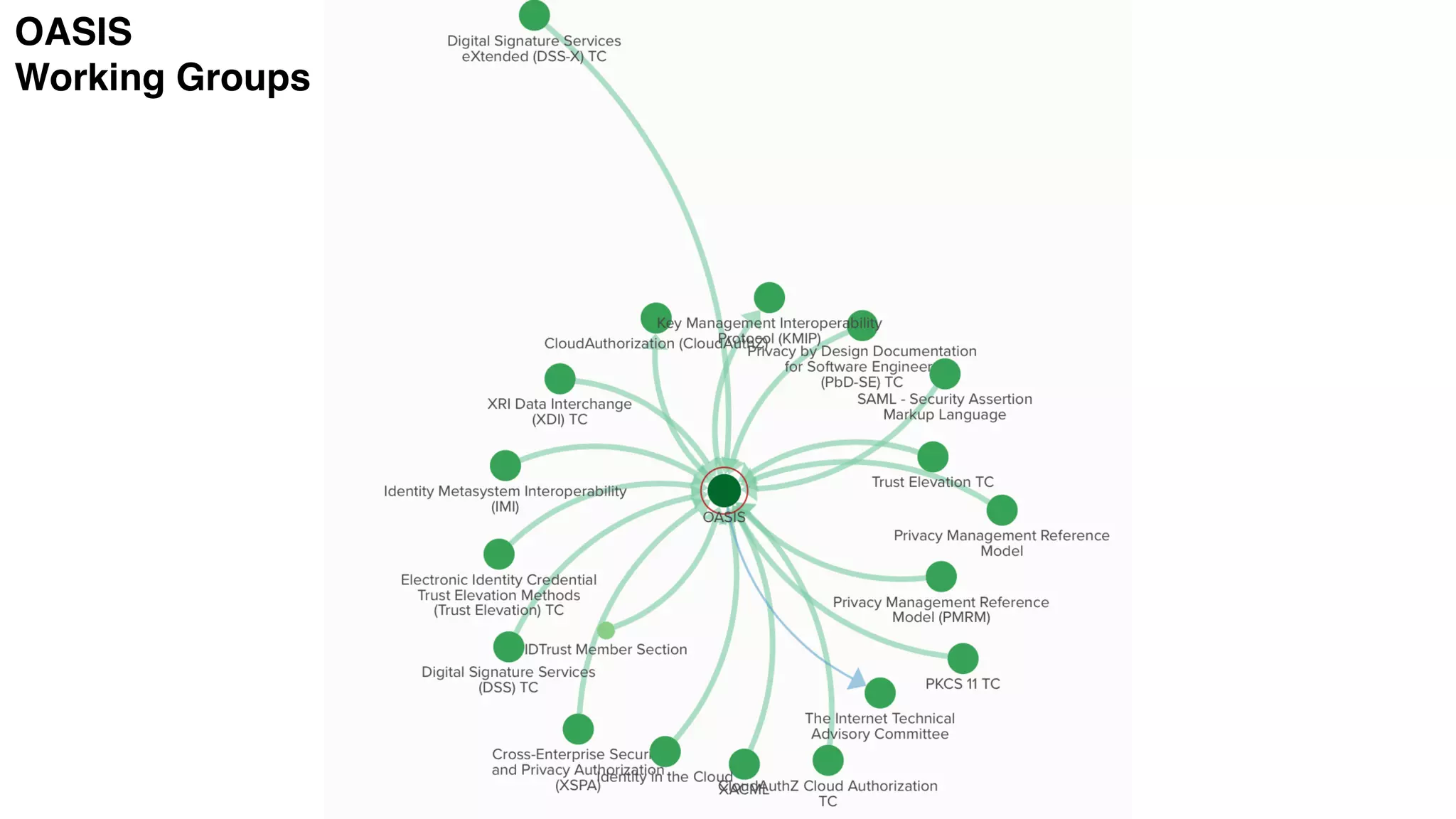
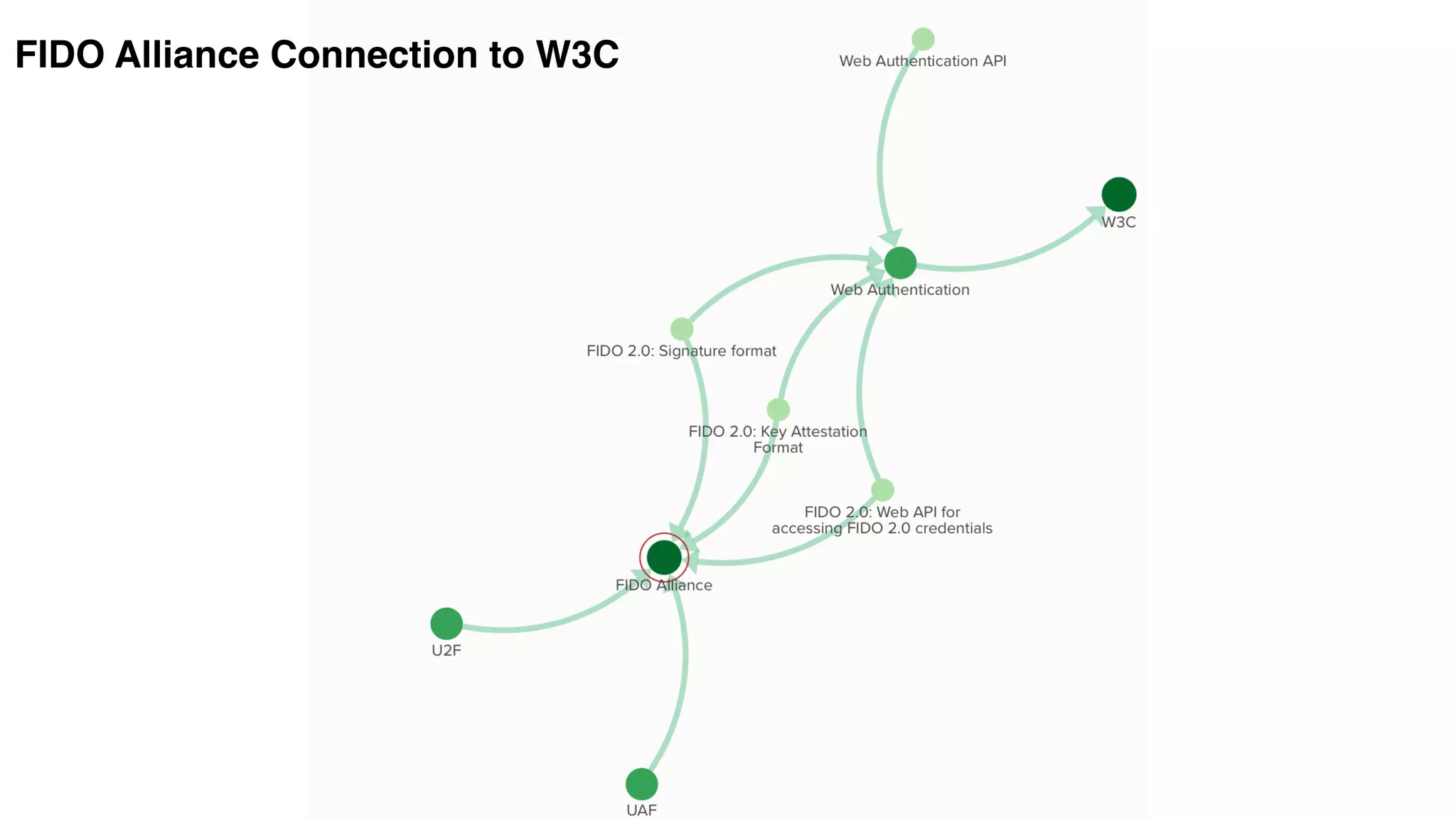
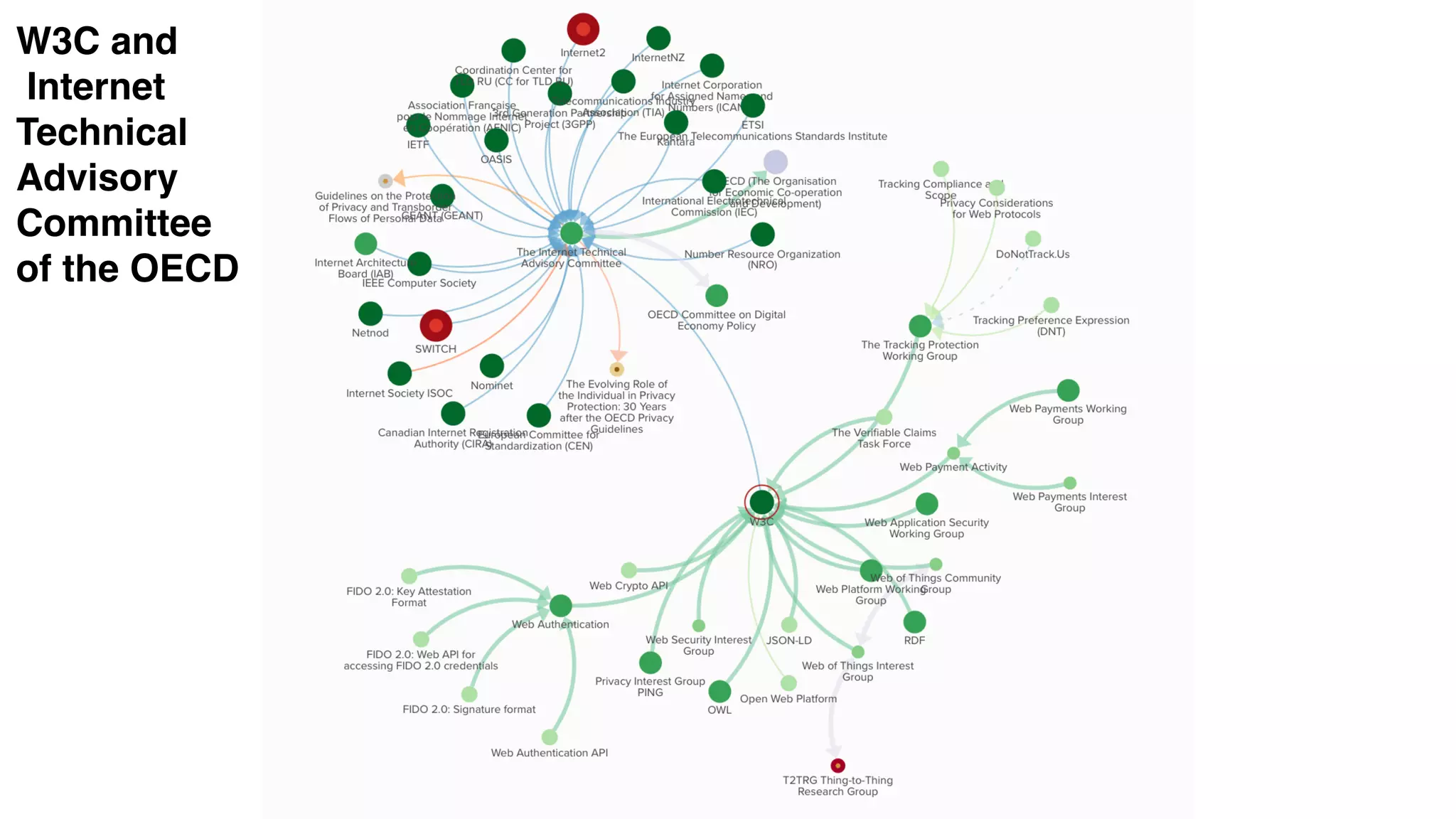
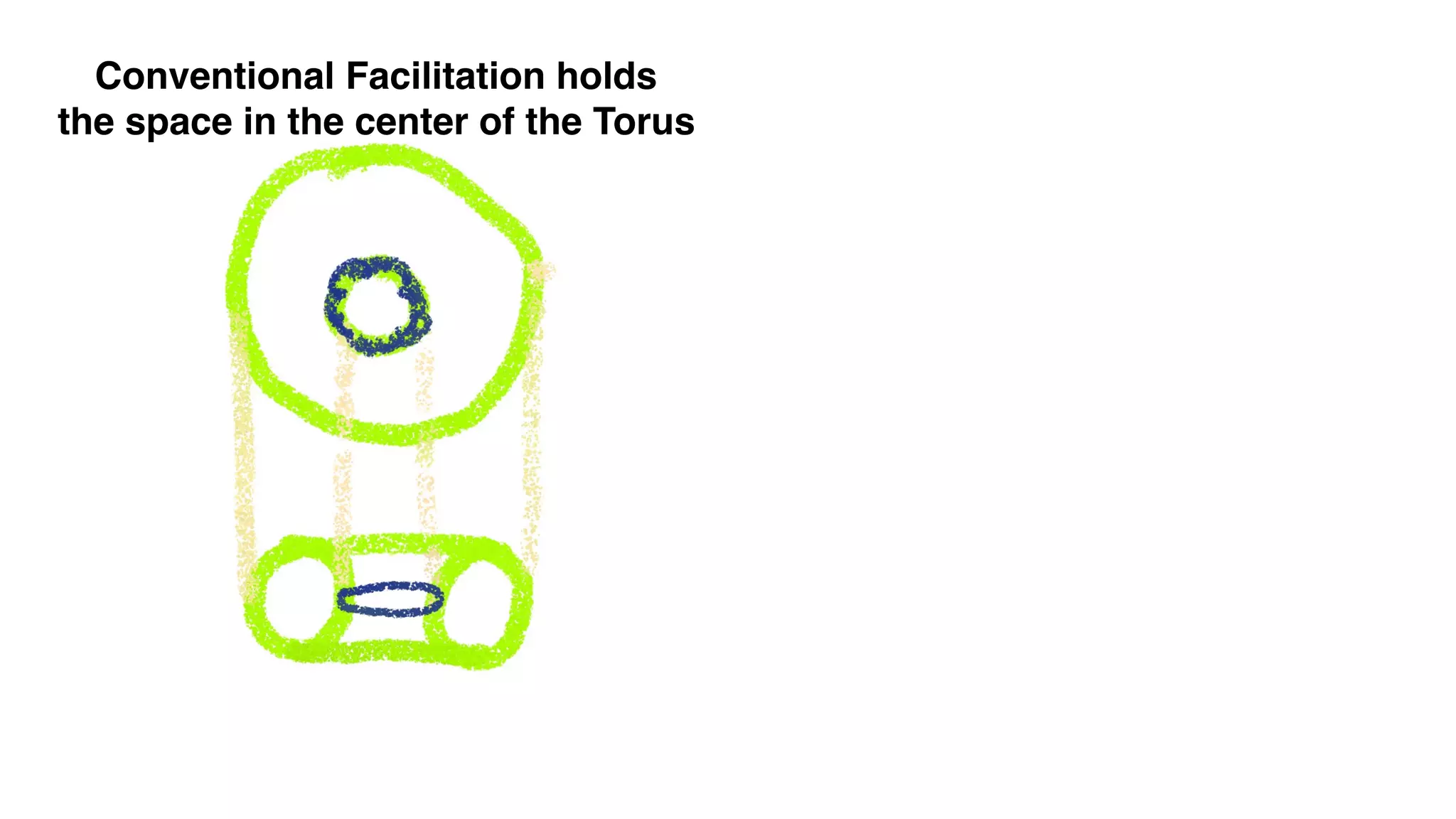
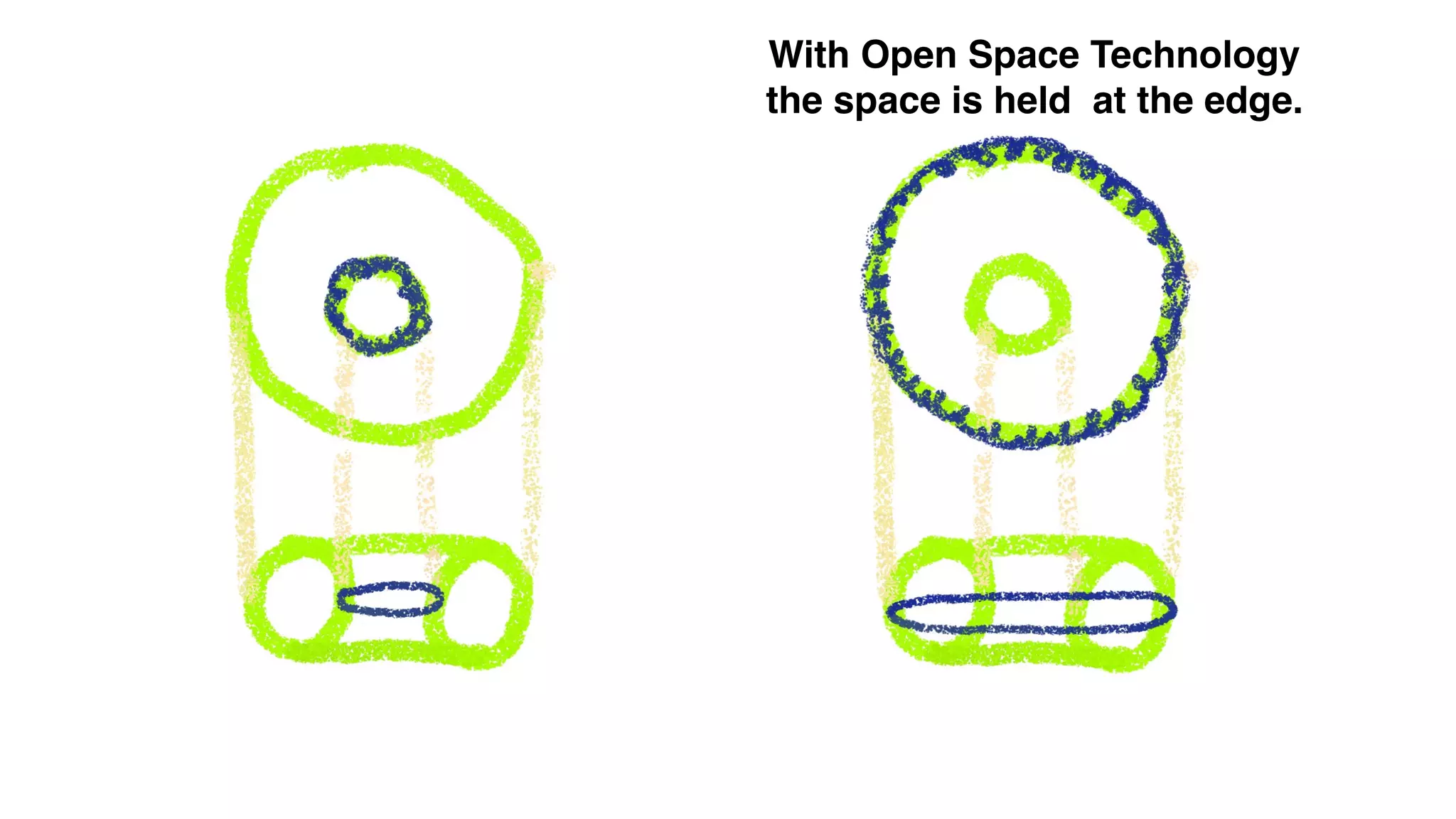
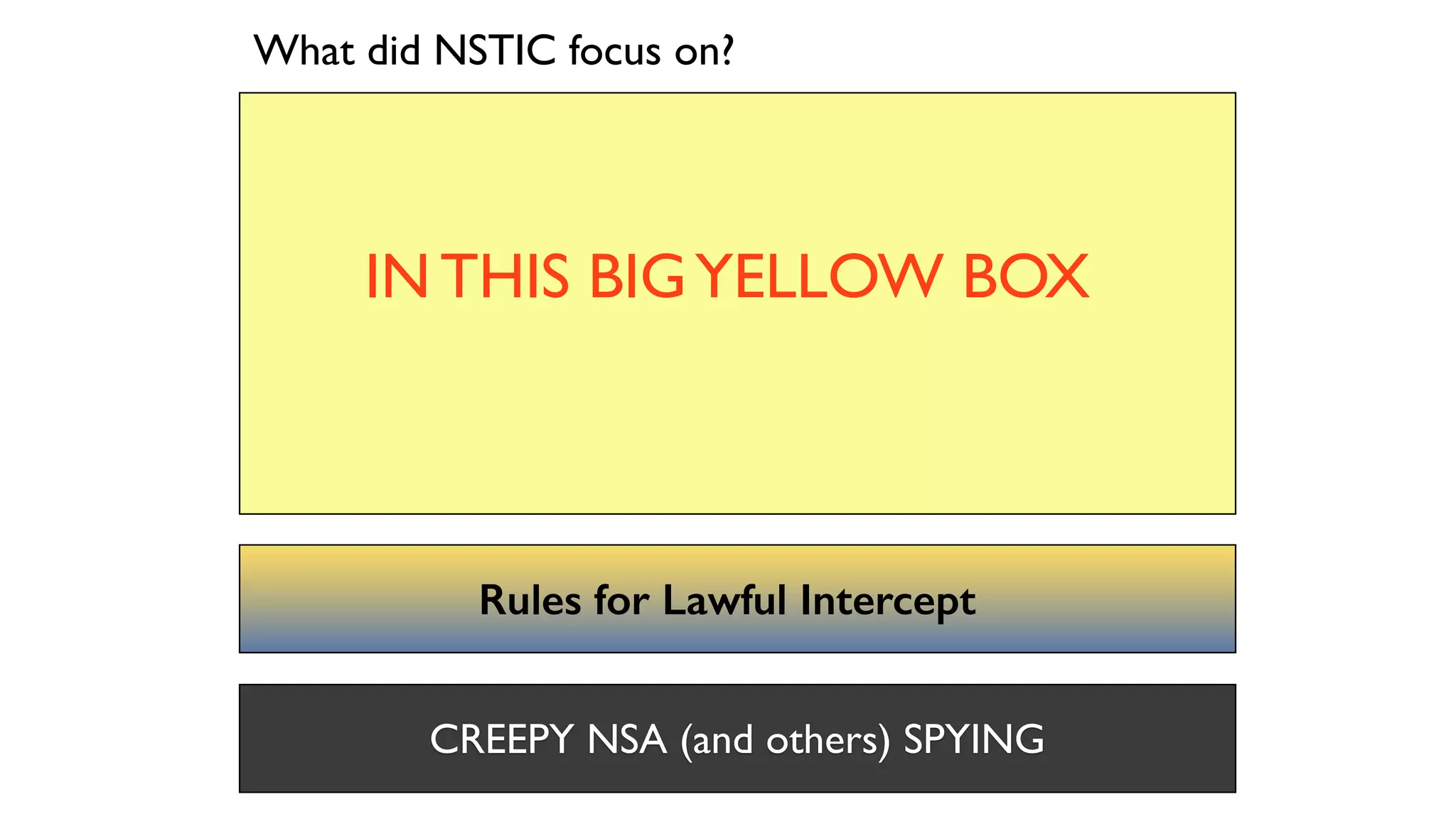
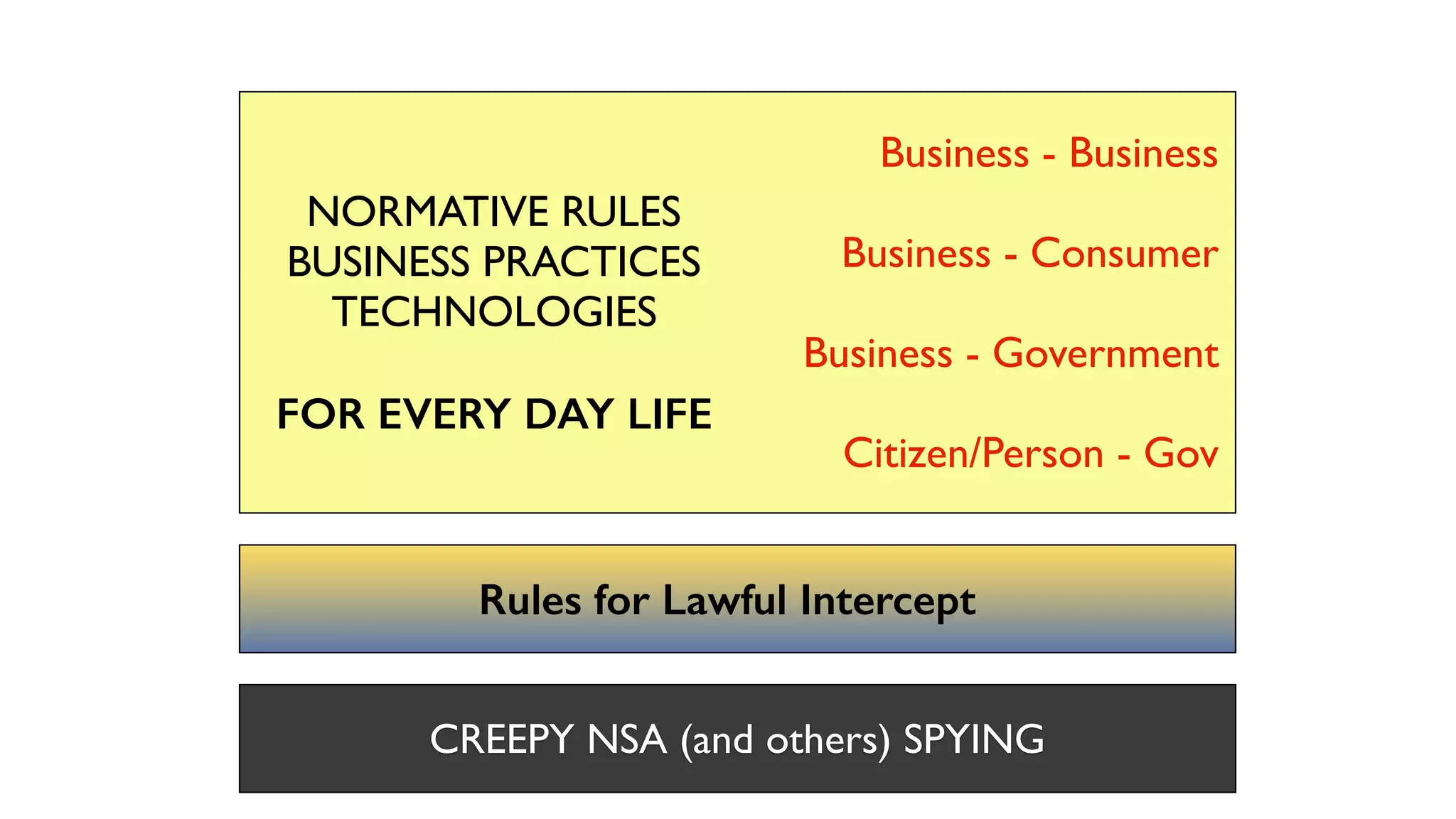
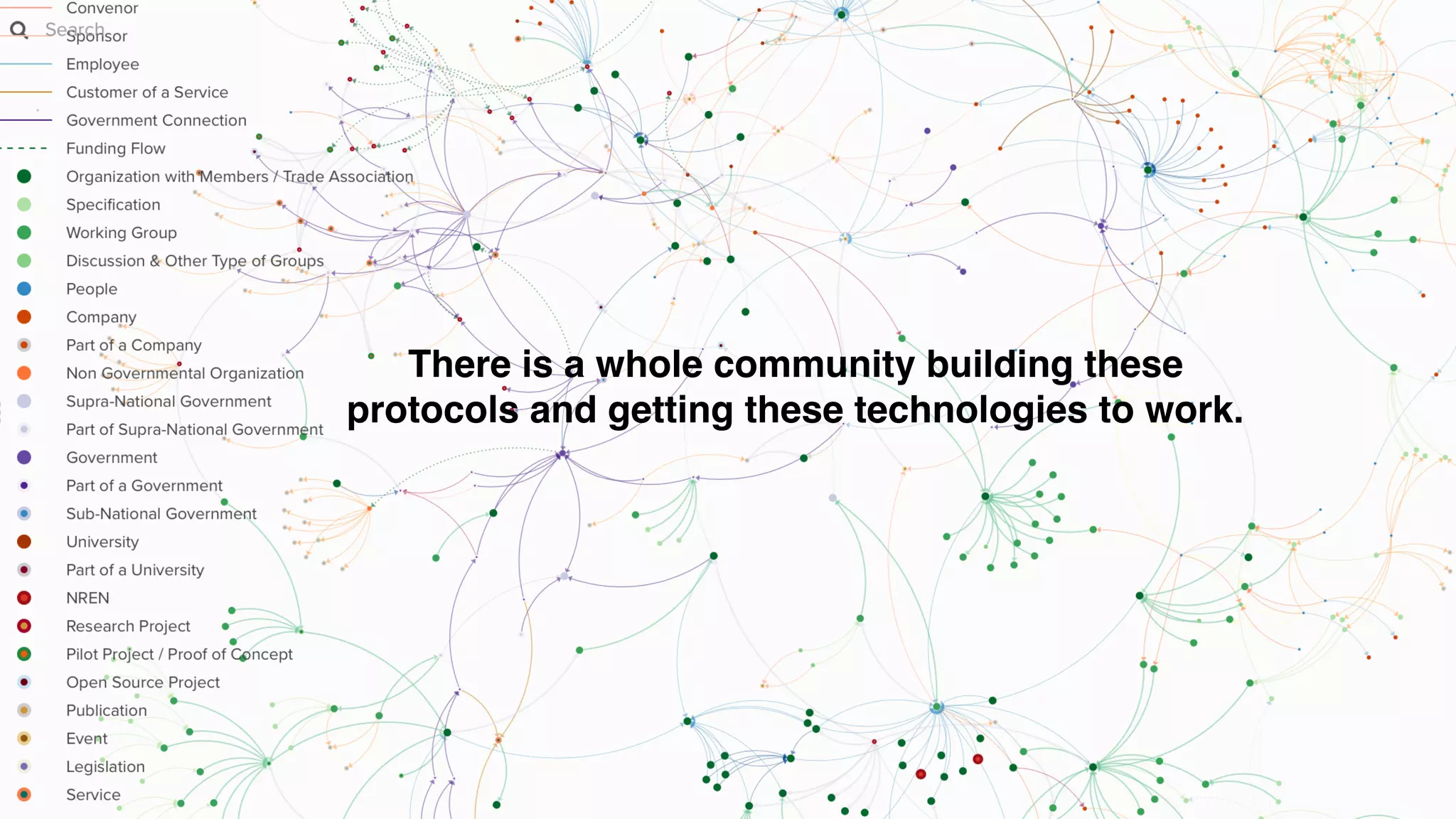
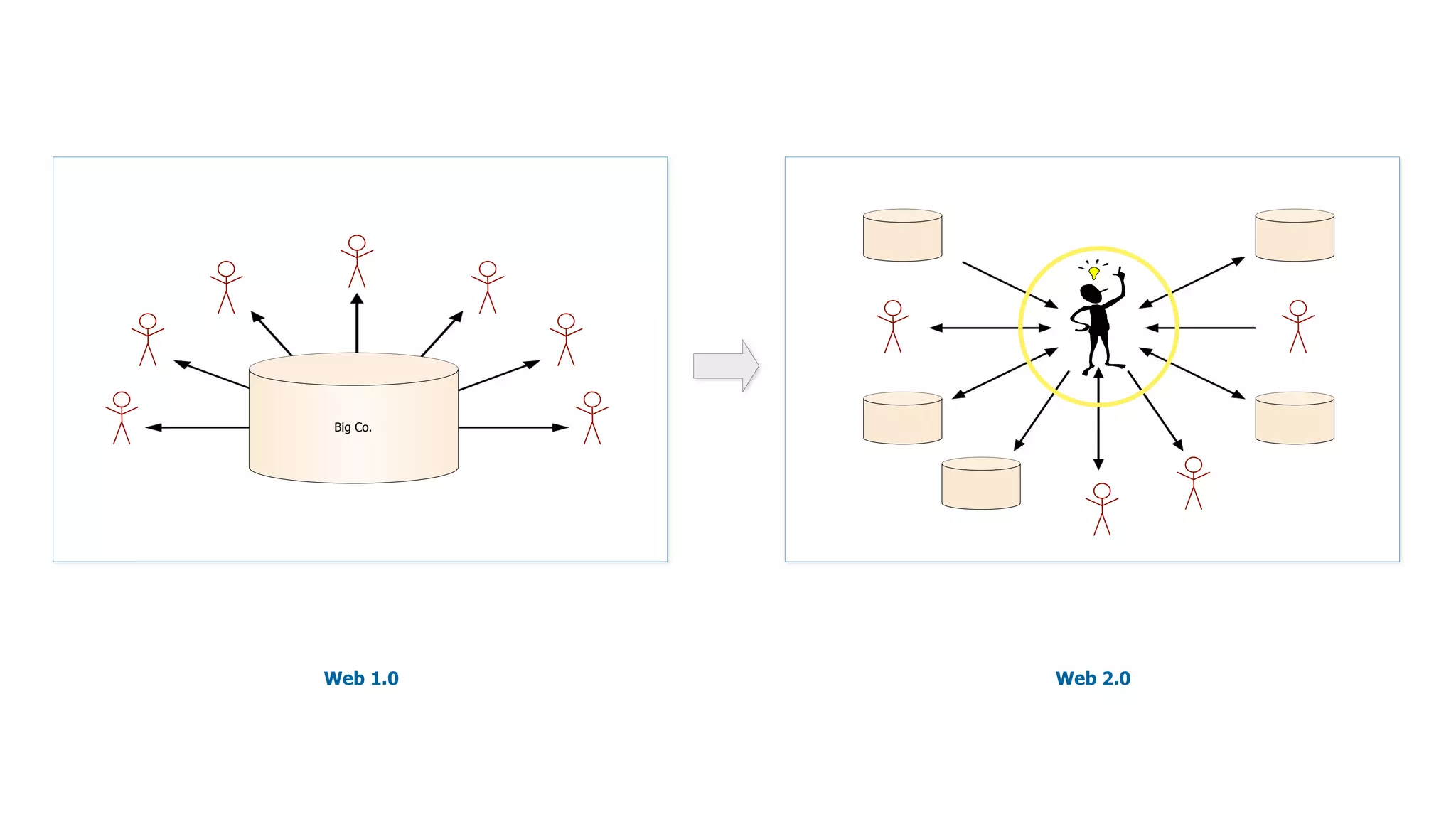
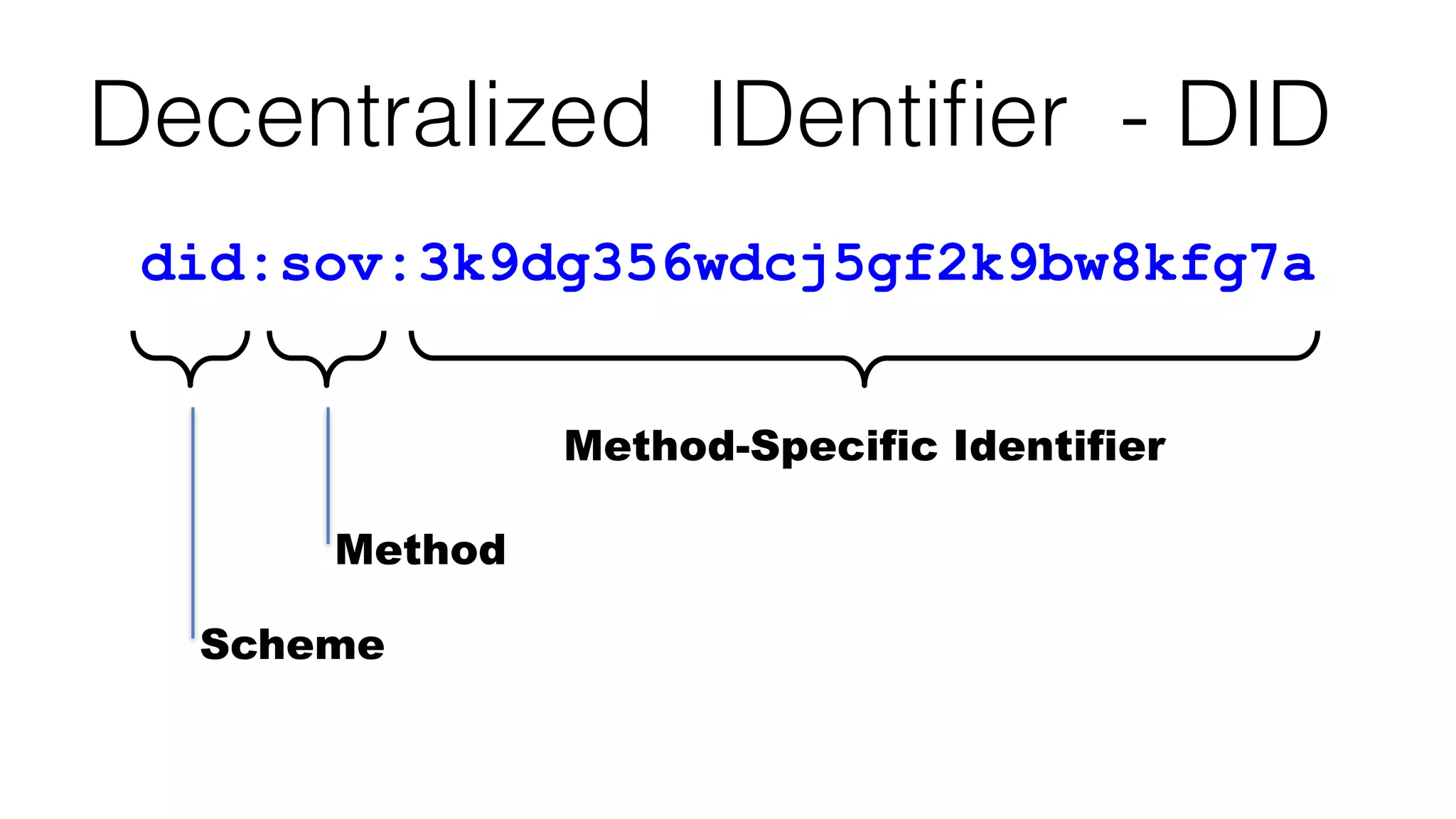
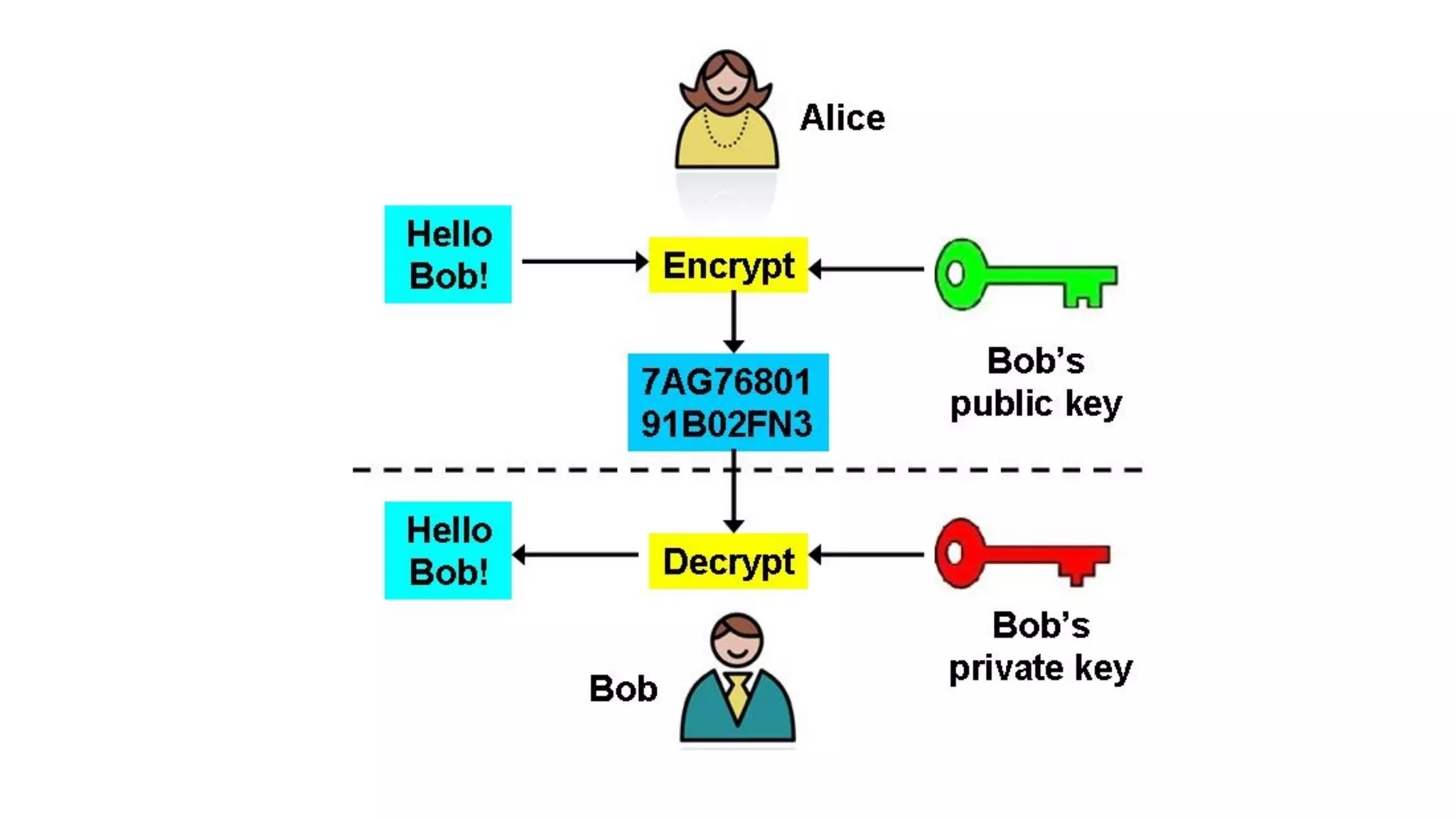
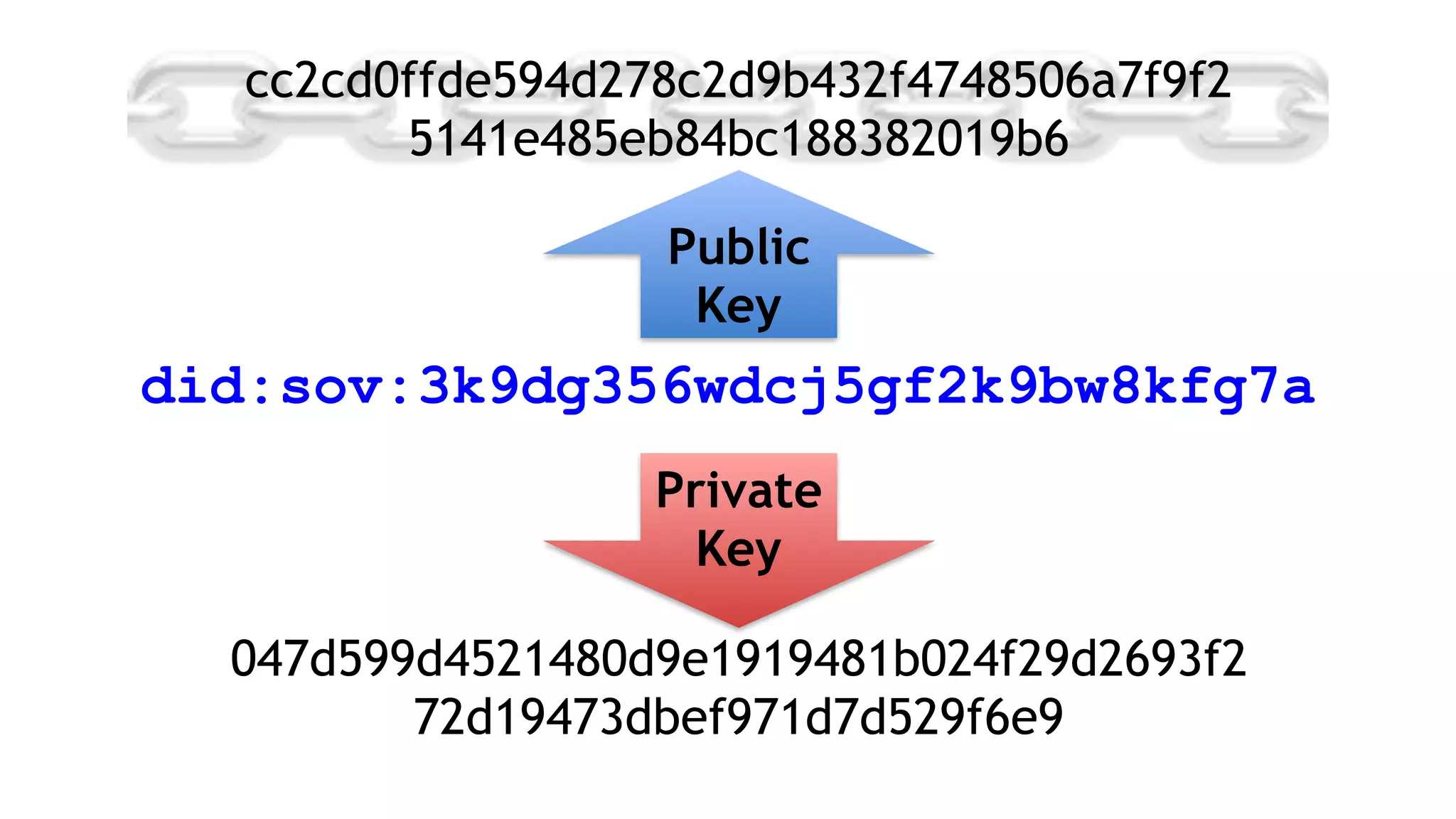
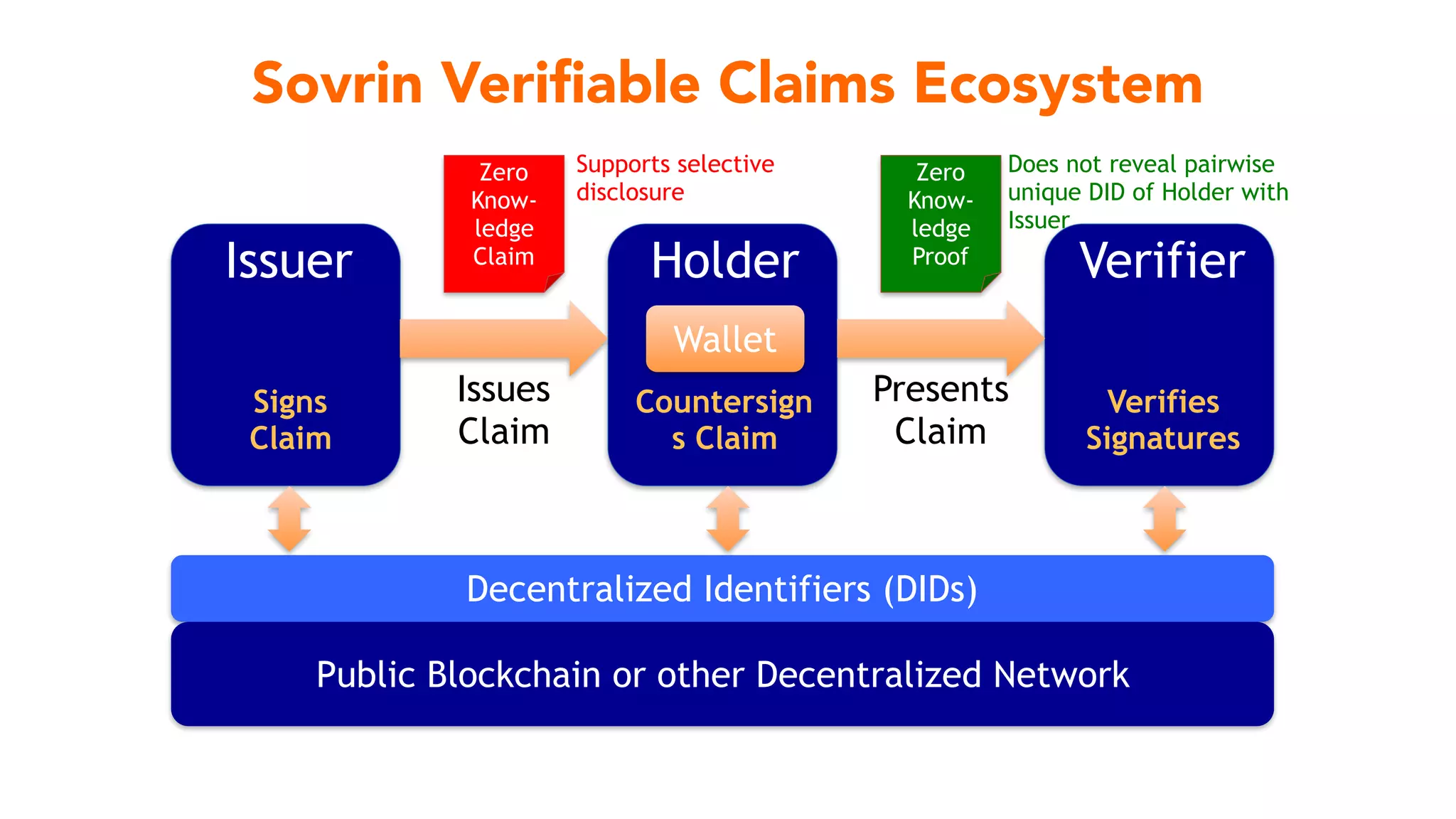
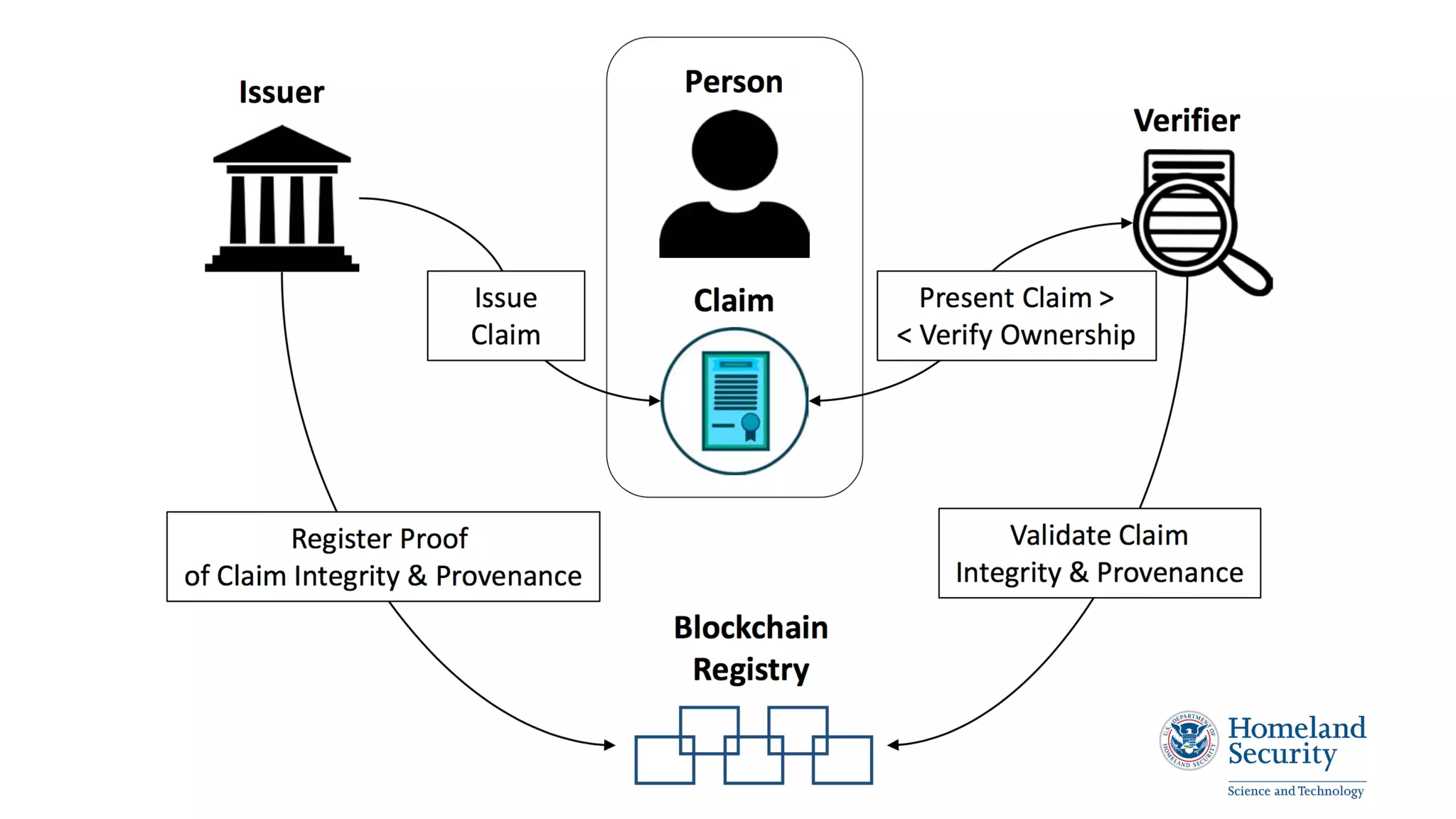
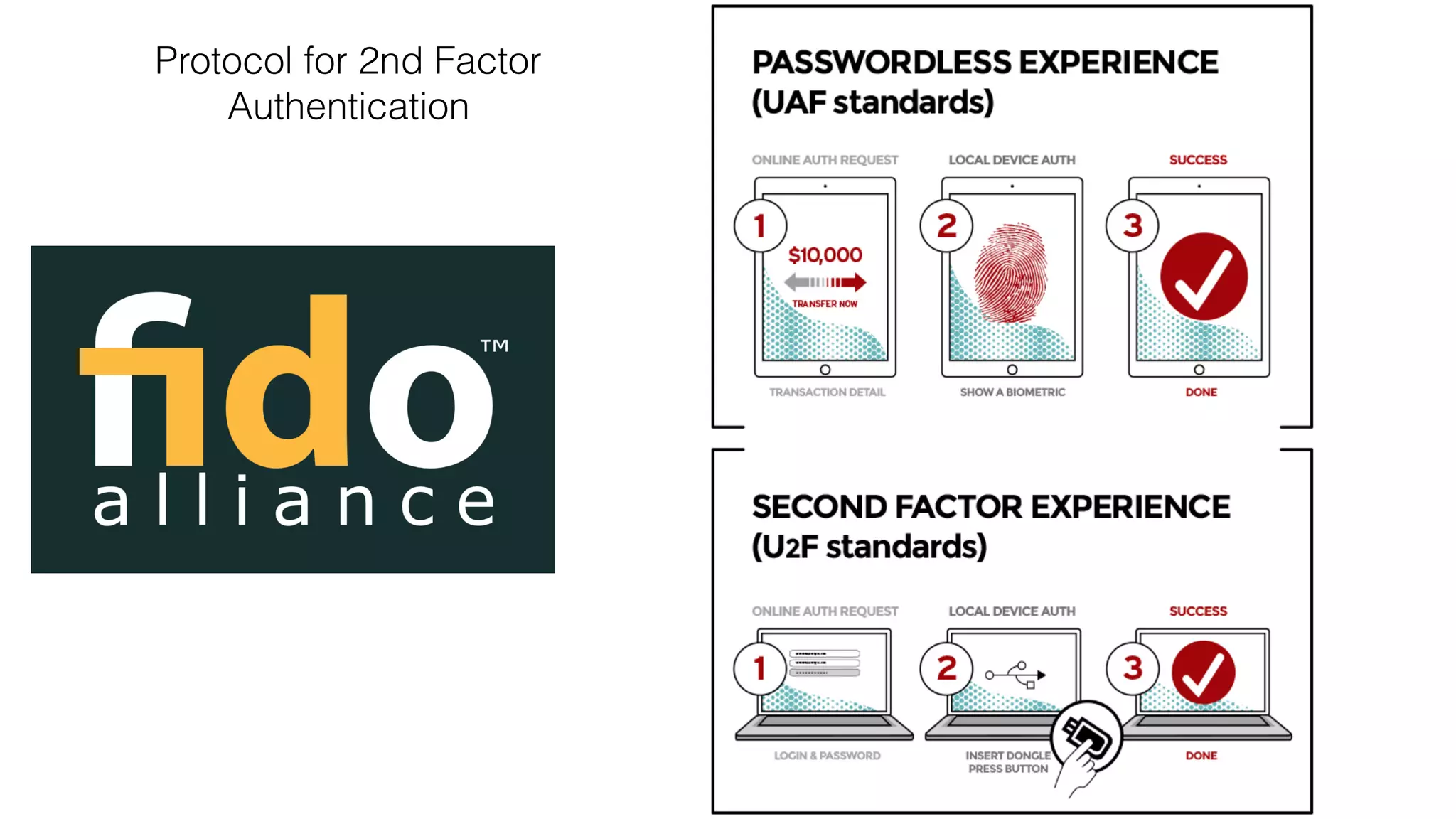
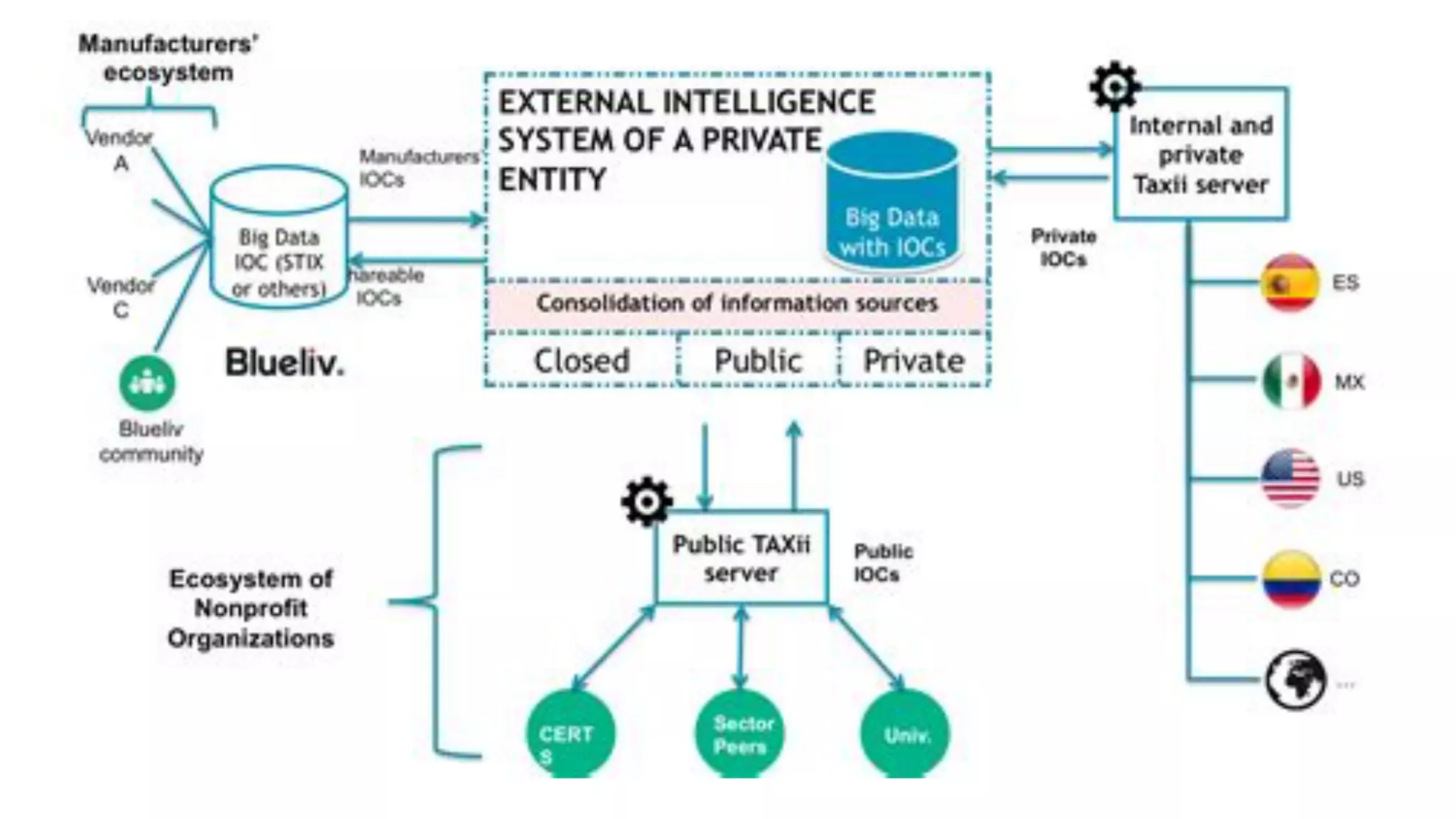
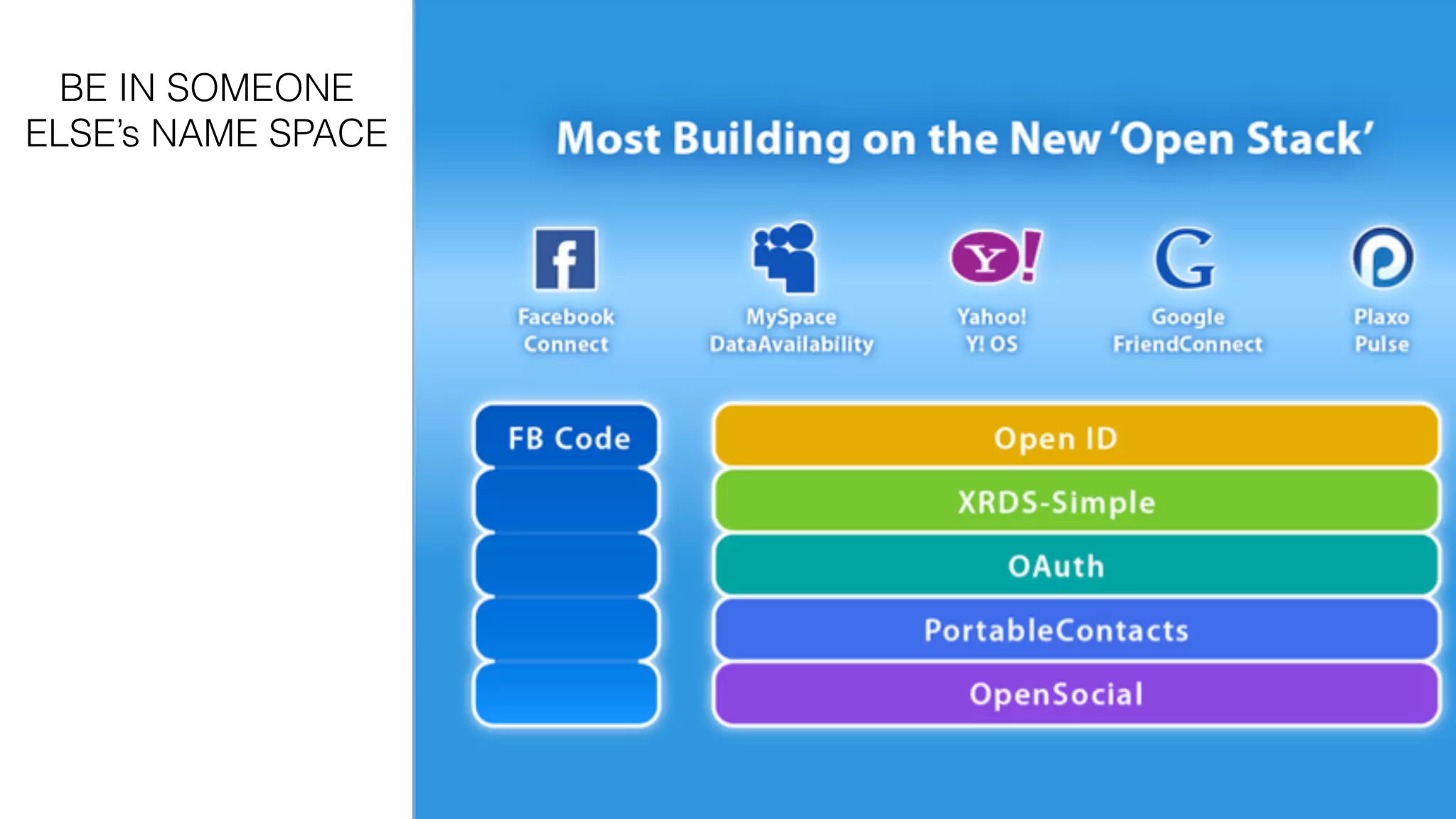
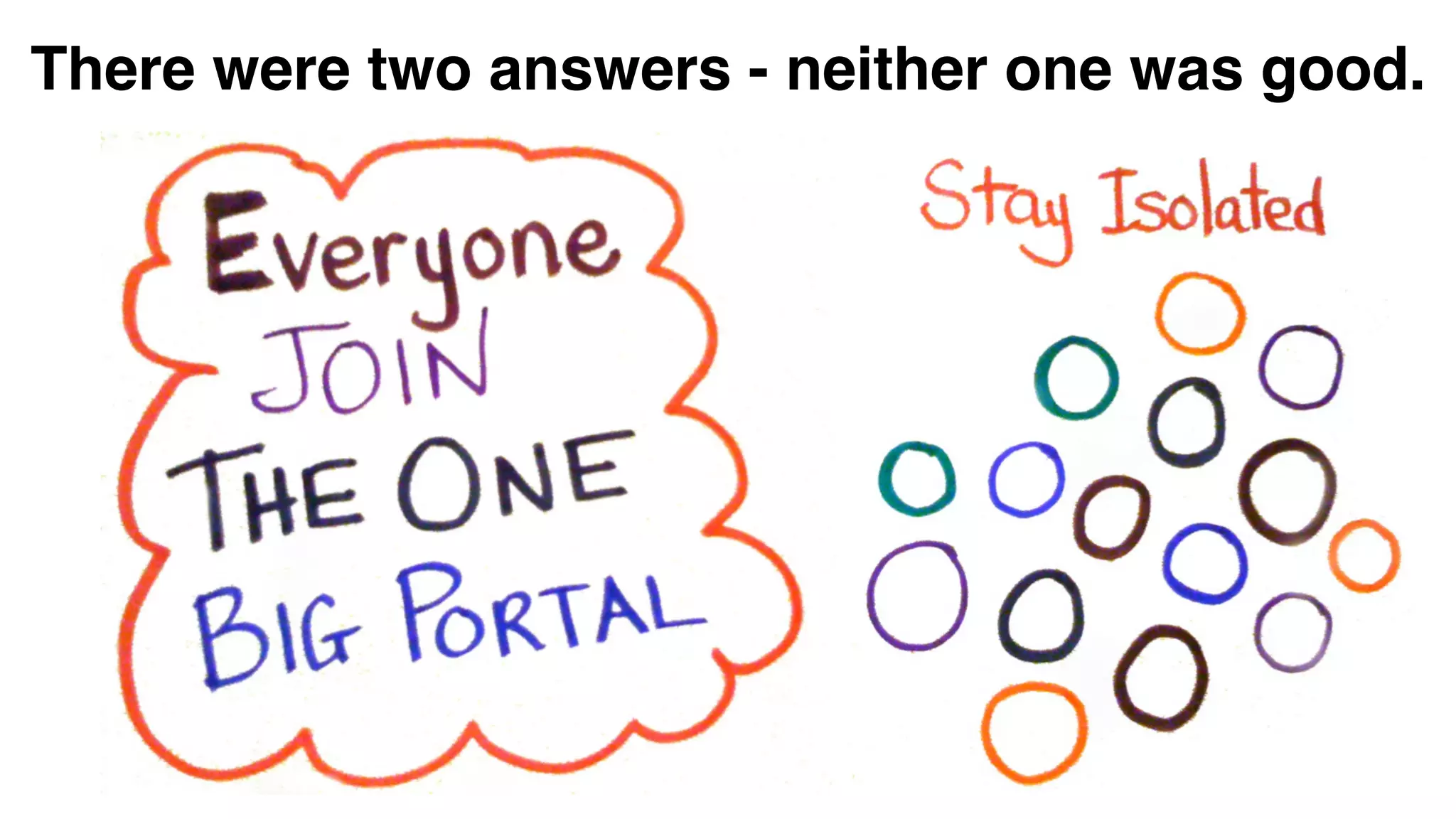
The document discusses the evolution of digital identity and the importance of control and trust in managing online identities. It highlights the concept of protocols as a means to achieve universalism and inter-operability in digital interactions while emphasizing the need for user-centric approaches in technology development. The text also advocates for inclusivity and the empowerment of marginalized communities in shaping future identity frameworks.

























![A digital profile is not treated [by corporations who host
them] as the formal extension of the person it represents.
But if this crucial data about you is not owned by you,
what right do you have to manage its use?
A civil society approach to persistent identity is a
cornerstone of the Augmented Social Network project.](https://image.slidesharecdn.com/whatisuniverse-modified-180523171401/75/My-Identiverse-The-Evolution-of-Digital-Identity-and-Openness-34-2048.jpg)