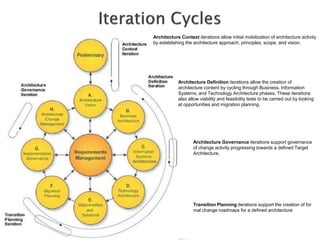
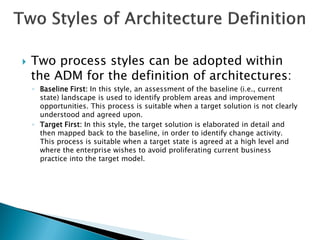
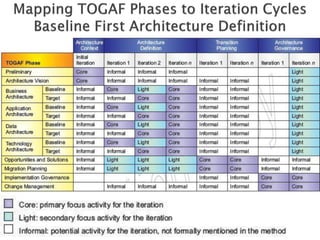
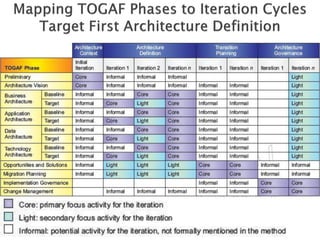
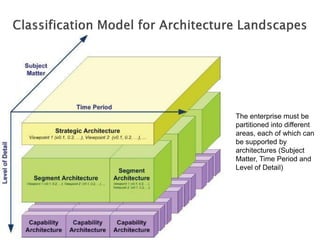
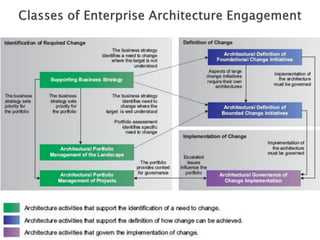
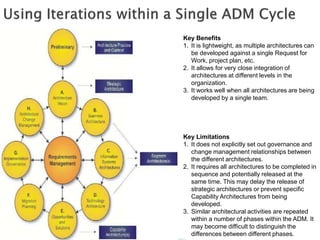
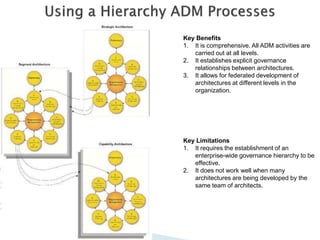
The document discusses different approaches to applying the Architecture Development Method (ADM) at various enterprise levels. It describes iterating the ADM cycle to establish architecture context, define architecture content through business, information systems, and technology architecture phases, and govern change progression towards the target architecture. Two definition styles are outlined: baseline first assesses current state to identify improvements when the target is unclear, while target first elaborates the target then maps back to identify changes when the target is agreed at a high level. The enterprise must be partitioned into areas served by different architectures. Applying the ADM across multiple levels provides comprehensive coverage but requires extensive governance, while applying it within a single level is more lightweight but risks delays and inefficient repetition between phases.