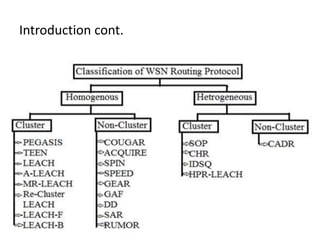
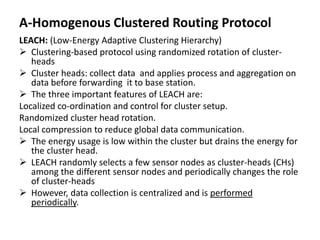
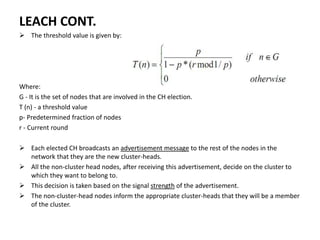
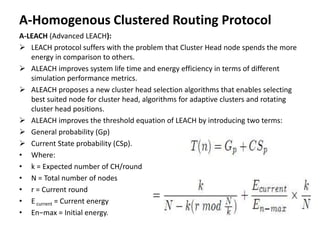
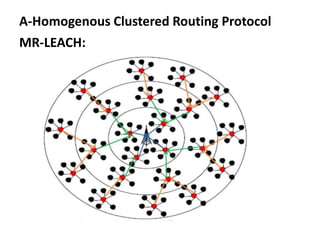
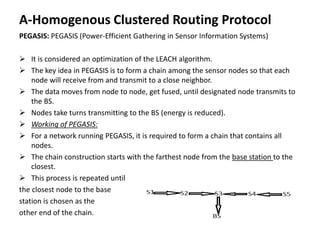
This document summarizes and classifies various routing protocols for wireless sensor networks (WSN). It discusses protocols that are homogenous (all nodes are identical) and heterogeneous (nodes differ). It focuses on clustered protocols where nodes are grouped into clusters to aggregate and transmit data. Specific clustered protocols covered include LEACH (Low-Energy Adaptive Clustering Hierarchy), ALEACH, MR-LEACH, PEGASIS, TEEN, and Re-Cluster LEACH. Each protocol is summarized with its key features and advantages/disadvantages.