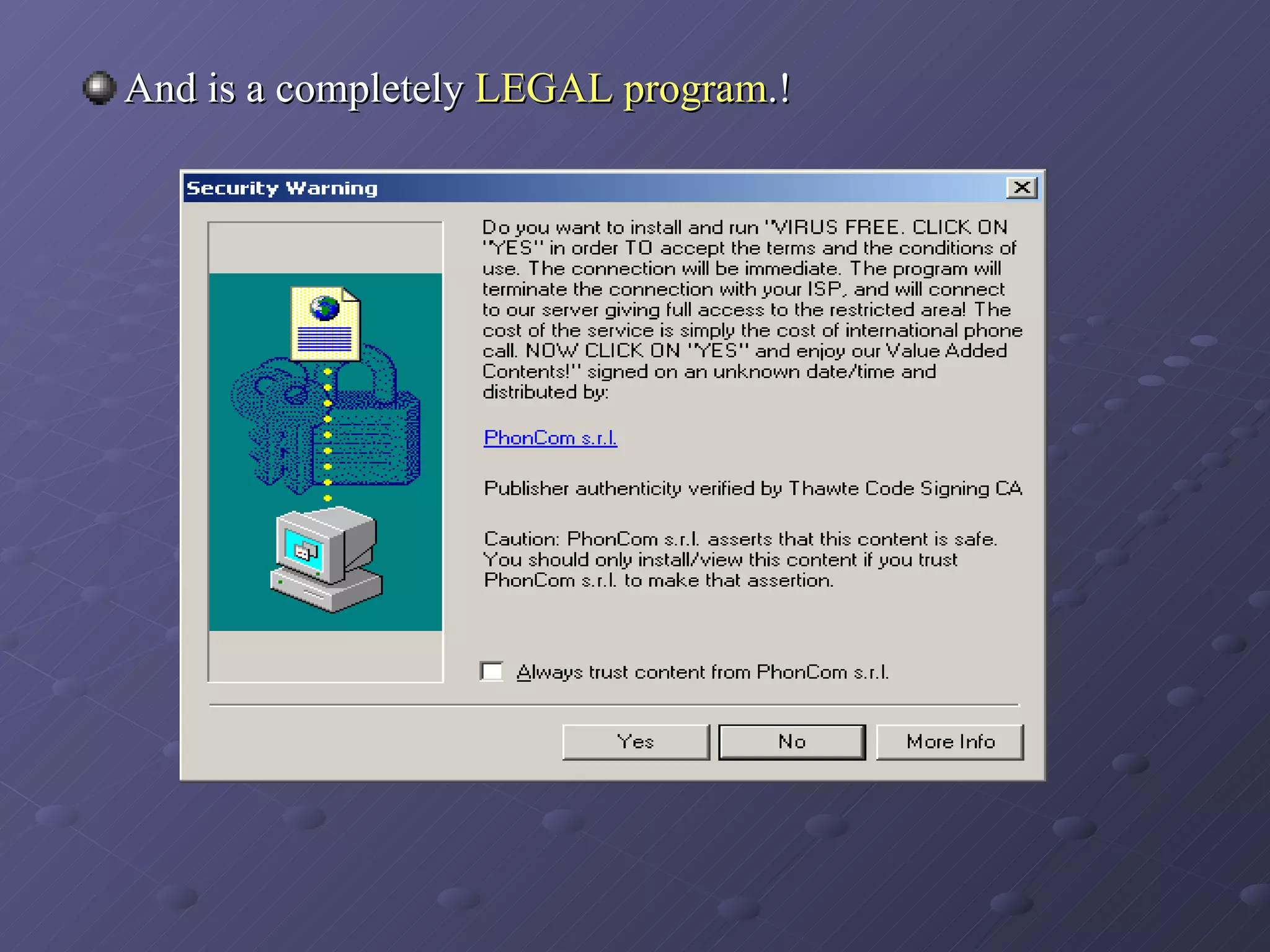
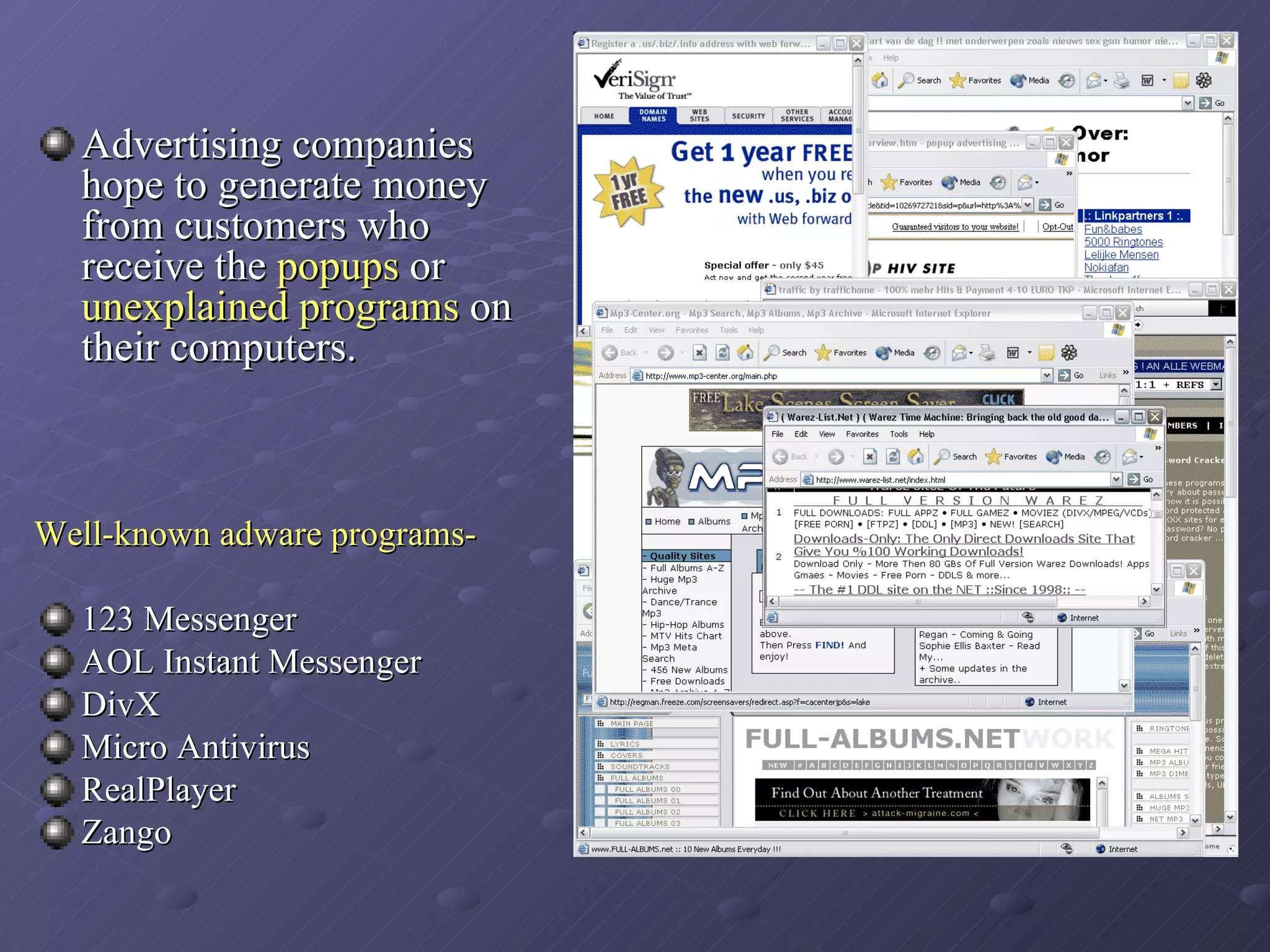
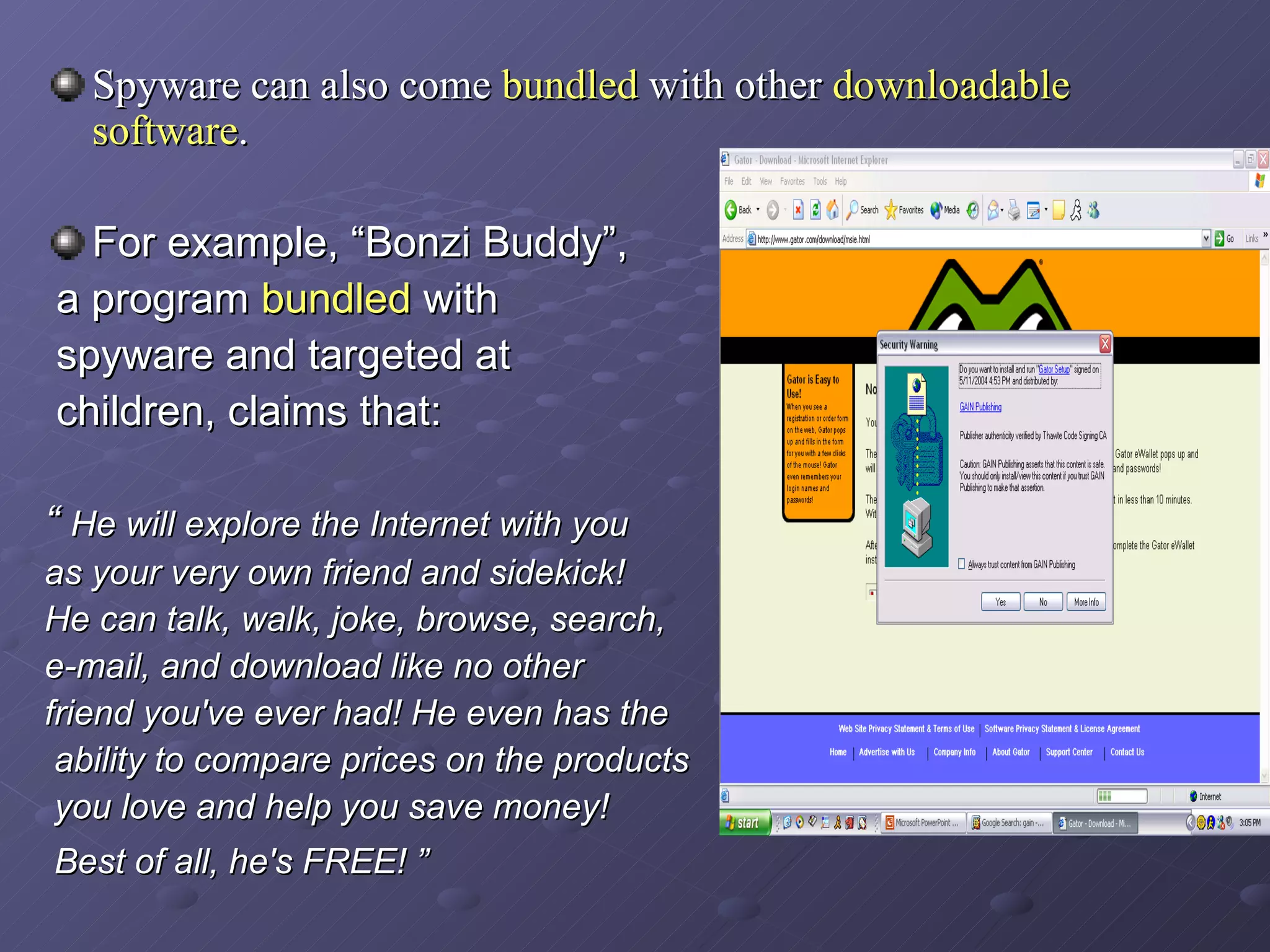
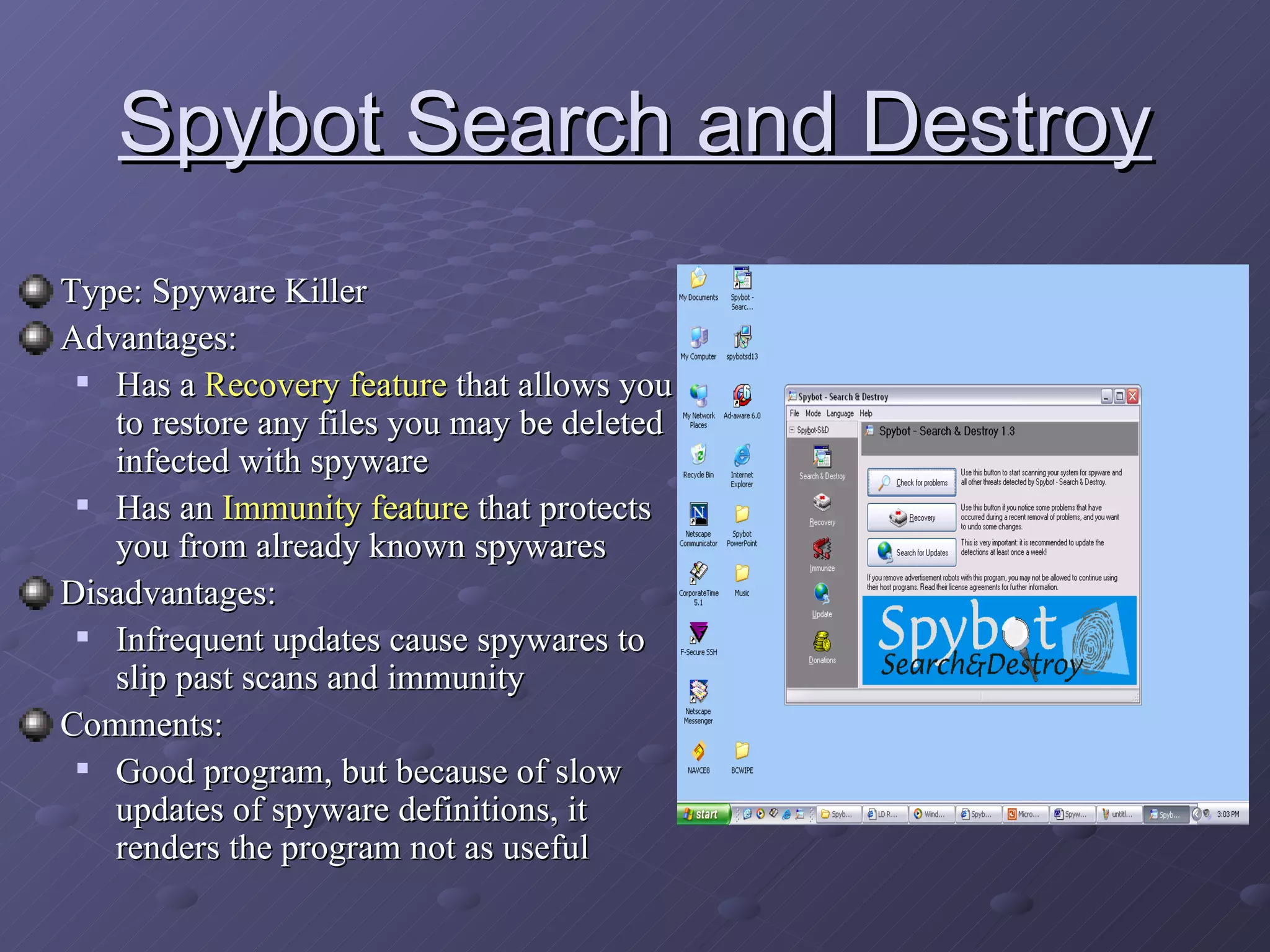
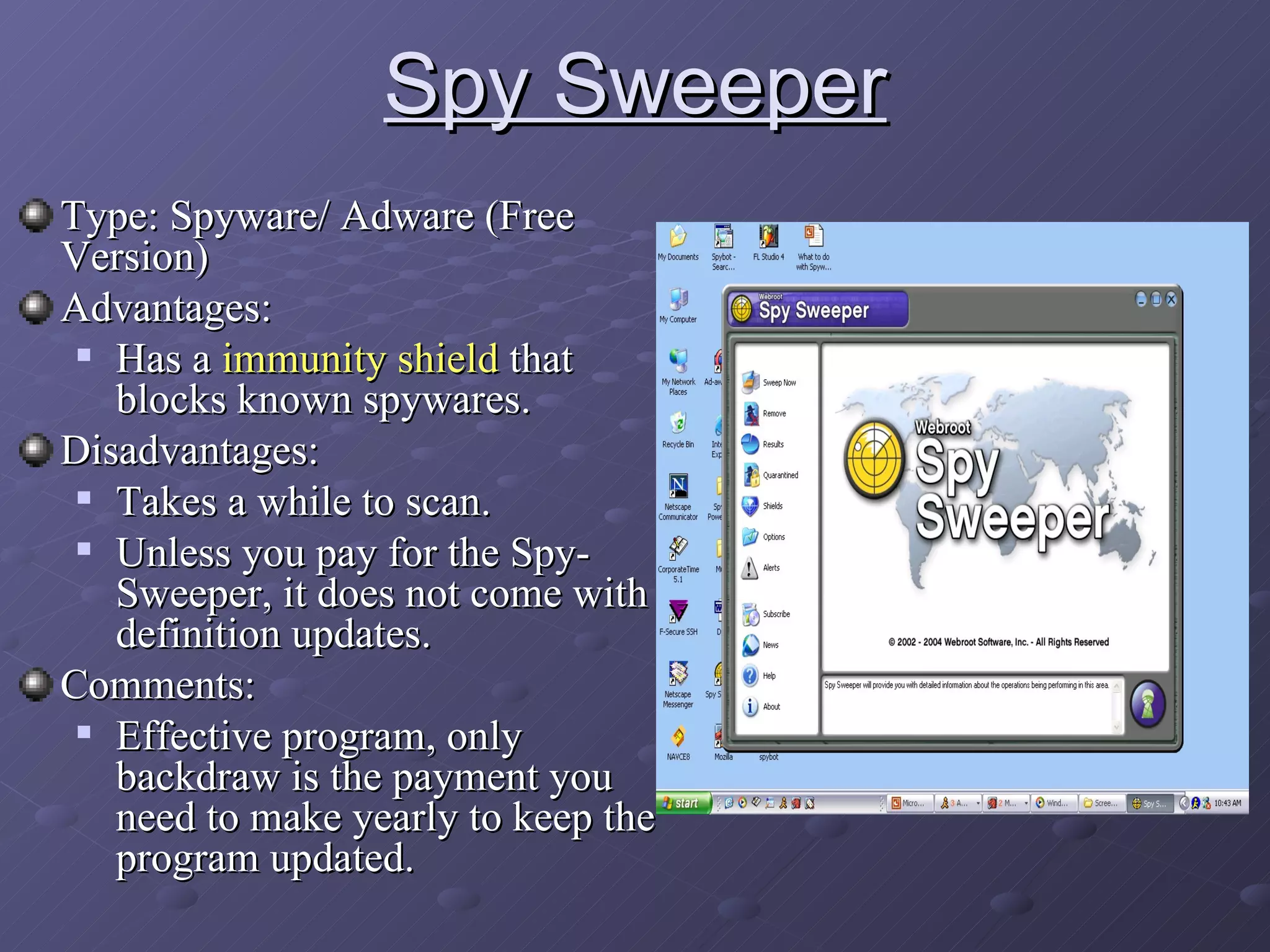
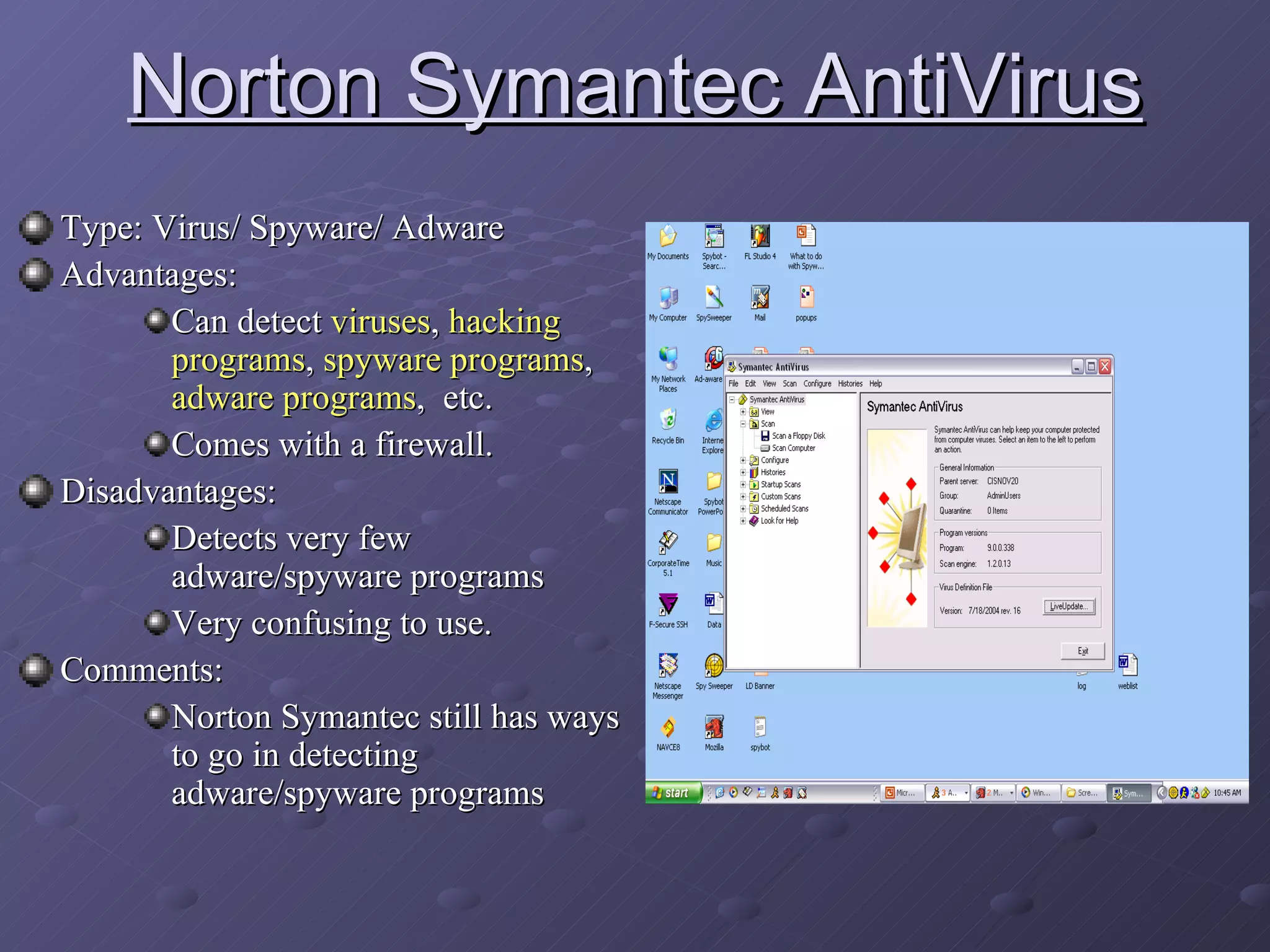
Spyware and adware are types of software that can be installed secretly on a computer to collect personal information or display advertisements. Spyware tracks users' browsing habits and other computer activities, while adware automatically displays ads. Both can slow computers and redirect browsers. Common symptoms of spyware/adware infections include frequent popups and a changed homepage. Programs like Ad-Aware, Spybot Search & Destroy, and Spy Sweeper can help detect and remove these programs. Users should avoid unnecessary downloads and popups to prevent infections.