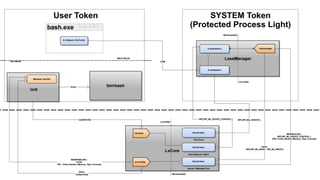
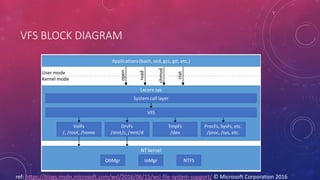
The document discusses the architectural overview of the Linux kernel hidden inside Windows 10. It describes the components that enable running Linux processes as "Pico processes" inside Windows, including the LXCORE kernel driver that implements the Linux ABI and API, and the LXSSMANAGER user-mode service that provides the external interface. The document outlines the initialization and functionality of these components, such as how they implement system calls, virtual file systems, and inter-process communication between Linux and Windows processes.