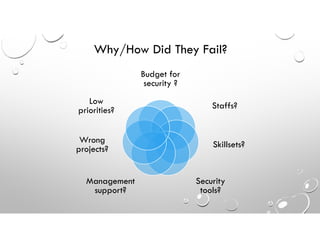
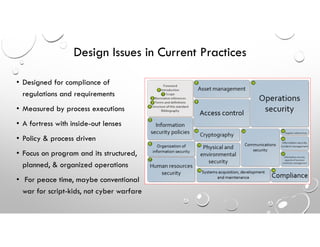
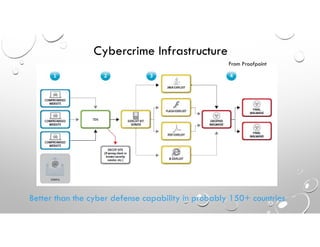
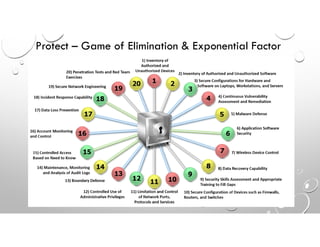
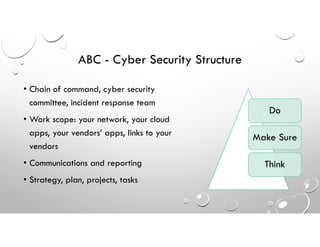
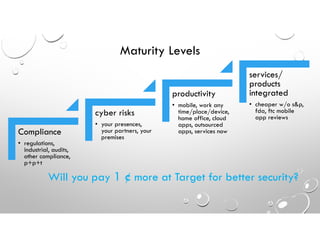
This document discusses why enterprise security often fails against cyber threats and provides recommendations. It summarizes that the traditional enterprise security model was designed for compliance rather than addressing modern cyber warfare tactics, resulting in vulnerabilities. The document recommends adopting the Cybersecurity Framework to better identify all IT assets, protect against threats through elimination techniques, and improve detection abilities. It also stresses the importance of response and recovery plans as well as measuring security effectiveness through readiness, capability, and quick response times.