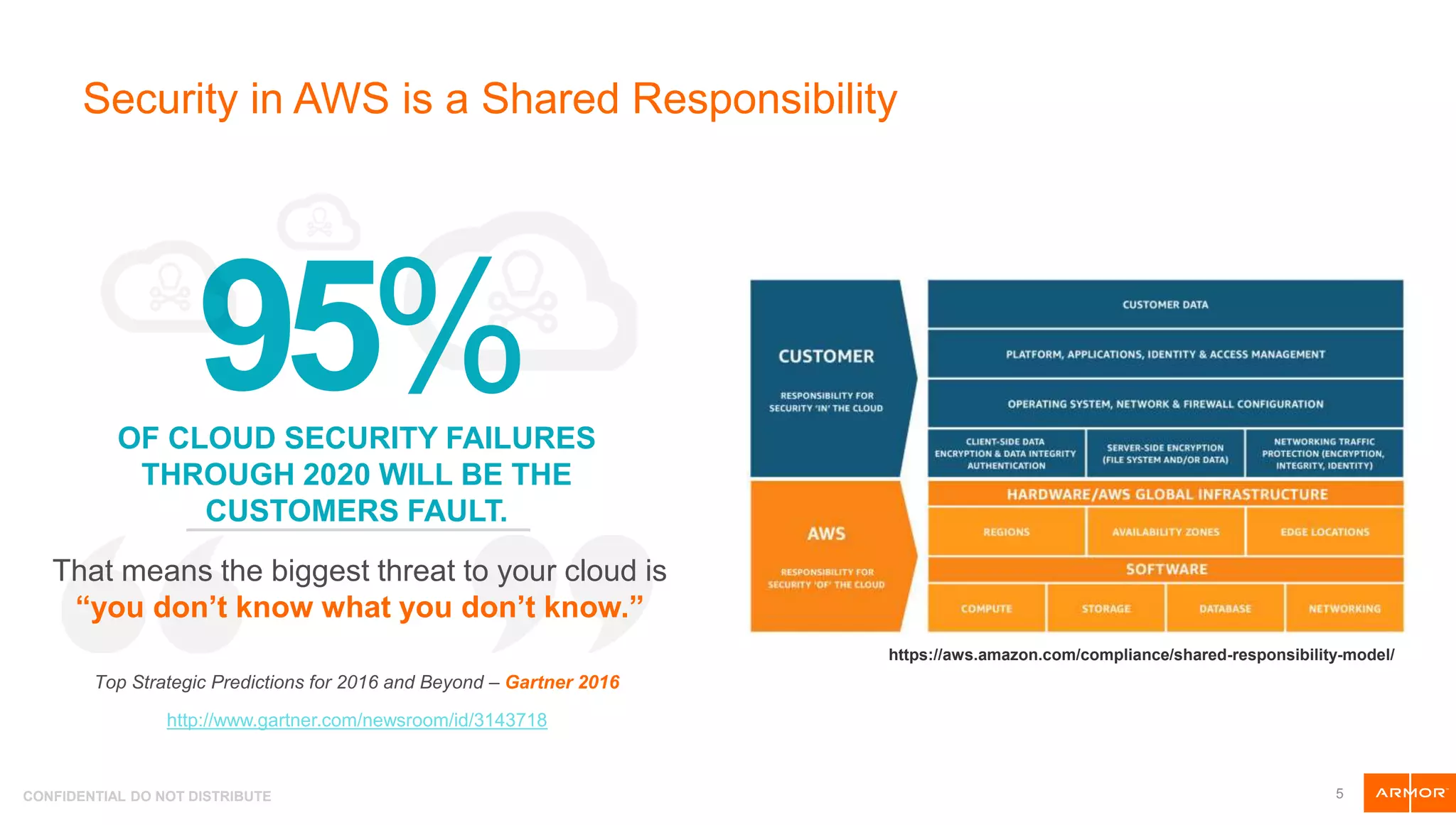
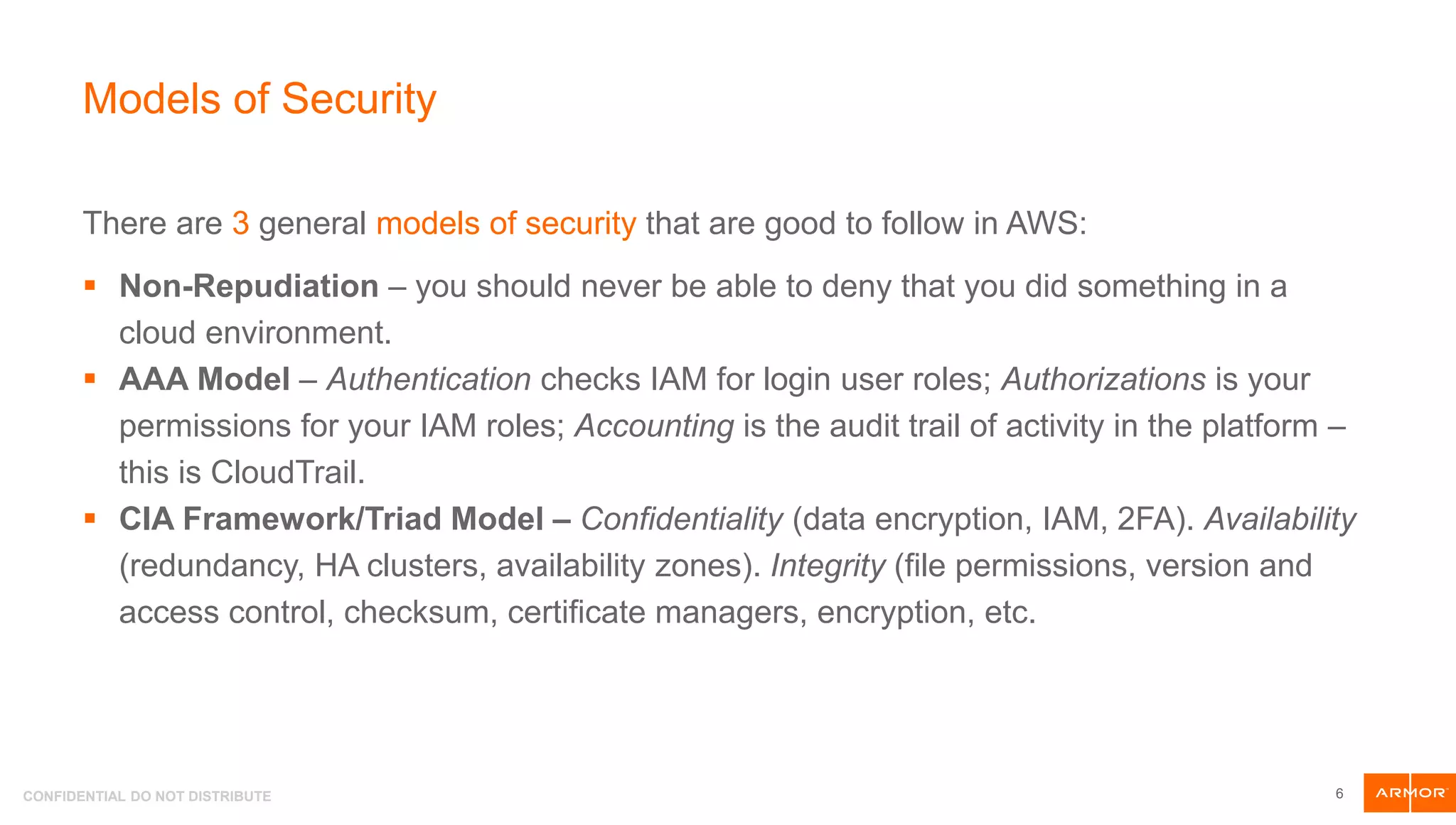
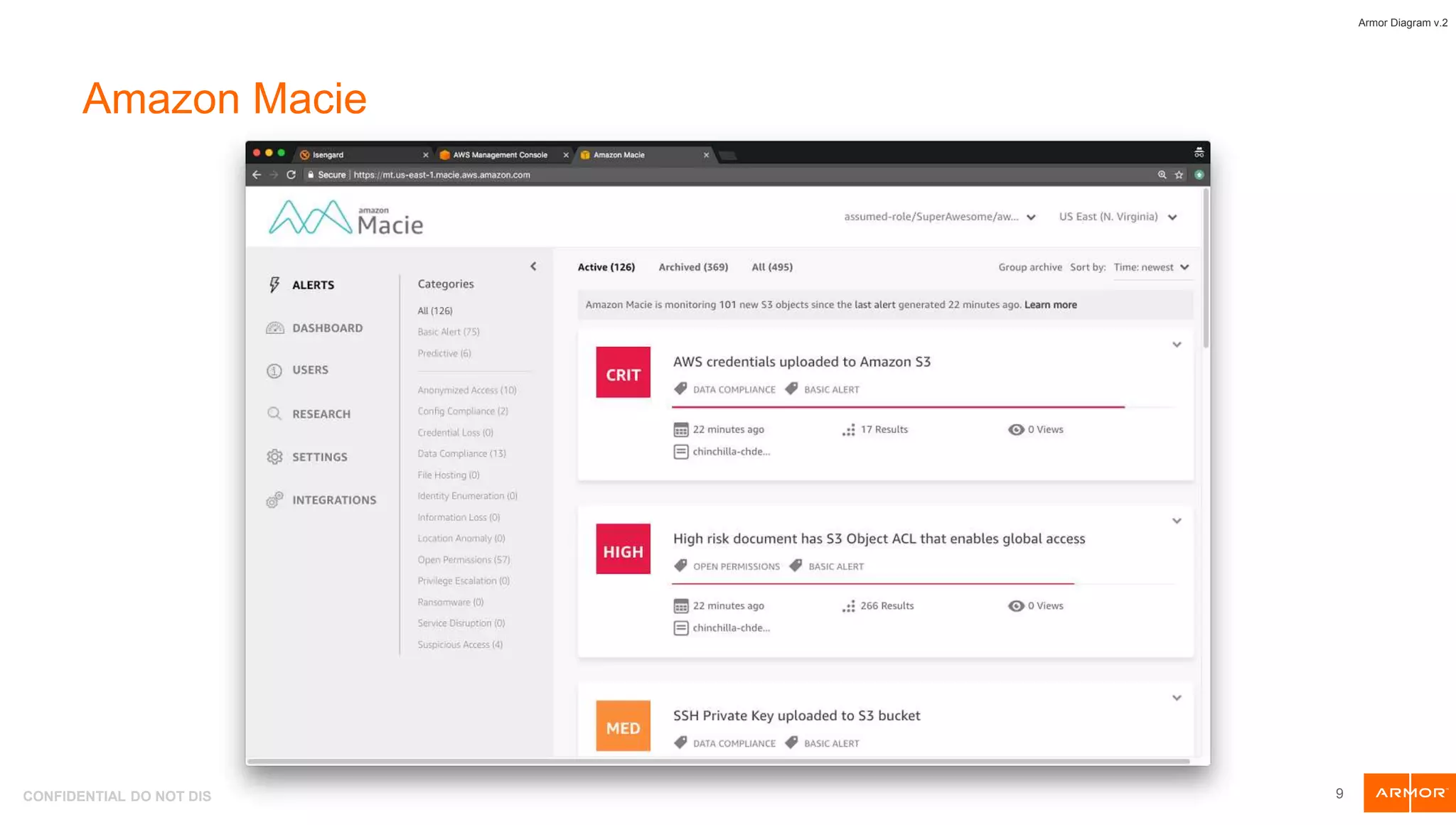
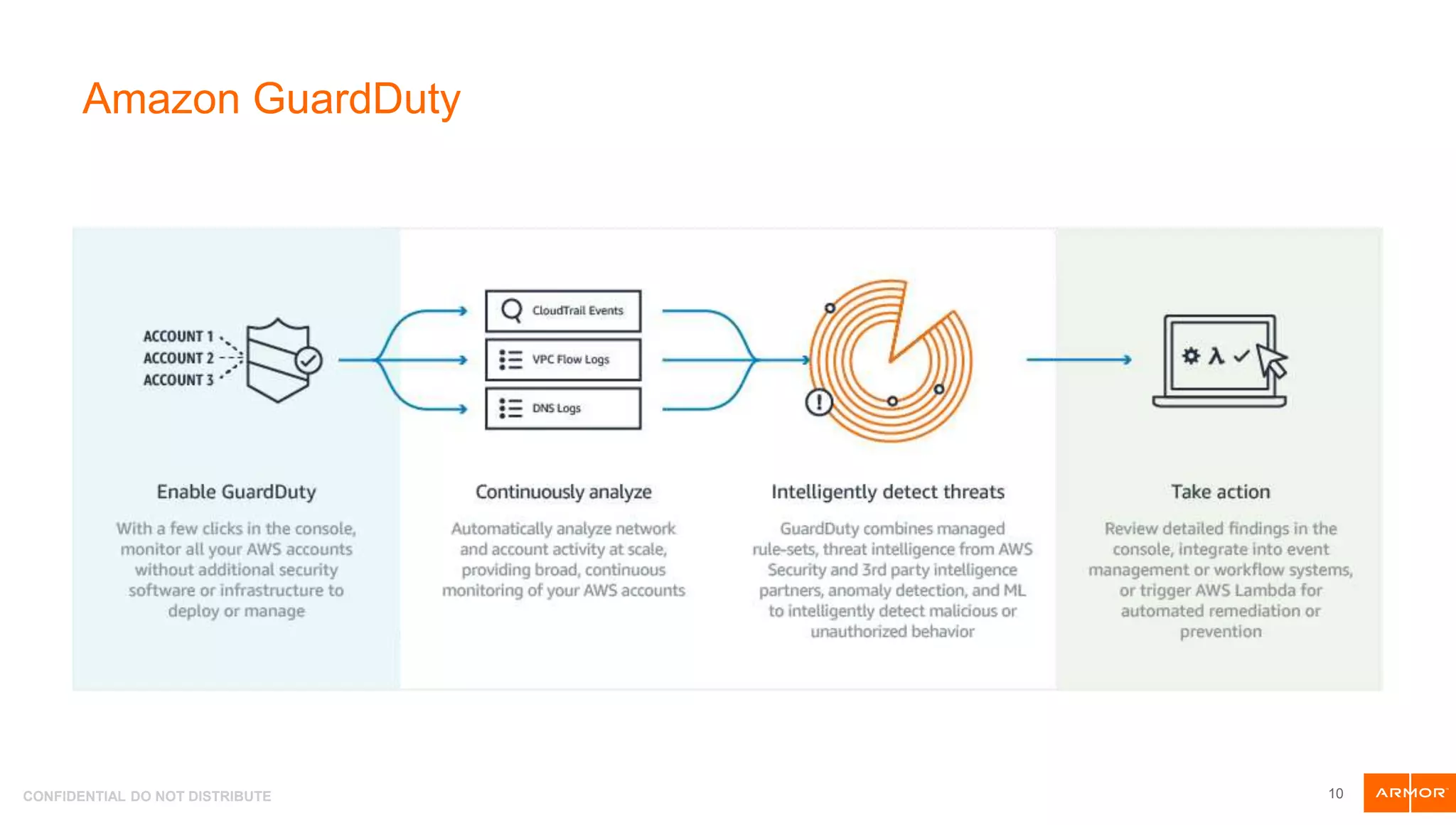
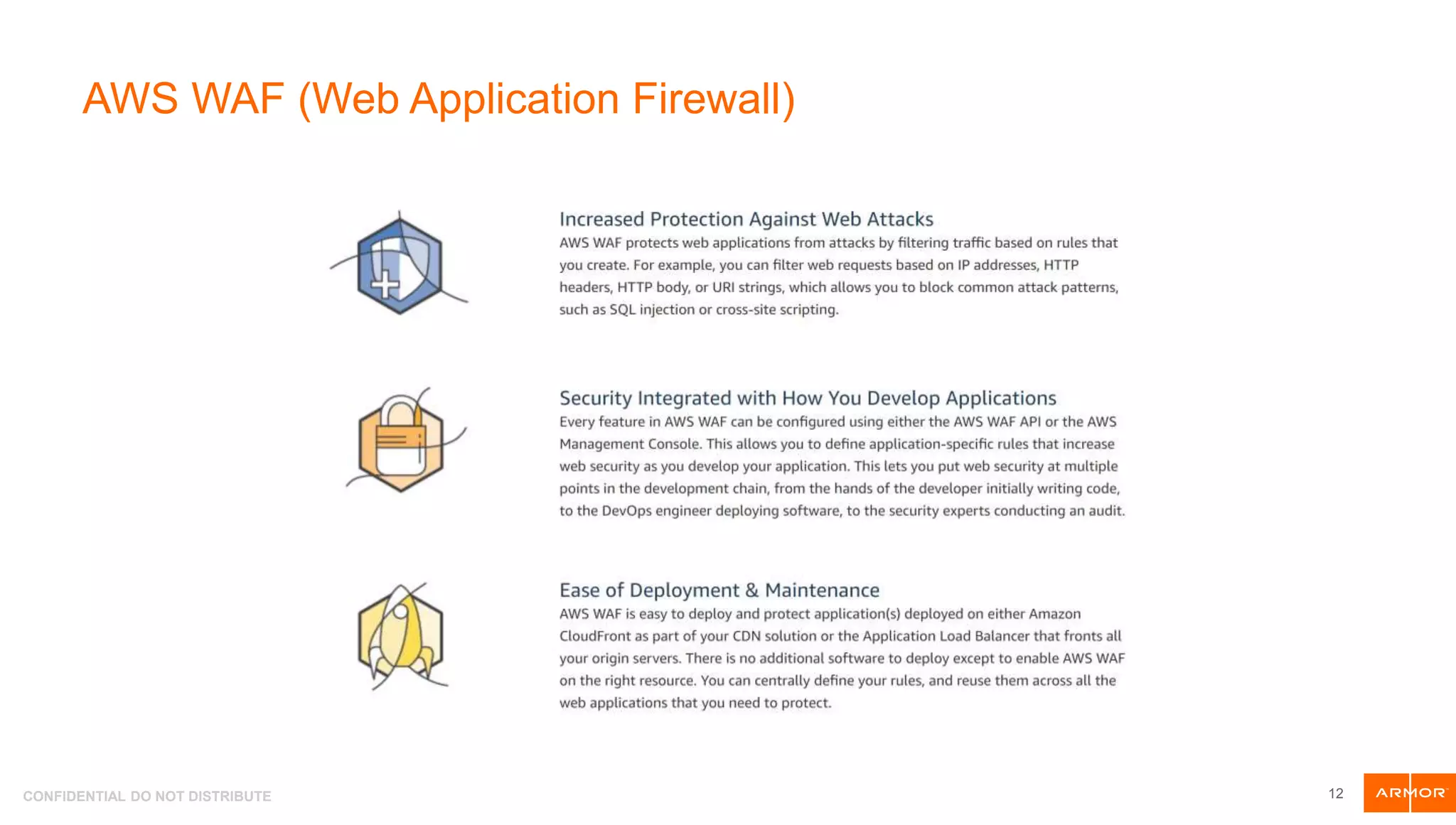
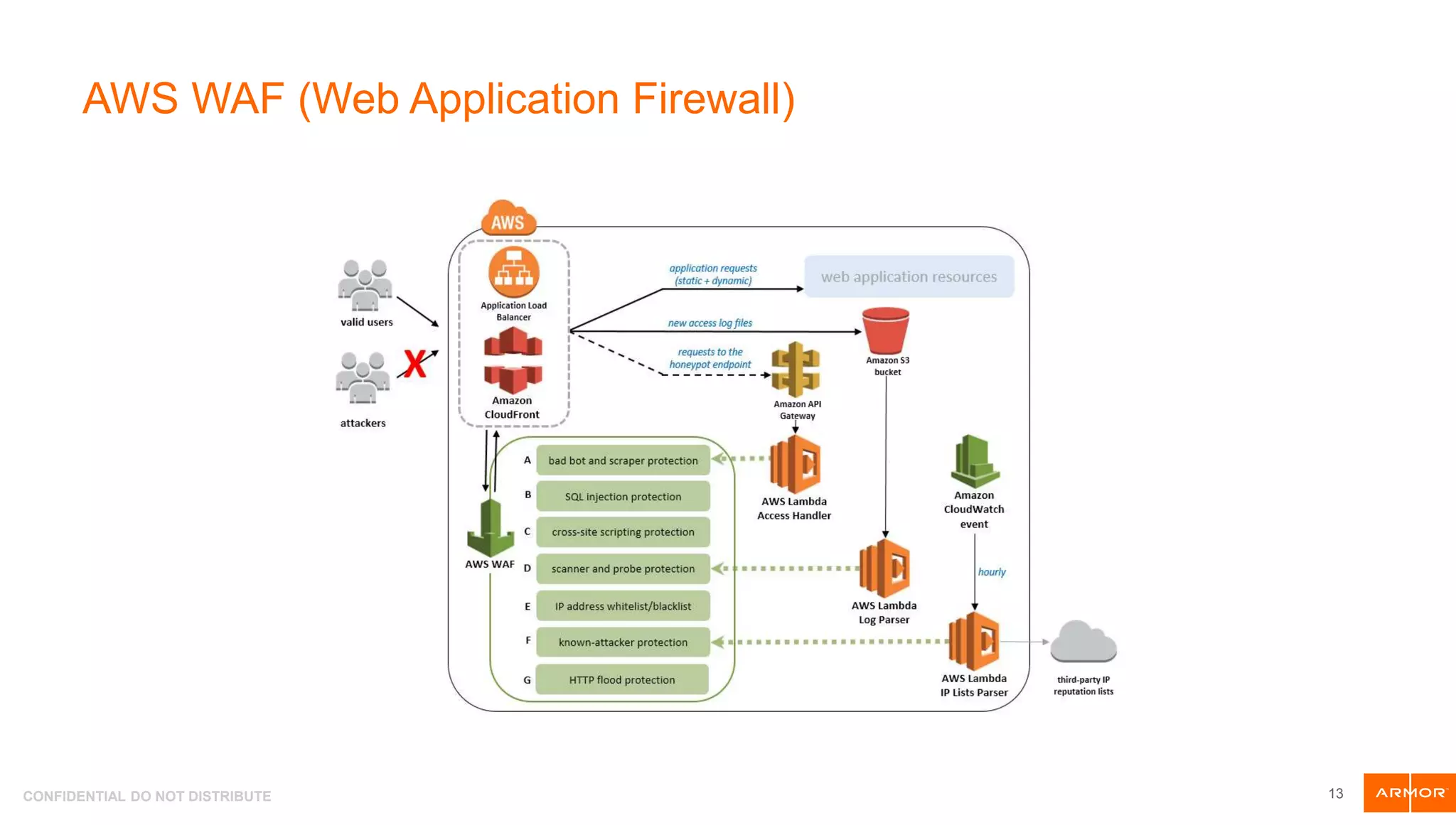
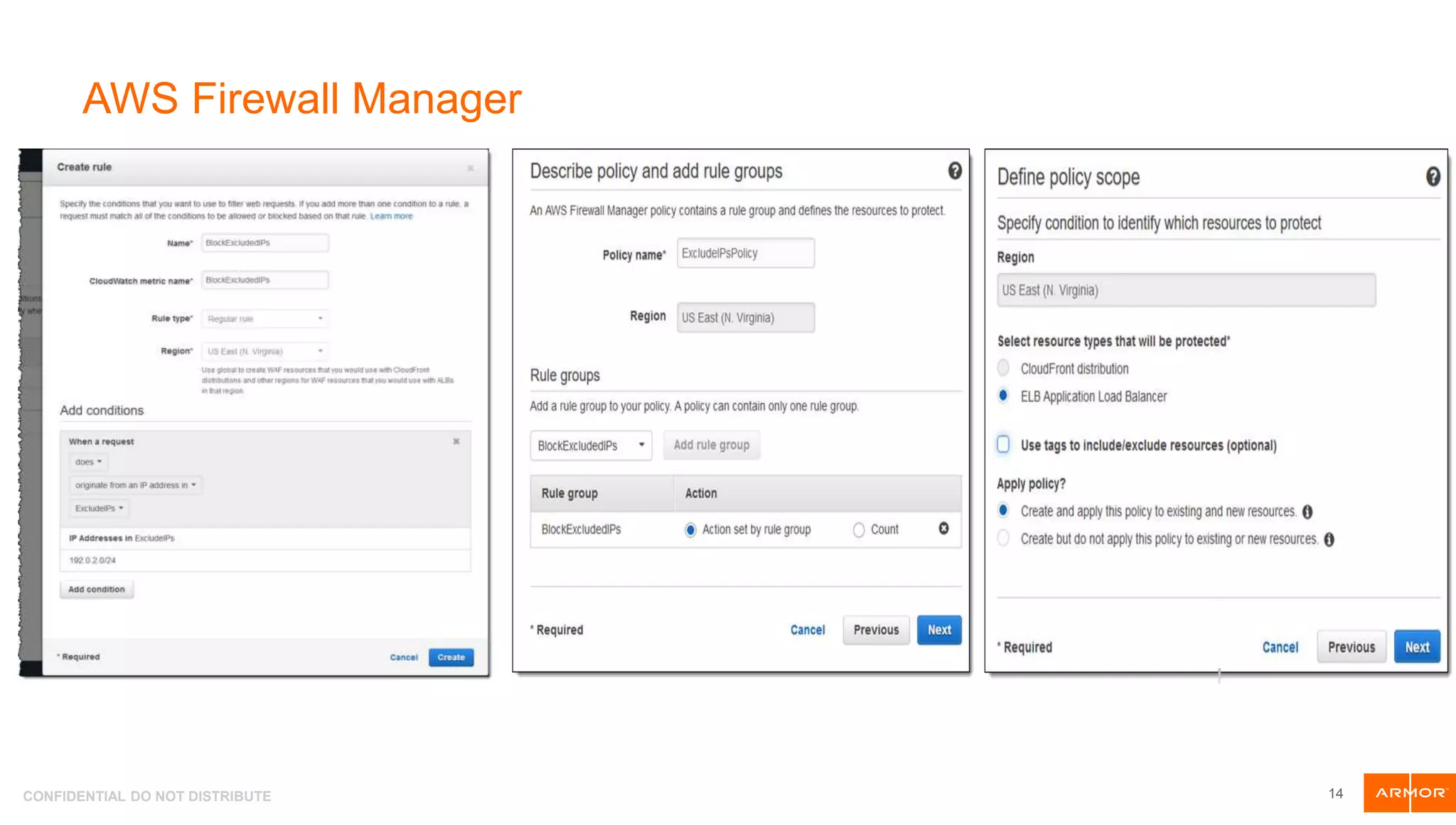
The document presents an overview of AWS security tools and highlights the shared responsibility model for cloud security, emphasizing that 95% of cloud security failures will be the customer's fault. It discusses trends in AWS security, including the integration of automation and threat hunting, as well as frameworks such as non-repudiation and the CIA triad. Various AWS security tools like Amazon GuardDuty, AWS WAF, and AWS Secrets Manager are also introduced as part of the security landscape.








![CONFIDENTIAL DO NOT DISTRIBUTE
Continuous Feedback Loop
Incident Context
Incident
Response
Playbooks and
Orchestration
Countermeasures
CONTINOUS RESPONSE REAL-TIME
VISIBILITY
Armor Management
Portal (AMP)
API Toolset
22
Local Network
[any device or appliance]
Armor Services
Host
[applications, OS, DBs]
Cloud Native
[Cloudtrail, etc.]
[FIM, IDS, VS, AM]
DATA SOURCES
REDUNDANT /
LIGHTWEIGHT
AGENT
Armor Agent
and Collector
Services
Metadata/Segmentation
Long-Term
Logging
Log
Ingestion/
Datalake
PROTECTION /
DETECTION
Correlation
Machine Learning
Behavior
Analytics
THREAT INTELLIGENCE
3rd Party Threat
Feeds
Armor
Threat Feeds
and Hunting
Community
Insights
The Spartan Platform
Armor Diagram v.2
Armor Anywhere
How Armor Uses AWS’ Native Tooling to Provide Security](https://image.slidesharecdn.com/awschicagopresentation-securitywithawsnativetooling-180523132835/75/Ryan-Smith-s-talk-from-the-AWS-Chicago-user-group-May-22-Security-22-2048.jpg)